- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
The limitations of password-only RADIUS Authentication
RADIUS (Remote Authentication Dial-In User Service) is a network authentication protocol used to centralize authentication for users accessing network resources. It’s commonly used to authenticate VPN connections; remote machines and servers; and network devices.
In many environments, RADIUS authentication involves the (Network Policy Server) NPS communicating with Active Directory to validate usernames and passwords before granting access. An additional layer of authentication involving password, PIN, or TOTP, called Access-Challenge, can also be initiated based on configuration.
While this setup provides reliable credential validation, password-only RADIUS authentication remains vulnerable to phishing, credential theft, and brute-force attacks. Native NPS configurations lack built-in RADIUS MFA and modern security flexibility without third-party or cloud extensions.
To achieve secure access, organizations must extend RADIUS authentication with MFA — without disrupting existing AD and NPS integrations.
Leverage RADIUS-based authentication with modern MFA for VPNs, machines, and enterprise app access
With ADSelfService Plus, you can enhance RADIUS authentication to protect critical endpoints via MFA for machines, MFA for RDP, and MFA for enterprise applications along with other advanced authentication methods. ADSelfService Plus also elevates the authentication process in RADIUS-based endpoints such as Microsoft Remote Desktop Gateway and VPNs logins by adding MFA methods like biometrics, TOTP, and push verification — without replacing their existing RADIUS server.
Step-by-step guide to how RADIUS MFA Works
Active Directory RADIUS authentication integration
Here’s how ADSelfService Plus integrates with your RADIUS server and Active Directory to secure access:
- User login: The user connects to a endpoint and enters their Active Directory username and password.
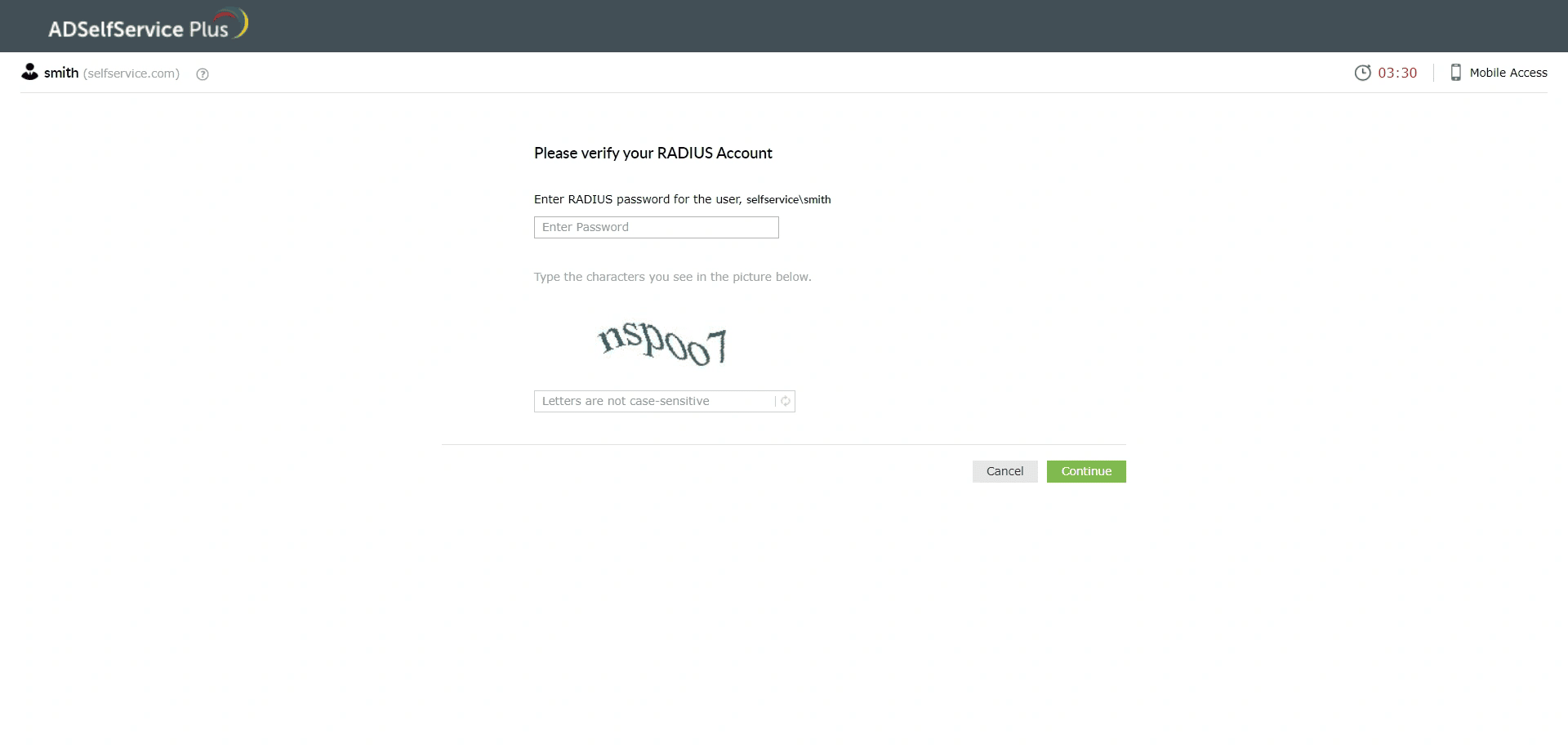
- Request to ADSelfService Plus: Once ADSelfService Plus verifies the Active Directory credentials, and prompts the user for their RADIUS password.
- Forward to NPS server: ADSelfService Plus then forwards the RADIUS password to the NPS server.
- Response from NPS: The NPS server validates the credentials with AD and returns one of the following responses:
- Access-Accept: Indicating successful authentication.
- Access-Challenge: Requiring the second factor configured in your RADIUS setup.
- Access-Reject: Indicating an unsuccessful attempt.
- Access decision: ADSelfService Plus relays the final response to the endpoint, granting access only if RADIUS MFA succeeds.

Advanced RADIUS server MFA
ADSelfService Plus augments the default RADIUS authentication process in VPNs and other platforms such as Citrix Gateway, VMware Horizon, and Parallels RAS with MFA.
- User login: The user initiates a VPN connection using their VPN client and enters their Active Directory username and password.
- Forward to NPS server: ADSelfService Plus forwards the credentials to the NPS server and receives its response.
- Response to ADSelfService Plus: The NPS server receives the credentials and sends an Access-Challenge response to ADSelfService Plus.
- RADIUS MFA: ADSelfService Plus prompts the user to complete the configured secondary authentication such as biometrics and YubiKey token.
- Response to NPS server: Once MFA verification succeeds, ADSelfService Plus returns an Access-Accept RADIUS response to the NPS server. If authentication fails, an Access-Reject response is returned.
- Access decision: The NPS server grants access only if an Access-Accept message is received from ADSelfService Plus, ensuring that both Active Directory credentials and MFA verification are successful.
Supported RADIUS MFA Methods
ADSelfService Plus supports a wide range of second factors for RADIUS authentication, including:
- Biometric authentication
- TOTP authentication
- Microsoft Authenticator
- YubiKey Authenticator
- Zoho OneAuth TOTP
- Push notification authentication
Comprehensive RADIUS MFA with Active Directory integration
ADSelfService Plus delivers seamless RADIUS MFA across VPNs, enterprise apps, and other network endpoints—without requiring any changes to your existing NPS server. By combining Active Directory and RADIUS authentication with advanced MFA capabilities, it ensures only verified users gain access to corporate resources.
- Centralize identity management through Active Directory and RADIUS authentication without modifying the existing NPS infrastructure.
- Apply granular MFA policies based on OU, group, domain, tailoring RADIUS MFA to different user segments.
- Implement conditional access to trigger RADIUS authentication only for specific locations, IP addresses, devices, or login times.
- Enable backup codes and recovery options to ensure uninterrupted access when the primary RADIUS MFA factor is unavailable.
- Audit all RADIUS authentications with detailed reports.
- Deploy at scale across multiple VPN and network gateways using ADSelfService Plus’s built-in RADIUS server MFA architecture.
This unified Active Directory RADIUS authentication approach simplifies deployment, enhances endpoint security, and delivers adaptive, context-aware verification—all without modifying your existing RADIUS server.
Benefits of Active Directory RADIUS authentication
- Enhanced endpoint security: Adds a strong second layer of authentication beyond AD credentials to local and remote network endpoints.
- Centralized control: Authentication requests are validated via the RADIUS server, keeping security policies consistent and not requiring complex configurations.
- Credential exposure protection: Even if passwords are compromised, unauthorized access is prevented by the
- Regulatory compliance: RADIUS MFA helps organizations meet requirements of regulations such as GDPR, HIPAA, PCI DSS, SOX, and NIST by enforcing MFA for sensitive systems.
Highlights of ADSelfService Plus
Adaptive MFA
Enable context-based MFA with 19 different authentication factors for endpoint and application logins.
Enterprise single sign-on
Allow users to access all enterprise applications with a single, secure authentication flow.
Remote work enablement
Enhance remote work with cached credential updates, secure logins, and mobile password management.
Powerful integrations
Establish an efficient and secure IT environment through integration with SIEM, ITSM, and IAM tools.
Enterprise self-service
Delegate profile updates and group subscriptions to end users and monitor these self-service actions with approval workflows.
Zero Trust
Create a Zero Trust environment with advanced identity verification techniques and render your networks impenetrable to threats.










