- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
What is the NCSC?
The National Cyber Security Centre (NCSC) is the UK’s authority on cybersecurity. Its password policy recommendations are designed to ensure security while remaining user-friendly. The NCSC emphasizes password length, memorability, and the blocking of weak passwords, rather than relying on complex character requirements.
What are the NCSC password requirements
The following table explains the password policy requirements of the NCSC and how ManageEngine ADSelfService Plus helps your organization comply with them.
| NCSC requirement | Requirement description | How ADSelfService Plus helps satisfy the requirement |
|---|---|---|
| Minimum password length | Passwords should be long enough to resist brute-force attacks. The NCSC recommends using three random words (for example, applecarpetmonkey). | ADSelfService Plus allows you to enforce a custom minimum password length, to encourage users to create longer passwords, such as three random words. |
| Password complexity | Traditional complexity requirements (a mix of cases, numbers, and special characters) are not required. | ADSelfService Plus enables you to customize or remove the requirement for including uppercase, lowercase, numeric, special, and Unicode characters in user passwords, if the user chooses a strong passphrase. |
| Block common or compromised passwords | Prevent the use of common, breached, or easily guessable passwords. | ADSelfService Plus allows you to restrict users from utilizing dictionary words, palindromes, predictable patterns, repeated characters, and consecutive characters from usernames and old passwords while setting new passwords. Integrating with Have I Been Pwned?, a breached password database, ensures that your users do not set weak or compromised passwords during password resets and changes. |
| Account lockout | Lock accounts after 10 failed attempts or limits to 10 guesses in five minutes. | ADSelfService Plus enables you to configure the number of failed logon attempts that are allowed for a user within a specified time and the lockout duration. |
| User guidance | Provide clear instructions on creating strong, memorable passwords. | ADSelfService Plus features a password strength meter that indicates the strength of a user's password and displays the password complexity rules, helping users understand and choose a strong password. |
| Two-factor authentication (2FA) | Strongly recommended, especially for privileged accounts. | ADSelfService Plus provides adaptive 2FA with 20 different authentication factors to secure organizational resources, such as machines, applications, VPNs, OWA, and RDPs. |
NCSC password guidance and tips
In addition to the password policy requirements, the NCSC also provides six essential tips to help individuals and organizations create a secure authentication policy. Here’s a brief overview of each tip, based on its most recent guidance:
Tip #1: Reduce your organization's reliance on passwords
Only use passwords where necessary and appropriate. Consider alternatives such as single sign-on (SSO), hardware tokens, and biometric authentication to reduce the burden on users. Always use MFA for important accounts and internet-facing systems to add an extra layer of security.
Tip #2: Implement technical solutions
Rely on technical defenses rather than expecting perfect user behavior. Use measures like account throttling (delays after failed login attempts) or lockout (after five to 10 failed attempts) to defend against brute-force attacks. Employ security monitoring to detect suspicious activity and use password deny lists to prevent common, easily guessed passwords from being used.
Tip #3: Protect all passwords
Ensure passwords are protected in transit (using HTTPS), at rest (using salted, iterated cryptographic hashes), and within access management systems. Prioritize securing privileged and vulnerable accounts, change all default passwords, and protect access to user databases. MFA should be the primary protection for high-value accounts.
Tip #4: Help users cope with password overload
Support users in managing multiple passwords by providing secure storage options, such as password managers. Avoid enforcing regular password expiry, as it leads to weaker passwords and user frustration. Instead, require password changes only if compromise is suspected. Use delegation tools instead of password sharing, and apply additional controls if sharing is unavoidable.
Tip #5: Help users generate better passwords
Encourage the use of password managers and their built-in generators for strong, unique passwords. Avoid complexity requirements (like mandatory special characters) as they are ineffective. Instead, set a minimum password length and use deny lists to block weak choices. The "three random words" approach is recommended for memorable, strong passwords.
Tip 6: Use training to support key messages
Focus training on practical advice, such as the dangers of password reuse, creating hard-to-guess passwords, and prioritizing the protection of high-value accounts. Teach users how to use password managers and MFA, and make training applicable to both work and personal accounts to reduce overall risk
Simplify NCSC compliance using ADselfService Plus
The ADSelfService Plus Password Policy Enforcer satisfies NCSC requirements and can be enforced for all or specific AD users based on their domain, OU, or group membership. With its adaptive MFA techniques, ADSelfService Plus ensures your organizational identities are effectively secured for a comprehensive Zero Trust environment.
- Enforce minimum password length: Require a custom minimum password length to encourage users to create longer, more secure passwords that align with NCSC password policy requirements.
- Relax password complexity: Do not require users to include uppercase, lowercase, numeric, or special characters as the NCSC password policy recommends focusing on password length and memorability, not complexity.
- Ban weak and compromised passwords: Block the use of leaked, weak, or easily guessable passwords, including dictionary words, repetitive or sequential characters, and palindromes, to reduce the risk of credential-based attacks.
- Mandate MFA for users: Secure user access to sensitive defense-related data by enabling adaptive MFA for endpoints, such as for machine logons, application logons, VPN logons, RDP logons, and OWA logons. Choose from a range of 20 different MFA authenticators, including FIDO passkeys and biometrics, to verify users' identities, helping organizations satisfy NCSC recommendations for strong authentication over privileged accounts.
- Password Policy Enforcer
- MFA
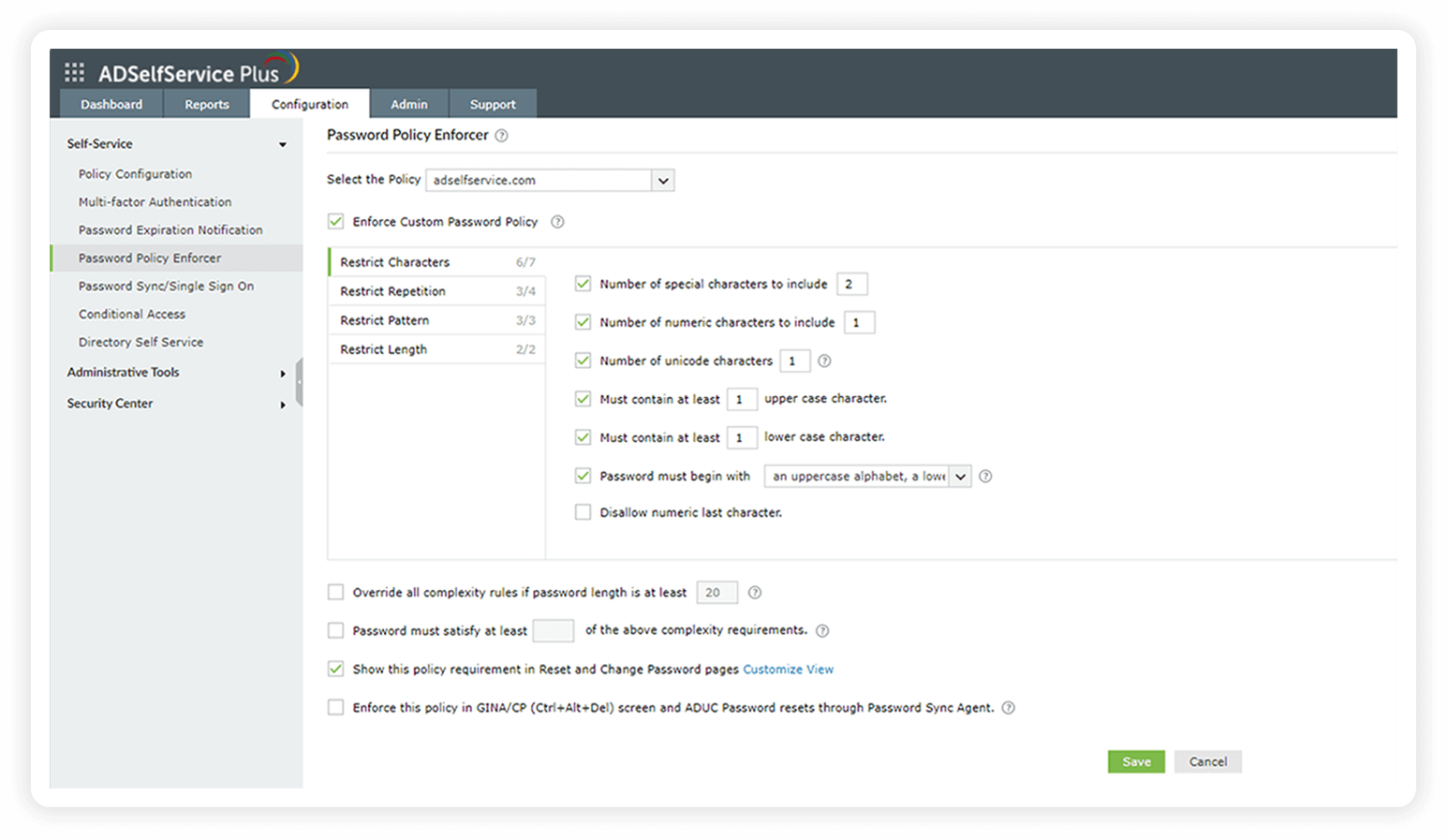
Restrict users from reusing any of their previously used passwords during password creation.
Configure the minimum password length and the inclusion of alpha-numeric characters in passwords.
Choose the minimum number of complexity requirements your users' passwords should satisfy as per your organization's security needs.
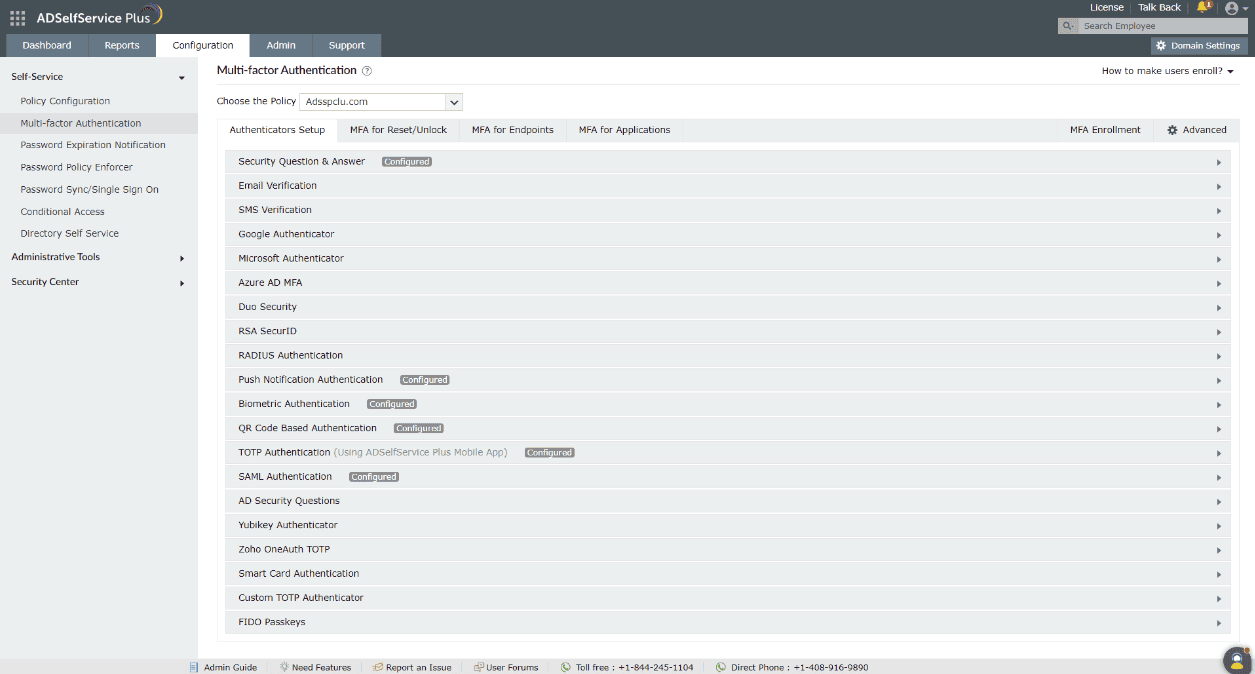
Choose from a plethora of different authenticators to verify your users' identities.
Secure all endpoints in your network using MFA.
Highlights of ADSelfService Plus
Password self-service
Eliminate lengthy help desk calls for Windows Active Directory users by empowering them with self-service password reset and account unlock capabilities.
One identity with a single sign-on
Gain seamless one-click access to more than 100 cloud applications. With enterprise single sign-on, users can access all their cloud applications using their Windows Active Directory credentials.
Password synchronization
Synchronize Windows Active Directory user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
MFA
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
Password and account expiration notifications
Notify Windows Active Directory users of their impending password and account expiration via email and SMS notifications.
Password policy enforcer
Strong passwords resist various hacking threats. Require Windows Active Directory users to adhere to compliant passwords by displaying password complexity requirements.










