What is a pass-the-ticket attack?
A pass-the-ticket attack occurs when an attacker essentially steals a Kerberos ticket granting ticket (TGT) or service ticket (TGS) to gain unauthorized access to systems and services within a network. They typically use malware, memory scraping techniques, or tools like Mimikatz to steal the tickets. With the stolen tickets, they don't require the user's password or hashed credentials, and they can easily impersonate legitimate users and move laterally across the network, making them a significant threat to enterprise security.
Pass-the-ticket vs. pass-the-hash
Pass-the-hash and pass-the-ticket attacks are both credential theft techniques and target authentication mechanisms. However, they differ in the following ways:
| Pass-the-ticket | Pass-the-hash |
|---|---|
| Involves stealing and reusing Kerberos tickets | Involves stealing and using hashed password credentials |
| Does not require password hashes but rather valid session tickets | Requires capturing NTLM hashes from compromised systems |
| More specific to Windows domain environments | Have a broader scope and can target multiple platforms beyond just Windows domains |
While both attacks allow lateral movement within a network, pass-the-ticket attacks are often more stealthy since they leverage valid Kerberos tickets rather than relying on credential hashes.
Pass-the-ticket attack example
- System compromise: An attacker gains initial access to a workstation or a domain controller within the organization network through a phishing email.
- Ticket extraction: Once inside, the attacker uses Mimikatz to extract all active Kerberos tickets from memory.
- Ticket injection: The attacker examines if there are Kerberos tickets for a domain administrator, and if so, they inject them into their own session to take on the identity and permissions of the domain admin.
- Lateral movement: Now, the attacker gains legitimate access to any of the resources that the domain admin has access to, without needing the credentials.
How to detect a pass-the-ticket attack
Typically, a pass-the-ticket attack can be detected by continuously monitoring all Kerberos events for anomalous patterns such as unusual ticket usage, ticket reuse, long-lived tickets, or logon anomalies.
Key Windows events to monitor:
How to protect against pass-the-ticket attacks
1. Implement strong credential hygiene
- Enforce least privilege access to limit exposure.
- Regularly rotate Kerberos keys and passwords.
- Use group-managed service accounts where applicable.
2. Enhance logging and monitoring
- Enable advanced Kerberos auditing in Windows event logging.
- Use SIEM tools to detect anomalies.
3. Deploy endpoint protection
- Utilize EDR solutions.
- Implement memory protection to prevent ticket extraction tools.
4. Network segmentation and access controls
- Restrict lateral movement with firewalls and network segmentation.
- Require MFA for privileged accounts.
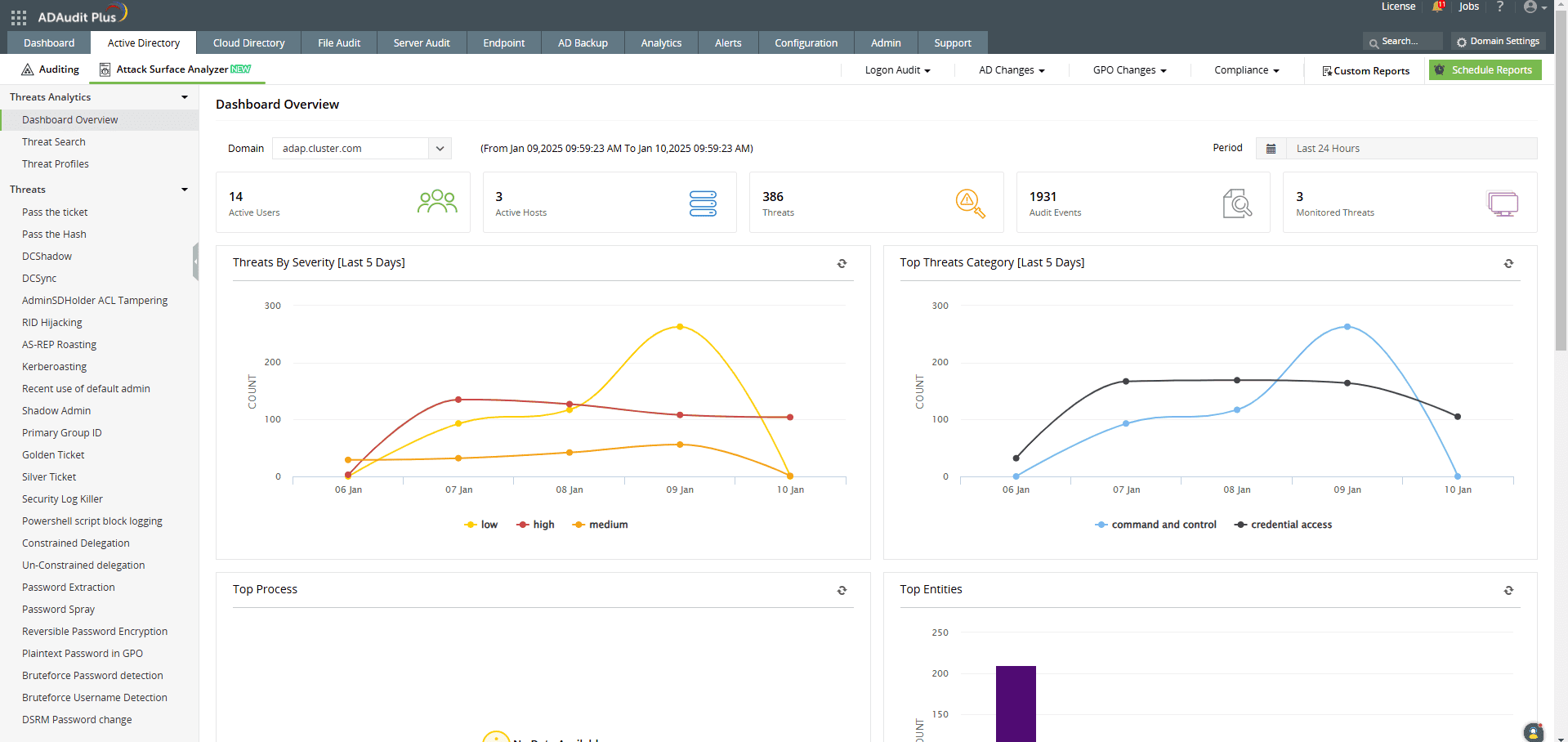
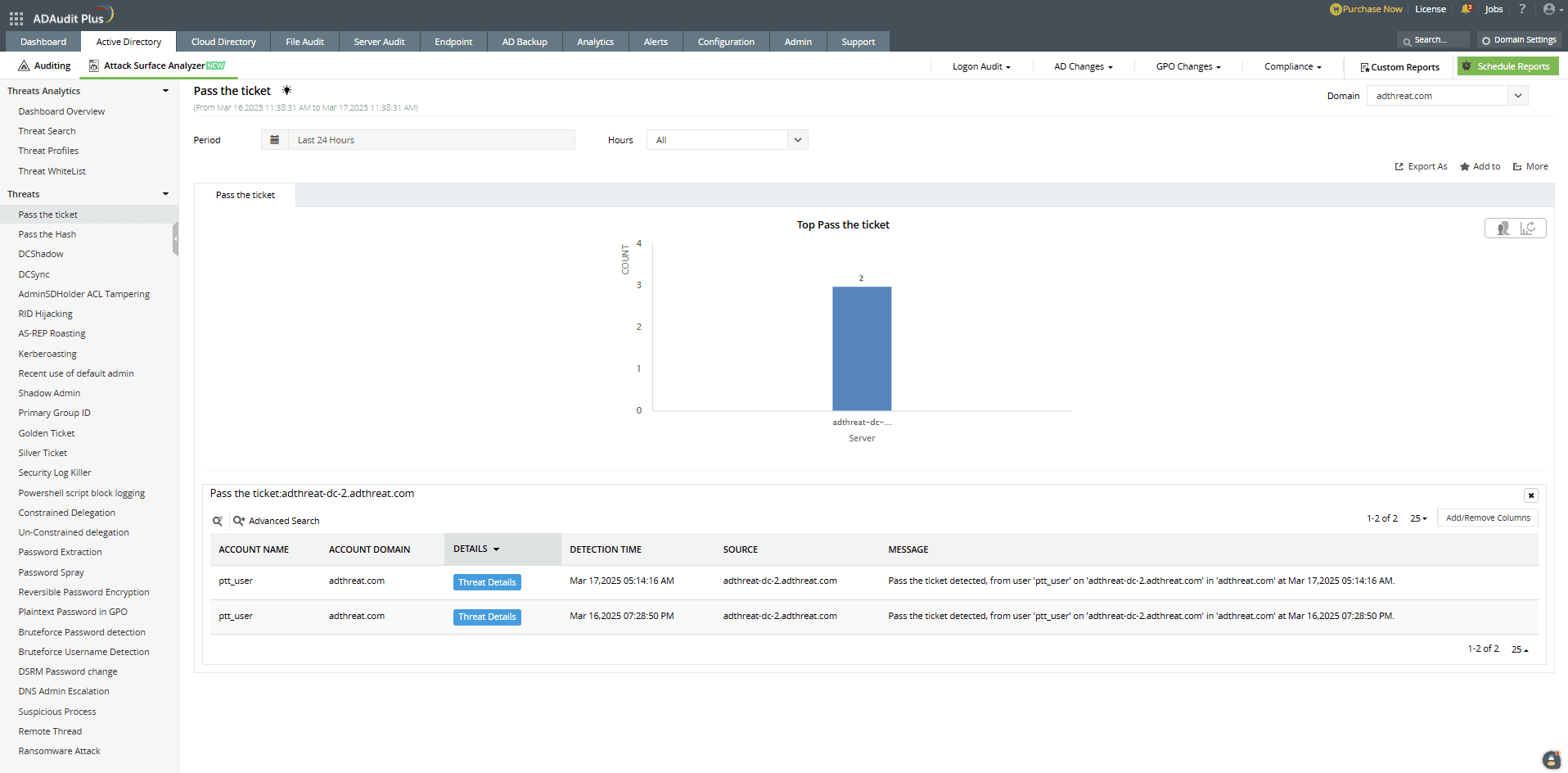
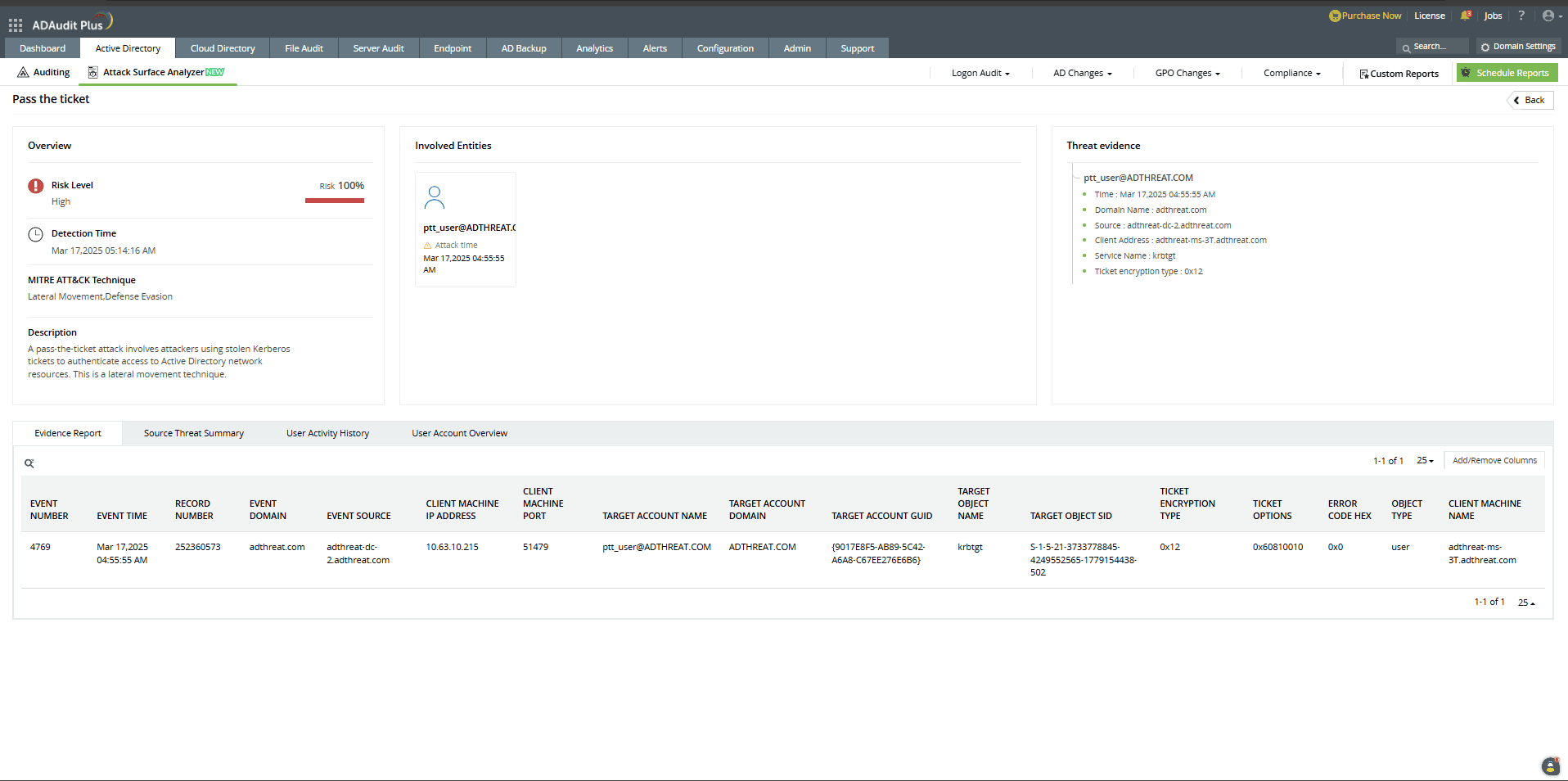
How ADAudit Plus can help you detect and mitigate pass-the-ticket attacks
ADAudit Plus' Attack Surface Analyzer features curated dashboards and specialized reports that help you detect and respond to pass-the-ticket attacks in real time. Powered by exclusive rules derived from the MITRE ATT&CK framework, the Attack Surface Analyzer delivers invaluable threat insights, enabling you to investigate potential pass-the-ticket attacks in just a few clicks.
Start protecting your on-premises and cloud AD resources with ADAudit Plus
Detect over 25 different AD attacks and identify potential misconfigurations within your Azure, GCP, and AWS cloud environments with the Attack Surface Analyzer.
See the Attack Surface Analyzer in actionWe're thrilled to be recognized as a Gartner Peer Insights Customers' Choice for Security Incident & Event Management (SIEM) for the fourth year in a row.