Vulnerability Reports
EventLog Analyzer has over 50 out-of-the-box reports for analyzing log data from vulnerability scanners such as Nessus, Qualys, OpenVAS, and NMAP. The reports are essential for discovering and remediating network vulnerabilities.
Reports on Nessus vulnerability data
The information on potential vulnerabilities in a network including credential failures, elevated privilege failures, registry access failures gathered from Nessus are provided as reports. The information in the reports is also presented in the graphical format for improved insights.
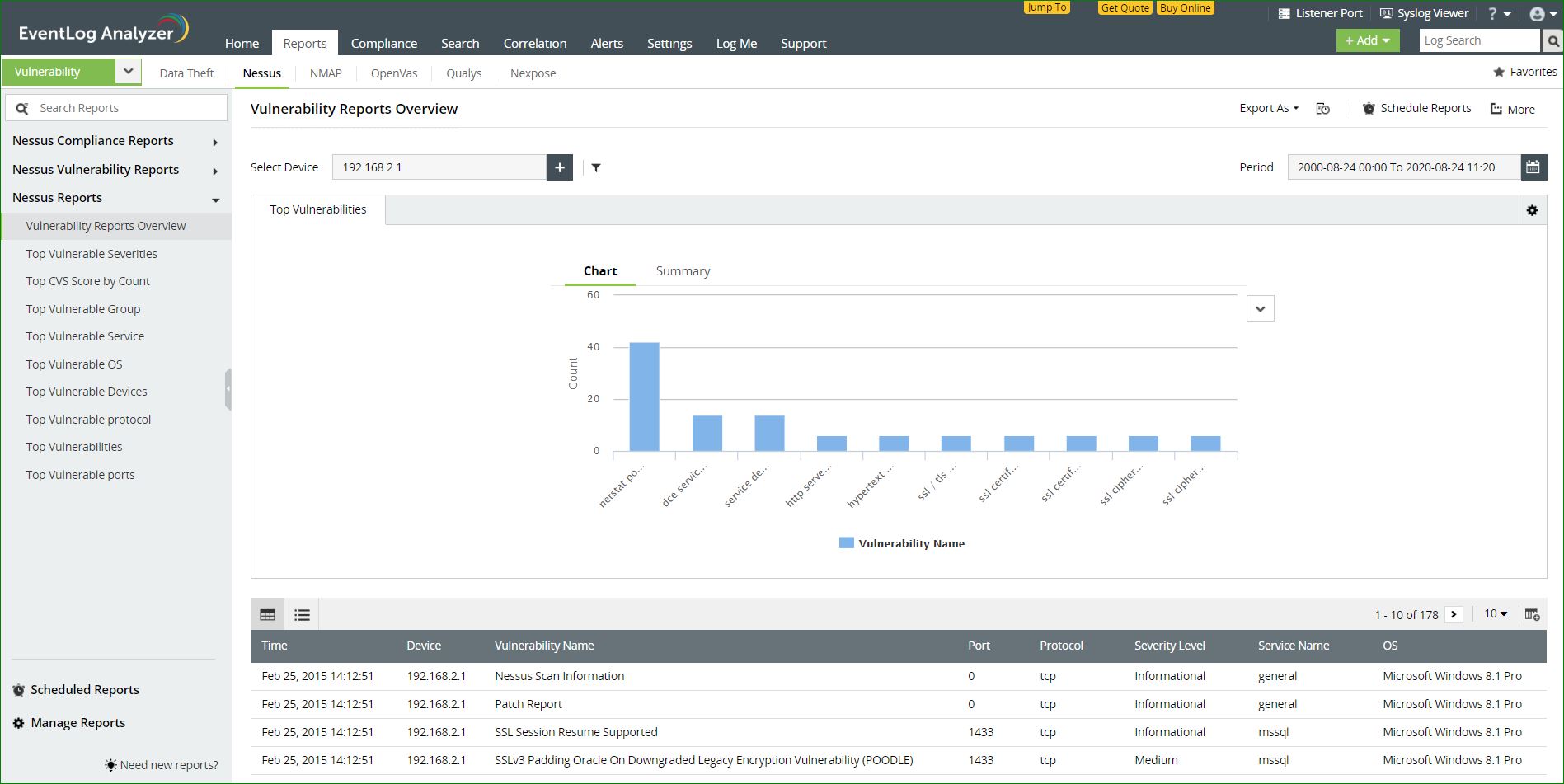
Available reports:
- GHOST in Linux - This report lists any detected instance of the GHOST vulnerability in Linux.
- Shellshock Report - This report contains information on the detected instances of the Shellshock privilege escalation vulnerability in Linux systems in your network.
- Admin Discovery Report - An overview of all the admin accounts in a network will be available in this report.
- Top exploitable vulnerabilities - An overview of the vulnerabilities in your network that are most prone to attacks will be available here.
- Credential failures report - An account of all instances of credential failures in your network will be displayed here.
- Elevated privilege failures report - Failed attempts at privilege escalation will be displayed here.
- Registry access failures - Failed attempts at accessing the Windows Registry will be recorded here.
- Patch report - A report of all the patches applied in the device will be displayed.
- Overall Nessus report - An overview of events in Nessus vulnerabilty scanners in your network will be available here.
Ensuring Compliance to regulatory mandates:
EventLog Analyzer helps in complying with regulatory mandates such as the GDPR, PCI DSS and NIST. These regulations mandate that critical events in devices and applications that could potentially lead to a data breach need to be monitored. If any indication of a breach is detected, remediating action has to be taken to mitigate this risk. Information from vulnerability scanners like Nessus form a critical part of the data that needs to be monitored.
For instance, the risk assessment (ID.RA) section of NIST compliance that states,
"The organization understands the cybersecurity risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals. Threat and vulnerability information is received from information sharing forums and sources."
The data from vulnerability scanners that can be used to ensure compliance to regulations are also categorized according to the device types, in EventLog Analyzer. The solution categorizes the reports as follows based on the devices' data that Nessus analyzes.
- Windows devices
- Unix devices
- Databases
- Cisco IOS
- Huawei
- Unix file contents
- IBM iSeries
- SonicWall, SonicOS
- Citrix XenServer
- VMware, vCenter, and vSphere infrastructure
Once the Nessus vulnerability scanner is added, this data from Nessus can be manually imported into EventLog Analyzer or automated imports can be scheduled. This data is then collated into comprehensive reports to comply with PCI DSS requirements.
- Denial of remote access software
- Denial of insecure communication
- Handling false positives
Reports on Qualys vulnerability data
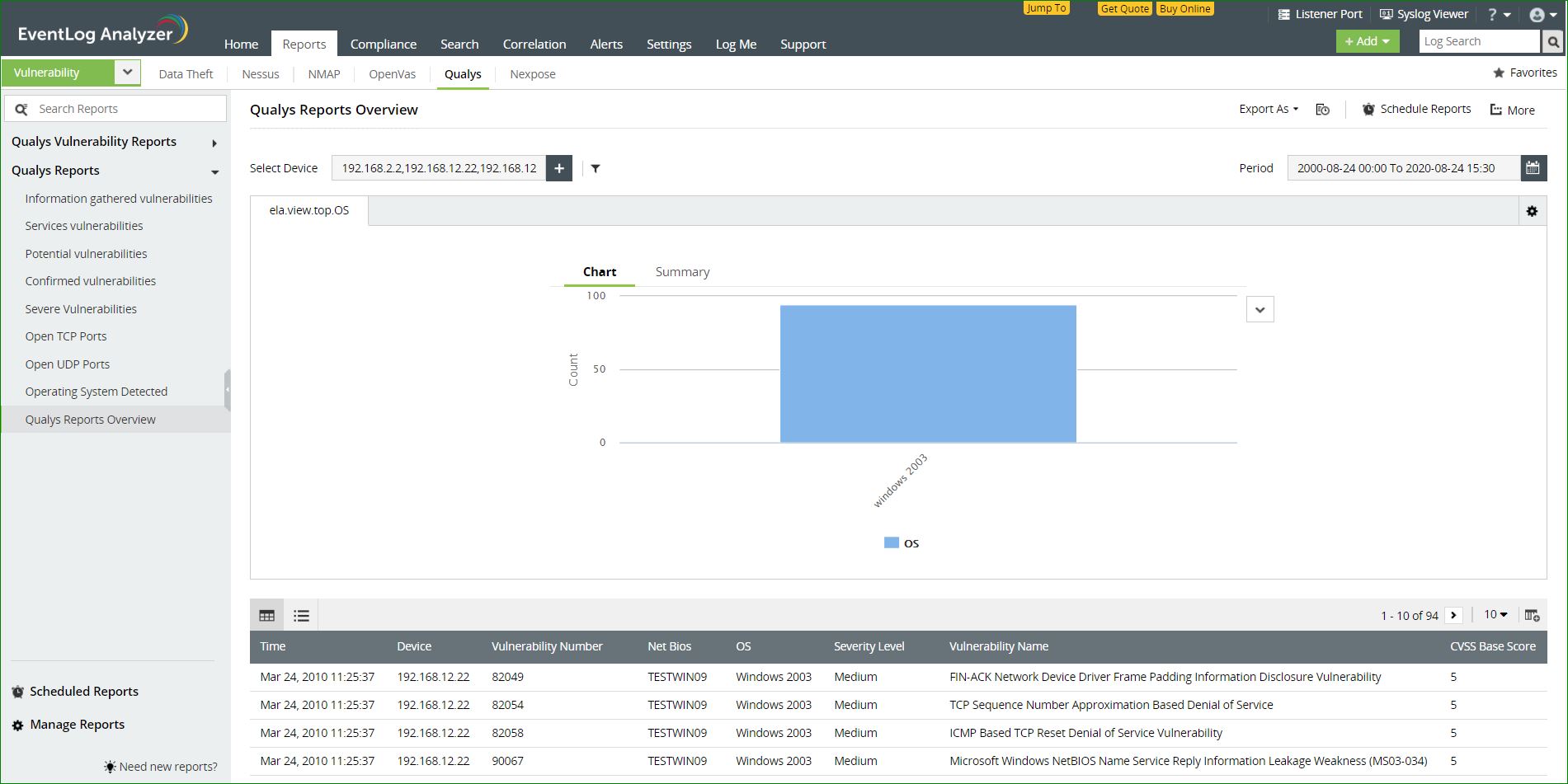
The information on potential vulnerabilities in a network including service vulnerabilities and potential vulnerabilities gathered from Qualys will be provided in these reports. This information is also presented in the graphical format for improved insights.
Available reports:
- Information gathered from vulnerabilities - Information that can be gathered from detected vulnerabilities such as CVSS scores and the severity level will be available in this report.
- Services vulnerabilities - Service vulnerabilities like open TCP and UDP services will be listed in this report.
- Potential vulnerabilities - Vulnerabilities that could be exploited by an attacker will be listed in this report.
- Confirmed vulnerabilities - Vulnerabilities that are above a CVSS base score of 5 will be listed in this report.
- Severe vulnerabilities - Vulnerabilities with the severity level 'Urgent'will be listed in this report.
- Open TCP Ports - Open TCP ports in the network will be displayed in this report.
- Open UDP Ports - Open UDP ports in the network will be displayed in this report.
- Qualys Reports Overview - An overview of all important events in Qualys reports will be displayed here.
Reports on NMAP vulnerability data
EventLog Analyzer can collect vulnerability data from open source, vulnerability scanning platforms such as NMAP. These reports can help you discover open ports in your network sorted according to device, service, or protocol.
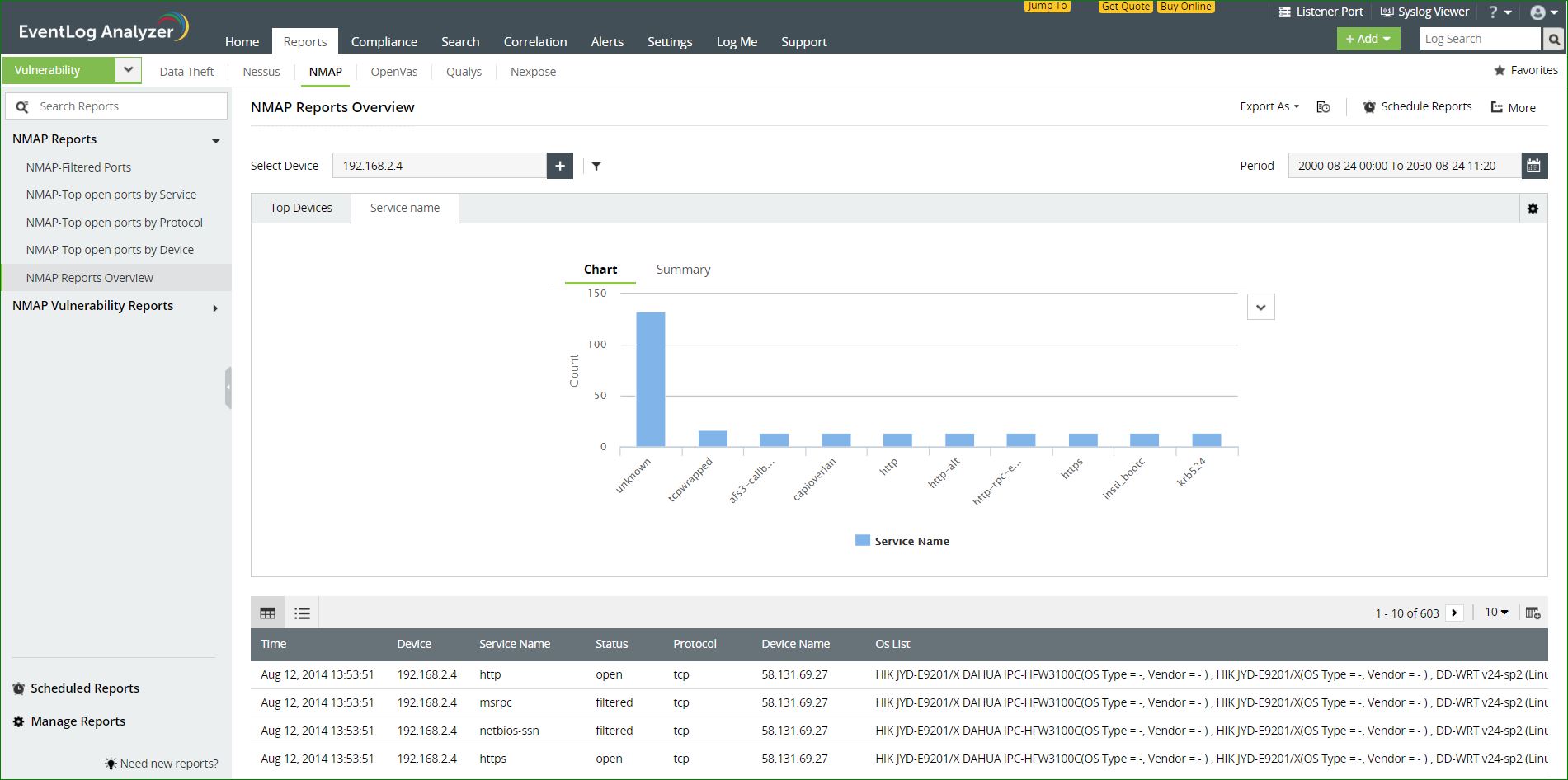
Available reports:
- Top Vulnerable Service - From NMAP data, the services in the system most prone to be exploited will be available here.
- Top Vulnerable OS - From NMAP data, the services in the operating systems most prone to be exploited will be available here.
- Top Open Ports - A list of all the open ports in the system will be available here.
- Open Ports - A list of all the open ports in the system will be available here.
- Top Vulnerable Devices - A list of the most vulnerable devices, according the the NMAP data will be available here.
- Top Vulnerable protocol - The most vulnerable protocols used in the system will be available in this report.
- Top Vulnerable ports - A list of the most vulnerable ports according to the NMAP data will be available here.
Reports on OpenVas vulnerability data
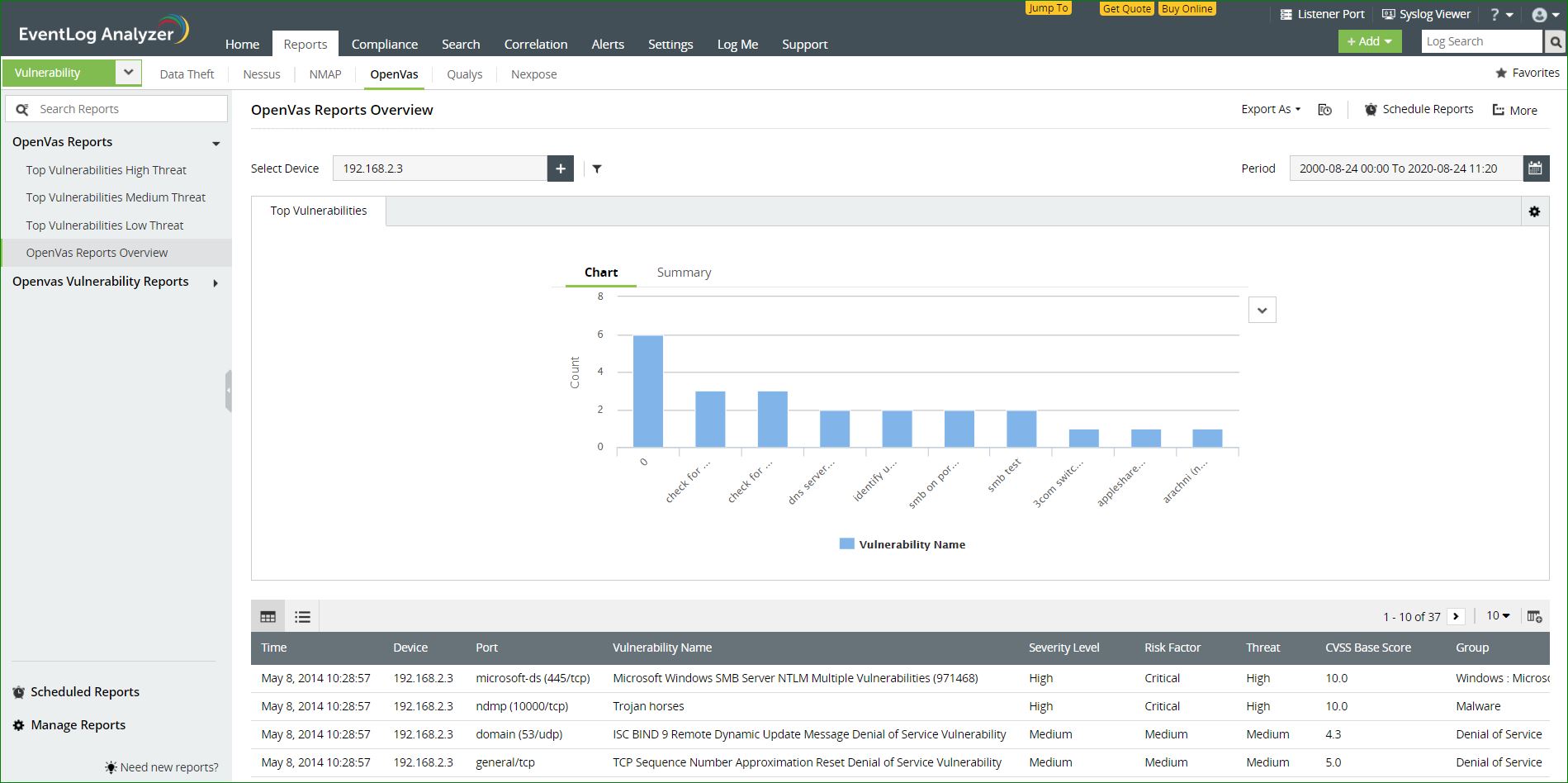
EventLog Analyzer collects data from OpenVas and helps you classify the reports based on the threat level as high, medium, or low.
- Top Vulnerabilities High Threat - Vulnerabilities that pose the highest risk of attacks will be listed here.
- Top Vulnerabilities Medium Threat - Vulnerabilities that pose a moderate risk of attacks will be listed here.
- Top Vulnerabilities Low Threat - Vulnerabilities that do not pose a high risk of attacks will be listed here.
Data from OpenVas is also segregated based on severity, CVS score, and group.
- Top CVS Score by Count - This report identifies the most frequent vulnerabilities categorized based on the CVS score.
- Top Vulnerable Group - This report lists the most vulnerable workgroups in your network based on the
- Top Vulnerabilities - This report lists the most common vulnerabilities in the network.
Reports on Nexpose vulnerability data
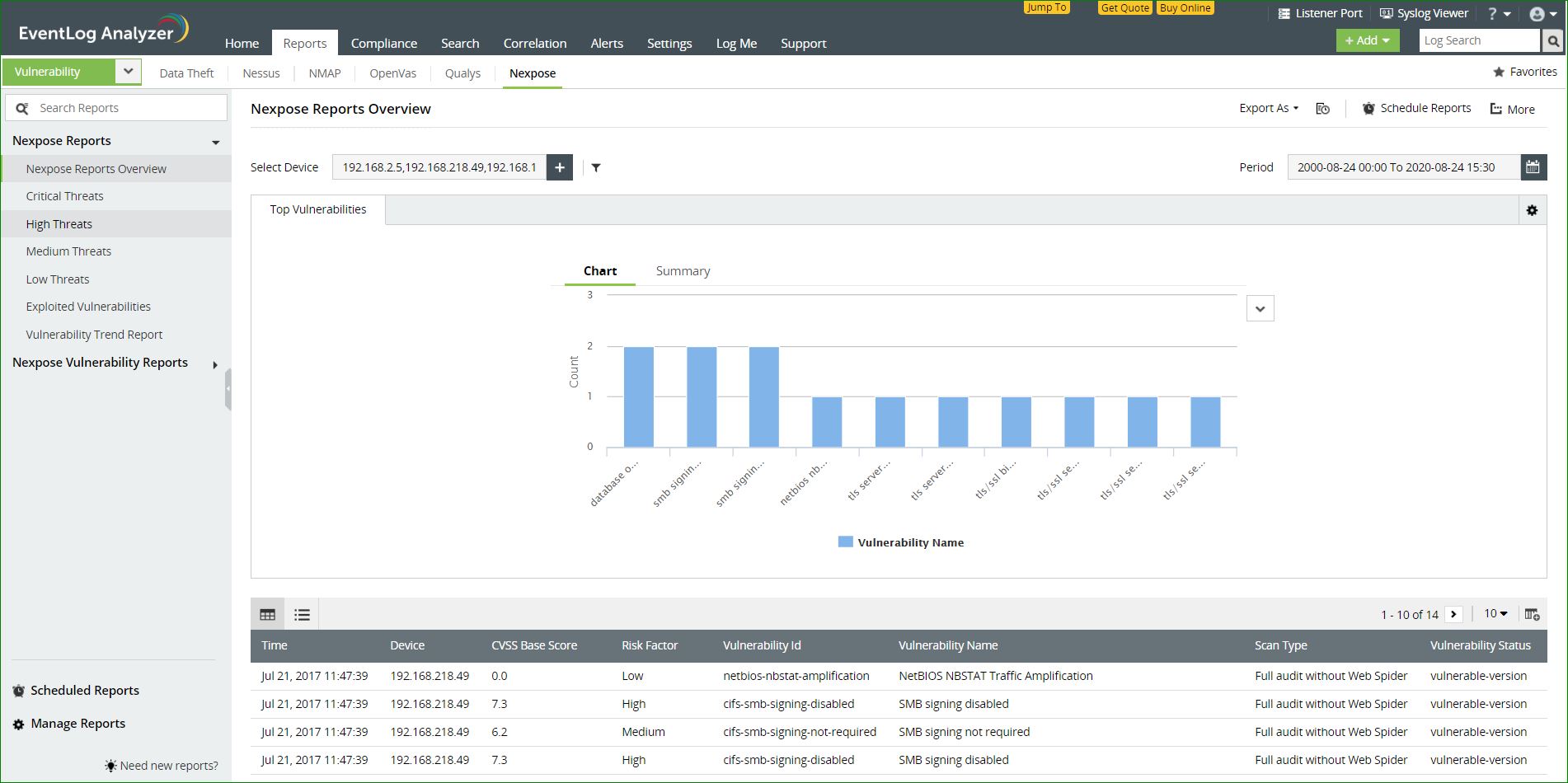
EventLog Analyzer collects data from Nexpose and categorizes the vulnerability information based on the level of severity.
Available reports:
- Critical threats - Vulnerabilities that pose the highest risk of attacks will be listed here.
- High threats - Vulnerabilities that pose a considerably high risk of attacks will be listed here.
- Medium threats - Vulnerabilities that pose a moderate risk of attack will be listed here.
- Low threats - Vulnerabilities that do not pose a high risk of attacks will be listed here.
- Vulnerability trend - The general trend that can be inferred based on the vulnerabilities in your network will be listed here.
 Click here to expand
Click here to expand




