Log aggregation
A log analysis tool effectively gathers logs from various sources such as servers, databases, applications, network devices, security systems, and cloud services. The tool can collect logs in real-time or on a predefined schedule. Once the logs are collected, the tool aggregates the data, centralizes it to one location, and provides a comprehensive view of the network activities.
Learn more about log collection
Log normalization
Considering the varied nature of log sources, a log analysis tool normalizes the data into a uniform format. It parses logs to extract key details like the timestamp, event type, source IP, and organizes this information for precise and efficient analysis. An efficient log analysis solution also comes with a custom log parser to create new fields to extract even more information from logs.
Learn more about log parsing and normalization
Log analysis
Once the log data is standardized and centralized, the tool conducts a detailed analysis involving:
Pattern recognition analysis
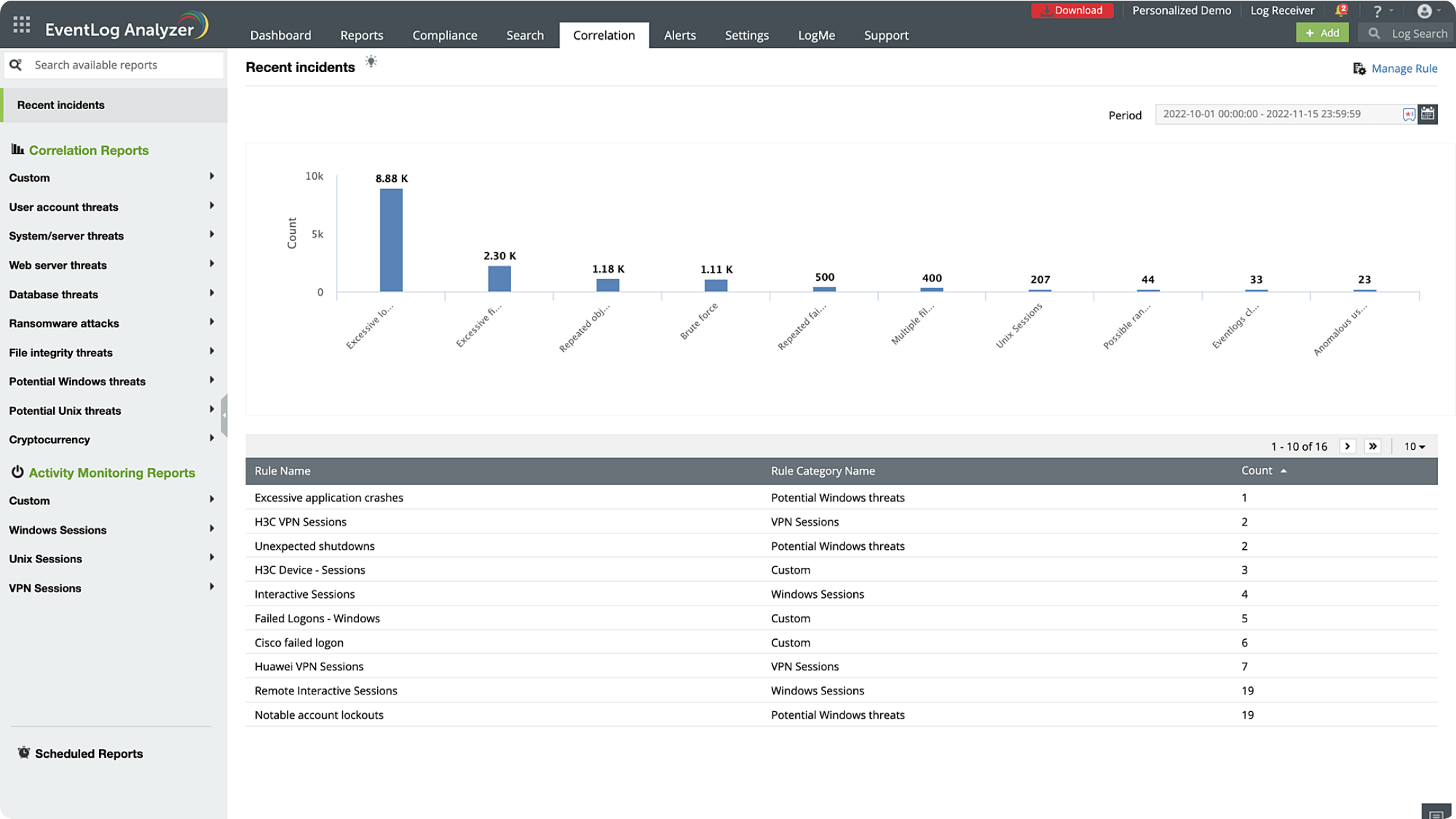
The tool identifies recurring patterns or trends over time, such as regular system activities, usage patterns, and security event trends.
Anomaly detection
It compares the current log entries with established patterns to spot anomalies or unusual activities that could signal known security threats.
It correlates logs from multiple sources to detect complex patterns, anomalies, and potential security threats.
Learn more about log analysis
Incident response and management
When a significant security event is detected, a log analyzer tool plays a crucial role in incident response and management by ensuring that potential security threats are addressed promptly and efficiently. The process involves several key steps:
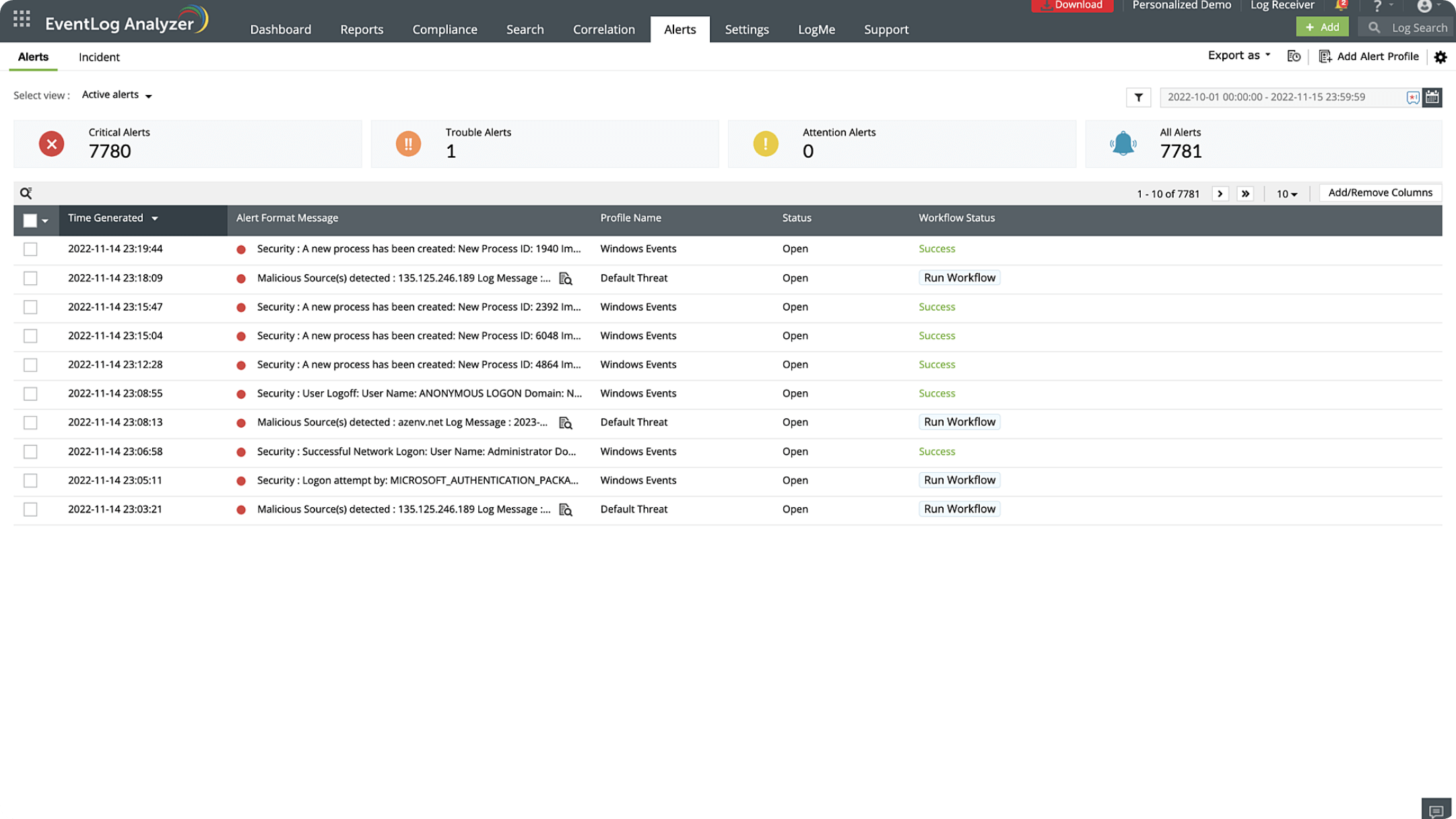
The first step in the process is the identification of a potential security threat. The log analyzer tool monitors log data and has access to updated threat data in the cybersecurity landscape, enabling it to quickly detect anomalies or unusual activities that may indicate a security threat.
Upon detection of a potential threat, the tool generates an alert. This alert is sent to the appropriate teams to ensure that they are immediately aware of the potential issue and can begin to address it.
In addition to alerting the relevant teams, a log analyzer tool can also initiate predefined workflows in response to the detected threat. These workflows represent a series of steps or actions that are automatically executed to contain the situation as the alerted teams looks into the issue.
This structured approach helps in minimizing the impact of any security incidents. It also enables the organization to maintain a high level of security, even in the face of unexpected or complex threats.
Learn more about incident response and management here
Reporting and visualization
Once log analysis is complete, the tool provides detailed reports with data visualization features to convert complex log data into easy-to-understand graphical representations to help you understand network activities, anomalies, and breach patterns.
Learn more about log visualization here
Log retention and archiving
Following the analysis, logs need to be securely stored for future reference and to comply with regulatory standards. A log analyzer tool manages this retention process by storing the logs for the required duration, archiving them in a secure manner, and keeping them readily accessible when needed. Some tools also offer features to manage archived logs efficiently, such as log compression, advanced search options, and more.
Learn more about log retention and archiving here
View more features