Log360 combines both open-source and commercial threat feeds with over 600 million blocklisted IPs to monitor for botnets continuously.
Log360 also provides information on the location of the source domain, the ISP of the organization that owns the domain, etc.
Log360 allows you to easily detect botnet attacks with over 30 predefined attack rules. You can also create your own correlation rules with the custom correlation builder.
Log360 provides instant alerts through emails and SMS when a malicious IP interacts with your network.
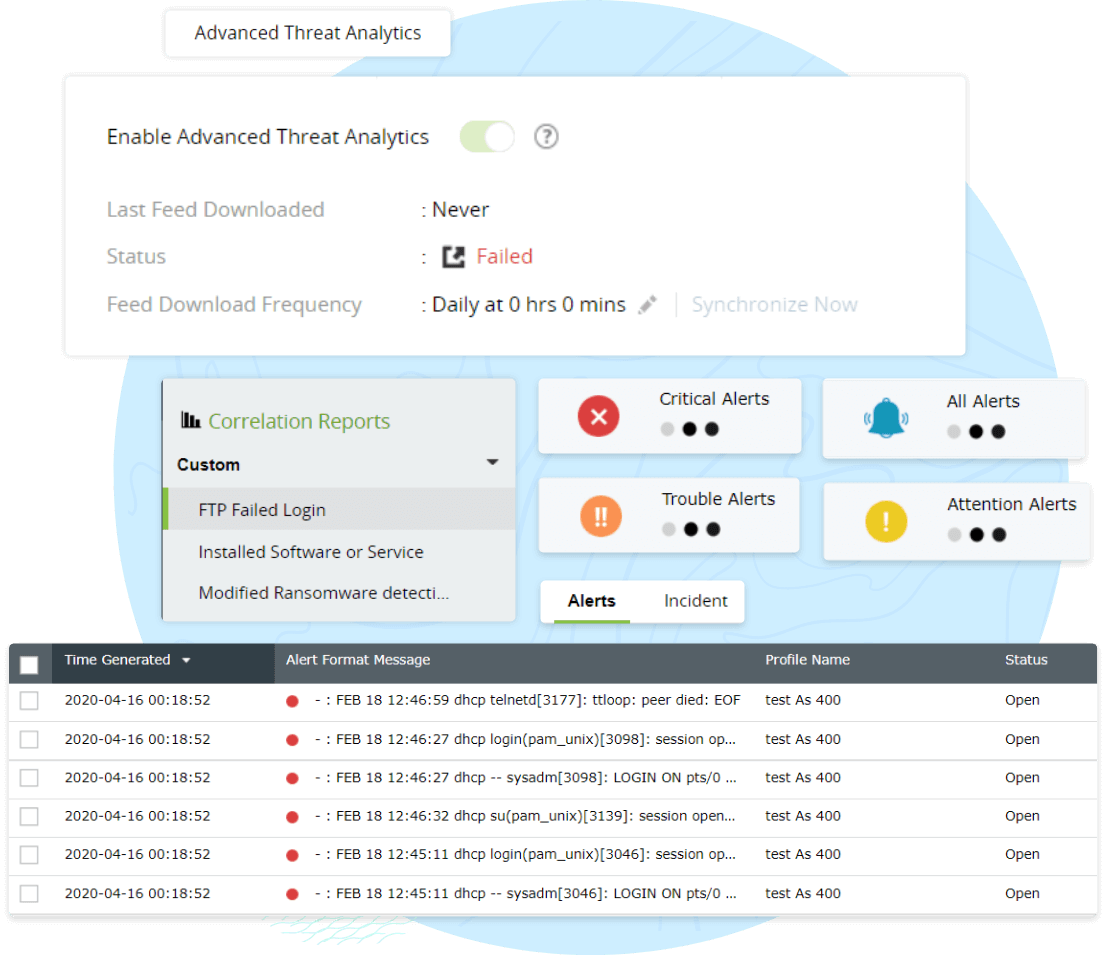
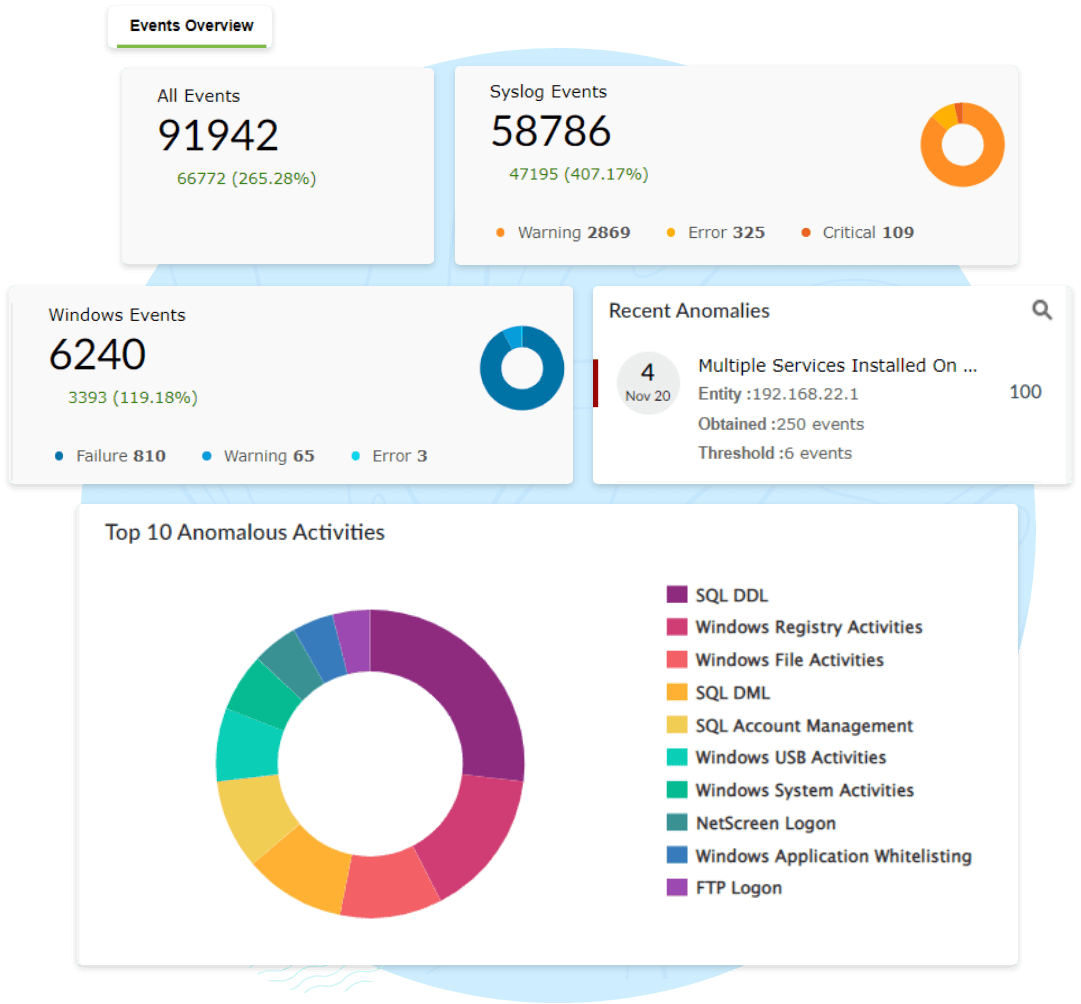
Log360’s incident dashboard sorts security incidents by priority and source, helping you keep track of each security incident from detection to resolution.
Log360 allows you to design custom incident workflows using a drag-and-drop interface. These workflows are triggered automatically when an alert is raised.
Log360’s built-in ticketing console automatically generates a ticket when an alert is triggered. You can keep track of the tickets created using the incident dashboard.
In addition to raising tickets in the built-in console, you can also integrate Log360 with external help desk software. Tickets can be assigned to an appropriate security admin in your organization for resolution.
Effortlessly comply with regulatory mandates, like PCI DSS, HIPAA, SOX, the GDPR, and the CCPA.
Learn MoreLeverage threat feeds to discover malicious IPs, domains, and URLs.
Learn MoreSpeed up incident mitigation by triaging security threats and automating incident response.
Learn MoreSpot anomalous behaviour with Log360’s UEBA module.
Learn MoreA botnet attack is a type of cyberattack that takes place when a group of devices connected to the internet are under the influence of a malicious attacker. The attacker uses these devices to launch large-scale phishing campaigns, DDoS attacks, or even exploitation of sensitive data.
Botnet attacks usually start when a cyberattacker gains unauthorized access to machines by injecting malware or trojans, or employing other social engineering tactics to gain access. After the initial access, the attackers use software to bring the machines under their control and launch large-scale cyberattacks.
Attackers use different tools and methods to carry out botnet attacks. Some of the most common attacks are: