ManageEngine's blueprint for endpoint management and a future-ready workforce
The 2000s can be called the decade of change. A lot happened in ten years. The world population crossed six billion, America saw its first African American president, and Bill Gates was the richest man alive for eight years. Most importantly, the 2000s also gave us the biggest tech change in our lifetime: the smartphone boom.
In 2009, Intel formally introduced a BYOD policy after a significant rise in employees bringing their own smartphones and laptops and connecting them to the corporate network. This revolutionized the workplace. Over a decade later, smartphones are now irreplaceable. Businesses are scrambling to find a system that allows personal devices and corporate information to coexist.
With remote work becoming the new norm, the road map for digital transformation is solely dependent on the choices we make now. Endpoint management has helped millions across the globe create a limitless workplace, covering every aspect of device management from PCs to smartphones. However, is it enough? How do you know if the measures you’re taking can protect your organization from future risks? Technology is growing faster than we can handle it. How do you keep up with the changes and provide your brand with an ecosystem in which it can thrive?
Why do you need this e-book?

A recent survey by Deloitte revealed that companies spend about 10 percent of their IT budget on cybersecurity. But does higher spending always mean a better cybersecurity maturity level?
Let’s say you’re going skydiving. You’re all strapped up and ready to go. Just as you’re about to jump, the instructor tells you there’s a 95 percent chance the parachute will work. Would you still jump out of the airplane? Would you leave that five percent to fate? Device management isn’t all that different. One small opportunity is all it takes to destroy years of effort.
Poor device management spares no one. It affects everyone from the CEO to tech support. As an organization, you have a lot at stake and not much room for error. Each year, companies lose millions to data breach lawsuits. This kind of crisis can be easily averted if you’re proactive in your efforts to manage employee devices. With the global launch of 5G paving the way for next-gen technology, you need to be prepared, if not one step ahead, with your endpoint strategy.
If you’re reading this, chances are you’re looking for a better endpoint system for your business. This e-book covers ManageEngine’s path to discovering the right device management plan—our achievements, mishaps, and everything in between. We’ll talk about the evolution of device management, the rise of BYOD, some real-life scenarios, and how we navigated through uncharted waters in the wake of COVID-19. We’ll also briefly discuss the future of mobility. Let’s dive in!
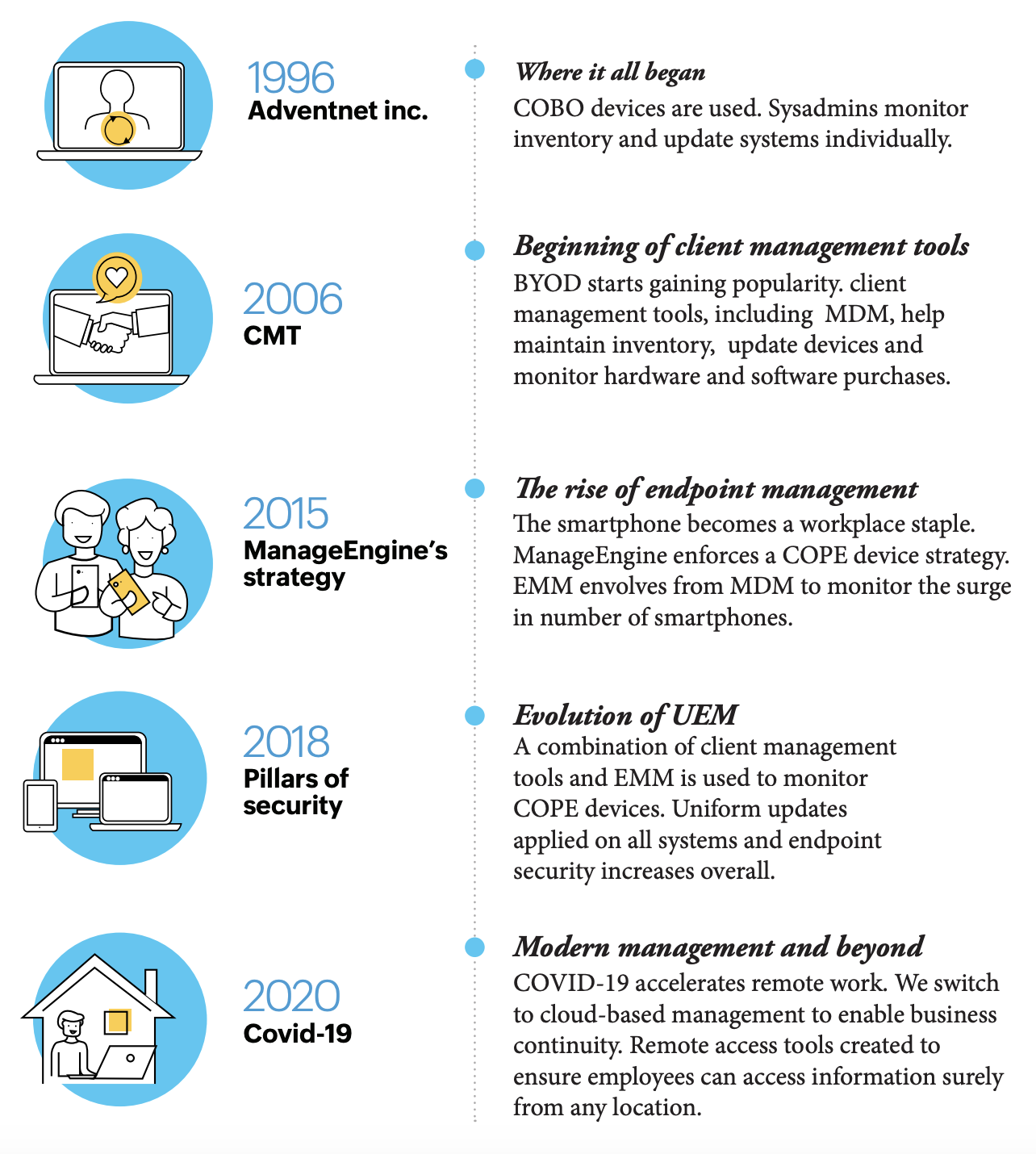
Our journey so far
Doing things our way
There's a saying that goes "It takes a wise man to learn from his mistakes, but an even wiser man to learn from others." Organizations spend years on market analysis, assessing trends, competition, risks, and opportunities before jumping into the market. ManageEngine isn't any different.
Instead of diving in headfirst trying to be the first of our kind, we learned from others' mistakes and meticulously tested our products in-house before their release. Playing it safe? Maybe. Nevertheless, the most secured plans come with a set of challenges. We started out with basic client management tools, moved to MDM, and finally created a comprehensive UEM system. During this period, we changed plans, locations, and even our name! It took years to reach where we are today, and we're nowhere near done. We are constantly trying to accommodate every need and create a holistic product that gives us exactly what we're looking for. We're trying to redefine management.
Why did we do that? Did it work?
ManageEngine’s device management through the years
Mistakes, losses, and a whole lot of repairs
Poor device management structure is your Achilles’ heel. In spite of your overall strength, your business functions can collapse if you’re unable to make sense of your management strategy. At ManageEngine, external devices were not a cause for concern up until about five years ago. Most employees used COBO devices so we didn’t focus on creating a device management plan. With the introduction of BYOD, devices became smaller and smarter, people took their work on the go, and security threats were larger than ever.
The biggest problem with a BYOD system is the lack of security. Employees might use unsecured Wi-Fi or mobile data, which leaves them vulnerable to attacks. If an employee loses their device, you’ve lost valuable, confidential information. That’s a lawsuit waiting to happen! Malware, compatibility issues, support costs, you name it—there are so many hurdles. One misstep can cause thousands of dollars in damages or worse, loss of trust and reputation. There’s nothing worse than losing a customer’s faith in your brand. Like they say, trust takes years to build and seconds to destroy.
We faced a number of challenges like:
- Unauthorized usage of apps and data sharing: Employees would often download apps that were not verified or approved by the company, and there was no way for us to monitor that. This also includes the use of hardware such as USBs to share information.
- Unknown devices entering the corporate network: Following a “trust but verify” system does reduce the risk of attacks, but it does not eliminate threats altogether.
- Device disparity: Corporate devices are usually procured from a predetermined list of original equipment manufacturers (OEMs). This usually consists of two to three vendors. In a BYOD setup, we had to be able to accommodate a wide variety of devices and ensure our applications were compatible with all of them. This removed the element of uniformity we craved.
- Difficulty in troubleshooting remotely
- Inability to deploy software and updates at once: Having to do it manually took up too much time, costing us valuable man-hours.
- Failure to conduct a remote wipe when an employee’s device was missing
- Most importantly, we did not have a centralized way to monitor activities. How would we know if we were compliant with data protection laws? Was customer information secure?
While these problems are neither unique nor universal, minimal device control and operational inefficiency definitely kept our Sysadmin team (and Legal and Compliance!) on their feet at all times. It started to look more like a never-ending battle with minor issues. Surely there had to be a better way to tackle this.
Next, we discussed requirements and strategy. When an employee walks out the door with sensitive information, it’s important to have an airtight device management plan in place. Once we saw a steady rise in device numbers, we decided to create a customized plan that worked for us. First we had to ask ourselves, What are we trying to fix? What are our goals? We came up with a list of requirements that would make device management easier.
Our plan should facilitate:
- Access control for deployment.
- Patch management.
- Automated processes to reduce admin workload.
- Remote access to devices.
- Restricted access—controlled admin privileges.
- Controlled use of external hardware (USBs).
- Power management.
- App restrictions and app blocklisting.
- Desktop and mobile integration.
- Geotracking for managed devices.
We picked company-issued devices to promote uniformity and cut down on operational costs in the long run. Now, how do we manage the devices? By creating a product that meets all our expectations. UEM with MDM as a built-in feature was the obvious choice. It gives us control over all our endpoints. We can monitor and carry out tasks almost effortlessly, not to mention the hours saved. For example, with endpoint management, IT admins get enrollment done in a third the time it would take to individually enroll devices. OS updates, which would usually be a week-long task, now only take a fraction of the time. A tool that we found to be particularly useful was Wake on LAN, which allowed us to schedule booting of Windows systems in the network remotely.
Finally, damage control. Devices go missing from time to time. When the inevitable occurs, we need a safety net. If an incident involving an end user occurs, it’s mandatory to file a report at the nearest police station. This is for any lost or stolen device at that particular location. The Sysadmin team issues a remote wipe, and records are updated accordingly. Our end goal during these circumstances is to be able to say “We’ve got it covered.”
Why now?
When we first started out, we had our endpoint management system with an integrated MDM module. But as BYOD’s undeniable popularity increased, it became evident that we were going to need a separate system to monitor gadgets, smartphones in particular. And we weren’t the only ones who saw the BYOD boom. Major players in the cloud software market, like VMware and SOTI, created their own systems. By 2012, there was an emerging market for MDM. In 2015, we released MDM as a separate product for customers and implemented that same solution within our organization.
MDM enhances network security and provides a centralized platform, especially for MSPs with a large number of devices. The ease of management using MDM is also what pushed us to consider COPE instead of BYOD. Having an in-house device management application, it just made sense to go with company-issued devices. We never have to worry about increasing costs to outsource device management or periodic renewals, and it’s far easier to push apps and updates to devices.
The steep rise of BYOD led to yet another step in endpoint evolution: EMM. Enterprise management solutions help secure corporate data while providing employees the flexibility of using their personal devices for work as well as the benefits offered by enterprise mobile management. The terms EMM and MDM are often used interchangeably. Both point to the idea of enhancing employee productivity by providing real-time management of employee devices to troubleshoot or configure. While MDM focuses on the device, EMM is a sophisticated version that protects not just the device but the information on it too.
One size does not fit all
ManageEngine follows a COPE approach. Employees are provided with a list of preapproved devices that meet the organization’s procurement standards (e.g., budget, availability, or business requirements), giving them the freedom to choose while maintaining a level of uniformity. An employee can also personalize their device, avoiding the need for two different devices. This way, the organization retains ownership. Company-issued devices are great for organizations with heavy security compliance requirements. They can exercise more control over mobility while respecting employees’ privacy. Moreover, because each device is preconfigured with the necessary security measures before it’s assigned to an employee, there’s less risk of a security breach and it isn’t a burden on the Sysadmin team. It makes repairs or replacements easier when compared to other approaches.
Our biggest challenge with COPE was keeping up with technology. Devices have to be frequently updated, more so for us, as we need to keep testing our products for compatibility across multiple platforms. After thorough evaluation, we stuck to a mid-range budget for employee devices that meets all our performance requirements and is supported by the OEM without breaking the bank. Luckily, the market today is flooded with a wide variety of smartphones, laptops, and peripherals at competitive prices. High-end devices are purchased exclusively for product testing.
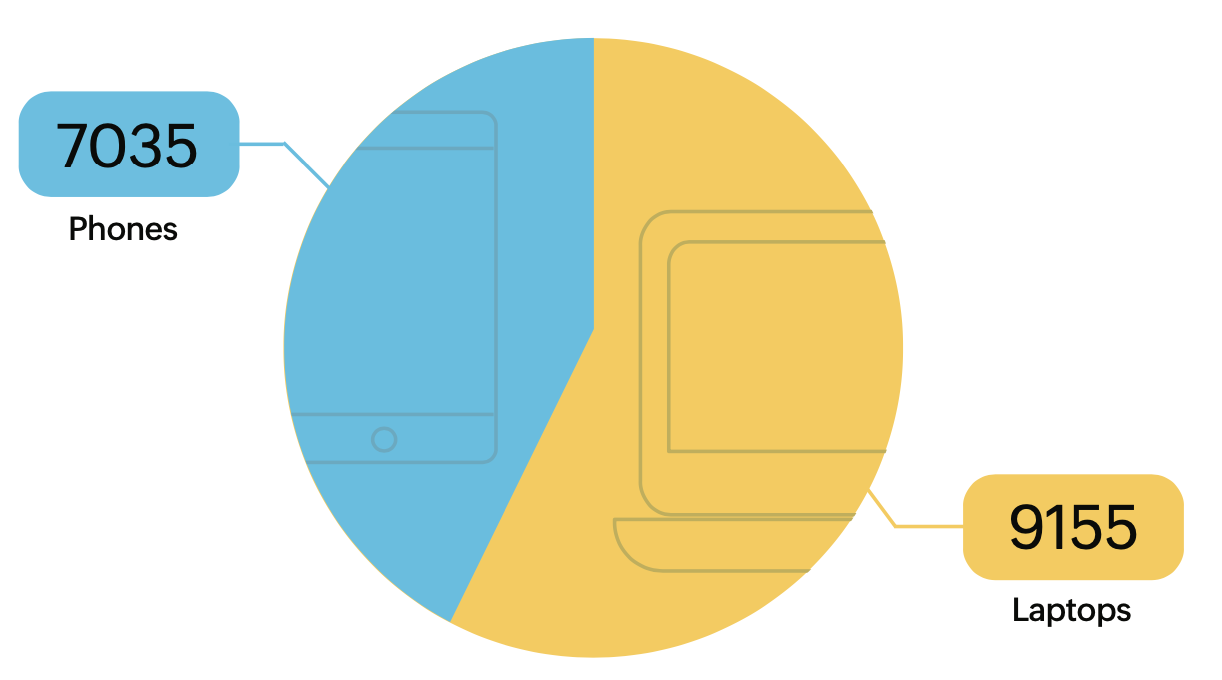
Number of devices in Zoho Corporation
-
Previous Chapter
‹ - ›