Firewall Duplicate Network and Service Objects - Optimization Reports
The Duplicate Objects sub-section in Firewall Analyzer Rule Management > Optimization sub-tab lists all the duplicate network and service objects used in the firewall rules.
This feature helps to find out the duplicate network and service objects of firewall. The result is derived by monitoring syslog data.
In this section, the most, least used network and service objects with hit counts are listed. The unused network and service objects are listed. On the left side, select the Device, Category - Service or Network and Type - Object or Object Group.
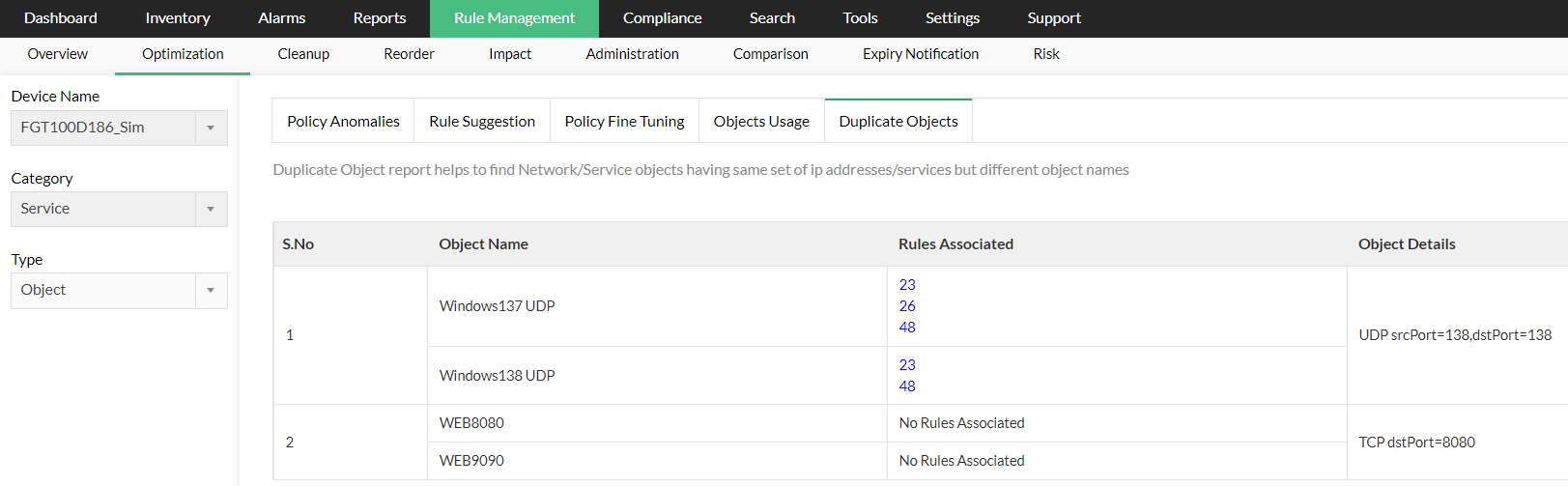
Duplicate Service Object report
The details are:
- Object Name - Name of the duplicate service object
- Rule Associated - Rule associated with the service object
- Object Details - Details of the object
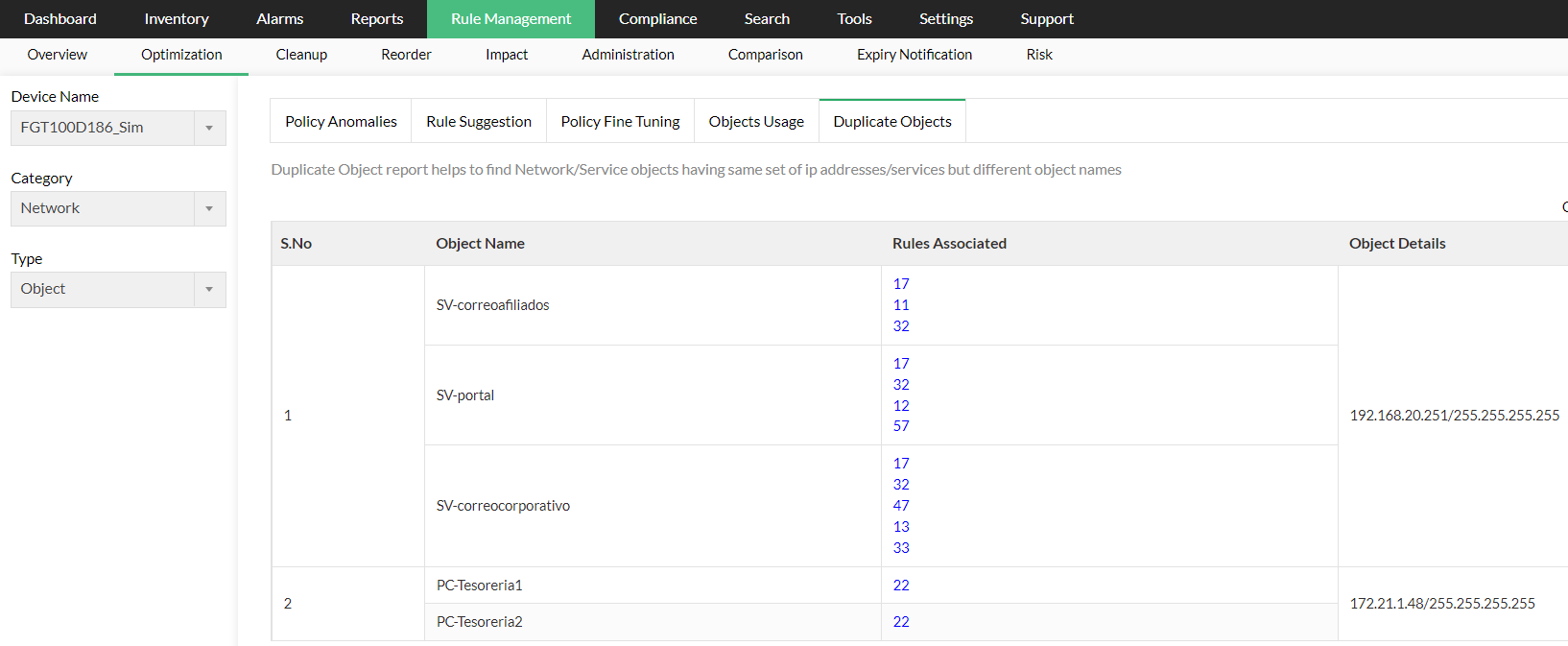
Duplicate Network Object report
The details are:
- Object Name - Name of the duplicate network object
- Rule Associated - Rule associated with the network object
- Object Details - Details of the object
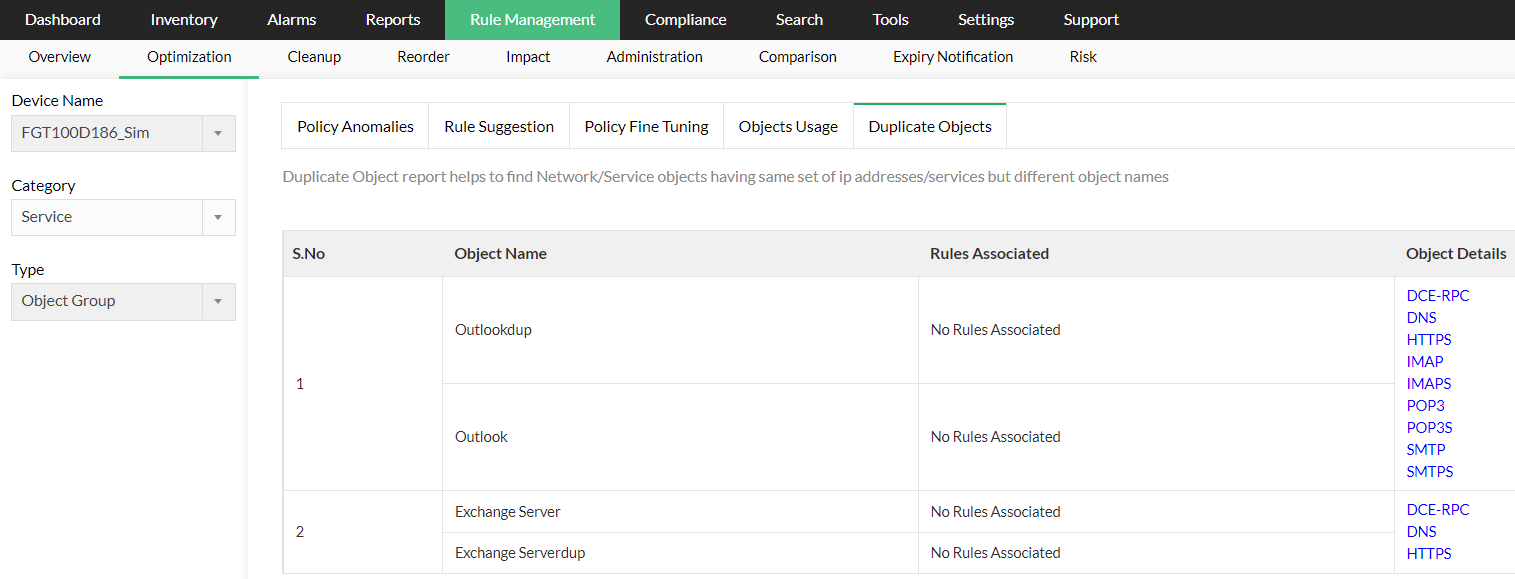
Duplicate Service Object Group report
The details are:
- Object Name - Name of the duplicate service object
- Rule Associated - Rule associated with the service object
- Object Details - Details of the object
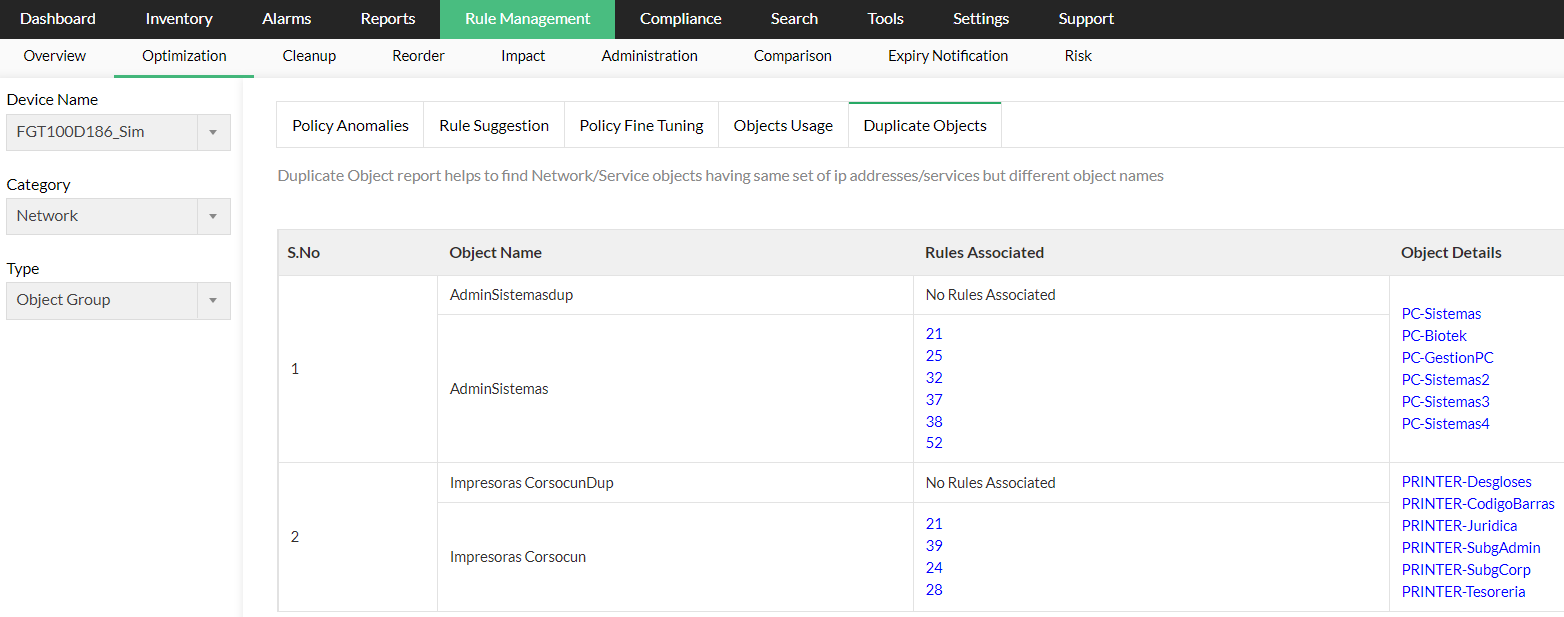
Duplicate Network Object Group report
The details are:
- Object Name - Name of the duplicate network object
- Rule Associated - Rule associated with the network object
- Object Details - Details of the object
Click on the rule number to view the details of the associated rule.
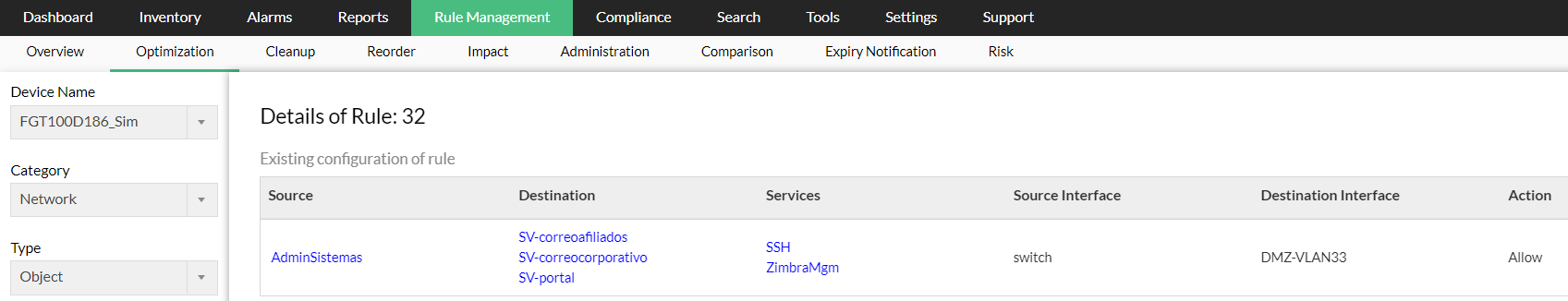
Details of the associated rules
The details of the rules associated with duplicated objects are displyed in the table. The details are Source, Destination, Service, and Action.
- Source - Source objects in the rule.
- Destionation - Destination objects in the rule.
- Services - Service objects in the rule.
- Source Interface - Source interface of the rule.
- Destionation - Destination Interface of the rule.
- Action - Permission actions of the rule.
Refer the Rule Management Report Support page, for the list of firewall devices.
Thank you for your feedback!