Chapter 2: The ManageEngine way
Taking IT management to the cloud
While ManageEngine was carving a name out for itself in the market, ManageEngine anticipated that cloud computing, accessing software over the internet, would be the next big thing. We predicted as early as 2007 that there would be a cloud explosion followed by consolidation.
When cloud computing was merely a concept, ManageEngine took the leap and decided to invest in on-premises and cloud-based solutions simultaneously. We started out with the on-demand version of OpManager, our network and server monitoring solution on a pay-as-you-go licensing model, and quickly expanded into help desk and desktop management.
Transitioning from on-premises to cloud solutions required following three approaches:
1) Existing tech, new product:
Zoho had just launched cloud-based applications, which gave us some much-needed technical insight. We were able to repurpose the existing code for some applications like our endpoint management suite of products.
2) New tech, existing product:
For some tools, like our help desk, we had a solid foundation in the on-premises version. With our insight into product management, workflows, and processes, we were able to adapt and transfer that knowledge to cloud solutions on a new tech stack.
3) New tech, new product:
Lastly, we took a completely different strategy for applications like website and server management, taking on a new product management angle and tech stack.
ManageEngine's business requirements depend heavily on internet-powered applications. From software accessed via browsers to mobile applications, infrastructure and technology play a critical role behind the scenes. Most data is stored in the cloud and can be securely accessed from any part of the world. As the world moves towards this cloud-powered model, more applications are churned out every day. To develop, deploy, configure, manage, monitor, and scale these applications, we need massive technical effort and resources with similar use cases being repetitively solved across applications.
In order to minimize effort and maximize output, these requirements can be provided as a common platform or framework. Zoho Corp uses a cloud platform that combines Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) tools. Developers can concentrate on building the application code (business logic) while the platform does the heavy lifting.
(I) Development
Secure by design:
Before DevOps, the early software development life cycle (SDLC) model used by most organizations was lean and product-oriented. Our focus was mostly on simple tasks and deliverables, which worked a decade ago. With the introduction of complex technologies, processes, and an increased focus on customer-centric services, our SDLC had to evolve.
Today, our SDLC mandates adherence to secure coding guidelines along with screening of code changes for potential security issues with our code analyzer tools, vulnerability scanners, and manual review processes. Each change and feature introduction is governed by a change management policy to ensure all application changes are authorized before implementation into production. We've talked about the finer details of ManageEngine's SLDC in our IT Release Management e-book.
Code-level security:
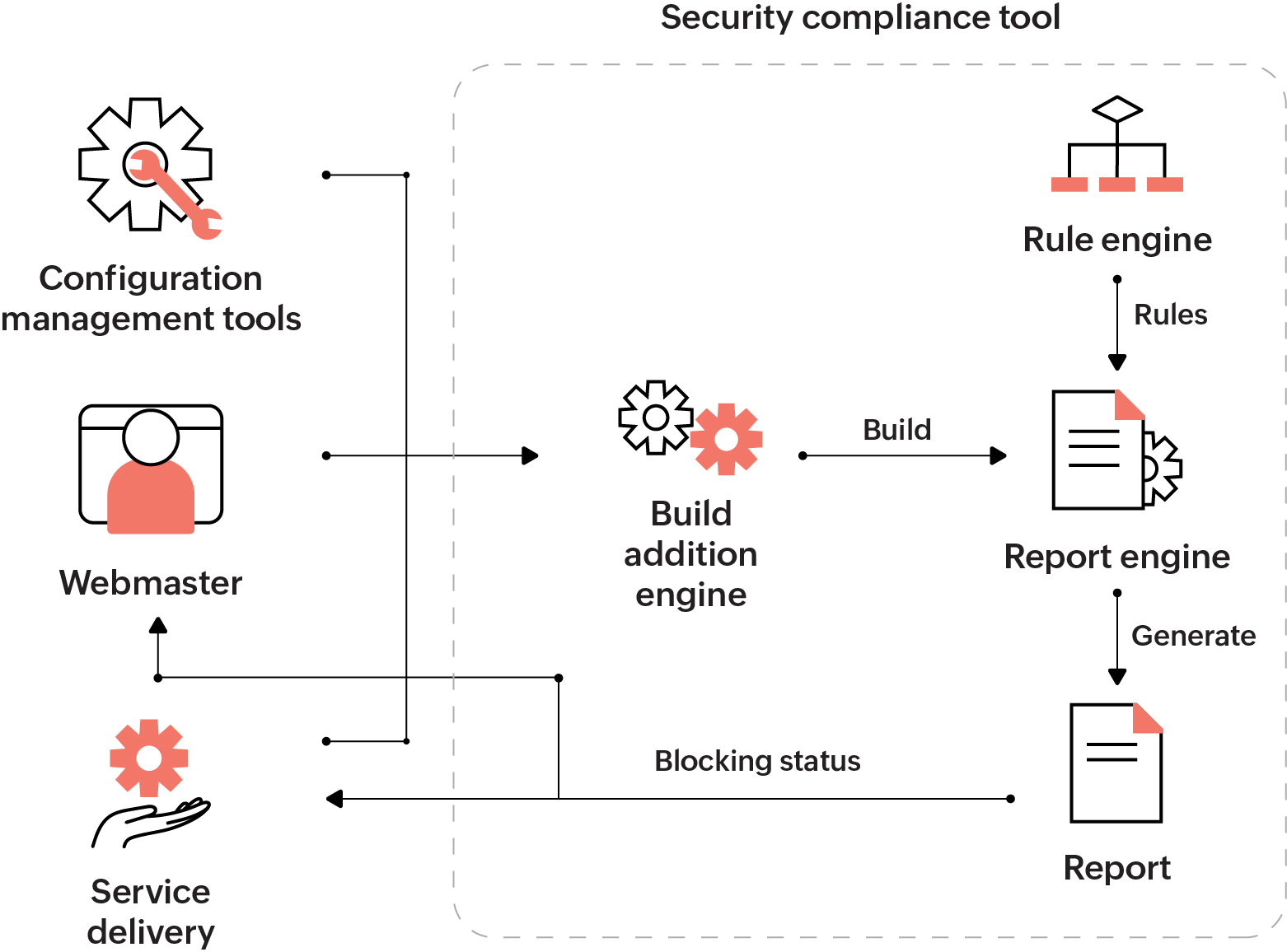
High-level overview of the internal security compliance tool
ManageEngine uses an internal security and compliance tool that identifies and reports the security vulnerabilities in a product executable. The goal is to promote secure software development by helping the developers identify the attack surfaces in their application and by providing solutions to minimize and secure those attack surfaces. The tool examines build executable, applies a set of rules, and prepares a security report containing the violations of the rules, if any. Based on the severity of the violations, the build release can be blocked.
A configuration team maintains the code created by the developers in our in-house centralized repository (like GitHub for general use). The team establishes and maintains the consistency of a product's performance, i.e, they use the product requirements, design, and operational information to sustain the product's functional and physical attributes throughout its life cycle.
(II) Infrastructure
Data centers:
Zoho Corp has data centers worldwide to cater to the needs of customers according to their region. Each region has multiple independent data centers to host products and smaller points of presence (PoPs) to support data center activity and provide a seamless user experience. Identity and access management (IAM) then functions as an additional layer that routes traffic to the appropriate data centers within each territory.
The birth of Mickey:
Once we started building more products, we needed a streamlined framework to speed up the development process and release features quickly without compromising on quality. Enter Mickey, our in-house proprietary solution. Mickey (short for Micro Kernel) is an easy-to-use framework that is used to develop web-based applications.
The code for commonly used features like authentication and authorization is repetitive across multiple ManageEngine products. Implementing them repeatedly is a waste of time and creates a lack of uniformity. Mickey acts as a base code and provides the infrastructure and an organized execution environment. Thanks to Mickey, product teams can focus on business logic instead of worrying about how the application runs.
Internal monitoring:
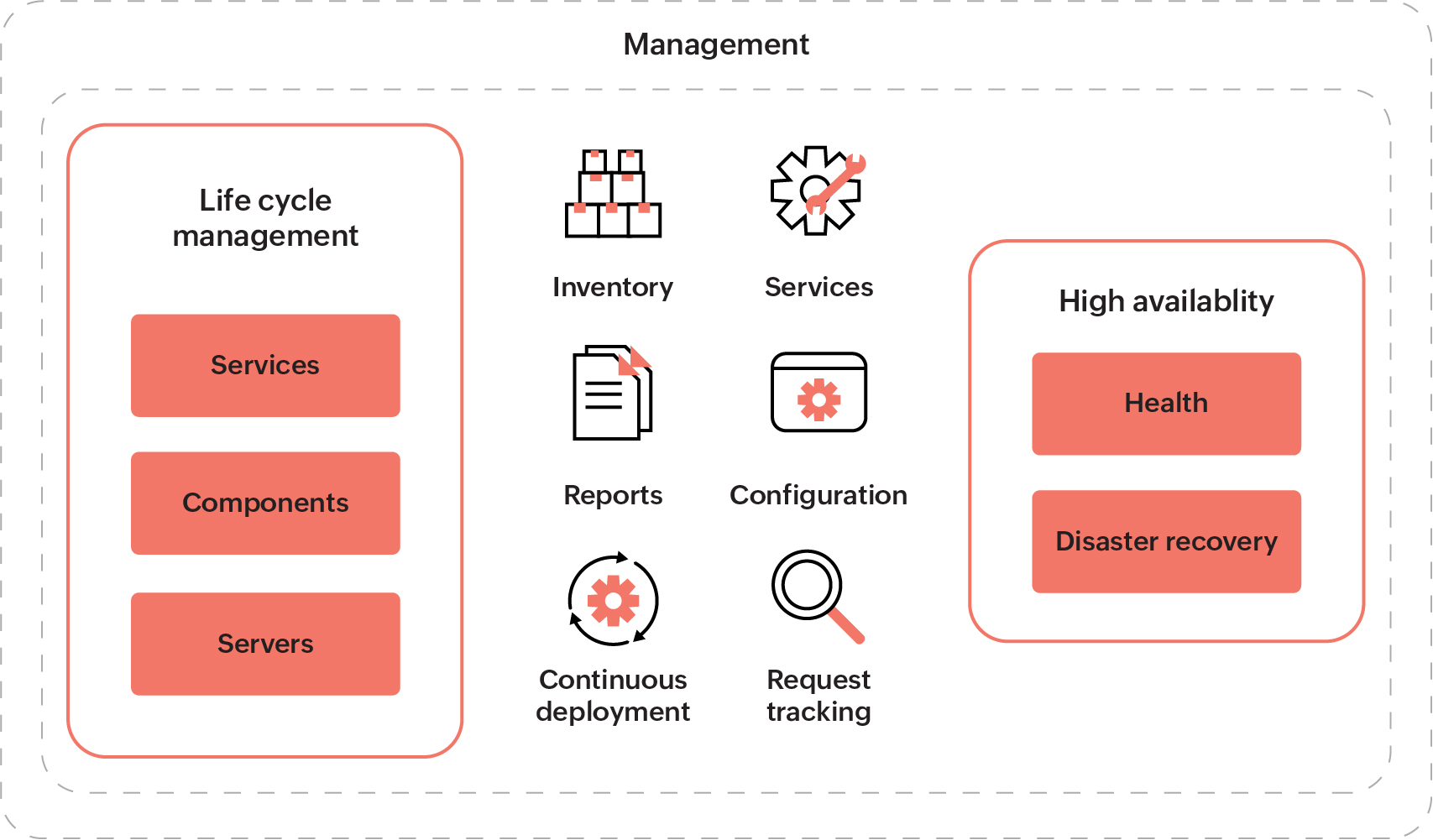
Zoho uses an in-house monitoring and instrumentation tool to keep the systems and processes involved in the cloud platform safe. Users can monitor parameters, components in a data center, and statistical data related to services via dashboards. In case the components or the processes running within a component have encountered an abnormality, raised events will be displayed on the dashboard, and alerts will be sent to the respective teams via email.
Admin console:
Zoho uses an in-house data center management tool to monitor and manage the complete data center infrastructure, cloud applications, and services used by the cloud applications.
Some of its responsibilities include:
- Inventory management.
- Operations management.
- Load balancer configuration.
- Server allocation.
- Certificate management.
- Disaster recovery switching.
(III) Information security
| Organizational security | Operational security | Infrastructure security | Data security | Identity and access control | General security |
|---|---|---|---|---|---|
| Endpoint security | Logging and monitoring | Server hardening | SDLC security | Single sign-on | Physical security |
| Internal audit and compliance | Vulnerability management | Network security and redundancy | Data isolation | Multi-factor authentication | Incident management |
| Security awareness | Malware and spam protection | Intrusion detection and prevention | Encryption | Administrative access | Responsible disclosures |
| Dedicated security and privacy teams | BCDR and back up | DDoS prevention | Data retention and disposal | Cloud access security brokers | Vendor and third-party supplier management |
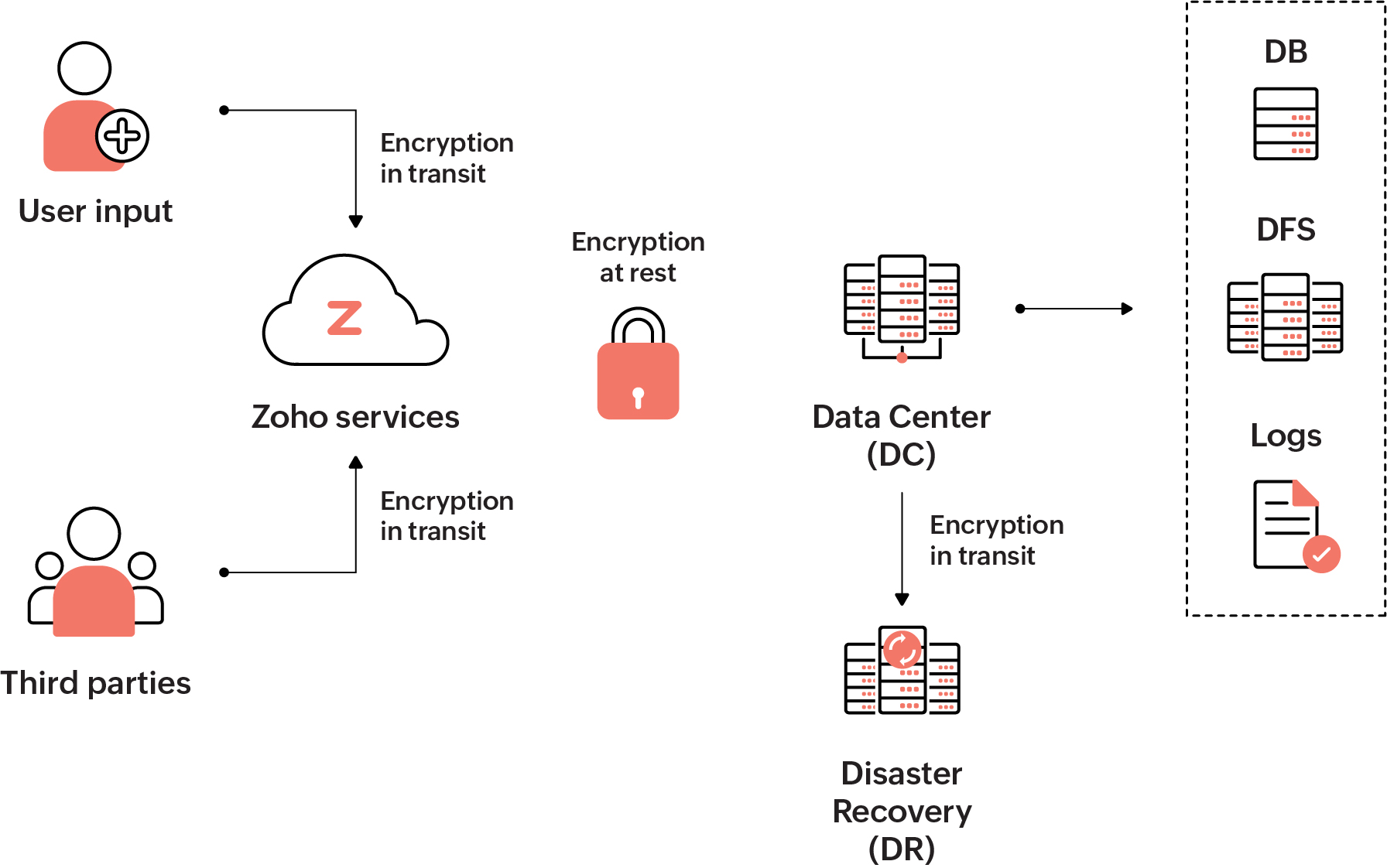
Gone are the days where we trusted anyone within the organization's network. ManageEngine's goal is to provide end-to-end security coverage for information that flows through the organization. Be it recording information like vendors, visitors, and employees or process control to restrict access, we have strict monitors in place to protect local information pertaining to our organization.
Customer data is encrypted both in transit (while customers are using our applications) and at rest in our servers. We also have a data deletion policy in place to discard customer data that is not in use or as requested by users. With the constant threat of cyberattacks, it's essential for us to be prepared through safety measures like internal and external testing to ensure our technology is up to date and capable of protecting sensitive information.
The ManageEngine Security Response Center (MESRC):
The MESRC monitors security forums like the US-CERT, National Vulnerabilities Database, and Bugtraq to identify and resolve vulnerabilities reported on ManageEngine products or on the third-party software bundled with ManageEngine's products. Users can report vulnerabilities through our bug bounty portal. After getting information about a vulnerability, the MESRC works with product experts to validate the claims, investigate the cause, and take up remedial measures and fixes. Once the solution is ready, it is provided as a service pack or patch to all customers following the usual support process.
Compliance:
Zoho has a dedicated compliance team to review procedures and policies; align them with standards; and determine what controls, processes, and systems are needed to meet the standards. The team also conducts periodic internal audits and facilitates independent audits and assessments by third parties. In our e-book, A CIO's guide to re-thinking compliance, we discussed the nuances of these regulations and our actions in detail. The following is a list of certifications and regulations upheld by the organization.
| Certifications | Role |
|---|---|
| ISO/IEC 27001 | Specifies the requirements for establishing, implementing, maintaining, and continually improving an information security management system within the context of the organization |
| ISO/IEC 27701 | Enhances the existing information security management system with additional requirements in order to establish, implement, maintain, and continually improve a privacy information management system |
| ISO/IEC 27017 | Gives guidelines for information security controls applicable to the provisioning and use of cloud services by providing additional implementation guidance for relevant controls specified in ISO/IEC 27002 and additional controls with implementation guidance that specifically relate to cloud services |
| ISO/IEC 27018 | Establishes commonly accepted control objectives, controls, and guidelines for implementing measures on safeguarding PII that is processed in a public cloud |
| ISO/IEC 20000 | Specifies requirements for an organization to establish, implement, maintain, and continually improve a service management system and supports the management of the service life cycle including the planning, design, transition, delivery, and improvement of services to meet the service requirements and deliver value |
| SOC 2 Type II | An evaluation of the design and operating effectiveness of controls that meet the American Institute of Certified Public Accountants' Trust Services Principles Criteria |
| SOC 2 + HIPAA | An independent third-party audit firm has examined the description of the system related to application development, production support and the related general information technology controls for the services provided to customers from Zoho's offshore development center based on security, privacy, and breach requirements set forth in HIPAA Administrative Simplification provisions. |
| CSA STAR Registry | The Cloud Security Alliance (CSA) defines and raises awareness of best practices to help ensure a secure cloud computing environment and help potential cloud customers make informed decisions when transitioning their IT operations to the cloud. The CSA assessment helps cloud service customers assess the security capabilities and practices of a cloud service provider. |
| GDPR | A pan-European regulation that requires businesses to protect the personal data and privacy of EU citizens for processing of their personal data |
| CCPA | A data privacy law specific to the processing of personal information of California residents that requires businesses to protect their personal information and provide privacy |
| Signal spam | Reports that help provide feedback loop (FBL) data, primarily technical information for identification of spammers and marketing abuse, from major ISPs like Orange.fr, SFR.fr, and so on. It has many spam reporting plug-ins for third-party browsers and email clients focused on French communities worldwide. |
Encryption:
Zoho Corp has established strict policies to adapt Transport Layer Security (TLS) to all its connections. TLS ensures a secure connection between end users and our servers by allowing the authentication of both parties involved in the connection and by encryption of data to be transferred. TLS protocol ensures third parties can't eavesdrop or tamper with communications.
For third-party communication, we use HTTPS. Transactions that involve sensitive data use asymmetric encryption. For these, we generate a pair of public and private keys in our key management service (KMS). We encrypt these pairs using a master key and the encrypted key pairs are stored in the KMS. The master key is stored on a separate server.
Public keys are made available to third parties through the certificates while we store the private key in the KMS; after authentication, the encrypted data is decrypted in the KMS.