How to enable Active Directory fine-grained password policy
Overview
This article explains how to enable fine-grained password policies (FGPP) in Active Directory groups and introduces a more advanced alternative to it: ManageEngine ADSelfService Plus' Password Policy Enforcer.
What is an Active Directory fine-grained password policy?
Active Directory comes bundled with a default password policy. This traditional password policy, however, cannot be customized for a specific set of users, groups, or OUs because it is only applicable to the entire domain. To overcome this significant drawback, Active Directory FGPP was introduced in Windows Server 2008. This allows granular password policies to be tailored to different users and groups within the domain.
The functionality of AD fine-grained password policy
- To use an FGPP policy, the domain must operate at a functional level of Windows Server 2008 and above.
- Implementing FGPP in Active Directory requires creating multiple Password Settings Objects (PSOs) inside the domain. Password and account lockout policies can be customized in each PSO.
- Domain admins or users with delegated permissions can create and assign PSOs in the Active Directory Administrative Center or using PowerShell. For detailed steps, visit this webpage.
- FGPP PSOs are applicable only to user objects and global security groups.
- When an FGPP is applied to a set of users or global security groups in a domain, the default domain password policy is no longer applicable to those objects.
- FGPPs can be used in cases where user accounts accessing sensitive data or synchronized with multiple confidential data sources require stricter password and account lockout policies.
Steps to enable fine-grained password policy in Active Directory
- Open Active Directory Administrative Center (ADAC).
- Go to Manage > Add Navigation Nodes. In the Add Navigation Nodes dialog box, select the required domain, then click OK.
- In the left-side pane, click the System container and open the Password Settings Container.
- In the Tasks section, click New, and then select Password Settings.
- In the page that appears, enter the necessary details to create a new Password Settings object. The Name and Precedence fields are mandatory.
Note: When configuring multiple policies, ensure proper FGPP precedence settings to avoid conflicts. The FGPP precedence value determines which policy takes effect when a user is subject to multiple password policies—lower precedence numbers have higher priority.
- Select your preferred settings:
- Minimum Password Length
- Password history
- Complexity Required
- Store Passwords with reversible encryption
- Protect from Accidental Deletion
- Minimum Password Age
- Maximum Password Age
- Lockout Policy
- Under Directly Applies To, click Add, enter the name of the group to which the FGPP policy should apply, and click OK.
- Review your settings and click OK to create the policy.
Steps to enable granular password policies
ADSelfService Plus offers the Password Policy Enforcer feature to help employees in your organization set NIST-compliant, sophisticated passwords that are almost impossible to crack. With ADSelfService Plus, you can enforce custom password policies that seamlessly integrate with the existing FGPP Active Directory configuration, providing more granular control. To enable them:
- Log in to ADSelfService Plus as an administrator.
- Navigate to Configuration > Self-Service > Password Policy Enforcer.
- Select the policy to which you want to apply the password policy rules.
- Enable Enforce Custom Password Policy.
- Define the complexity requirements for new passwords by checking the necessary boxes:
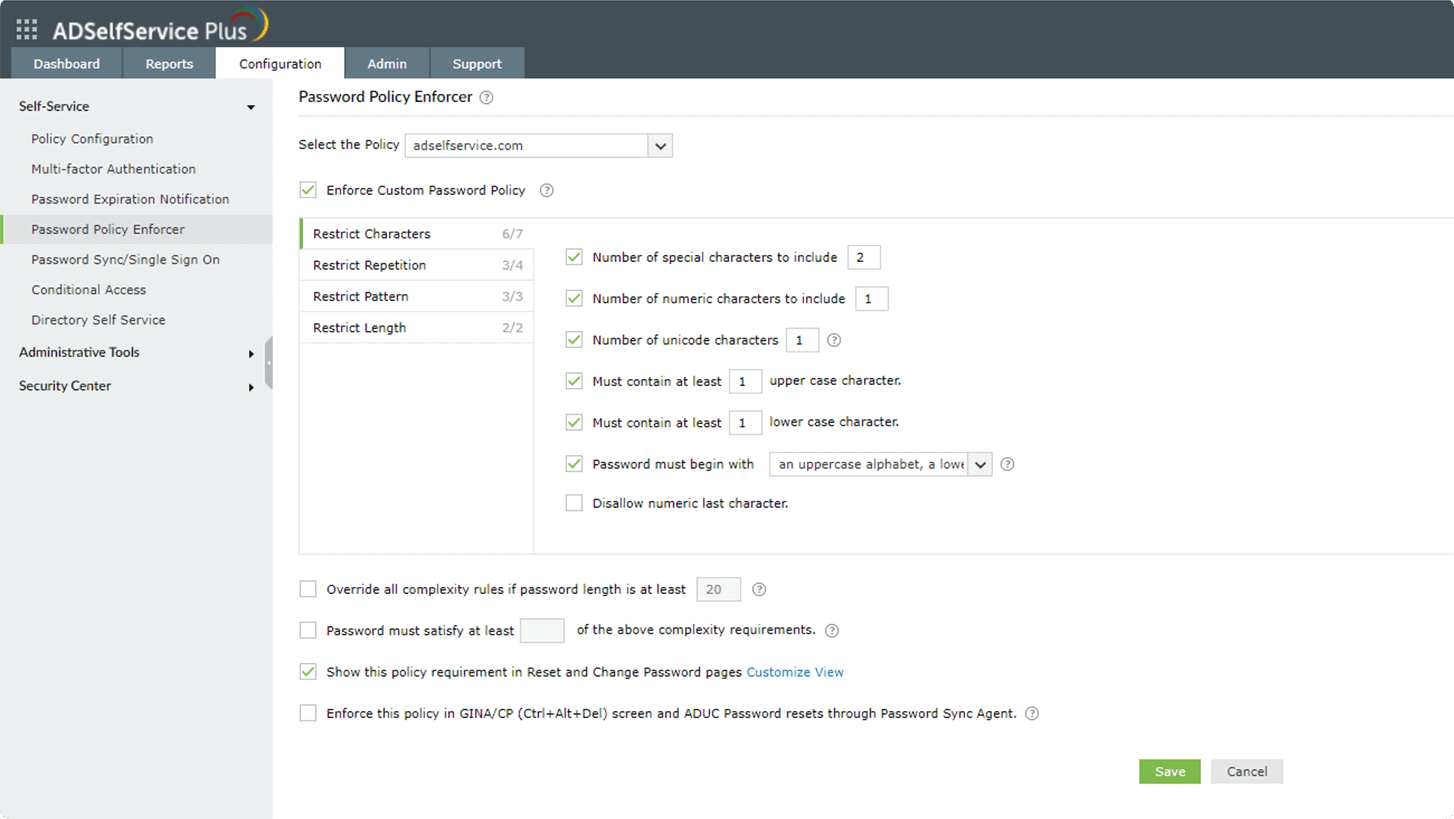
- Restrict characters: These password policy settings include mandating the number of special, numeric, and Unicode characters. You can also set the type of character with which the password must begin.
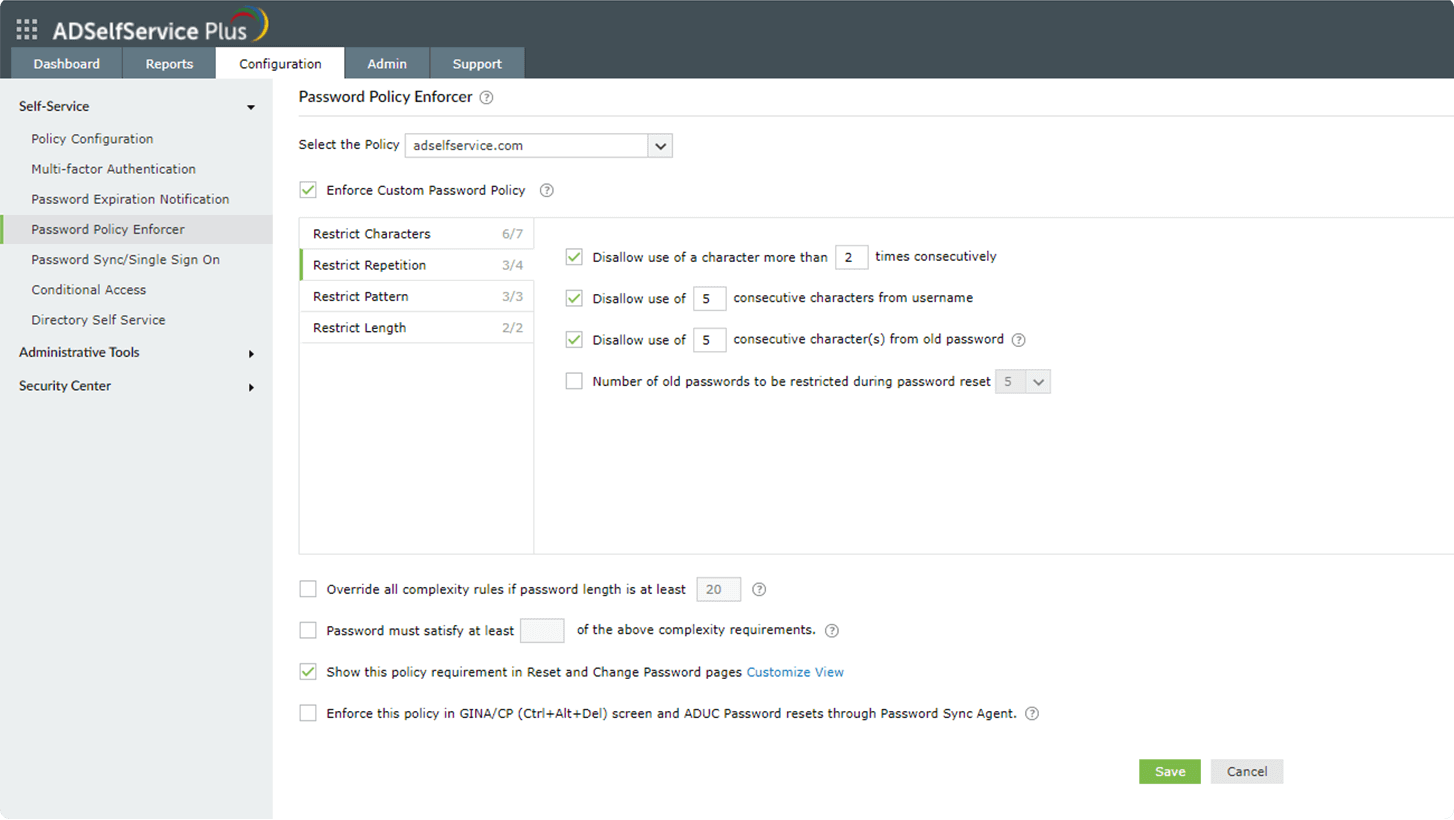
- Restrict repetition: These settings restrict the use of consecutive characters from usernames or previous passwords. Consecutive repetition of the same character can also be restricted.
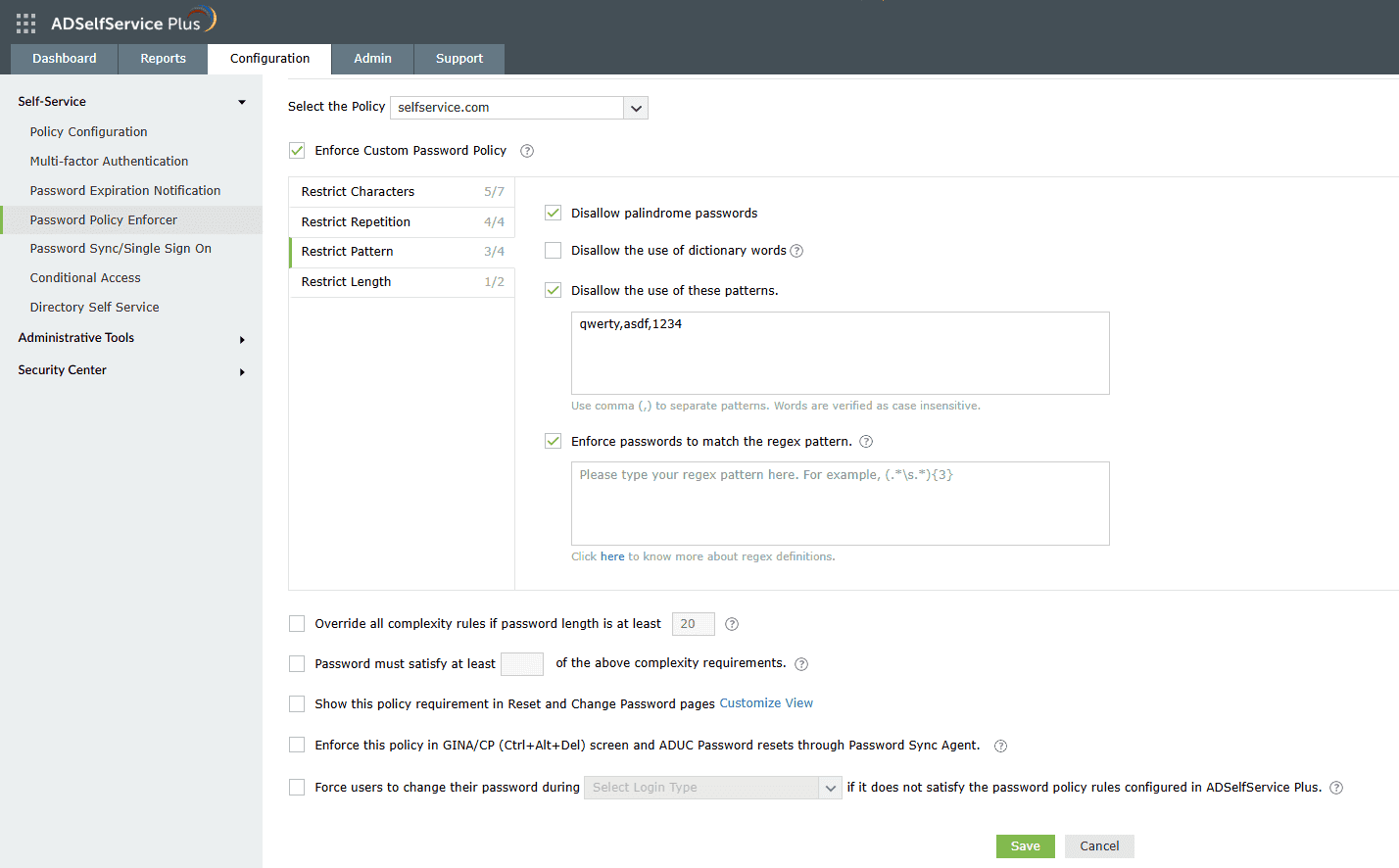
- Restrict pattern: The settings under this tab restrict the use of custom dictionary words, patterns, and palindromes in passwords. You can configure custom regex patterns that your users' passwords must meet, allowing you to define precise password requirements for your organization.
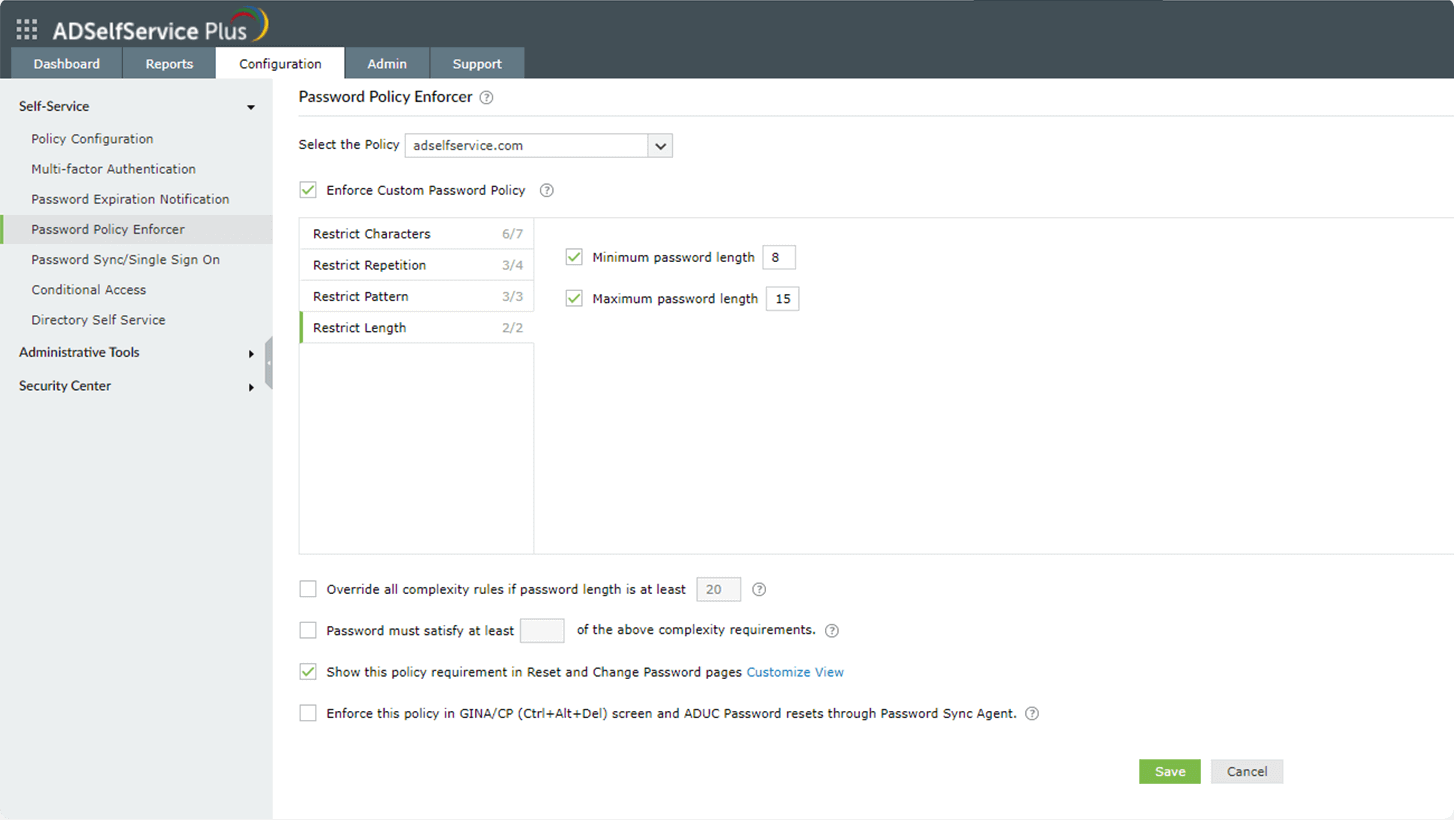
- Restrict length: These rules let you set both a minimum and maximum number of characters for the password.
- You can also configure the following settings for your custom password policy.
- Override all complexity rules if password length is at least ___: Enable this option to bypass all complexity rules if the password meets or exceeds the specified length.
- Password must satisfy at least ___ of the above complexity requirements: Ensure the password complies with a minimum number of the specified complexity rules.
- Show this policy requirement in Reset and Change Password pages: Display the rules of your custom password policy on the password reset and change password pages, replacing the default domain password policy.
- Enforce this policy in GINA/CP (Ctrl+Alt+Del) screen and ADUC Password resets through Password Sync Agent: Apply the custom password policy configured in ADSelfService Plus during password reset operation via the ADUC interface and during password change on the Ctrl+Alt+Del screen.
- Click Save to finish the configuration.
Limitations of Active Directory fine-grained password policy
- FGPPs do not do justice to the term "fine-grained" since they are not applicable to OUs.
- They are not deployed using Group Policy Objects and take effect for users only based on their group memberships.
- Applying and managing multiple FGPPs can be a challenging task due to the complications involved in keeping track of the assigned policies.
- Because of their limited password and account lockout settings, FGPPs cannot meet password compliance regulations such as the NIST password standards.
- FGPPs cannot prevent sophisticated, modern password attacks like dictionary and brute-force attacks.
Benefits of granular password policy
- Helps users pick strong passwords by enforcing strong password rules and providing real-time feedback using the Password Strength Analyzer.
- Encourages passphrases by revoking password policy requirements when the passphrase exceeds a certain length.
- Implements granular password policies for users belonging to specific domains, OUs, and groups, helping organizations implement truly fine-grained password policies.
- Exposes breached passwords during password creation, empowering users to employ secure passwords that are insusceptible to account takeover.
- Enforces password policies universally for multiple enterprise applications by way of password synchronization.
- Meets compliance standards for regulations such as NIST, the PCI DSS, CJIS, HIPAA, and the GDPR.
Highlights of ADSelfService Plus
Allow Active Directory users to self-service their password resets and account unlock tasks, freeing them from lengthy help desk calls.
Get seamless one-click access to 100+ cloud applications. With enterprise single sign-on, users can access all their cloud applications using their Active Directory credentials.
Intimate Active Directory users of their impending password and account expiry via email and SMS notifications.
Synchronize Windows Active Directory user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Strong passwords resist various hacking threats. Enforce Active Directory users to adhere to compliant passwords by displaying password complexity requirements.
Enable Active Directory users to update their latest information themselves. Quick search features help admins scout for information using search keys like contact numbers.



