Privilege escalation: What you need to know and how to defend your network
This article helps you to understand more about privilege escalation attacks, how they differ from other exploits, and how to mitigate and take a stand against these threats. Let us first examine what a privilege escalation attack is.

A privilege escalation attack is when a standard user gains access to a different user's account by impersonating that user. Privilege escalations also occur when a user tricks systems into granting permissions which are higher than what the application developers or IT admins intended to provide to a normal user account. In either case, escalations are carried out with malicious intent.
There are essentially two ways that privileges can be escalated: horizontal escalation and vertical escalation. Horizontal escalation occurs when a user gains access to another account within the same range of permissions or privileges. Vertical escalation occurs when the perpetrator uses a normal user account to gain elevated permissions equal to what an administrator would have.
Let's first look at the risks presented by these threats to larger networks in a corporate environment. Then, we'll walk you through how you can safeguard your own network from such exploits.
What are the risks presented to an enterprise?
- Damaged reputation from leakage of users' private data
- Theft of sensitive files and/or extortion
- Modified system settings or the creation of new users
- Intrusion of malware to perform malicious tasks such as keystroke logging
The following images show where one might find the user account control and application permission settings
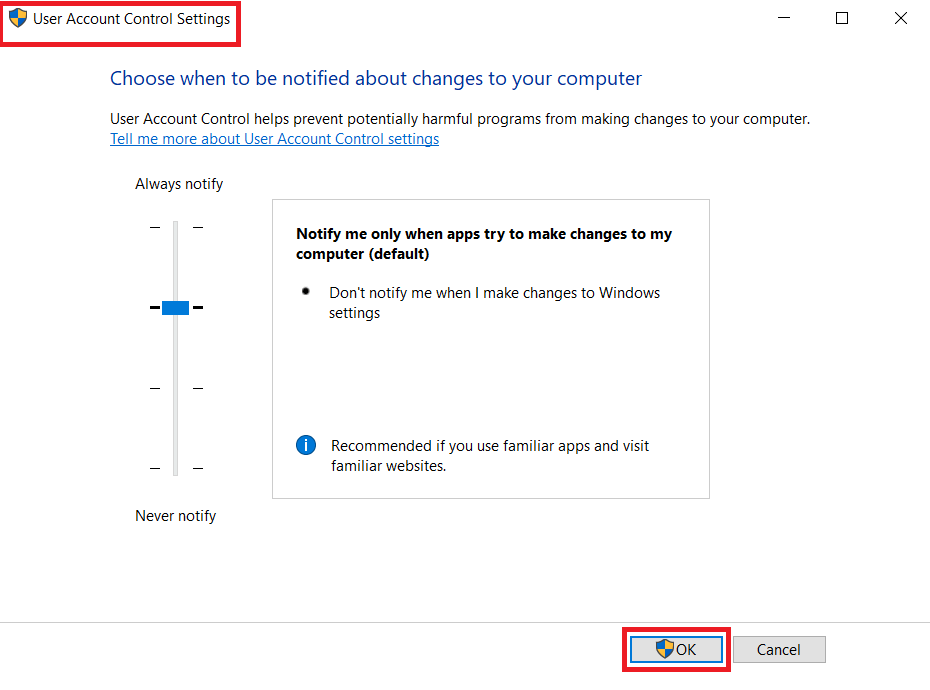
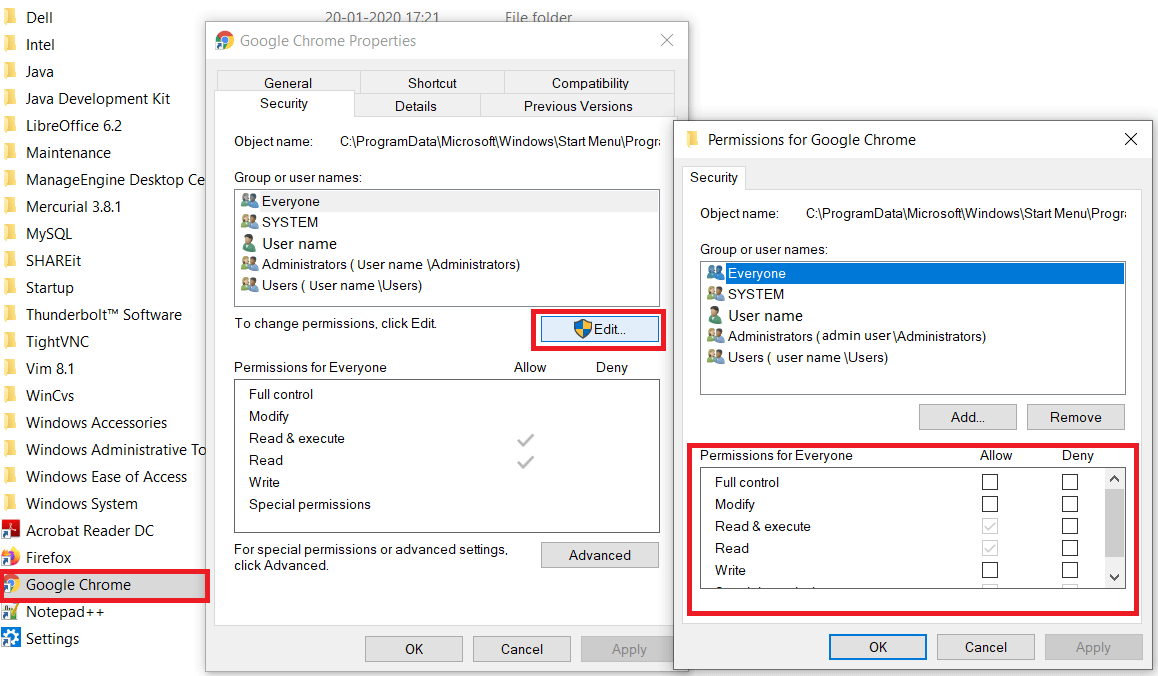
How are privilege escalations carried out?
Privilege escalation in the context of a web-server
Let’s take a look at a privilege escalation attack in the context of a web server. A privilege escalation attack can be carried out when a website makes access control decisions based on untrustworthy input returned by the browser. The attacker may tamper with the contents of an HTTP cookie when the session identifier is exchanged between the web server and browser whenever a user logs into the website. Web servers need to understand which system they are currently communicating with on each subsequent HTTP request.
Session identifiers keep vital information such as the session ID, user ID, and user roles. An attacker may easily manipulate or steal this data to impersonate another user by loading the cookie on their browser, thereby tricking the web server into granting them the privileges and permissions of that user.
Cross-site Scripting (XSS)
Another sophisticated method used for privilege escalation is called cross-site scripting, or XSS. Using XSS, attackers introduce malicious code within a website’s content and simply wait for users to click on the piece of content that contains the script. Once this is done, the script runs and collects all information regarding the session and cookies, which it then sends to the hacker's web server instead of to the normal web server that hosts the site. All this happens while the user is completely unaware of what is going on in the back end.
Web servers are key internet-facing components, and since they are prone to web-based attacks, it is imperative to keep them secure and configured accurately. Making HTTP cookies tamper-proof with digital certificates, and placing critical information related to cookies on the server side, are viable measures to prevent such exploits.
The above situations are classic examples of horizontal privilege escalations. Vertical privilege escalation attacks are more alarming to an organization because of the potential to affect other computers and access shares across the network.
Most privilege escalation attacks are based on leveraging inadequate security configurations and software vulnerabilities present in the network. Ensuring that your antivirus software is up-to-date, and updating or patching software applications as soon as they are released by vendors, can go a long way in preventing attacks of such nature.
Here are some common methods used by attackers
Buffer overflows
Buffers are memory spaces allocated for programs to run and store temporary data within the random-access memory (RAM) of a computer. A buffer overflow , also known as a buffer overrun, occurs when a program writes data outside of the allocated buffer into other areas of program memory which are not designated to store this data. This vulnerability paves the way for attackers to introduce malicious code that elevates their privileges.
For example: Certain applications or programs are not meant to be used by standard users in an organization, and are controlled by a more privileged user, such as an administrator or technician. Applications that track systems on the network and monitor employee usage fall under this category. A standard user may use a buffer overflow to inject scripts that deter an application or program from functioning correctly to gain elevated permissions and intrude into other systems on the network.
Buffer overruns are often overlooked by software developers, and it is essential to install application updates when they are released to ensure maximum security for your enterprise.
Security misconfigurations
Installing applications with elevated permissions by default increases your client systems’ attack surface, making it easy for attackers to navigate to other systems on the network. I recommended to install applications with the least privileges or permissions possible, and require users to send a request to the system administrator when they need to make changes to their computer.
A malicious user can use system services that run in the background and can elevate their privileges. To do this, a user can manipulate authentication mechanisms by altering the function of error handlers. In such scenarios, the user may also introduce a malicious error handler that could grant them access to the system's key resources.
How to thwart a privilege escalation attack?
There are multiple ways to prevent a privilege escalation attack, but for now let’s consider the most crucial ones.
Data Execution Prevention
Data Execution Prevention (DEP) is a hardware feature embedded in Windows systems to enhance security. To understand how this works, consider the RAM of a computer, where program memory is stored while the application is running. In reality, there are two types of memory stored in the RAM. One is the actual executable code, and the other is data that represents the state of a program.
When DEP is enabled, if a specific piece of data is run as executable code, Windows blocks the request and the program crashes. Since code written to the data section of the RAM can easily be malicious, DEP should be enabled for computers in a network. In our case, this code may contain instructions to elevate the privileges of a standard or normal user.
Address space layout randomization
Address space layout randomization (ASLR) is a security technique that makes it harder for attackers to utilize buffer overruns and other software vulnerabilities to execute code with privileged instructions at known addresses within the memory.
ASLR randomizes components of program memory such as stack, heap, and library, which makes it difficult to find important locations or addresses in the memory (e.g. the function address). ASLR is a feature of the operating system, and renders stack memory non-executable.
Restricting the use of kernel mode
From a system's perspective, there are four types of users: standard user, administrator, root, and kernel user. While carrying out privilege escalation attacks, the cybercriminal gains administrative privileges to pose as a normal user, and strives to become a root or even a kernel-level user.
Once the kernel level is attained, the attacker can execute any piece of code that directly impacts the operating system of the computer, and can perform malicious acts. Using a digital signing certificate to access root and kernel modes will help fix this issue.
Software vulnerabilities
Patching software is a simple, yet effective approach to prevent privilege escalations, as it improves the security of applications and minimizes the opportunities for attackers to navigate from one system to another, reducing an enterprise’s overall attack surface. Also important while managing a network, but easily overlooked, is patching third-party applications.
Services are components that perform functions in the back end, and are repetitive or run for long periods of time. These include checking for new data, processing data, etc. Applications sometimes use a service that has elevated permissions for the individual system. For this reason, applications that use background services for their complete functioning must be closely monitored.
How can Vulnerability Manager Plus help?
All the preventive measures stated above are relatively easy to establish and effective in preventing exploits on individual computers. However, when managing a large group of systems on a network, such as an office network, implementing these measures becomes very tedious and time-consuming.
Vulnerability Manager Plus is an endpoint security product from ManageEngine that bridges this gap by managing systems within a corporate environment with ample scalability. Vulnerability Manager Plus helps system administrators detect misconfigurations and software vulnerabilities present in systems across the network, and displays them in a centralized, browser-based console.
Let's look at some interesting features of Vulnerability Manager Plus.
- Identify account privilege management settings from a dedicated misconfigurations tab, and deploy the right settings to your network endpoints.
- Detect software vulnerabilities based on buffer overflows, privilege elevations, XSS, and remote code execution. Deploy patches, or carry out manual resolution if a patch is not available.
- Track web server misconfigurations, antivirus updates, and much more.
Download Vulnerability Manager Plus today to tighten the security of your managed systems.