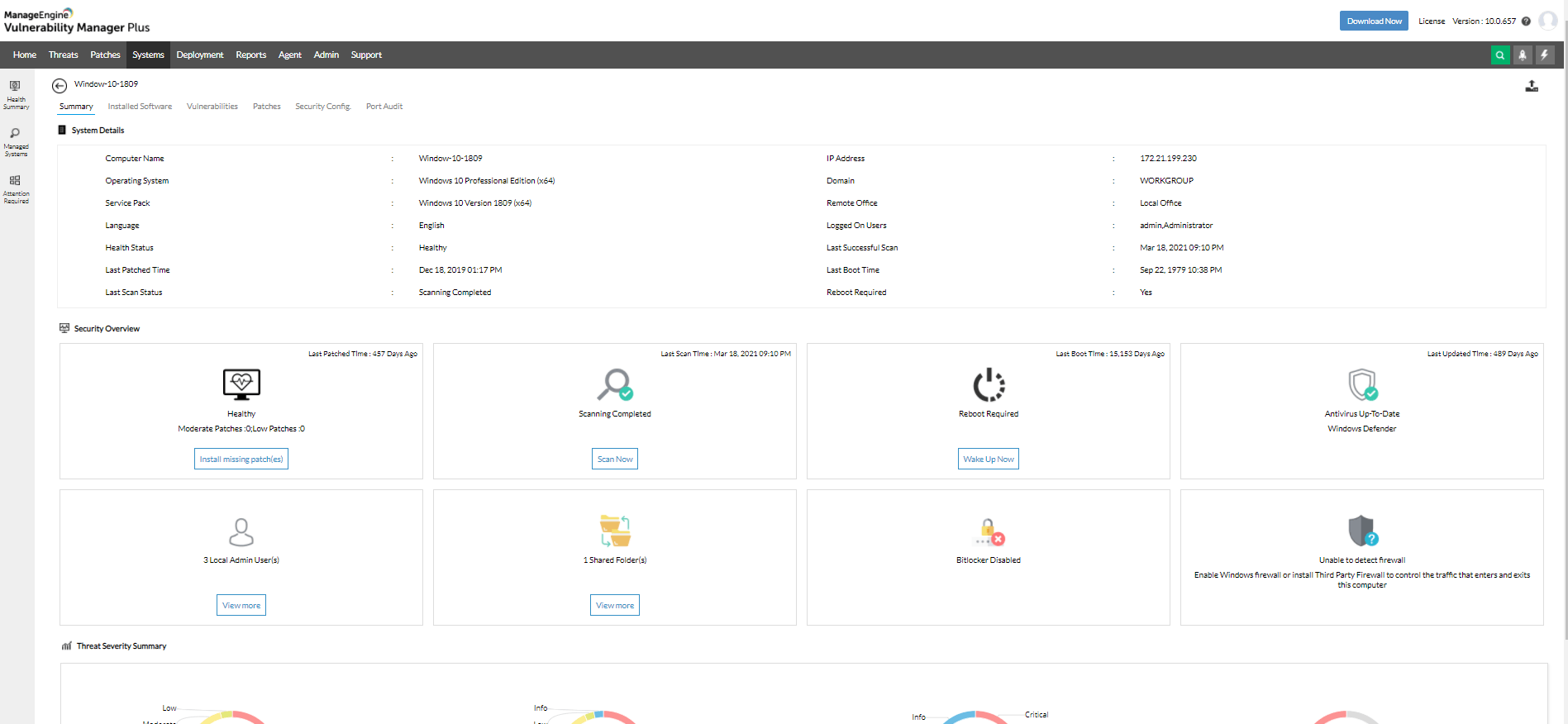
What is a vulnerability scanner?
A vulnerability scanner is an advanced, automated tool designed to scan the endpoints in a network to detect software vulnerabilities, unauthorized open ports, misconfigurations, compliance issues, and other security loopholes. This tool is essential in identifying potential security threats and ensuring robust protection of the enterprise IT infrastructure.
A modern vulnerability scanner offers the following capabilities:
- Continuous and automated scanning, thereby allowing real-time monitoring of IT environments and reducing the attack surface without manual intervention.
- Comprehensive detection and identification of CVEs, misconfigurations, missing patches, and security anomalies, providing a holistic security assessment.
- Unified console with seamless integration across patch management, service desk, SIEM, and other IT solutions to ensure swift remediation of identified vulnerabilities.
- Compliance reporting and audits to maintain compliance with various regulatory standards by providing detailed audit trails and compliance reports.
What are the three types of vulnerability scanners?
Based on their functionalities and architecture, vulnerability scanners can be classified into three different types:
- Application-based Vulnerability Scanners: These vulnerability scanning tools scan the applications installed in the network's endpoints for common vulnerabilities and flaws, database security, configurations, and other security protocols.
- Network-based Vulnerability Scanners: Such tools scan the endpoints (servers, laptops, routers, etc.) in the network to detect misconfigurations, vulnerable systems, unpatched software, and so on.
- Cloud-based Vulnerability Scanners: Cloud vulnerability scanning tools scan and detect vulnerabilities in cloud-hosted applications, service providers, servers, and cloud deployments.
For organizations looking to try out a vulnerability scanner to proactively identify and remediate security weaknesses, ManageEngine Vulnerability Manager Plus, with its free edition can be the ideal solution, pre-implementation.
This free vulnerability scanning tool offers an advanced set of capabilities free of charge for up to 25 devices with a single technician to manage the endpoints.
Below we cover:
- Limitations of traditional vulnerability scanners
- Capabilities of ManageEngine's vulnerability scanner
- How does a vulnerability scanner work?
- Frequently asked questions about vulnerability scanners
What are the limitations of traditional vulnerability scanners?
Traditional vulnerability scanners that can only detect vulnerabilities without offering any mitigation often fail to provide holistic security for the network. Here are the limitations of traditional vulnerability assessment tools:
- Failure to provide continual visibility since they provide only a point-in-time snapshot of the network assets. Moreover, systems and network configurations change all the time. With new devices and software instances being constantly added to the network every now and then, the network is left open to vulnerabilities and other risk avenues.
- These tools have a constricted scope of functionalities and require integration with other siloed tools to offer overall network security. This results in increased network load, bandwidth consumption and a higher vulnerability response time.
- The lack of a consolidated dashboard makes it harder to gain insights into the vulnerability and mitigation status of the network and understand the outstanding risks.
All-in-one platform for vulnerability scanning and more!
Scanning for vulnerabilities, system misconfigurations and other security loopholes in the network isn't enough, if those aren't mitigated promptly. This is where Vulnerability Manager Plus stands out. By leveraging the agents installed in the systems, this solution combines vulnerability scanning, patch deployment, security configuration management, and other mitigation strategies together into a single console. This shortens the time taken to detect and remediate vulnerabilities and misconfigurations.
With Vulnerability Manager Plus, you only need one tool and one agent to manage all your system vulnerabilities. This means it's easy to use in changing environments and you don't have to waste time scanning multiple times for the same issues. The tool automatically gathers all the important information and helps you quickly fix any problems.
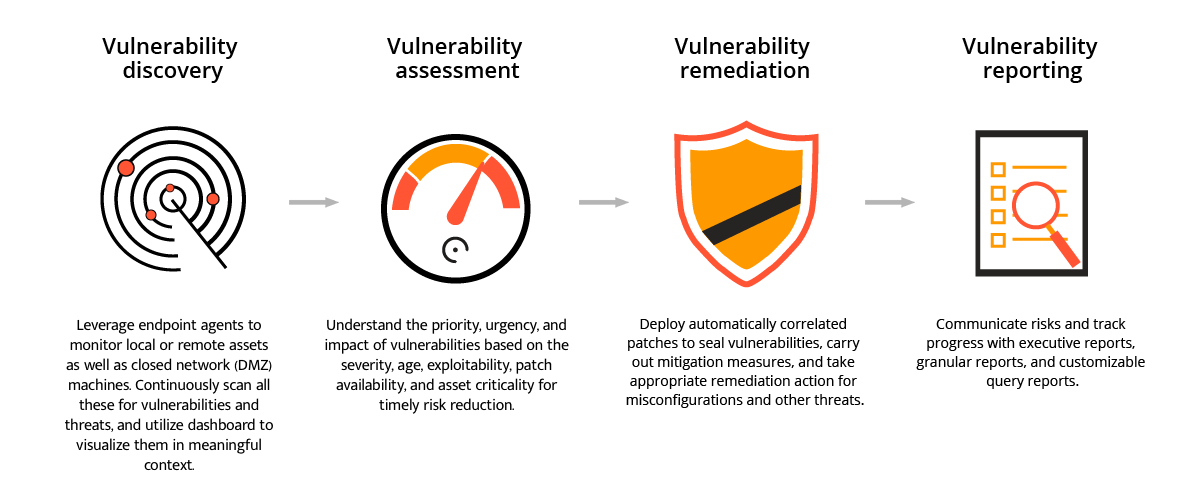
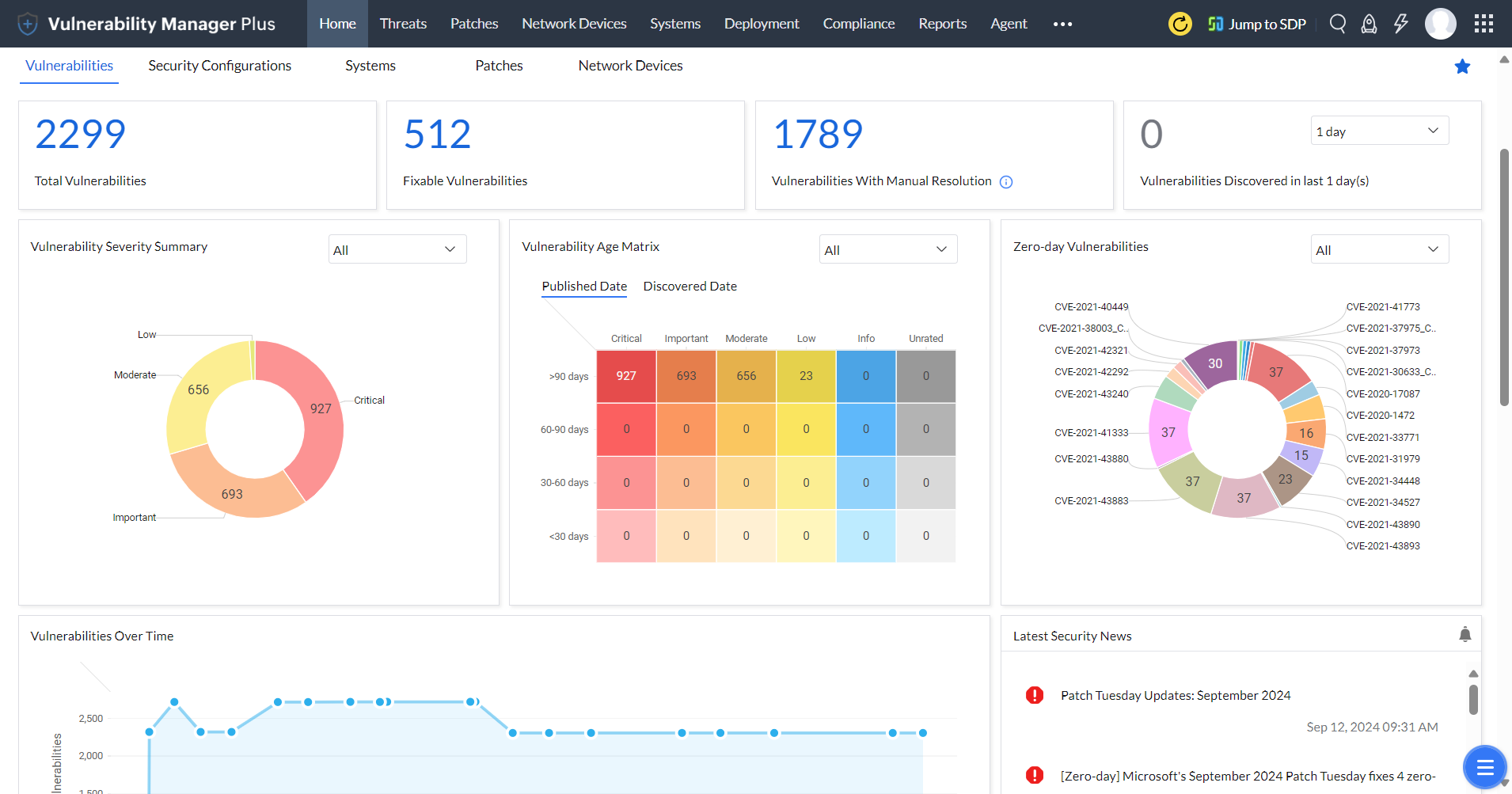
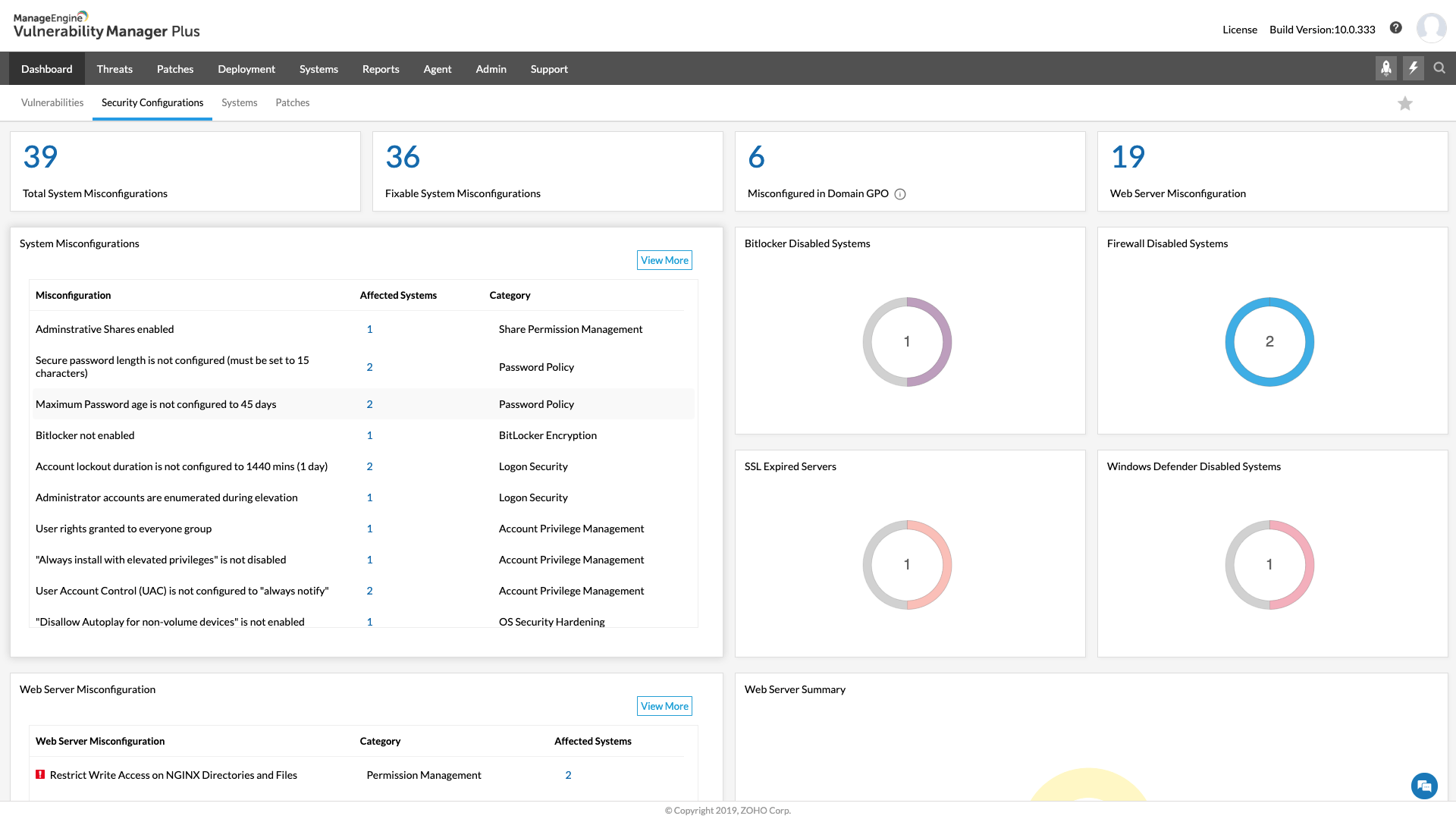
Comprehensive vulnerability scanning
Eliminating blind spots is the basis of successful vulnerability management. To achieve this, Vulnerability Manager Plus:
- Detects known or emerging vulnerabilities across all your network endpoints, including workstations, laptops, servers, web servers, databases, virtual machines, and content management systems.
- Offers continuous visibility into your endpoints, whether they are located at the local office, in a demilitarized zone, at a remote location, or always on the move.
- Extends your visibility beyond just vulnerabilities and identifies misconfigurations, high-risk software, active ports, and much more.
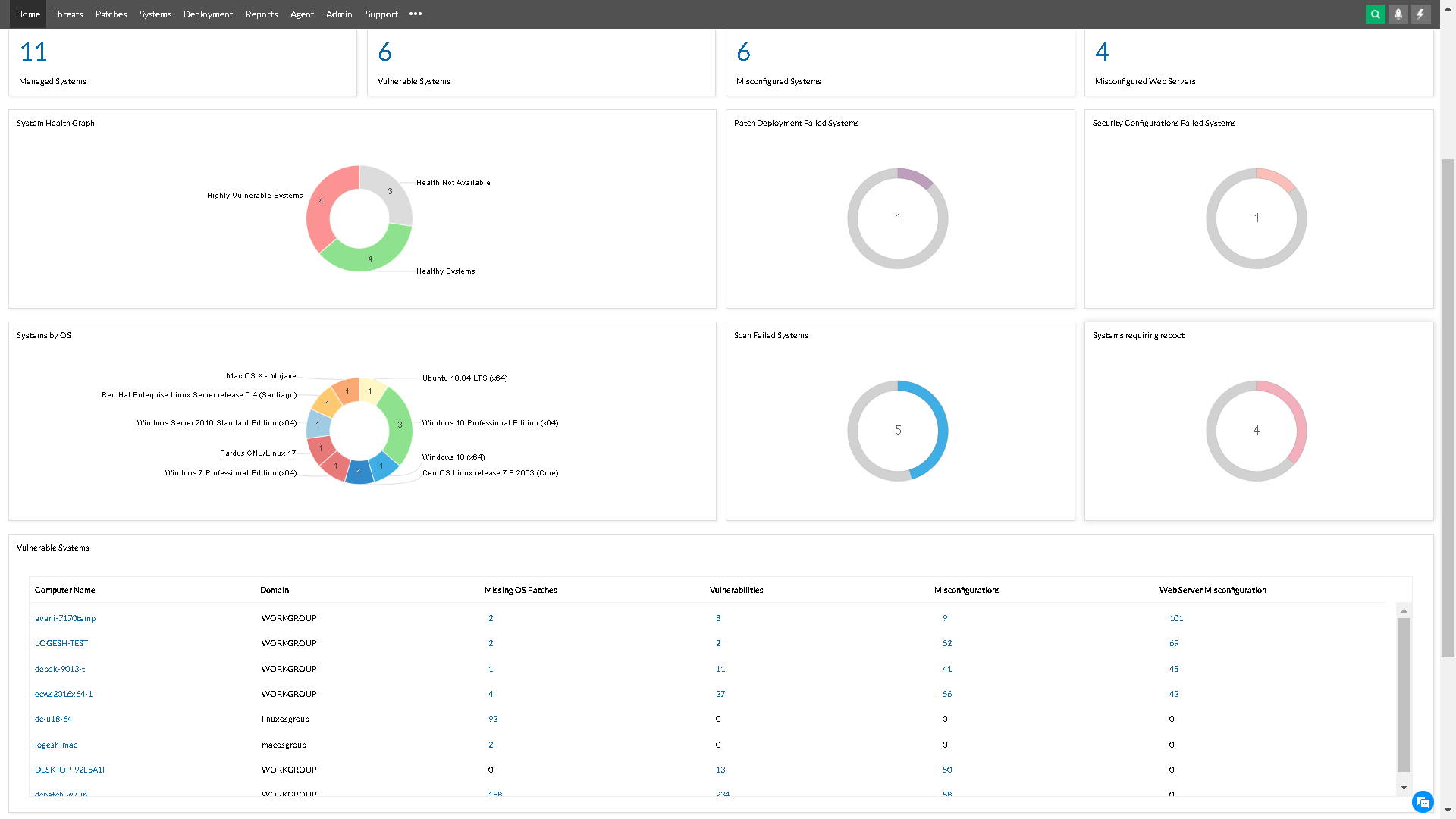
Intuitive dashboards with rich contextual information
Are you overwhelmed with a flood of security scan data? With Vulnerability Manager Plus, you can easily see how secure your organization is overall, and which areas need the most attention. It's all presented in easy-to-understand dashboards, so you don't have to be a security expert to make sense of it.
Risk-based vulnerability assessment
Visualize, analyze, and prioritize your response to exploitable and impactful vulnerabilities based on:
- CVSS scores and severity ratings.
- The availability of exploits.
- A security news feed that's continually updated with articles on vulnerabilities that attackers are discussing, experimenting with, or using, and current exploits circulating in the wild.
- Vulnerability age.
- Affected asset count.
- A drilled-down view of assets that displays whether web servers, databases, or content management systems are installed on them, along with vulnerabilities on those installations.
- CVE impact type.
- Patch availability.
- A dedicated view to swiftly pinpoint zero-day or publicly disclosed vulnerabilities.
Learn more about the importance and benefits of risk-based vulnerability management over traditional vulnerability management.
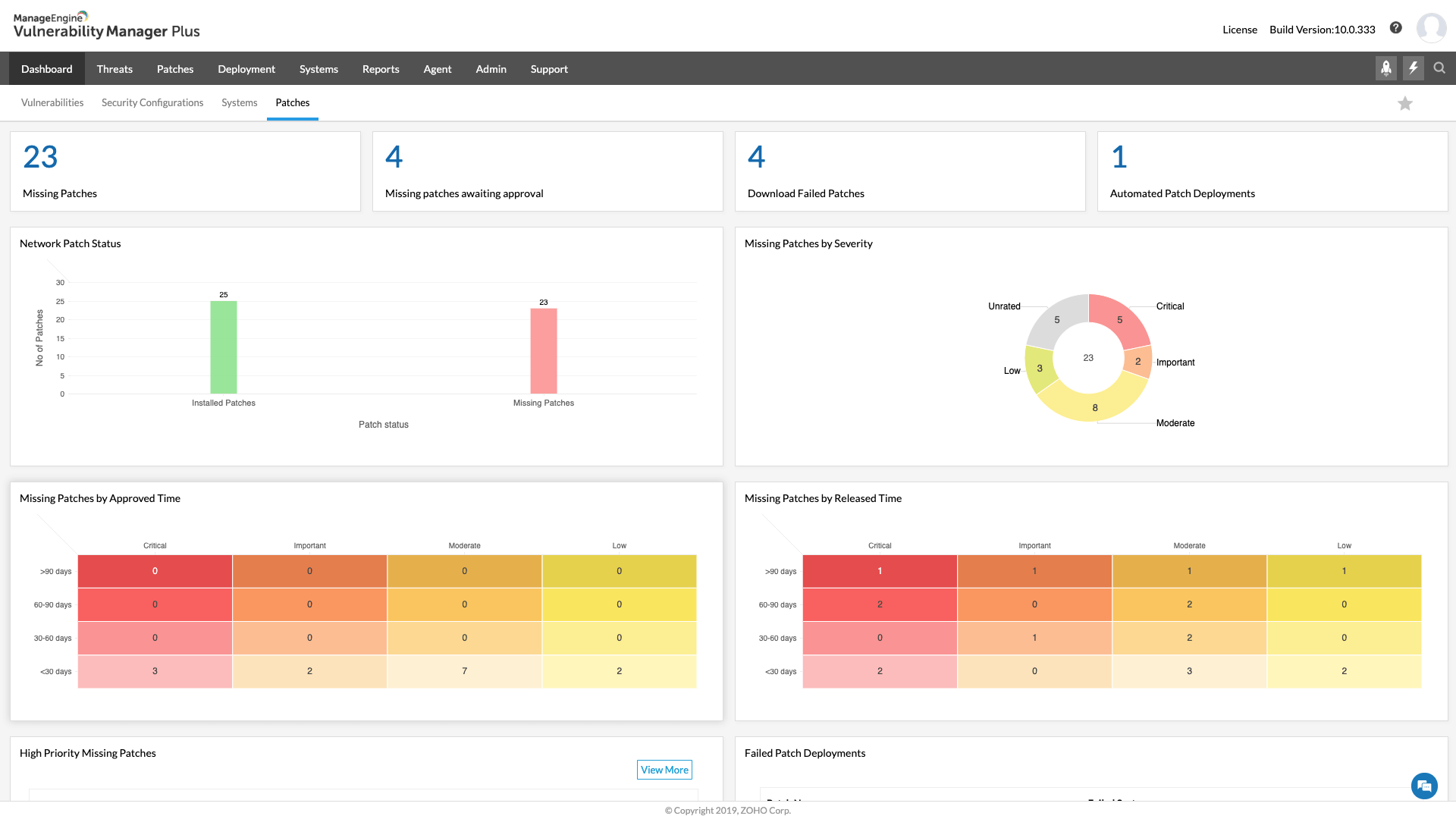
Built-in remediation
Our system has a feature that helps you fix security problems quickly and easily. It can automatically identify which problems are most important and suggest patches to fix them. You can also set up automatic updates to keep your system safe without needing to manually manage it. Additionally, you can use the system to configure security settings and remove risky software from all your devices at once. This means you can focus on other things while our system takes care of keeping your devices secure.
Vulnerability reporting
To keep your computer network secure, it's important to regularly check for and fix any weaknesses. But it's also important to keep track of how you're doing! That's where Vulnerability Manager Plus comes in - it has lots of different reports that show you how your network security is improving over time. You can choose different types of reports, like ones that show lots of details or ones that are easy to understand. You can even set it up so the reports are sent directly to important people in your organization, without you having to do anything!
Scan and secure your endpoints now with 30 days of free, unlimited access.
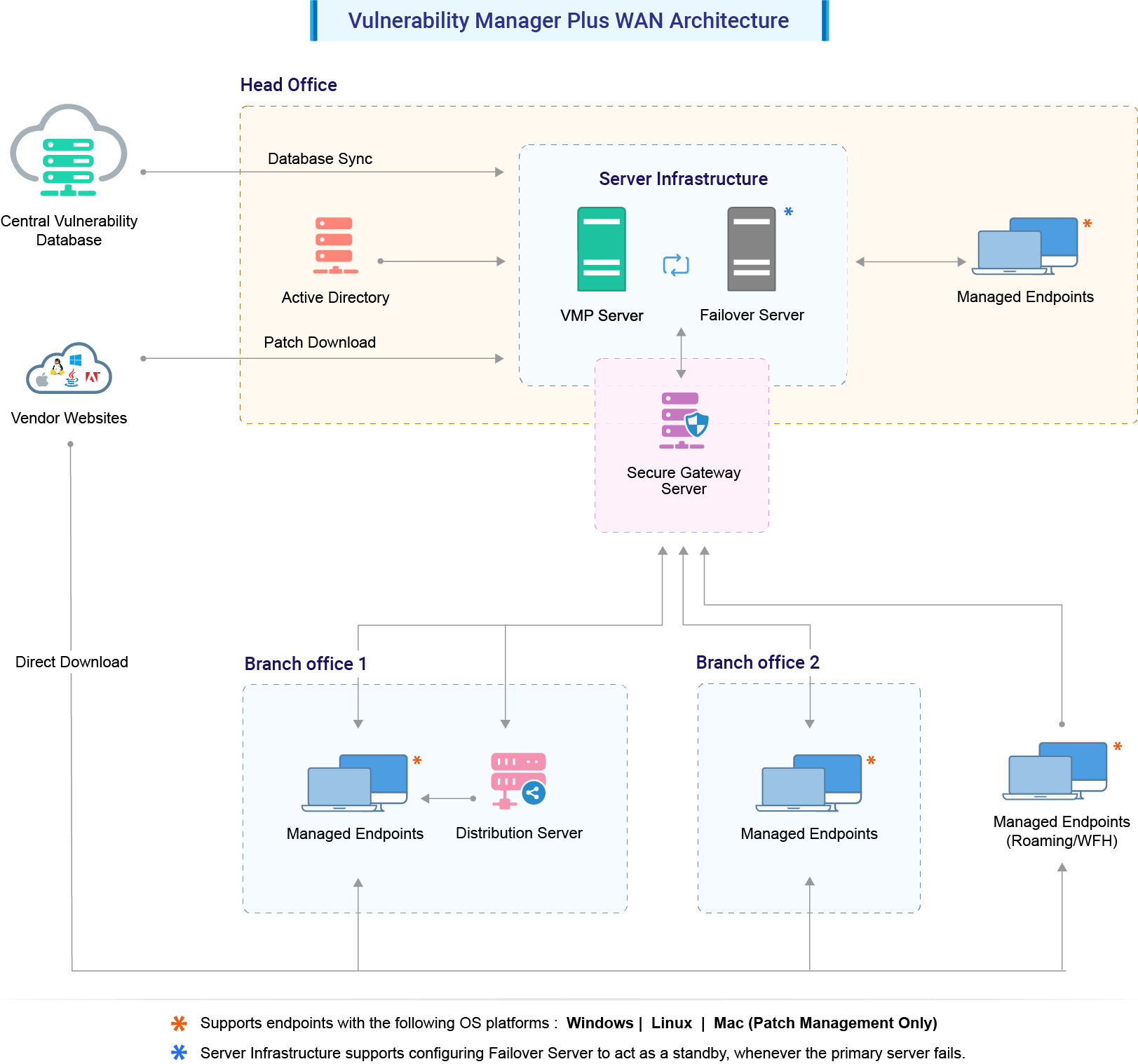
How does ManageEngine's vulnerability scanner work?
Below is a detailed breakdown of how Vulnerability Manager Plus works:
- Our team of experts scans the internet to find all possible vulnerabilities and threats that have been recently disclosed, along with the patches required to fix them.
- This information is thoroughly tested for accuracy and then stored in a central vulnerability database maintained by our security specialists.
- The database is periodically synchronized with the vulnerability database in the Vulnerability Manager Plus server that is installed in the user's enterprise.
- Agents are installed on all endpoints in the enterprise so that devices can be managed directly from the server console.
- Endpoints in local or remote offices can be managed by configuring the SOM policy. Roaming users who are always on the move will be assigned a default remote office, which helps keep them managed.
- The agents conduct a detailed vulnerability scan based on new vulnerability details from the servers and repeatedly check all endpoints for the existence of those vulnerabilities.
- The IT admin is shown the scan results, including valuable information such as the exploit status, severity, and patch availability, allowing them to prioritize which vulnerabilities require immediate attention.
- Thanks to the Automated Patch Deployment feature, the patches for vulnerabilities can be deployed automatically from the product console as soon as they are discovered.
- Vulnerability Manager Plus allows admins to create flexible patch deployment policies so that end users’ productivity isn't compromised during patching.
- With just a few clicks, the admin can squash any vulnerability in their network using Vulnerability Manager Plus.
Don't worry if some harmful elements find their way into your business despite your best efforts, as ManageEngine's Vulnerability Manager Plus has you covered. This software comes with a wide range of features to help you manage security and system misconfigurations, keeping all kinds of threats away from your enterprise.
FAQs about Vulnerability Scanning Tools
1) What are vulnerabilities?
Vulnerabilities are weaknesses in software that hackers can use to access sensitive information or cause damage to an organization. People who care about security are always looking for these weaknesses and give them a special name and score. The company that made the software gets a certain amount of time to fix the problem before the public finds out about it. Once the weakness is known, anyone can try to use it to hack into your system. Unfortunately, some people might not follow the rules and will tell others about the weakness before the company can fix it. If your organization uses software with a weakness, you could be in trouble.
2) What is Vulnerability Scanning?
Vulnerability scanning is a security process that checks your computer systems to find any weaknesses or vulnerabilities that could be used by hackers to gain unauthorized access. It's like a thorough check-up for your network and software, where any potential security risks are identified and reported back to you so that you can take action to fix them. This helps to protect your organization's digital assets and ensures that sensitive information remains secure.
3) What is a Vulnerability Scanner?
A vulnerability scanner is a tool that helps IT administrators check all the computers and devices in a company to find any weaknesses or risks that could cause security problems. It's like a security guard that looks for potential dangers and alerts the team to fix them before anything bad happens.
5) Why do you need a vulnerability scanner?
It's important for organizations to be aware of potential security weaknesses in their computer systems, even if they have software updates available to fix them. If these weaknesses are not addressed, they can be exploited by attackers and lead to serious problems like data leaks or financial losses.
To create a secure environment, it's essential to stay informed about these vulnerabilities and take steps to fix them. By using a vulnerability scanner tool, organizations can quickly find and fix these weaknesses, which can help protect against attacks and keep sensitive information safe.
6) What are the differences between a vulnerability scanner and an antivirus?
Vulnerability scanners and antivirus software are both crucial for maintaining cybersecurity, but they serve different purposes and function in distinct ways.
A vulnerability scanner is a tool that systematically examines the endpoints in the network to identify security weaknesses, such as software vulnerabilities, misconfigurations, and open ports. It helps organizations proactively address potential security risks before they can be exploited by attackers.
In contrast, antivirus software is designed to detect, prevent, and remove malicious software, including viruses, worms, and trojans. It operates by scanning files and system memory for known malware signatures and behaviors. These provide real-time protection, ensuring any detected threats are immediately quarantined or removed to prevent infection.
To summarize, while vulnerability scanners focus on identifying security gaps to prevent potential attacks, antivirus software aims to detect and neutralize active threats.
7) What are the challenges of vulnerability scanning?
Vulnerability scanning is a critical aspect of cybersecurity, but it faces several challenges that can impact its efficiency and accuracy. Here are some of them:
- Identifying and prioritizing vulnerabilities: A significant challenge with any vulnerability scanning tool is accurately identifying and prioritizing vulnerabilities. With numerous potential vulnerabilities detected during each scan, it's crucial to determine which ones pose the greatest risk and need immediate remediation. This process often requires evaluating the severity and potential impact of each identified vulnerability.
- Dealing with false positives and false negatives: Vulnerability scanner software can generate false positives (non-issues flagged as vulnerabilities) and false negatives (actual vulnerabilities missed). These inaccuracies necessitate manual verification, which can be time-consuming and resource-intensive, leading to potential delays in addressing real threats.
- Handling network complexities: Modern IT environments are highly complex and diverse, encompassing various devices, operating systems, applications, and configurations. Ensuring comprehensive vulnerability scanning across such heterogeneous networks without causing disruptions poses a significant challenge.
- Keeping up with the rapidly evolving threat landscape: Cyber threats evolve quickly, and vulnerability scanner software must continuously update to detect the latest vulnerabilities. Staying current with emerging threats requires constant updates and improvements to the scanning tools.
Effectively addressing these challenges is crucial for maintaining a robust cybersecurity posture and protecting organizational assets from potential threats.
8) What are the benefits of a vulnerability scanner?
Implementing a vulnerability scanner such as ManageEngine Vulnerability Manager Plus offers a comprehensive solution for organizations aiming to enhance their cybersecurity posture. Here are some of its benefits:
- Comprehensive vulnerability scanning across the entire IT infrastructure, including endpoints, network devices, servers, and applications. This ensures no potential threat is overlooked, providing a robust security assessment.
- Automated patching and remediation that not only detects vulnerabilities but also provides actionable insights and automated solutions to fix these issues promptly, reducing the risk of exploitation.
- Unified console with centralized visibility that allows administrators to monitor, detect, and address vulnerabilities, simplifying the cybersecurity management across the organization.
- CIS benchmark and compliance management to ensure that the organizations stay compliant with industry standards and regulations such as GDPR, HIPAA, and PCI-DSS. It provides detailed reports and audit trails, making it easier to demonstrate compliance during audits.
- Real-time Alerts and reporting to ensure that security teams are immediately notified of any vulnerabilities and can take swift action to mitigate risks.
9) How to choose the right Vulnerability Scanning Tool?
To find the best tool for scanning your organization's vulnerabilities, you need to consider things like how it works, how much it can handle, how much it costs, and what features you need. By looking at these factors, you can find the ideal tool that fits your organization's needs.
10) Is there a free vulnerability scanner?
ManageEngine Vulnerability Manager Plus offers an advanced set of features including but not limited to automated detection of vulnerabilities and missing patches, security and web server misconfigurations, port audit, vulnerability mitigation for network devices, and so on.
This free vulnerability scanner is available free of charge for up to 25 endpoints. To know more about it, check out the features of the free edition.
11) Why does an agent-based vulnerability scanner give you an edge over agentless scanning?
Agents are lightweight software packages installed into the endpoints. These agents can offer continual scanning and monitoring of the endpoints in the network when compared to agent-less solutions. Moreover, agent-based scanners have minimum impact on the network since the scans can be pre-scheduled.
Another major benefit of agent-based vulnerability scanners is that they can offer vulnerability scans for systems in air-gapped networks as well as BYOD systems.