- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
What is the DFARS?
DFARS sounds like military jargon, doesn't it? Well, you're not wrong. It stands for Defense Federal Acquisition Regulation Supplement and refers to the Department of Defense's additional security requirements, which go beyond standard government contracting regulations.
When you're working on defense projects, you're dealing with information that threat actors would love to get their hands on. Maybe it's technical specs for a new aircraft component or operational details about military inventory. The Department of Defense (DoD) figured out years ago that standard password policies weren't satisfactory anymore as too many contractors were getting hacked.
So they created what's known as Clause 252.204-7012. Sounds boring, right? But this little clause packs a punch. It's essentially the DoD's cybersecurity playbook for protecting something called Controlled Unclassified Information (CUI). Think of CUI as sensitive but not classified intel that won't end up on the evening news if leaked but could still cause real damage in the wrong hands.
The reality is straightforward. Poor cybersecurity will cost you contracts, but ensuring compliance keeps business flowing. And it all starts with strong password and authentication policies.
What are DFARS password requirements
The following table explains the password policy requirements of the DFARS and how ADSelfService Plus helps your organization comply with them.
| DFARS requirement | Requirement description | How ADSelfService Plus helps satisfy the requirement |
|---|---|---|
| Section 3.5.1
System user identification |
Identify system users, processes acting on behalf of users, and devices before allowing access to organizational systems. | With ADSelfService Plus, you can secure information system access by enabling adaptive MFA for endpoints, such as for machine logons, application logons, VPN logons, RDP logons, and OWA logons. It supports a wide range of multi-factor MFA methods, including biometrics, OTPs, and authenticator apps. |
| Section 3.5.2
Identity authentication |
Authenticate (or verify) the identities of users, processes, or devices as a prerequisite to allowing access to organizational systems. | ADSelfService Plus supports a wide range of MFA methods, including biometrics, OTPs, and authenticator apps. It ensures that only authenticated users and trusted devices can have access to organizational information systems. |
| Section 3.5.3
Multi-factor authentication |
Use multi factor authentication for local and network access to privileged accounts and for network access to non-privileged accounts. | ADSelfService Plus supports a wide range of MFA methods, including biometrics, OTPs, and authenticator apps. It ensures that only authenticated users and trusted devices can access organizational information systems. |
| Section 3.5.4
Replay-resistant authentication |
Employ replay-resistant authentication mechanisms for network access to privileged and non-privileged accounts. | ADSelfService Plus provides FIDO2 authentication, which is resistant to replay, phishing, and man-in-the-middle attacks. |
| Section 3.5.5
Identifier reuse prevention |
Prevent reuse of identifiers for a defined period. | ADSelfService Plus prevents a single user from having multiple concurrent active sessions for a defined period. |
| Section 3.5.6
Disable inactive identifiers |
Disable identifiers after a defined period of inactivity. | ADSelfService Plus provides a Restrict Users feature that allows administrators to automatically or manually disable user identifiers after a defined period of inactivity. The feature can target various stale account types, including inactive users, and can be configured to run on a scheduled basis to automatically block users who have been inactive for a specified number of days. |
| Section 3.5.7
Password complexity |
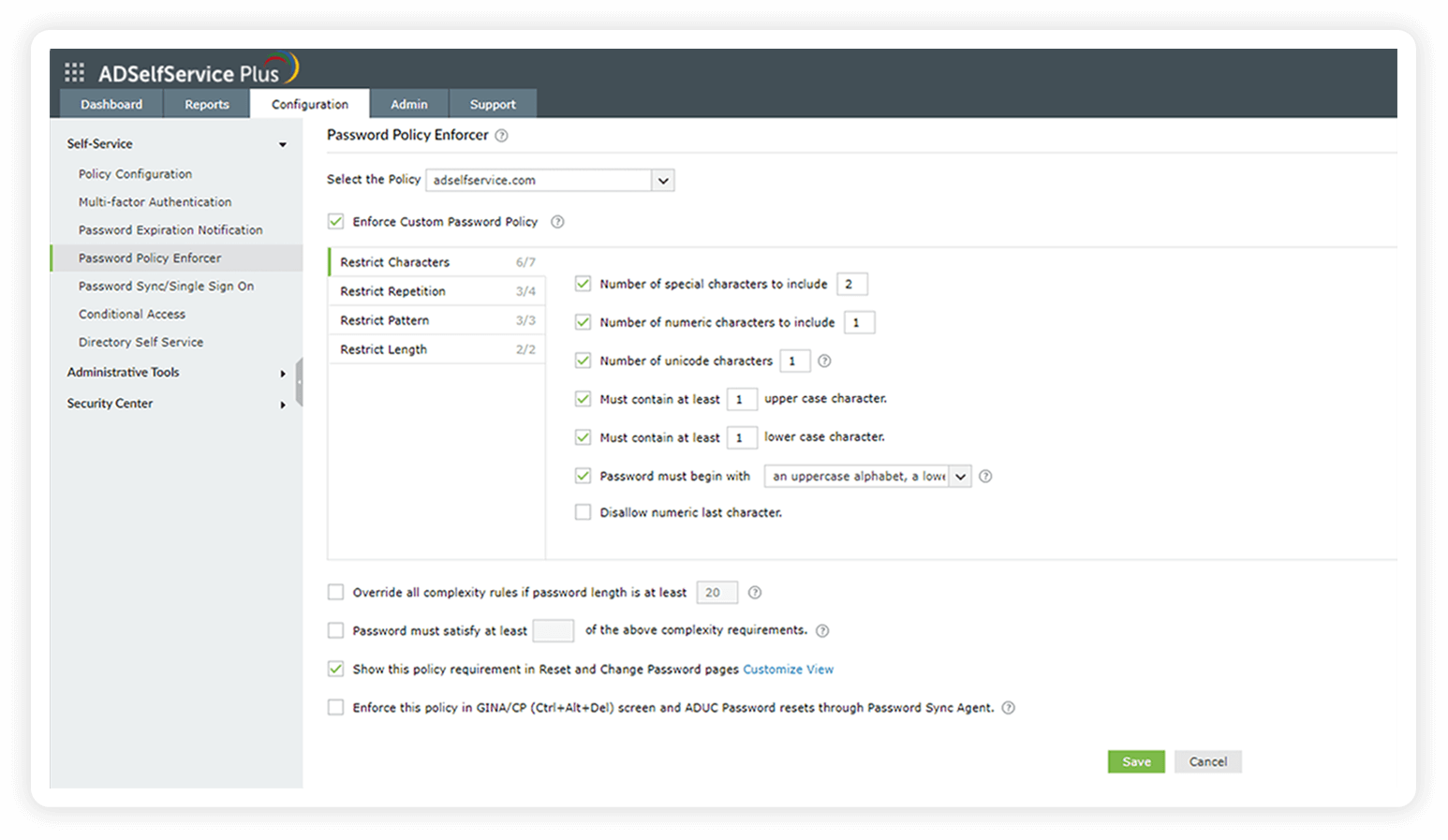
Enforce minimum password complexity requirements and require users to change characters when new passwords are created. | ADSelfService Plus addresses your compliance requirement for minimum password complexity and character changes through its Password Policy Enforcer. This feature allows you to define granular password rules, including required character sets (uppercase and lowercase letters, numbers, special characters), minimum length, and restrictions on character repetition and patterns. |
| Section 3.5.8
Password history |
Prohibit password reuse for a specified number of generations. | ADSelfService Plus allows you to specify the number of previous passwords that a user cannot repeat while choosing a new password. |
| Section 3.5.9
Temporary passwords |
Allow temporary password use for system logons with an immediate change to a permanent password. | ADSelfService Plus can enforce password changes during first login. Users logging in with a temporary password are immediately prompted to reset it through the self-service portal or login agent. |
| Section 3.5.10
Cryptographic protection |
Store and transmit only cryptographically-protected passwords. | ADSelfService Plus ensures all password storage and transmission uses strong encryption (AES-256) and integrates with AD's native cryptographic protection mechanisms for password security. |
| Section 3.5.11
Authentication feedback |
Obscure feedback of authentication information during the authentication process. | ADSelfService Plus does not display passwords by default when entered but gives users the option to view them, if required. |
Simplify DFARS compliance using ADselfService Plus
ADSelfService Plus' Password Policy Enforcer satisfies DFARS requirements and can be enforced for all or specific AD users based on their domain, OU, or group membership. With its adaptive MFA techniques, ADSelfService Plus ensures your organizational identities are effectively secured for a comprehensive Zero Trust environment.
- Mandate MFA for users: Secure user access to sensitive defense-related data by enabling adaptive MFA for endpoints, such as for machine logons, application logons, VPN logons, RDP logons, and OWA logons. Choose from a range of 20 different MFA authenticators, including FIDO passkeys and biometrics, to verify users' identities.
- Ensure password complexity: Ensure user passwords contain uppercase, lowercase, special, and numeric characters.
- Enforce password history: Ensure password strength by enforcing password history during native password resets in the Windows Active Directory Users and Computers (ADUC) console.
- Enforce secure first-time and temporary passwords: Require immediate password resets on first login to ensure temporary passwords don’t remain in circulation.
- Password Policy Enforcer
- MFA
Require users to create a new, unique password that has not been previously used.
Configure the minimum password length and require the inclusion of alpha-numeric characters in passwords.
Choose the minimum number of complexity requirements your users' passwords should satisfy as per your organization's security needs.
Require users to create a new, unique password that has not been previously used.
Configure the minimum password length and require the inclusion of alpha-numeric characters in passwords.
Choose the minimum number of complexity requirements your users' passwords should satisfy as per your organization's security needs.
Choose from a plethora of different authenticators to verify your users' identities.
Secure all endpoints in your network using MFA.
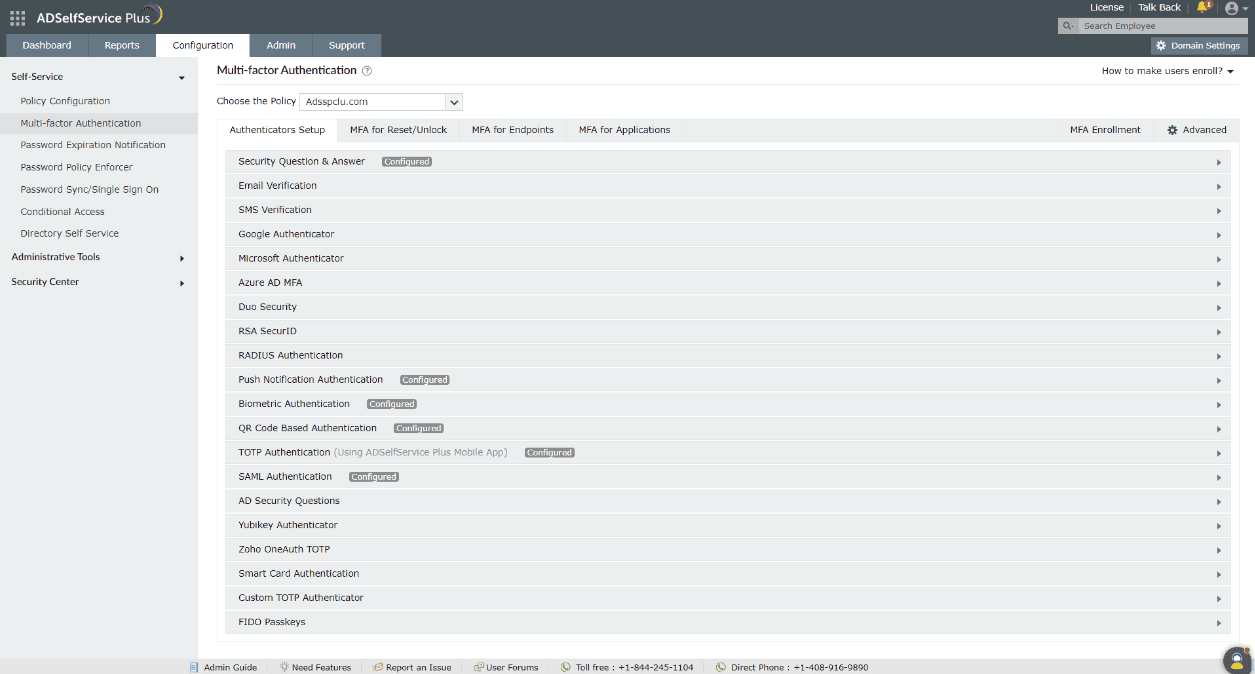
Choose from a plethora of different authenticators to verify your users' identities.
Secure all endpoints in your network using MFA.
Highlights of ADSelfService Plus
Password self-service
Eliminate lengthy help desk calls for Windows Active Directory users by empowering them with self-service password reset and account unlock capabilities.
One identity with single sign-on
Gain seamless one-click access to more than 100 cloud applications. With enterprise single sign-on, users can access all their cloud applications using their Windows Active Directory credentials.
Password synchronization
Synchronize Windows Active Directory user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
MFA
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
Password and account expiration notifications
Notify Windows Active Directory users of their impending password and account expiration via email and SMS notifications.
Password policy enforcer
Strong passwords resist various hacking threats. Enforce Windows Active Directory users to adhere to compliant passwords by displaying password complexity requirements.










