- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
Why you need a password policy enforcer for Active Directory
Weak, reused, or non-compliant passwords remain one of the biggest security risks in Active Directory environments. Active Directory Group Policy's password policy tool offers only basic controls, making it difficult for IT admins to enforce strong, organization-wide password standards. Without a robust password policy enforcer, users may create passwords that are easy to guess, violate compliance mandates, or fail to meet internal security requirements.
Like many organizations, you may struggle to find a password policy enforcement solution that offers the flexibility, control, and depth needed to address modern security challenges. You need a comprehensive Active Directory password policy enforcer that supports granular rules, real-time strength checks, and consistent configuration across your network.
Native Windows Active Directory password policy
What are the Active Directory password policy requirements?
- Minimum password length
- Minimum password age
- Maximum password age
- Password complexity requirements
- Password history enforcement
- Reversible encryption for storing passwords
Loopholes in Windows Active Directory password complexity
- There is no one-size-fits-all Active Directory password policy. Password policies should be customizable to suit different hierarchies, geographical regions, and departments within an organization. However, an Active Directory password policy lacks this flexibility, and it cannot be applied to OUs.
- When admins reset passwords using the Active Directory Users and Computers (ADUC) console, the native password policy settings cannot be enforced.
- The ability to prevent consecutive repetition of the same character does not exist within the native password policy settings.
- Dictionary words, patterns, and palindromes cannot be restricted while configuring a password policy natively.
- The native password policy settings cannot be configured to define the number of characters required from specific character types.
- An Active Directory password policy cannot prevent sophisticated, modern password attacks, like dictionary and brute-force attacks.
- On the whole, it's challenging for admins to keep tracking the assigned password policies in a particular domain.
Tips from experts: NIST password guidelines
The National Institute of Standards and Technology (NIST) revolutionized password security with its guidelines. Here are the key recommendations from the NIST 800-63B for enterprises:
5.1.1.1 Memorized Secret Authenticators
- Memorized secrets shall be at least eight characters in length if chosen by the subscriber.
5.1.1.1 Memorized Secret Verifiers
- Verifiers should permit subscriber-chosen memorized secrets to be at least 64 characters in length.
- All printing ASCII characters as well as the space character should be acceptable in memorized secrets. Unicode characters should be accepted as well.
- When processing requests to establish and change memorized secrets, verifiers shall compare the prospective secrets against a list that contains values known to be commonly-used, expected, or compromised. For example, the list may include, but is not limited to:
- Passwords obtained from previous breach corpuses.
- Dictionary words.
- Repetitive or sequential characters (e.g., 'aaaaaa', '1234abcd').
- Context-specific words, such as the name of the service, the username, and derivatives thereof.
- Verifiers should offer guidance to the subscriber, such as a password-strength meter, to assist the user in choosing a strong memorized secret.
Active Directory's native password policies don't fully align with modern NIST guidelines. This is where Manageengine ADSelfService Plus helps bridge the gap in identity security.
Effective Active Directory password rules with ADSelfService Plus
ADSelfService Plus' Password Policy Enforcer overcomes the limitations of native Active Directory password policies. It enables organizations to implement custom and strong password policies that seamlessly integrate with the existing Active Directory policy. This strengthens Active Directory passwords to ensure that organizational resources remain protected against cyberthreats.
How to strengthen an Active Directory password policy with ADSelfService Plus' Password Policy Enforcer
The Password Policy Enforcer in ADSelfService Plus can be set to enforce the following password policy requirements.
- Restrict characters
- Restrict repetition
- Restrict pattern
- Restrict
length - Restrict compromised
passwords
Restrict characters: This section of the Password Policy Enforcer includes mandating the number of special, numeric, and Unicode characters. You can also set the type of character that the password should start with.
Configure the inclusion of alpha-numeric characters in passwords.
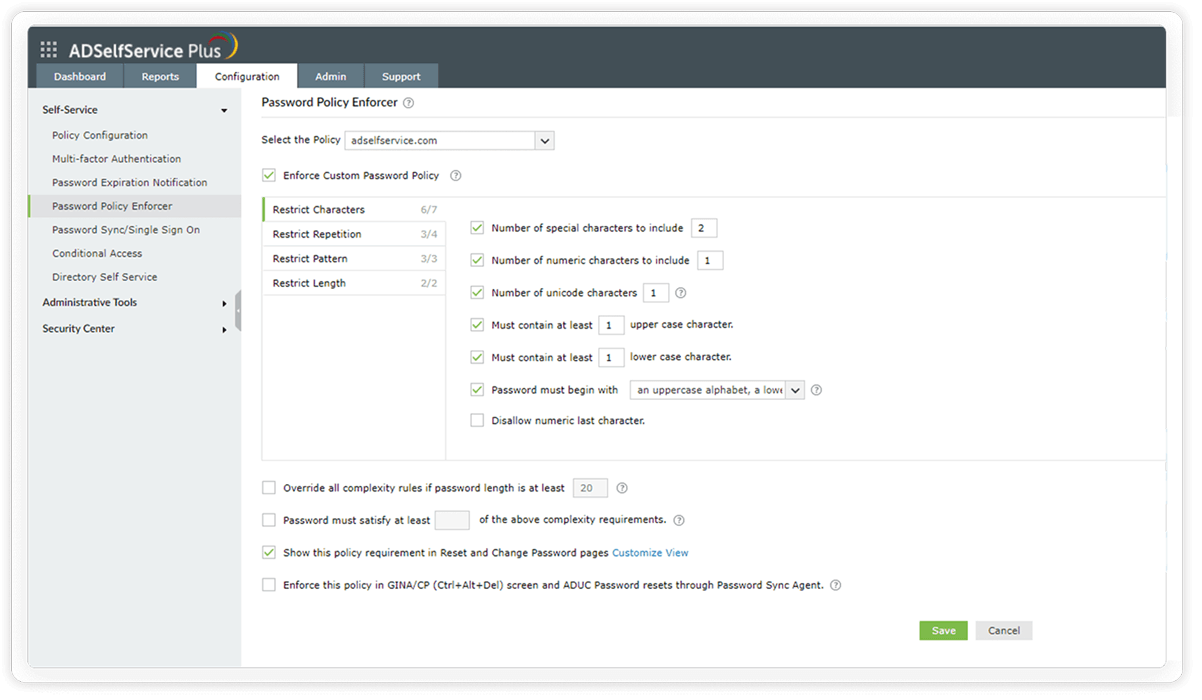
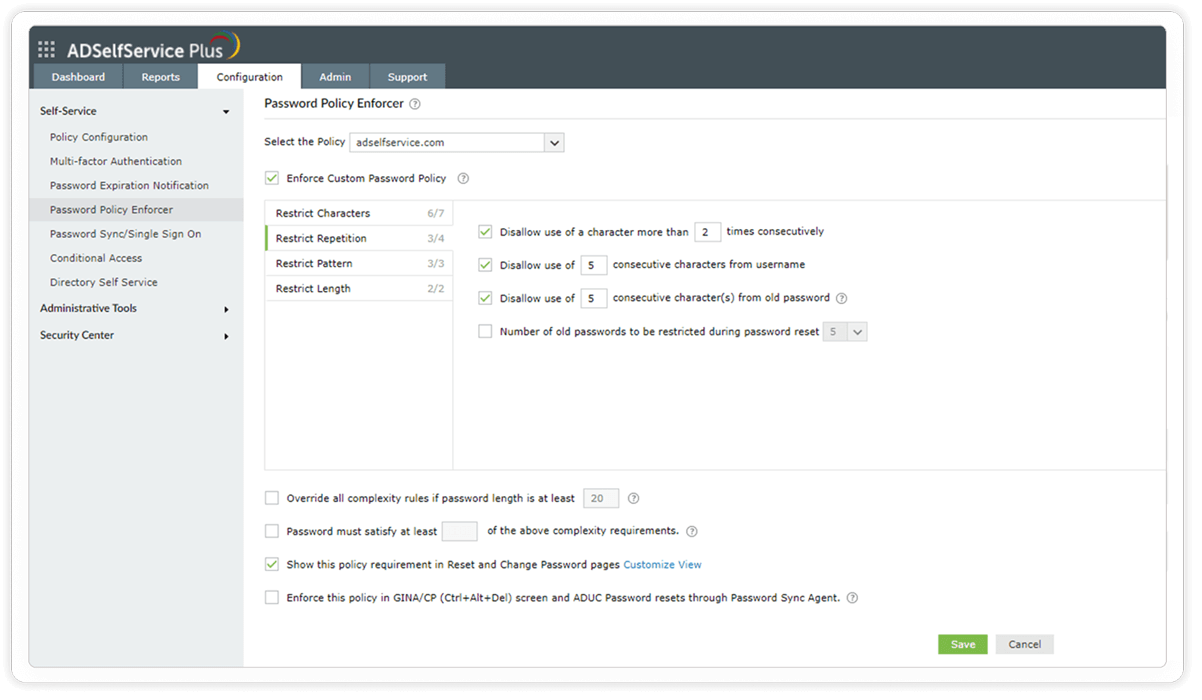
Restrict repetition: This section of the Password Policy Enforcer allows you to enforce password history and restrict the use of consecutive characters from usernames or previous passwords. Consecutive repetition of the same character can also be restricted.
Restrict users from reusing their previous passwords during password creation.
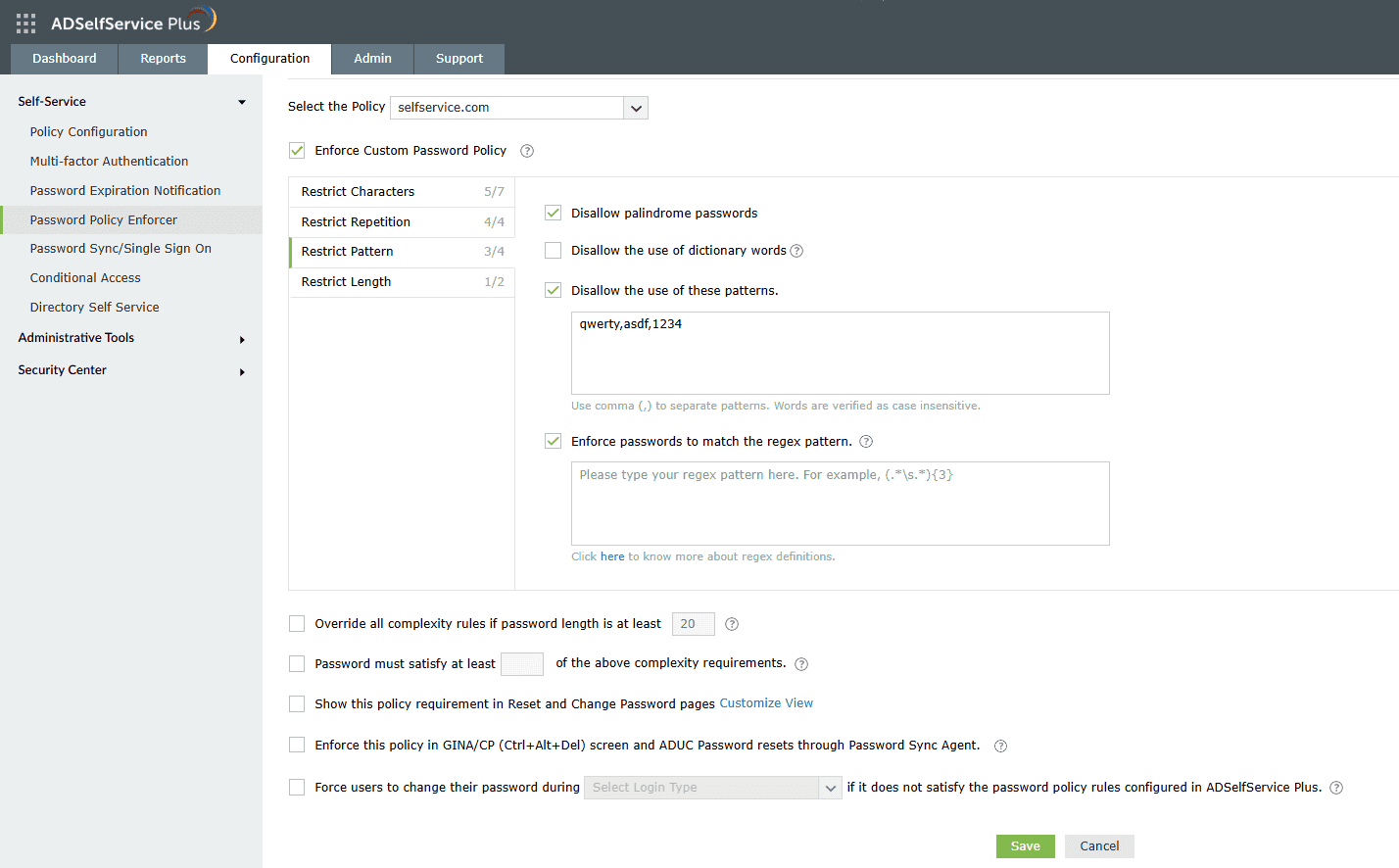
Restrict pattern: This section of the Password Policy Enforcer restricts the use of custom dictionary words, patterns, and palindromes in passwords. You can configure custom regex patterns that your users' passwords must meet, allowing you to define precise password requirements according to your organization’s needs.
Restrict users from using common patterns, dictionary words, and palindromes in their passwords.
Enforce a custom and granular password policy using regex patterns.
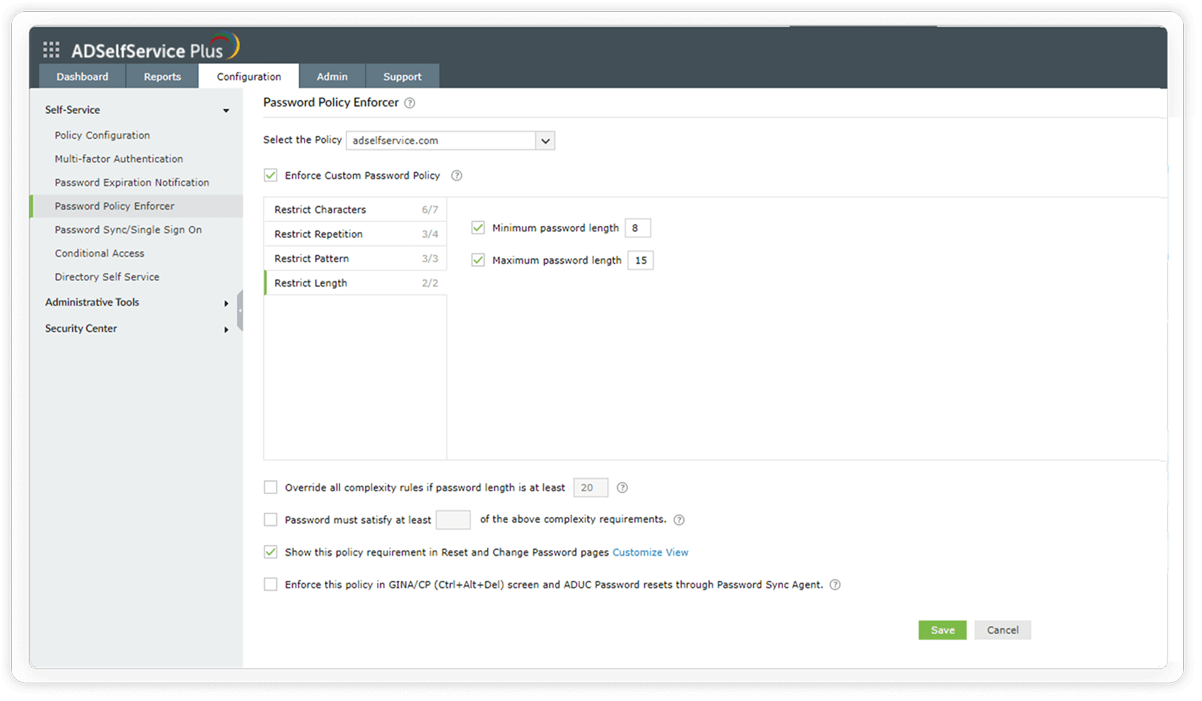
Restrict length: This section of the Password Policy Enforcer lets you set both a minimum and maximum number of characters for the password.
Configure the minimum and maximum password length to satisfy the NIST password guidelines.
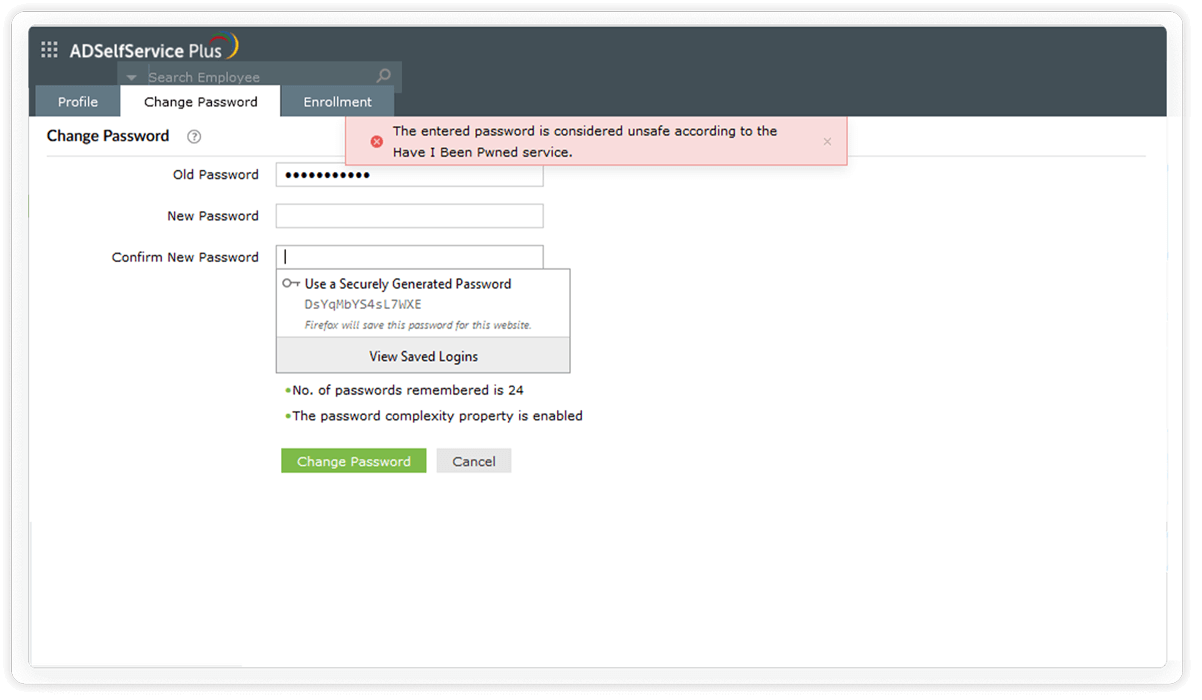
Restrict compromised passwords: ADSelfService Plus lets you integrate with the Have I been Pwned service, which bans the use of passwords involved in previous hacks and prevents credential stuffing attacks.
GPO password policy vs. Fine-grained password policy vs Password Policy Enforcer
| Capabilities | GPO password policy | Fine-grained password policy | ADSelfService Plus |
|---|---|---|---|
| Enforce uppercase, lowercase, numeric, and special characters, as well as Unicode. | X (All types cannot be enforced together) | X(All types cannot be enforced together) | ✓ (Inclusion can be enforced for all these characters) |
| Block breached passwords, dictionary words, or custom dictionary entries. | X | X | ✓ |
| Prevent repeated characters, sequences, palindromes, and username-based patterns. | X | X | ✓ |
| Restrict reuse of old passwords or consecutive characters from them. | X (Old passwords in their entirety can be blocked) | X (Old passwords in their entirety can be blocked) | ✓ |
| Set minimum and maximum lengths; allow bypass of complexity for long passphrases. | X (Complexity cannot be bypassed for passphrases) | X (Complexity cannot be bypassed for passphrases) | ✓ |
| Apply policies to specific OUs, groups, or scenarios (logon screen, ADUC resets). | X (Policies cannot be enforced for specific groups or OUs) | X (Policies cannot be enforced for specific groups or OUs) | ✓ |
| Display password requirements directly on the Windows logon screen. | ✓ | ✓ | ✓ |
Benefits of implementing password policies using ADSelfService Plus
Highlights of ADSelfService Plus
Password self-service
Unburden Windows AD users from lengthy help desk calls by empowering them with self-service password reset and account unlock capabilities.
Multi-factor authentication
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
One identity with single sign-on
Get seamless one-click access to more than 100 cloud applications. With enterprise single sign-on (SSO), users can access all their cloud applications using their Windows AD credentials.
Password and account expiry notifications
Notify Windows AD users of their impending password and account expiry via email and SMS notifications.
Password synchronization
Synchronize Windows AD user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Password policy enforcer
Strong passwords resist various hacking threats. Enforce Windows AD users to adhere to compliant passwords by displaying password complexity requirements.
FAQ
A password policy is a set of rules created and enforced to strengthen user passwords. A password that satisfies and enforces all the rules of a password policy helps better secure the underlying data against potential password attacks. A password policy includes rules that specify minimum password length, maximum password age, password history requirements, and password complexity details.
A password attack refers to a threat actor trying to authenticate themselves maliciously into your password-protected account using a compromised password. The different types of password attacks are dictionary attack, brute-force attack, credential stuffing, phishing, manipulator-in-the-middle attack, password spraying, and keylogger attack.
A dictionary attack involves a threat actor trying to hack into a user account by repeatedly trying various combinations of dictionary words. Often, the words used are not necessarily dictionary words but predictable password choices, like names, birth places, or pet's names, which users normally tend to use in their passwords. For this reason, users are advised to avoid such words while setting passwords.
In a brute-force attack, all possible combinations of characters are systematically tried. In contrast, a dictionary attack uses a predefined list of commonly used phrases or variations of those phrases to attempt to gain unauthorized access. Dictionary attacks are generally faster but rely on the assumption that the correct password is among the entries in the dictionary list.
Active Directory password complexity requirements are settings that mandate that users include certain special characters, like uppercase, lowercase, or non-alphanumeric characters, and to avoid using their usernames in their passwords. Users have chosen strong passwords when the complexity requirements of the enforced domain password policy are met.
Securing a user account or data endpoint with only a password makes it most vulnerable to the password attacks of today. Deploying multi-factor authentication mechanisms are a good practice to render compromised credentials useless to hackers. Strong authentication mechanisms like biometrics have made passwordless user authentication possible.
The default Active Directory domain password policy defines configurable rules for user account password creation. This password policy is only applicable to the entire domain to which it is linked, and it cannot be customized for a specific set of users, groups, or OUs. Active Directory's FGPP, on the other hand, overcomes this drawback and allows password policies to be tailored to different users and groups within the domain.










