What are DoS and DDoS attacks?
A DoS attack is a hacking technique that floods the victim's server, network, or application with an overwhelming number of requests, packets, or messages from a single source. So, what is a DDoS attack? DDoS attacks are similar, except that instead of one source, the attack originates from multiple sources.
The first thing an attacker does is take control of a network and the devices in it. These devices are infected with malware and used to carry out the attack. This collection of infected devices under the attacker's control is called a botnet.
Rather than infiltrating the network, in a DoS or DDos attack, the objective of hackers is to take down the target site and make it unavailable to regular users. This could affect the reputation of the organization and lead to a loss of trust among customers.
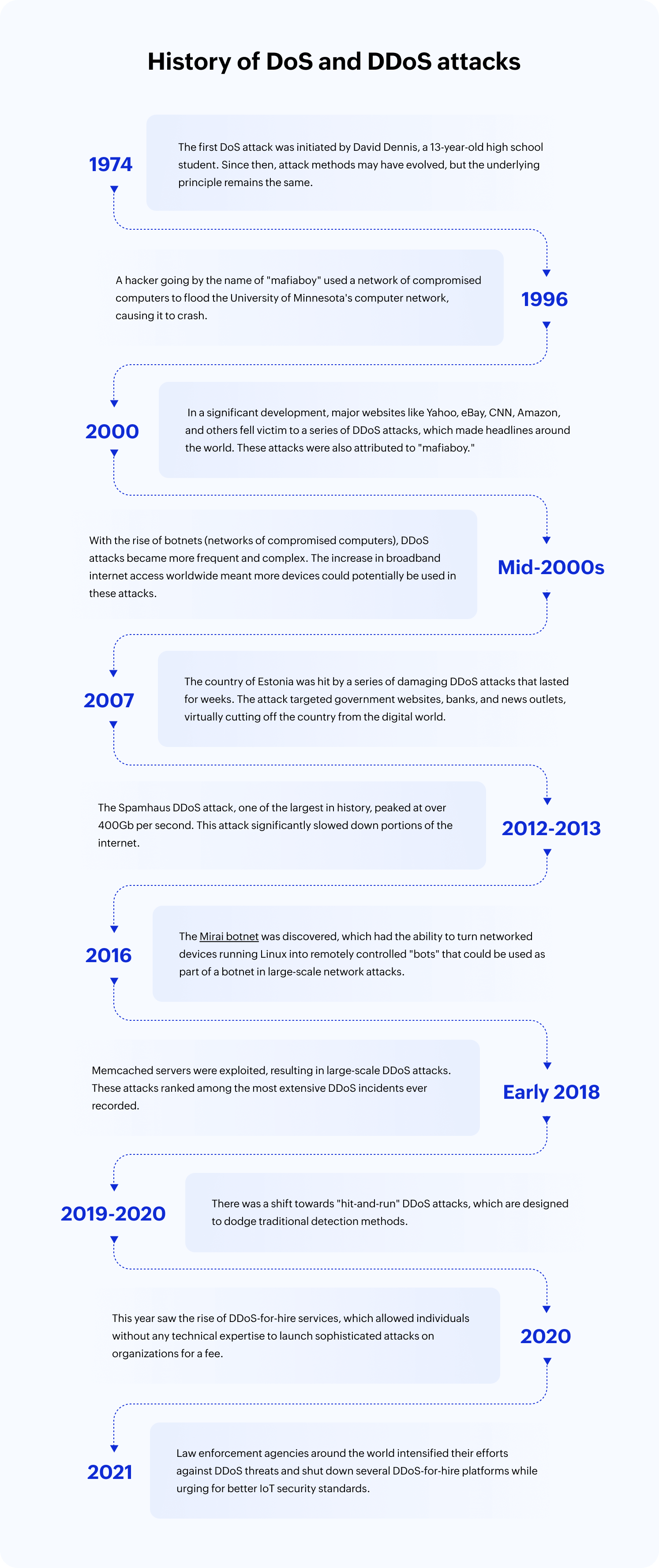
History of DoS and DDoS attacks
Types of DoS attacks
Flood attacks are the most common type of DoS attack. They involve overwhelming a network with traffic until it can't handle any more, thereby denying service to legitimate users. Examples include:
1. Ping flood (ICMP flood) attack
This type of attack overwhelms a target by sending a large number of ICMP echo request (ping) packets, exhausting network resources and causing temporary unresponsiveness.
Example:
Let’s assume a small online shop has a server. An attacker who wants to disrupt the store’s business sends a torrent of ICMP echo request packets using a simple command like:
The server gets overwhelmed by the incoming requests, leading to slowdowns or even a complete halt of the services, affecting the store's ability to process orders.
2. SYN flood attack
This attack exploits the TCP three-way handshake by flooding the target with a high volume of SYN packets, preventing legitimate connections from establishing.
Example:
A popular online gaming server could be targeted by a competitor who wishes to disrupt the gaming experience. The attacker uses a tool to send thousands of SYN requests but never completes the handshake by sending the corresponding ACKs. This can be done using a tool like hping3:
The server's resources are consumed by the incomplete connections, and legitimate players find themselves unable to connect to the server.
3. UDP flood attack
This attack floods the target with a large number of UDP packets, causing resource exhaustion and network disruptions.
Example:
An attacker who wants to disrupt a VoIP service can use a script that sends UDP packets to random ports on the target system, such as:
Since UDP doesn't require a handshake, the target system is flooded with packets it cannot process, leading to a degradation of service or complete unavailability. This can result in dropped calls or poor call quality for legitimate users.
Types of DDoS attacks
To execute a DDoS attack, threat actors exploit vulnerabilities in various network protocols and application layers. They launch attacks through different vectors. The three major types of DDoS attack include:
1. Volumetric attacks
This attack overwhelms the target with a massive volume of traffic, consuming its bandwidth and resources.
You could create a large amount of traffic using a tool like hping3:
Example:
Imagine an online news portal during an election. An attacker could use a botnet to send a massive amount of data to the portal's servers, making it unavailable for users during a critical time.
This would send packets as quickly as possible to the target, attempting to consume its bandwidth.
2. TCP state exhaustion attacks
This attack exploits weaknesses in TCP connection handling to exhaust server resources.
Example:
A small e-commerce site could be targeted with a TCP state exhaustion attack, where the attacker opens many connections and leaves them incomplete, filling up the server's connection table. This can lead to a denial of service for genuine customers.
You can simulate a TCP state exhaustion attack using a tool like hping3 to create SYN packets:
3. Application layer attacks
This attack targets specific applications or services to exhaust server resources, affecting application performance.
Example:
A blog site with a search feature that's not optimized could be targeted. An attacker might automate thousands of complex search queries, consuming server resources and slowing down or crashing the site.
Here's a Python script that could simulate this scenario:
# The target URL with the search endpoint
target_url = 'http://example-blog-site.com/search'
# A list of complex search queries
queries = ['complex query 1', 'complex query 2', 'complex query 3', 'complex query 4'] * 1000
# Iterate through the queries and send the requests
for query in queries:
params = {'query': query}
response = requests.get(target_url, params=params)
# Optional: Print the response status to monitor the progress
print(f'Status code: {response.status_code}')
This script sends repeated requests to the target blog site's search endpoint with various complex queries. If the search function is not well-optimized and the queries are genuinely resource-intensive, this could consume server resources and impact the site's performance.
Attack flow
- Inspection
Attackers identify potential targets and vulnerabilities for exploitation.
- Botnet formation
The attacker assembles a botnet by infecting numerous devices with malware, which can be done using phishing or other malware delivery techniques.
- Launch
The botnet is activated to flood the target's network or service with a deluge of traffic.
- Overwhelm
The target's resources are overwhelmed, causing disruption and denying access to legitimate users.
- Post-attack
Attackers may analyze the attack's success and plan for future attacks, potentially targeting new vulnerabilities.
Detection mechanism
Detecting DDoS attacks in real time is critical to minimize their impact. Effective DDoS detection mechanisms include:
- Traffic anomaly detection
Analyzing traffic patterns to identify unusual spikes or deviations.
- Behavior analysis
Monitoring user behavior to spot suspicious or abnormal activities.
- Rate-based thresholding
Setting predefined thresholds for network traffic and triggering alerts when they're exceeded.
Best practices
Best practices to prevent DoS and DDoS attacks
- Use infrastructure upgrades and redundancy
Having a robust and scalable infrastructure can help withstand a sudden influx of traffic. Implementing redundancy, such as having multiple servers in different locations, can ensure continued service even if one server is targeted.
- Perform regular security audits and patch management
Regularly check for system vulnerabilities and keep all your software, including operating systems, applications, and any security tools, updated. Install patches and fixes as soon as they become available.
- Have an incident response plan
Have a clear and well-practiced response plan in place. This ensures you know what to do if an attack happens, which can significantly reduce the potential damage.
- Monitor traffic
Monitoring your network traffic can help you identify patterns indicative of a DoS or DDoS attack. Using tools that can alert you to unusual traffic patterns can help you respond quickly when an attack happens.
- Use a DDoS mitigation service
These services specialize in detecting and mitigating DDoS attacks, providing an extra layer of security. They can help absorb the traffic associated with these attacks and prevent them from reaching your network.
- Use a SIEM solution
A SIEM solution provides real-time analysis of network traffic and system logs, swiftly identifying abnormal patterns indicative of DDoS attacks. This proactive approach empowers you to mitigate threats before they escalate, enhancing your cybersecurity posture.
Detect and mitigate with Log360
Log360 offers a range of features that can help detect and mitigate DDoS attacks effectively.
Real-time log management
Real-time log collection in Log360 is instrumental in detecting DDoS attacks because it provides immediate access to up-to-date network activity data. This real-time data is critical for effectively identifying and responding to DDoS attacks as they happen.
DDoS attacks can escalate and cause significant damage within a short period. By collecting log data in real time, Log360 can quickly detect anomalies and unusual patterns associated with DDoS attacks. This prompt detection enables security teams to respond swiftly and mitigate the impact before it causes a large disruption.
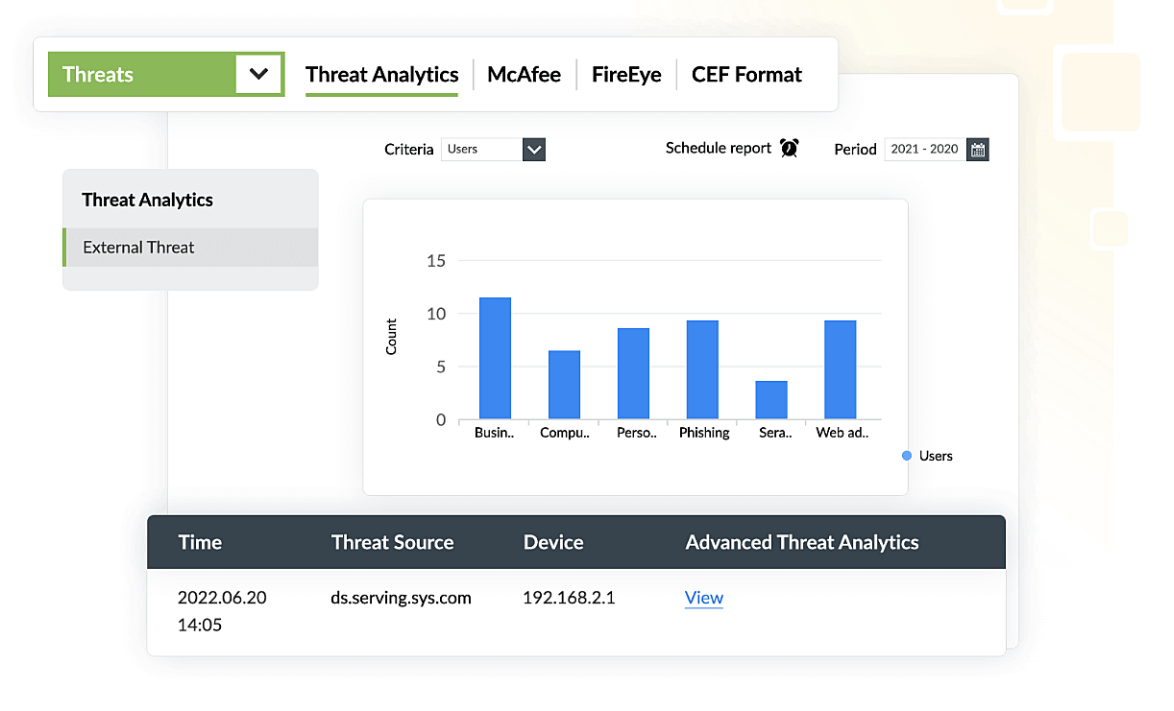
Log360 provides comprehensive oversight for a diverse array of devices, including routers, firewalls, servers, and various network components. This holistic approach allows you to recognize the telltale signs of DDoS attacks through attack patterns. The attack pattern might be similar to this:
- Sudden traffic spikes and a high failed connection rate
- Concentrated requests from specific IPs or geographical areas
- Traffic spikes during off-peak hours
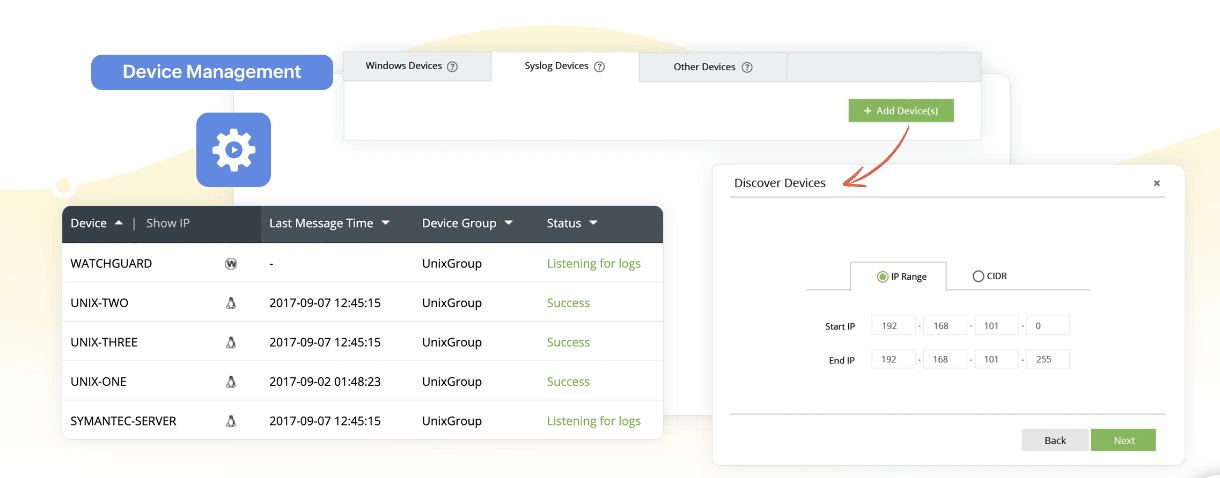
Machine-learning-based user and entity behavior analysis (UEBA)
Leveraging real-time log data, Log360 creates behavior profiles for network entities such as users, applications, and servers, and swiftly identifies anomalies indicative of DDoS activity. Through adaptive learning and real-time analysis, Log360 continuously updates its knowledge to keep pace with evolving DDoS attack patterns.
With Log360's UEBA, you can analyze user and device context, enabling swift incident response and empowering organizations to mitigate the impact of DDoS attacks effectively. Log360 also provides dedicated and subsidized DoS reports that help you gain vital insights for proactive defense. These reports shed light on attack trends, identifying patterns of excessive traffic and connection failures. By highlighting these important points in your network, Log360 helps you to fortify your defenses against DoS attacks.
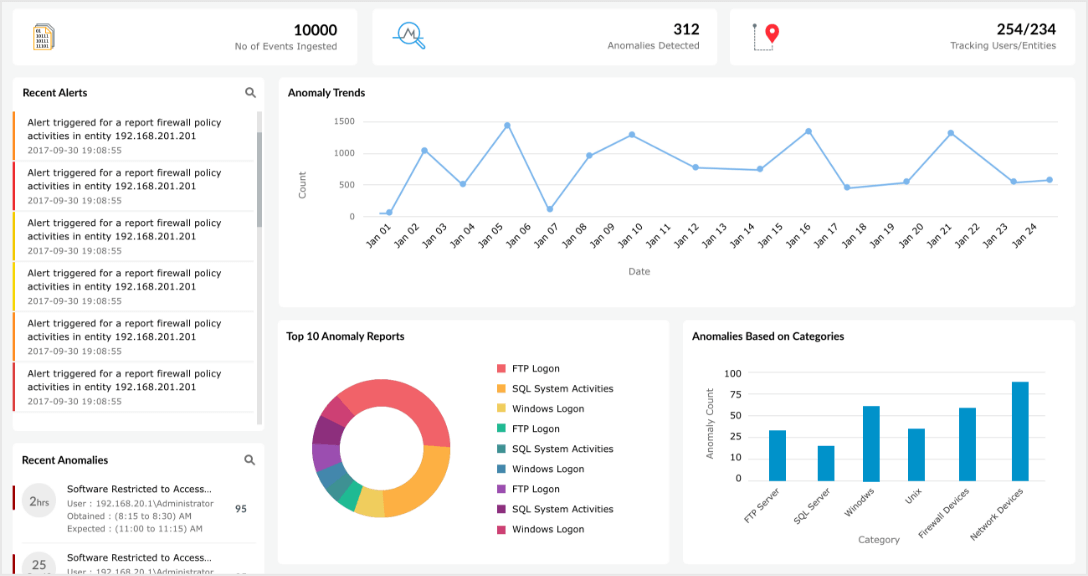
Threat intelligence
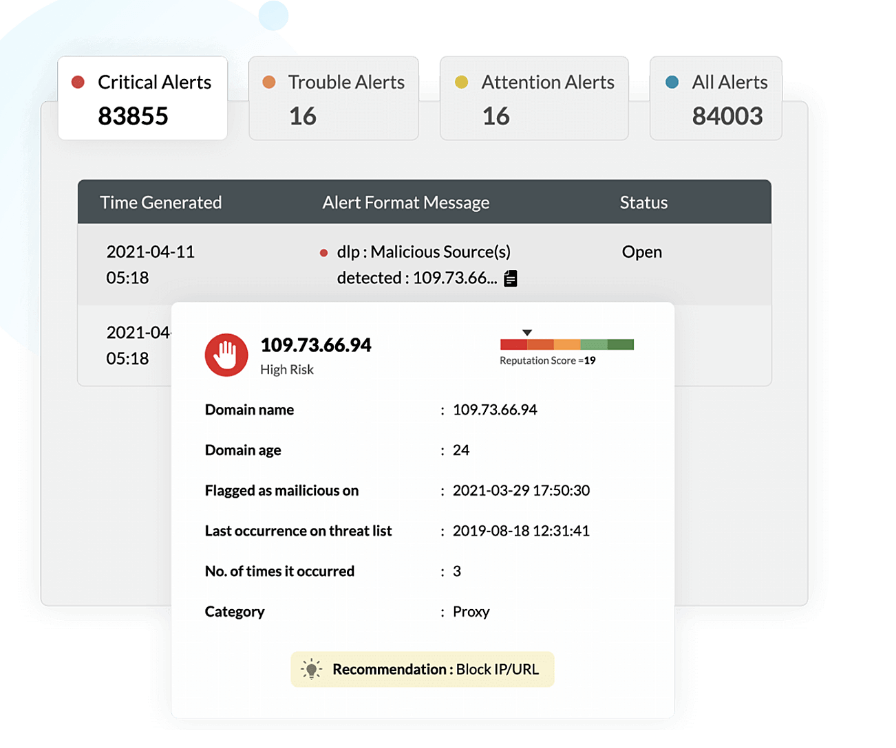
Log360's integration of threat intelligence revolutionizes DDoS attack defense. By tapping into a vast repository of known threat indicators, it identifies and blocks traffic from malicious sources.
Log360 detects unusual behavior or patterns that deviate from established norms. These are flagged as potential threats, not just spikes, ensuring precise threat identification. Swift, automated responses are triggered to mitigate potential damage. As the threat landscapes evolve, Log360 adapts by updating its intelligence database, providing continuous, up-to-date defense. Log360's threat intelligence ensures proactive, informed security measures against DDoS attacks.
- What are DoS and DDoS attacks?
- History of DoS and DDoS attacks
- Types of DoS attacks
- Types of DDoS attacks
- Attack flow
- Detection mechanism
- Best practices
- Detect and mitigate with Log360