

The compliance feature helps with adherence to specific baseline configurations for endpoints to improve security and meet regulatory requirements. Each compliance policy is a collection of rules, based on globally-accepted standards and best practice guidelines for security configurations, which can be used to audit your endpoints and software running in them to understand and improve their security posture. The first line of defense against cyber attacks is to ensure foundational security configurations are implemented and maintained in your endpoints. Endpoint Central compliance module helps you to that end by regularly auditing your systems' configurations compliance against known standards like CIS benchmarks and providing detailed steps to help comply with them.
Applies to:
The Center for Internet Security (CIS) develops benchmarks for a variety of applications, operating systems, servers, and databases through a unique consensus-based process involving a community of cybersecurity professionals and subject matter experts from around the world. CIS benchmarks contain standards and best practices for fine-tuning security configurations of a target system. CIS Benchmarks are used by organizations, across the globe and sectors, in meeting security and compliance objectives. Besides, configuration recommendations detailed in PCI DSS (Payment Card Industry Data Security Standard), HIPPA (Health Insurance Portability Accountability Act), FISMA(Federal Information Security Management Act), and other regulatory frameworks aligns with, and point to CIS benchmarks as the definitive standard.
Endpoint Central out-of-box CIS policies are direct derivatives of latest CIS benchmarks and are officially certified by CIS to be used in audits. The certifications are earned by submitting test cases for all the rules (recommendations for configurations) within each benchmark for validation by CIS personnel. With Endpoint Central CIS compliance feature, endpoint security configurations can be assessed for compliance with the rules in CIS policies and remediation actions are recommended for each violation. Each rule in the policy is assigned a profile. The profile indicates the security level of the recommended configuration.
View the complete list of CIS benchmarks officially supported by Endpoint Central.
You can find the CIS policies in the console by navigating to Compliance → Policy Groups and clicking on Create Group button. After selecting the platform, you will be redirected a new window where, you can see a list of policies. Selecting a policy reveals a detailed breakdown of the constituent rules for that policy. The following image offers a look at how CIS benchmark policy is structured.
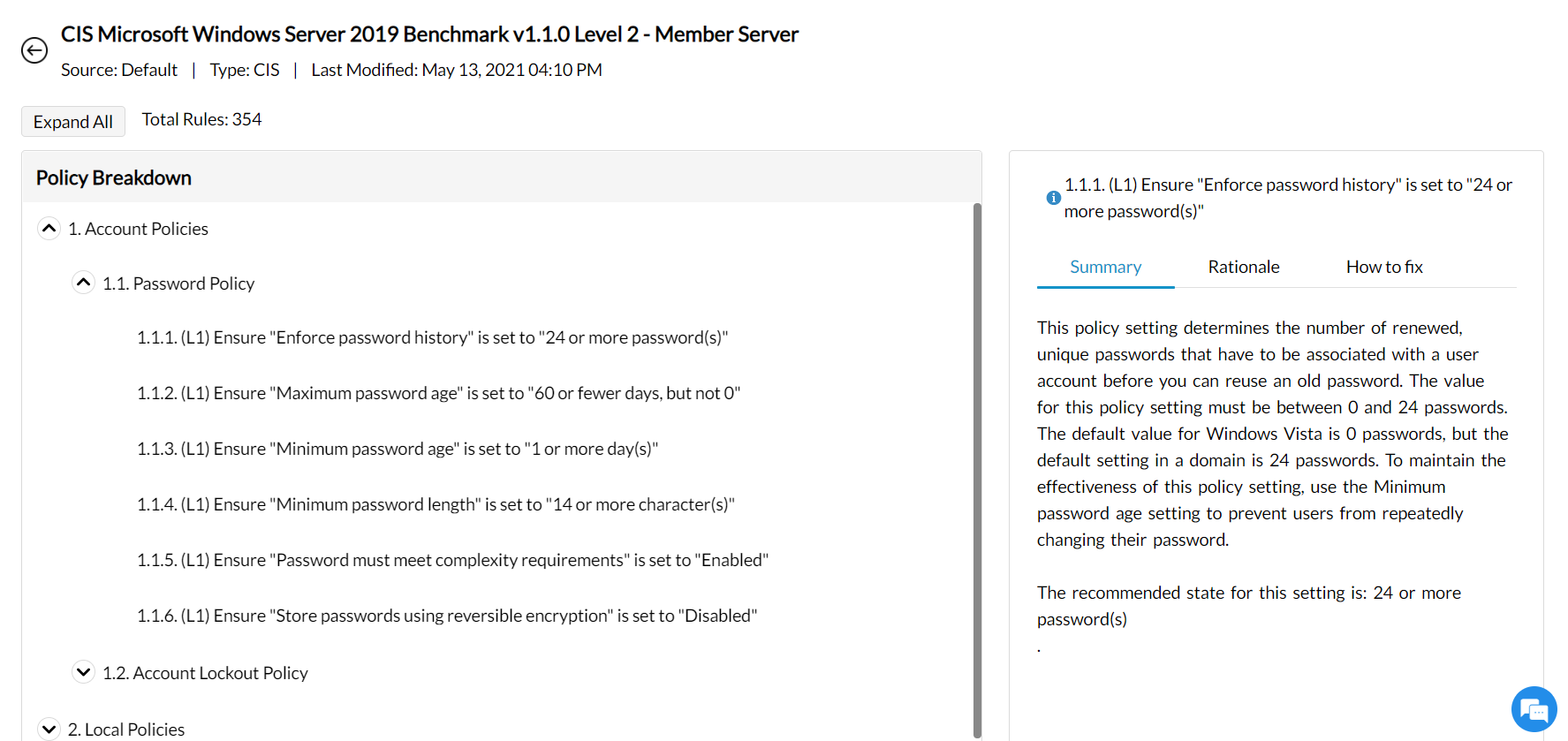
Note: By clicking on Compliance → Policy Group and then clicking on Built-in Templates, you can see the pre-created policy templates by ManageEngine; you can also use that for compliance scanning purposes.
The rules within each CIS policy are grouped based on the component it pertains to, such as password policies, account lockout policies, etc. Click on the component title to expand and view the rules. Each rule suggests a recommended value for a security configuration. During the audit scan, your systems' security configurations will be assessed for compliance with these rules. Clicking on the rule reveals:
After selecting the required CIS compliance policies, click on Create Group to finish creating policy group. You can use this policy group for CIS compliance audit purposes.
Note: New compliance policies or changes related to existing compliance policies from the central vulnerability database synchronize regularly with the central server at 1 am everyday. This compliance data sync will not happen during the usual vulnerability database sync. Refer to this article for troubleshooting in case the compliance data sync fails.
Note: The feature isn't available in all countries. Reach out to support for further details.
If you have any further questions, please refer to our Frequently Asked Questions section for more information.