IT asset management example: An educational institution
What's inside the video
- 4 real life scenarios
- How to turn every service request into an experience to boost your ITSM maturity
- Case study: New hire request - to fill 8000 open positions
- For employee onboarding to function smoothly, how it should work
- KPIs that matter
- Take your major incident management (MIM) process up to notch
- Case study: Major availability incident hits a web performance company
- Their incident team debugging the situation
- Major availability incident management framework
- Major availability incident management framework with ServiceDesk Plus
- A structured approach to effectively roll out a major change
- Case study: How do you roll out a change effectively and help your company embrace change?
- The SMB embraces change with ServiceDesk Plus
- Is the change process effective?
- Use case: Build a rock solid ITAM strategy and grow your organization's ITAM maturity
- An educational institution has to upgrade from Windows 8 to the latest version
- Major challenges
- How to easily solve these challenges
- Track metrics that matter
Chapter-1
Chapter-2
Chapter-3
Chapter-4

Download your free copy of the presentation
Video transcription
Use case: Build a rock solid ITAM strategy and grow your organization's ITAM maturity

Now, let's proceed to our final scenario for today, which is how to build a rock-solid IT asset management strategy to control your IT infrastructure. So organizations such as educational institutions typically manage hundreds of assets. So, for example, an educational institution would have to manage the students' workstations, the workstations of management, sometimes faculty, etc. And they also need to monitor each of these assets, ensure that all the operating systems are upgraded and take care of any security vulnerabilities. So we'll see how that is done in the context of an educational institution.
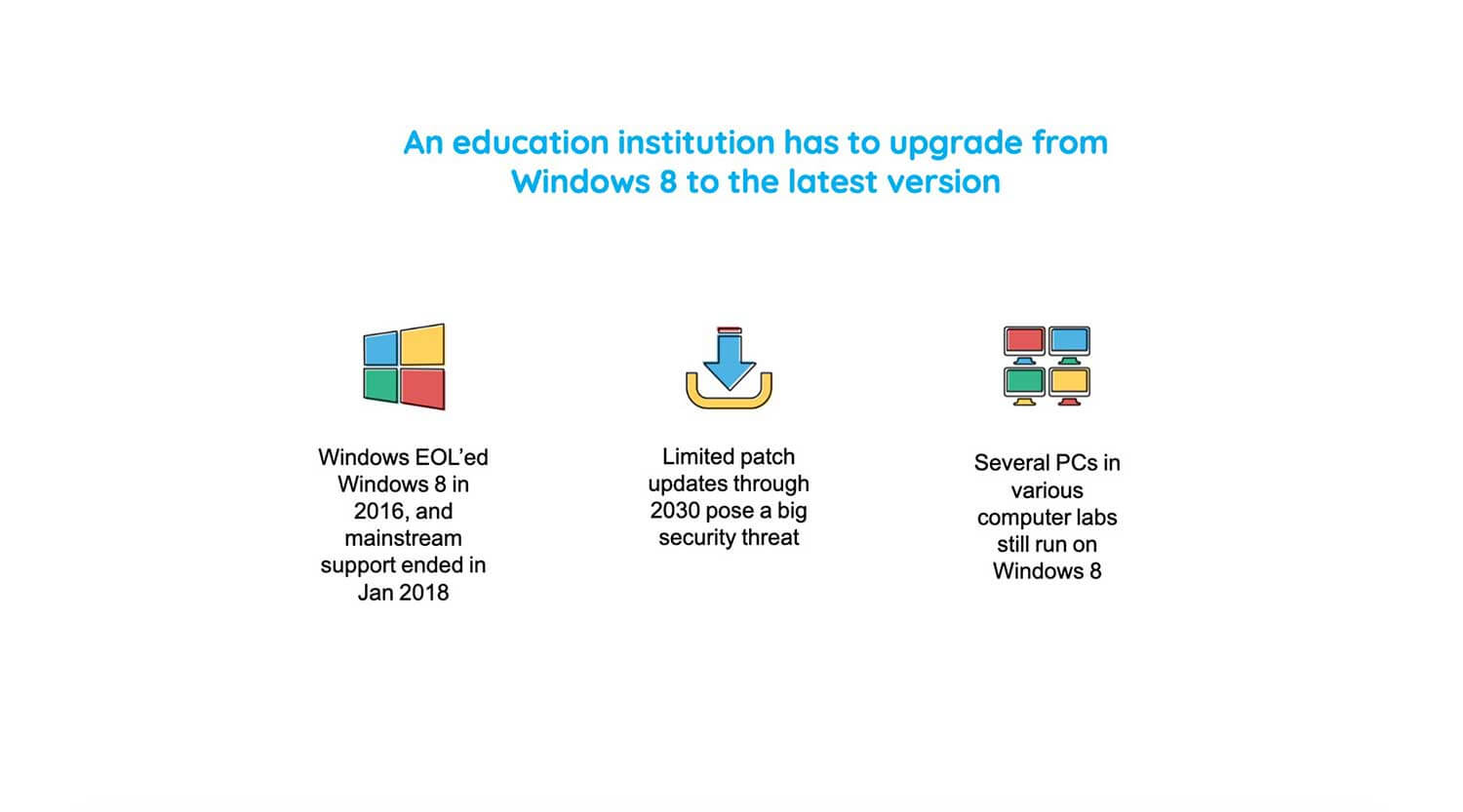
An educational institution has to upgrade from Windows 8 to the latest version

So, in this case, we have an educational institution which has to upgrade from Windows 8 to the latest operating system, and that is because, as we all know, Windows 8 was EOLed in 2016, and mainstream support has already ended in Jan 2018. While limited patch updates are available, this still poses a big security threat because you wouldn't really be receiving major security updates. So, that exposes this educational institution's assets for cyberattacks such as malware and ransomware. And the concern here is that several PCs in various labs still run on Windows 8. So they face some major challenges in responding to this situation.
Major challenges

So those were drilling down to those assets which were vulnerable, identifying the software, and rolling out the upgrades with minimal disruption.
So the third challenge was because some of these assets supported their critical IT services. So they had to ensure that the upgrade process did not cause any ripples throughout their organization. So, here is a simple five-step process to approach this scenario.
How to easily solve these challenges
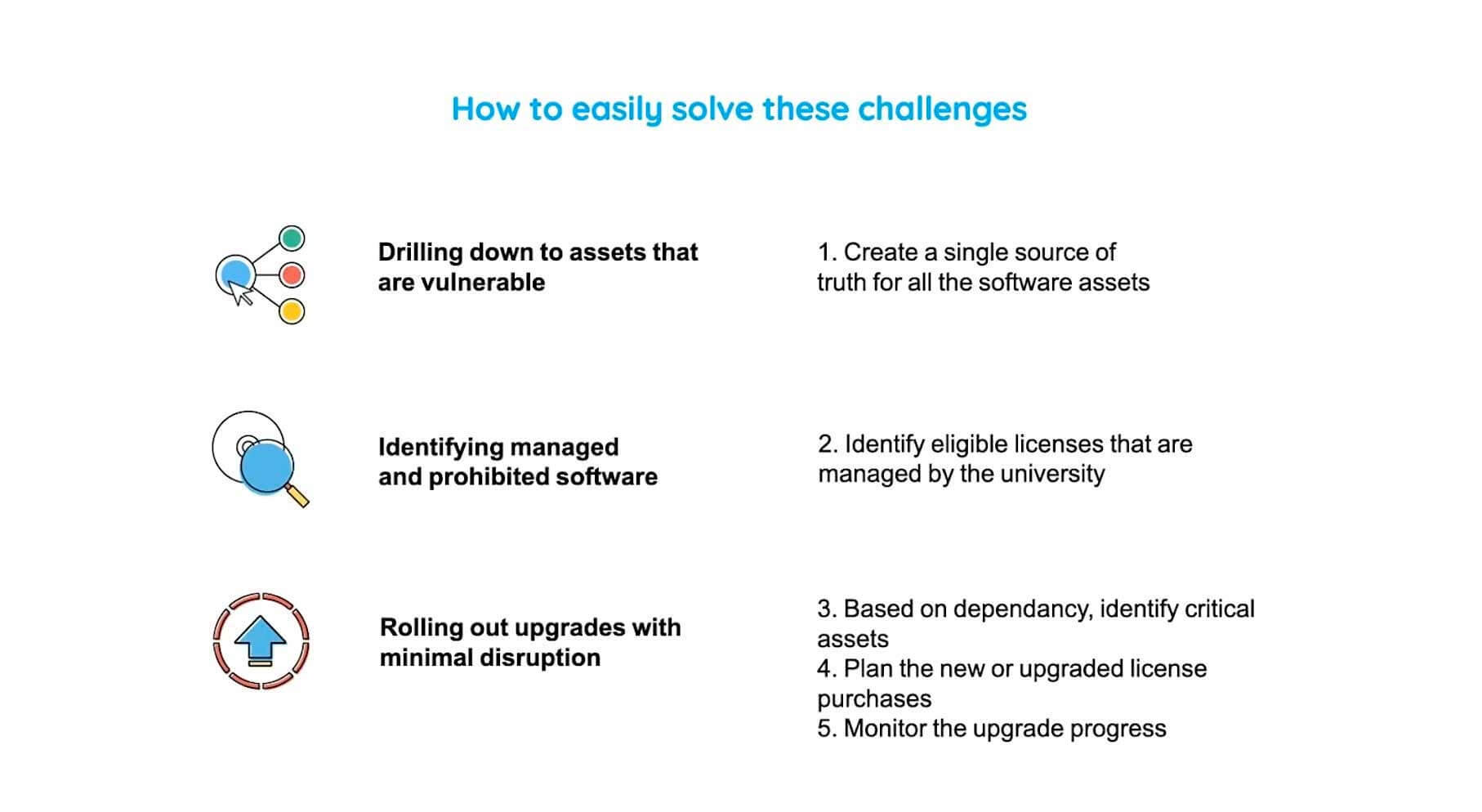
First, you create a single source of truth for all your software assets. Secondly, you identify just the eligible licenses managed by the university. Three, based on the dependencies, we identify the critical assets. And finally, we plan the new or upgraded license purchases and monitor the entire upgrade process.
So, here is the workflow again, and let's see how the asset management module and ServiceDesk Plus helps you to implement this workflow.
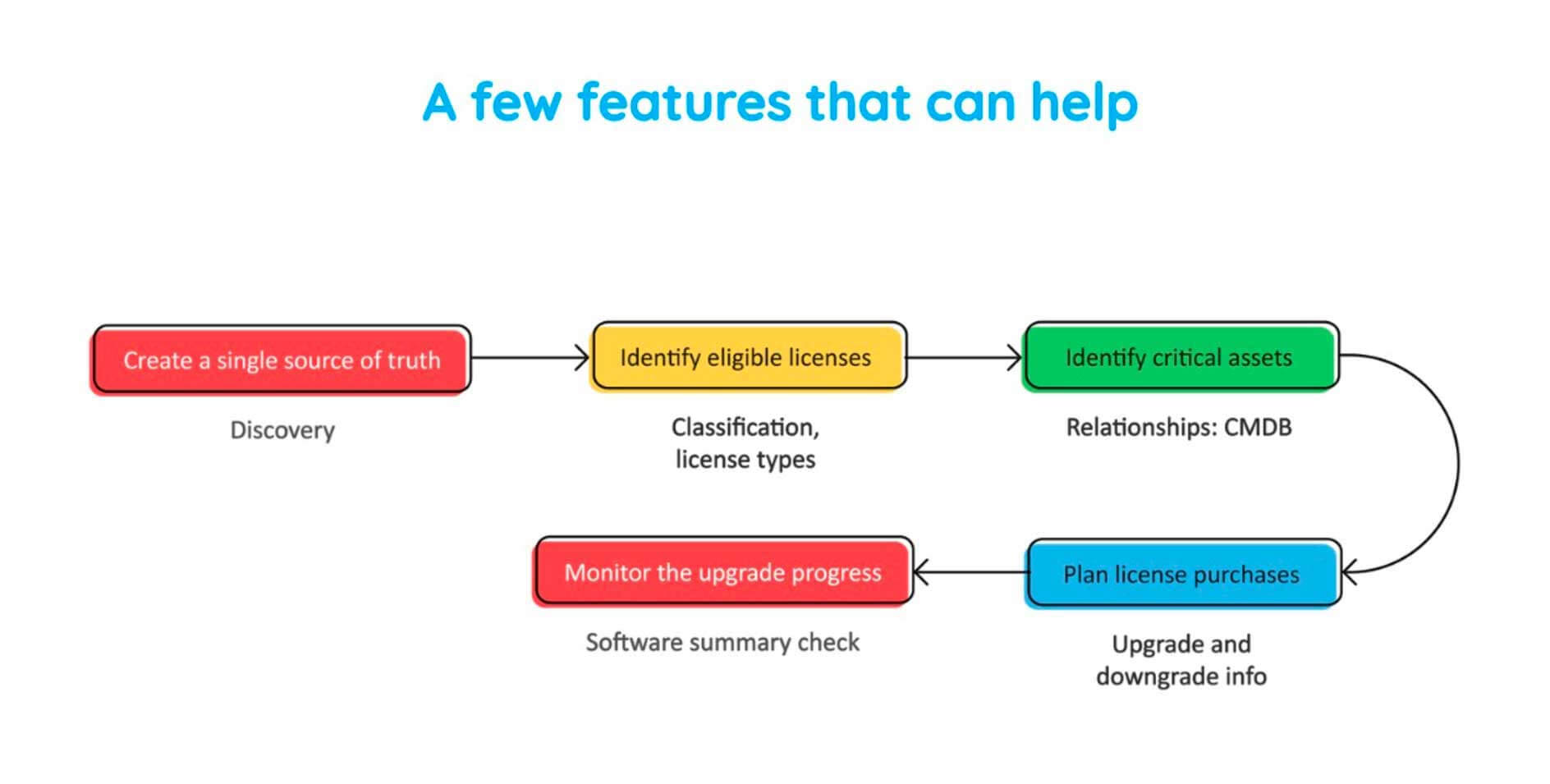
Let me click on admin module over here, and as you can see, right at the center of your screen, you have something known as Discovery. These various discovery techniques allow certain scanning methods, which help you to scan all assets which are part of your organization. So, the Windows agent configuration, provides the Windows agent, which helps you to fetch software and hardware inventory information from your Windows workstations and servers. The network scan allows you to discover networks which are part of your organization and scan assets which are part of such networks.
The distributed assets scan comes handy when you have assets distributed across different geographical locations, and sometimes organizations use Microsoft SCCM for their inventory management. So we have SCCM integration tool, which helps you to fetch all such asset data onto ServiceDesk Plus.
So, once you've leveraged all these discovery techniques, you would have created a single database of all your assets. Let me click on asset to show you one such database. So as you can see, this is the database of that educational institution we talked about. We have all the workstations which were detected and inventoried. We have all the asset classifications such as those assets in store, those which have been unassigned, those in use, those in repair, etc. So let me quickly show you how the asset details look like.
So let me click on the 0141 asset. So as you can see, the CI details are displayed, which provide an overview as to what this asset operates. The hardware information provides you detailed information regarding the processor, network adapters, hard disk, etc. Again, have your software information, which has all the software installed on this particular asset. And the relationships tab, as we saw before provides you all the dependencies which are fetched from your CMDB.
The history tab provides you a history of the workstation scan history and the asset ownership history request. So sometimes you might have assets which are the cause of incidents, or you might have requests which are associated to assets. So you can associate all of them in this tab. So you can even associate problems and change details. And in case you're creating specific contracts related to assets, you could really go ahead and add them over here.
And finally, we'll come to the financials tab. The financials tab helps you to view the cost information associated with assets. So that is really important because IT departments typically spend a lot in maintaining assets. So we could configure depreciation methods and measure the current book value, the remaining useful life so that it would be really handy when you're planning for future purchases or leases. So now we've created all of our assets into a single database. Let's go back to our best practice workflow again.

So, we created a single source of truth using the various discovery techniques. Now, all that is left is to identify the eligible licenses associated and among those, the critical assets, and finally roll out the OS upgrade. So, let me click on software over here and more specifically the software summary. So, once you've scanned all your assets, all the associated software licenses would automatically be fetched onto your database. So as you can see, you have the compliance tab over here, which provides you the picture on how compliant you are with your software licenses. And over here, you have different classifications of software such as managed software, prohibited software, freeware, etc.
So since Windows 8 is a software which is being managed by this organization, let me click on managed software. So right at the top, we have Windows 8 Professional Edition. So this has been EOLed, so we are concerned with identifying those assets which are vulnerable. So as you can see right now on your screen, this educational institution has purchased 14 Windows 8 licenses of which 4 have been installed on specific assets. Let me click on that. As you can see, we have identified those four assets, which are right now running on Windows 8. So since we have created a single database of our assets, the process of drilling down and identifying assets which were vulnerable was made real easy.
Now, the next step is to identify the critical assets. So let me click on the third server over here, and the relationships drawn from the CMDB would help us to identify the criticality of this asset. So, let me go onto the Relationships tab, and as you can see, the email services are being hosted on this particular asset, which means in case of a cyber-attack or in case of any security vulnerability, this educational institution's email services would have to take the hit, and we wouldn't really want that. So we need to roll out an OS upgrade to this asset as soon as possible.
So let me go back to software being run on this asset. We'll scroll down to Windows 8 Professional Edition, and let me go ahead and select this particular asset. And if I click on actions, there, I have the Add Software License option. So we could go over here and upgrade the license by providing the purchased license and the license key associated with this.
So this helps you to update your database and monitor the upgrade process to its entirety. So, first, it seemed like a very daunting task, right? We had hundreds of assets, and we needed to identify just four among them. But since we had created a single database and had the right capabilities, we were able to do it in just a few seconds. I hope that would have really helped you if you're managing hundreds of assets and if yours is a very large enterprise.
Track metrics that matter
Now, as usual, we'll have to look at some of the metrics that matter and that which you need to track.
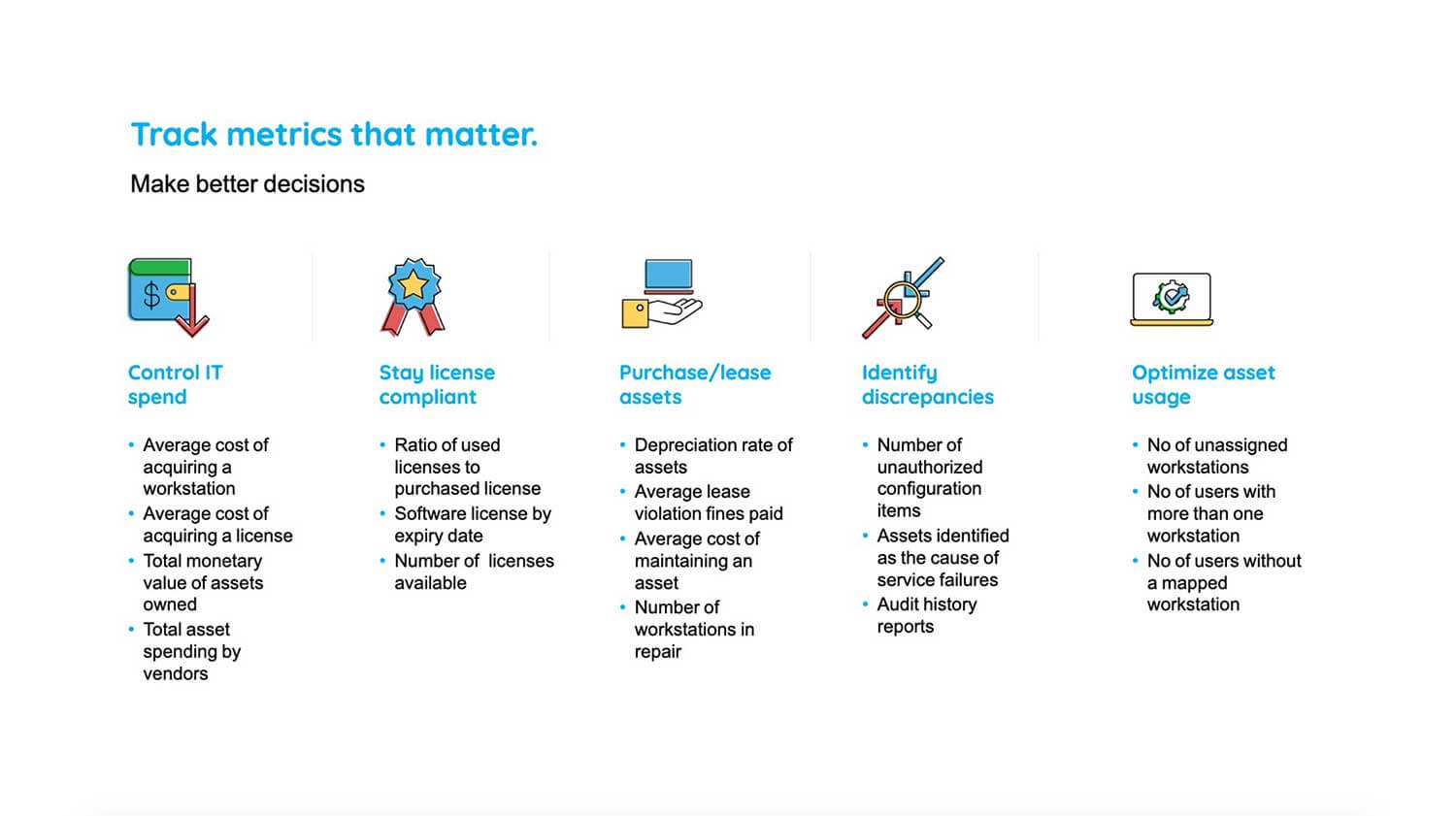
So you need to control your IT spend, and for that, you need to measure the average cost of acquiring a workstation. Your organization should also stay license compliant. So you should measure the ratio of used licenses to purchase licenses. And again, you need to plan your future purchases, identify discrepancies with respect to assets, and optimize your asset usage. So these are the metrics specific to such categories which would have really helped you to manager your assets real easy. So, let me just leave this screen on for a few seconds for you to take note of that.
And we've also arrived at the end of our webinar. So let me quickly summarize what we saw today. So we discussed four different IT situations. We discussed each of them in detail, we saw the associated challenges or roadblocks in some cases, and we saw how a best practice workflow comes in handy in responding to such situations. And finally, and most importantly, we saw what are the right capabilities that an ITSM tool should have for implementing these best practices in real life. So I hope now that you would have some kind of clarity on how we can go about translating these best practices into your ITSM approach.
Thank you

So, that brings this webinar to a closure, and if you have any questions related to what we discussed today, please go ahead and ask. So in case you're wondering that you need to go back to certain things that we discussed, don't worry, we will be sending you a recording of this webinar via email along with the FAQs. And in case you have any further queries, you could also send an email to hello@servicedeskplus.com or to this email ID over here, which is displayed on your screen right now. So that is my email ID, and you could go ahead and ask any questions which you feel will help your organization.
So, guys, thank you for joining this webinar today and have a nice day. Thank you. Once again, if you have any further queries, you could send an email to the email ID displayed on your screen. Have a nice day. Thank you.