Issue: One of the main intrusion techniques used by hackers is password theft. In fact, stolen credentials ranked among the top 5 data breach action types in 2022.
Use case: Most organizations rely heavily on passwords to secure their network resources. However, users deal with their password saturated lives by often creating weak passwords and reusing them across critical business accounts. This makes stealing passwords the easiest way to get hold of network resources. Hackers only need to crack one user's password to enter an organization's network and cause havoc.
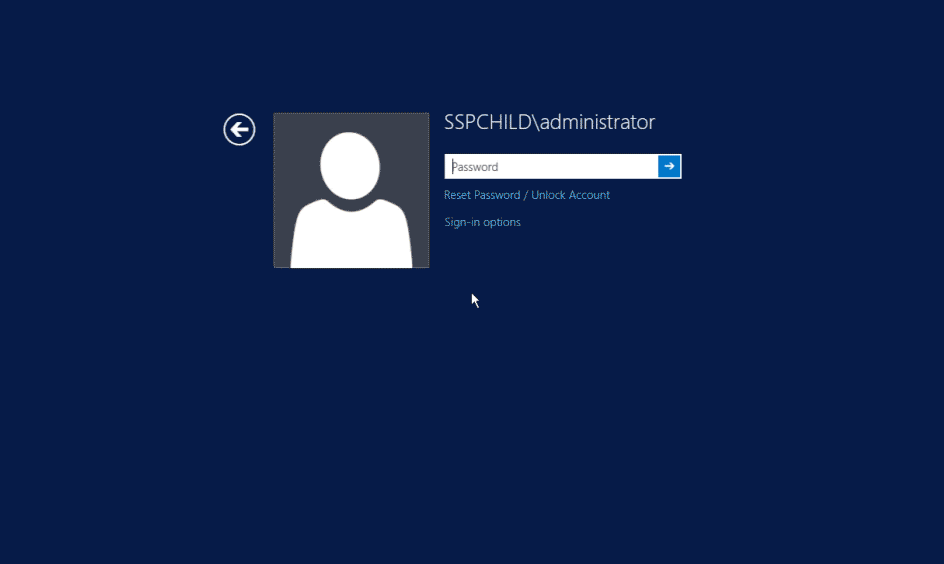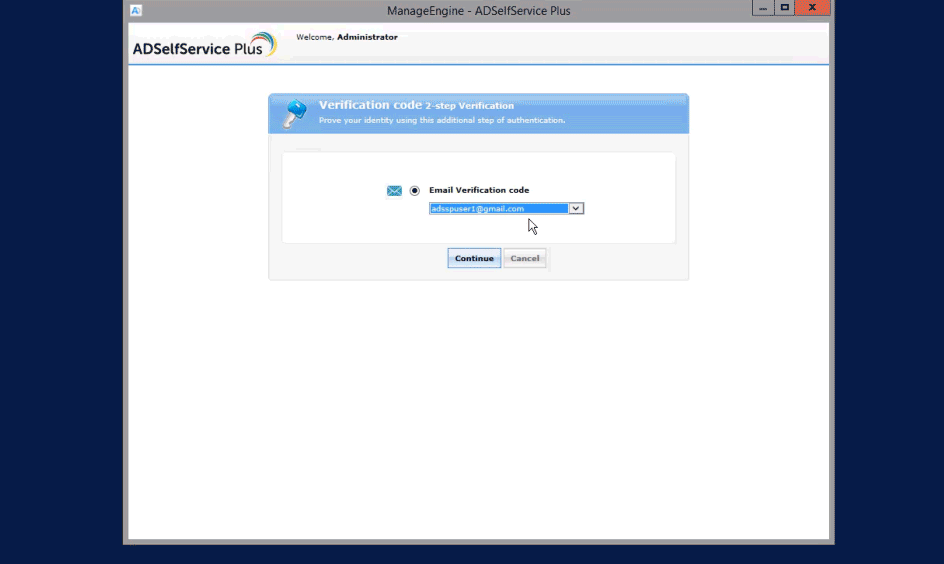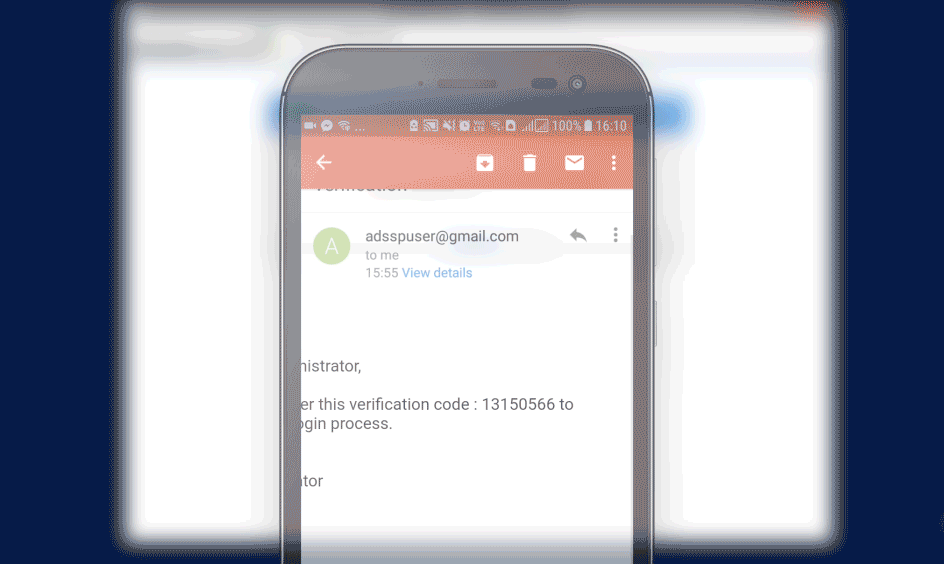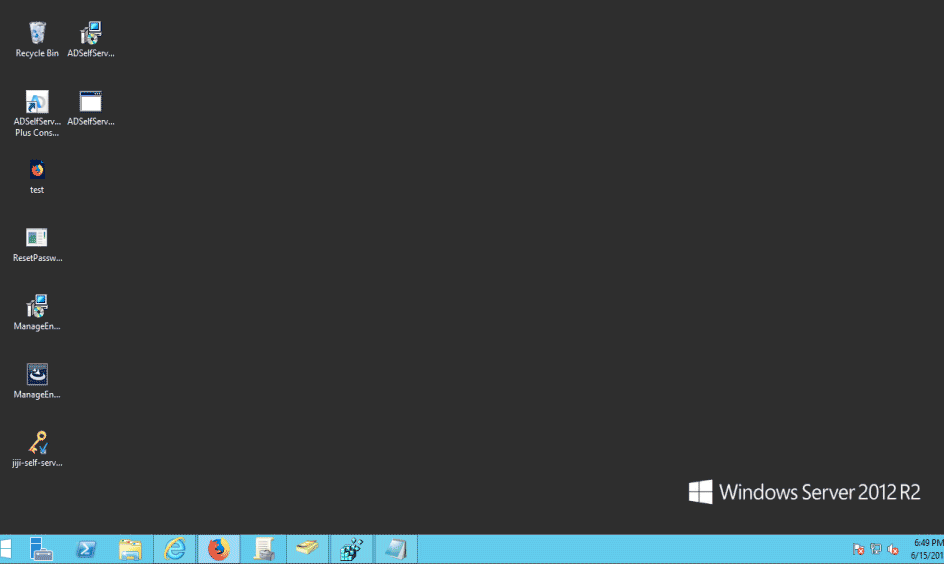
Solution: ADSelfService Plus makes stolen passwords ineffective by enabling additional layers of authentication using:
The solution supports upto 19 methods for MFA including Fingerprint or Face ID Authentication, YubiKey Authentication, Google Authenticator, Microsoft Authenticator, and Azure AD MFA. Click here to get the complete list of authenticators.
To enforce MFA for Windows/macOS/Linux logons logons
To enforce 2FA for SAML-enabled cloud applications
Need further assistance? Fill this form, and we'll contact you rightaway.
Allow Active Directory users to self-service their password resets and account unlock tasks, freeing them from lengthy help desk calls.
Get seamless one-click access to 100+ cloud applications. With enterprise single sign-on, users can access all their cloud applications using their Active Directory credentials.
Intimate Active Directory users of their impending password and account expiry via email and SMS notifications.
Synchronize Windows Active Directory user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Strong passwords resist various hacking threats. Enforce Active Directory users to adhere to compliant passwords by displaying password complexity requirements.
Enable Active Directory users to update their latest information themselves. Quick search features help admins scout for information using search keys like contact numbers.