How we can help
Explore ManageEngine Log360 with a 30-day free trial
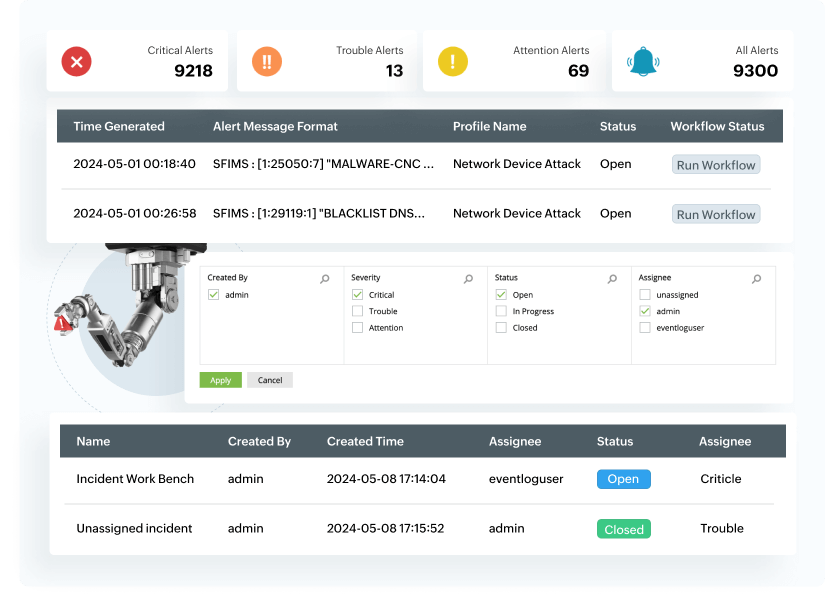
Your SOCs command center for seeing threats, not noise
ManageEngine Log360:
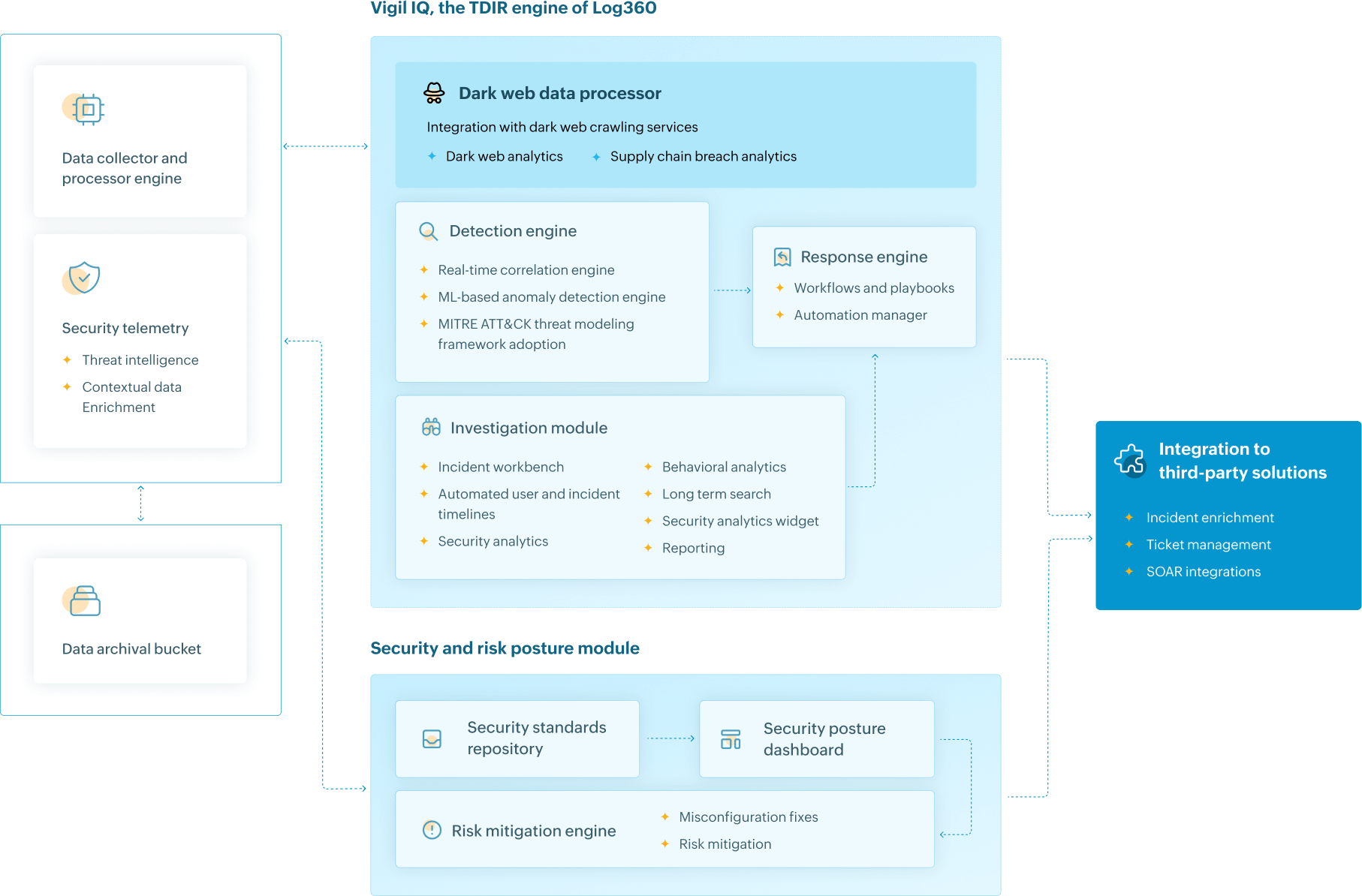
Vigil IQ—Log360's automated threat detection, investigation, and response (TDIR) module—equips your security operations center (SOC) to proactively combat threats, improve efficiency, and maximize security posture. It addresses the core challenges faced by SOCs with:
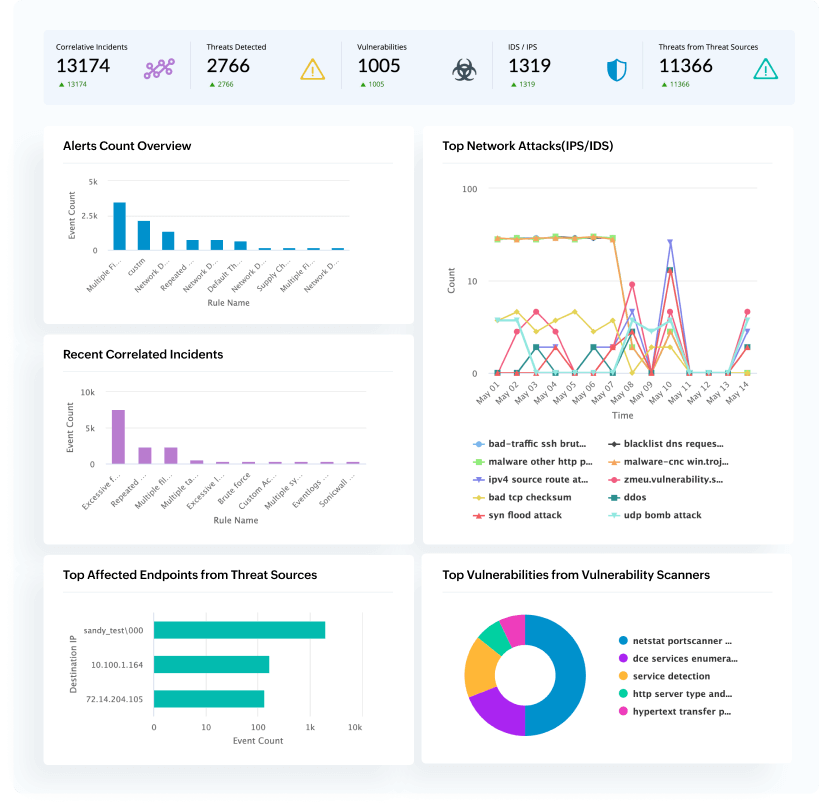
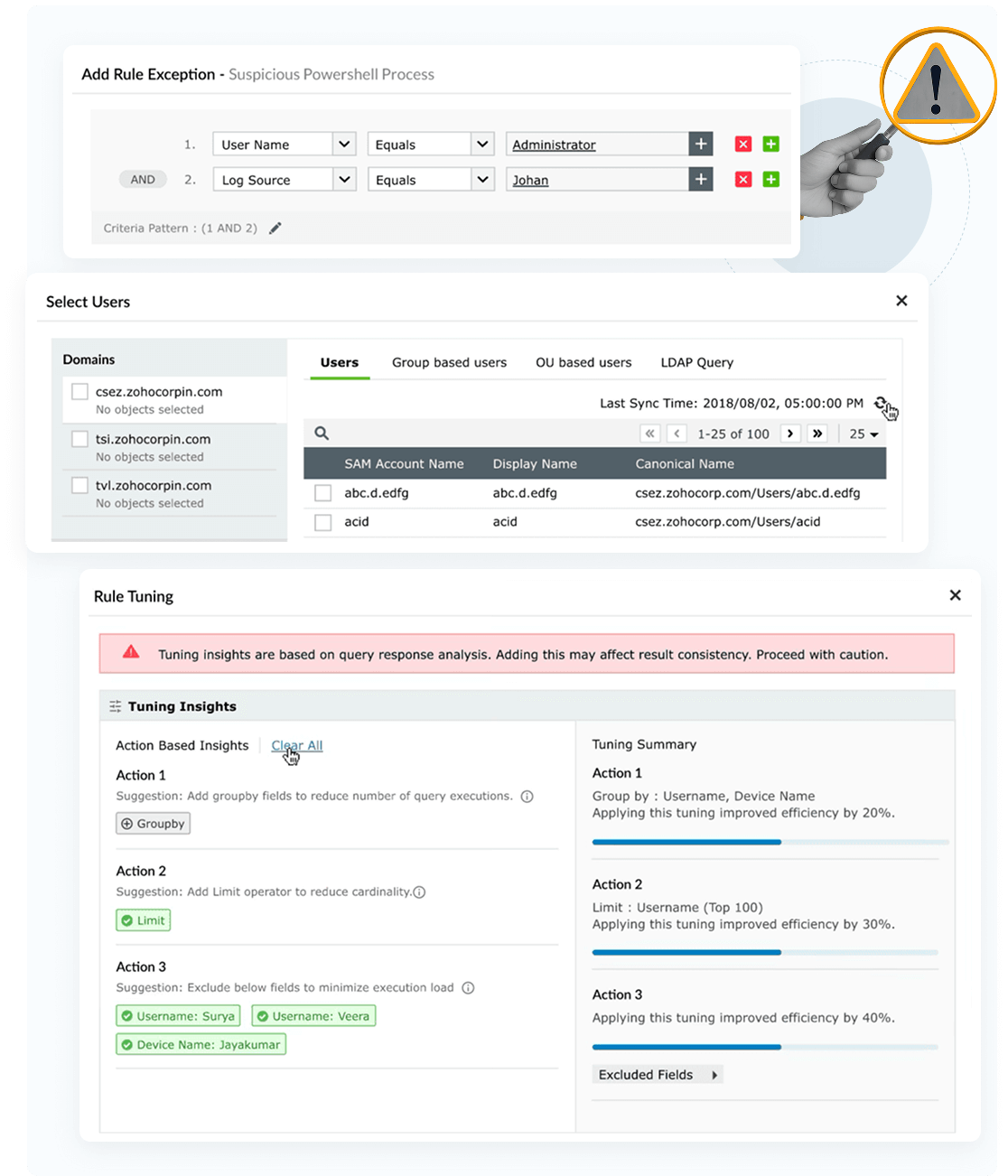
Transform your signal-to-noise ratio with intelligent detection management. Log360's enhanced precision tuning tackles alert fatigue and reduces false positives while maintaining complete threat coverage. Focus on real threats, not noise.
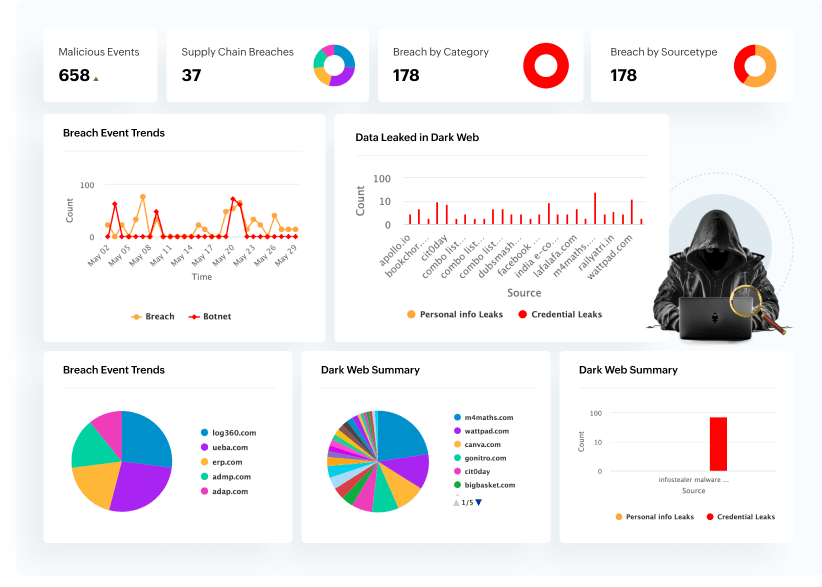
Stop data breaches from malicious outsiders—even before they start—with proactive dark web monitoring. Hunt down credentials and personal data leaked on the dark web. Get actionable insights on the dark web breaches and supply chain credential leaks before attackers exploit them, keeping your enterprise a step ahead of its adversaries. Take a guided tour of dark web monitoring capabilities.
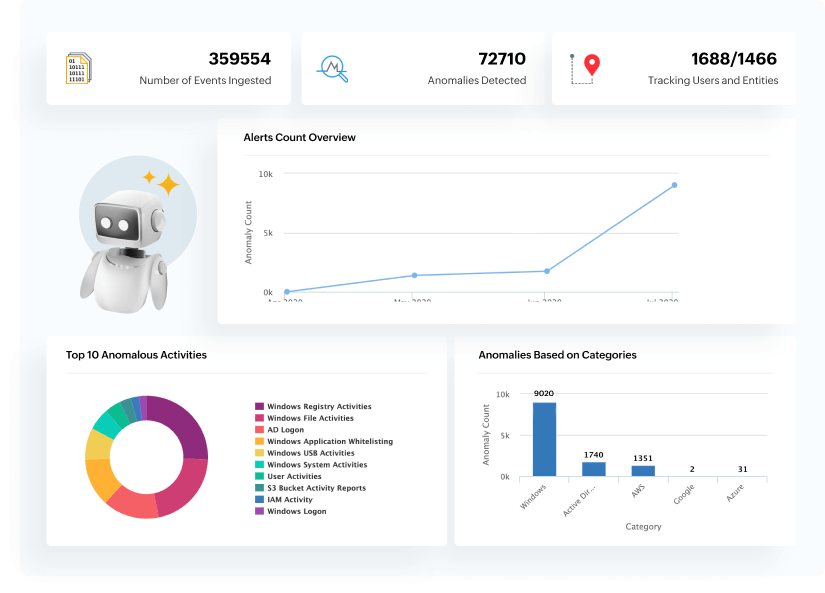
Learn morePinpoint anomalies that signal potential user-based threats with AI-driven behavior analytics that continuously adapts and analyzes user activities. The user entity and behavioral analytics (UEBA) comes with integrated risk management to prioritize suspicious activity, detecting both slow-burning threats and complex attack patterns. User identity mapping and dynamic peer grouping refine anomaly accuracy with user context.
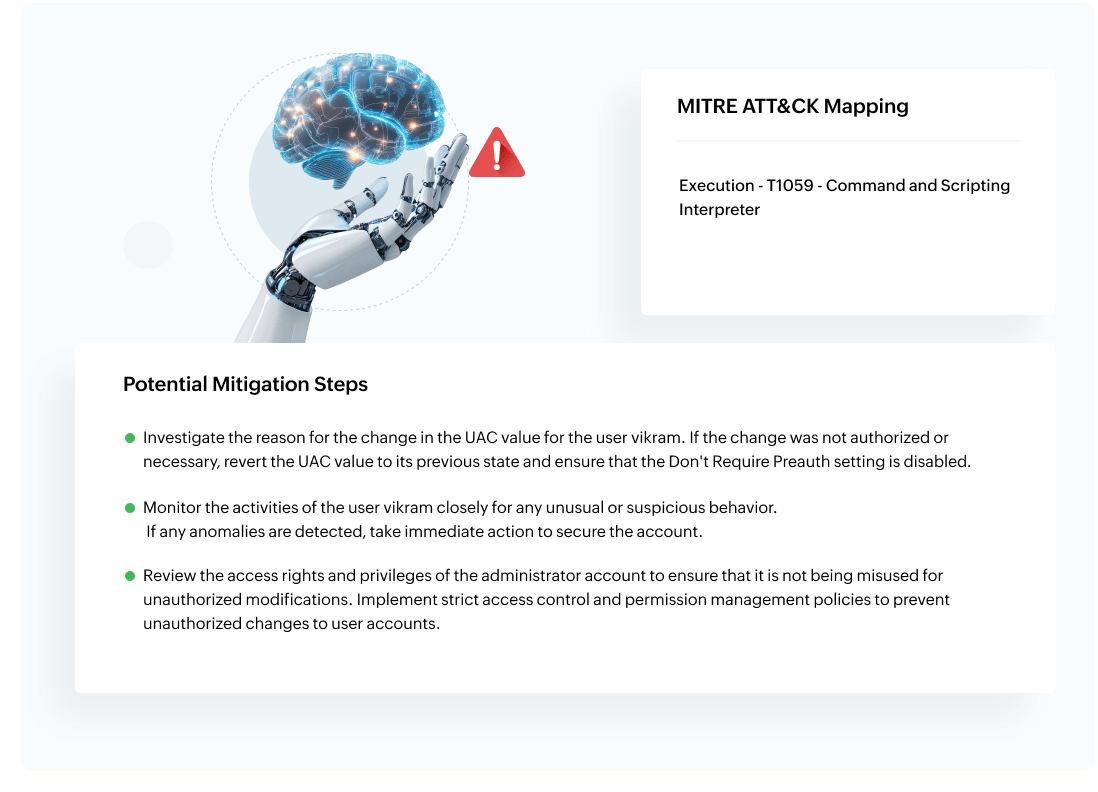
Learn moreZia Insights uses generative AI to simplify security investigations. It provides human-readable summaries of logs, alerts, and incidents, maps events to MITRE ATT&CK® techniques, visualizes attack timelines, and offers remediation guidance. Zia Insights helps SOC teams reduce manual effort, improve response time, and gain deeper threat context.
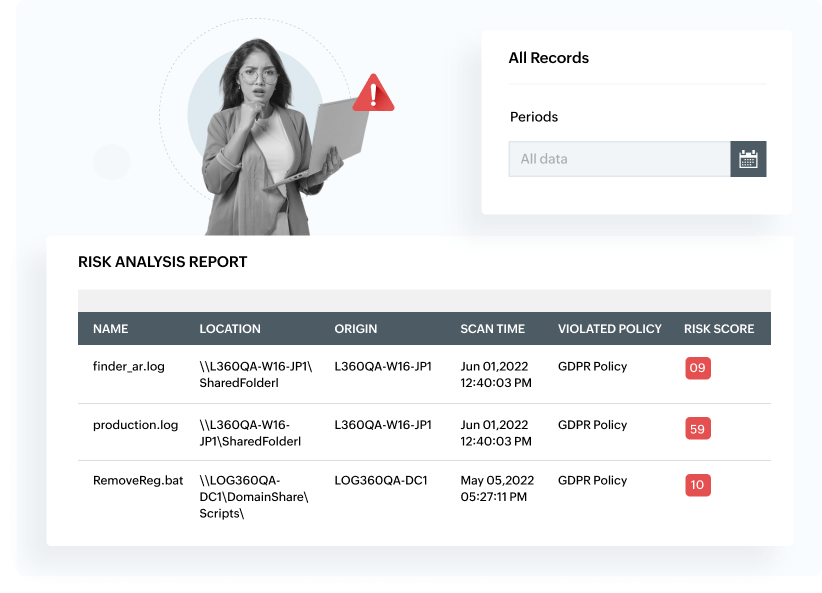
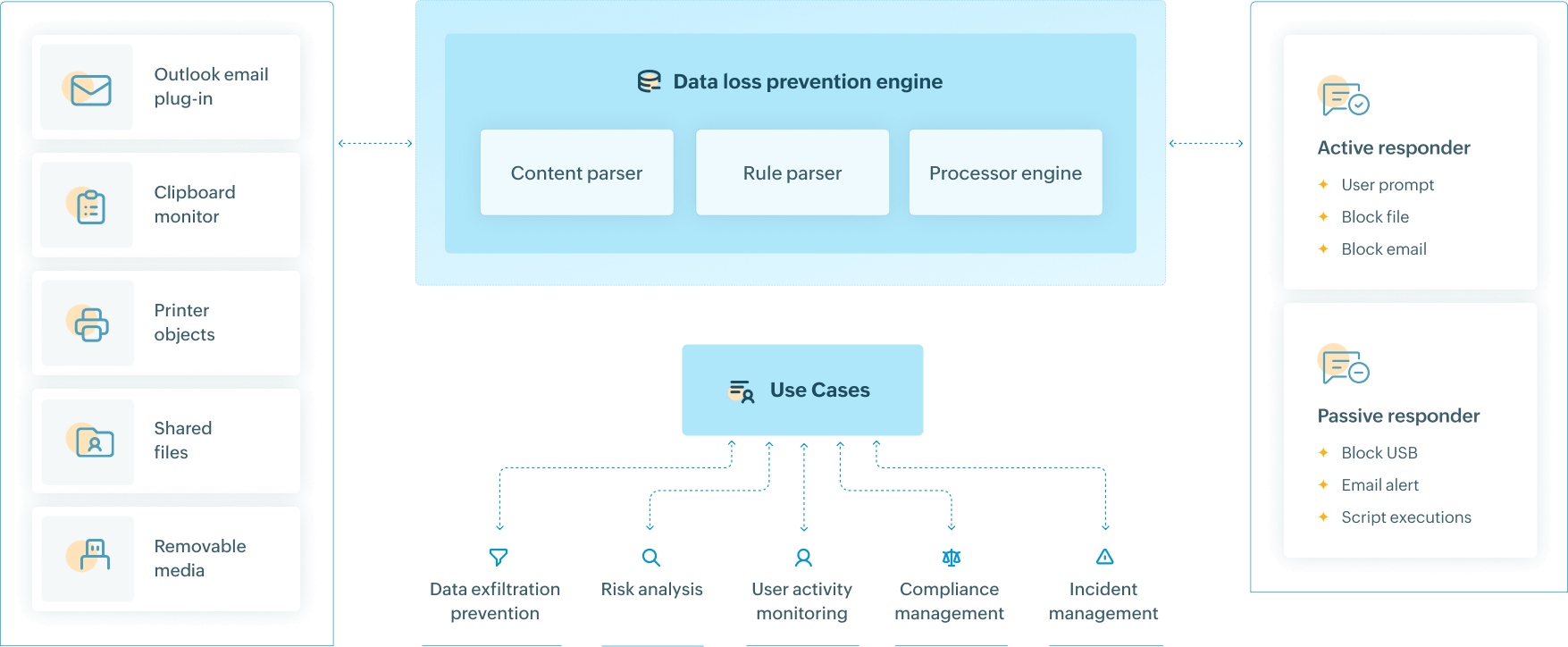
Learn moreDiscover sensitive data residing in your network with automated e-discovery. Customize discovery policies to scan your network for specific confidential data discovery. Classify sensitive data based on the risk associated with them and the type of personal information they contain to optimize the access control and security required to be implemented for the specified files. With integrity monitoring, you'll ensure the sensitive files residing on the Windows platform and databases such as SQL stay secured from accidental or intentional modifications. Prevent data exfiltration through AI-powered anomaly detection.
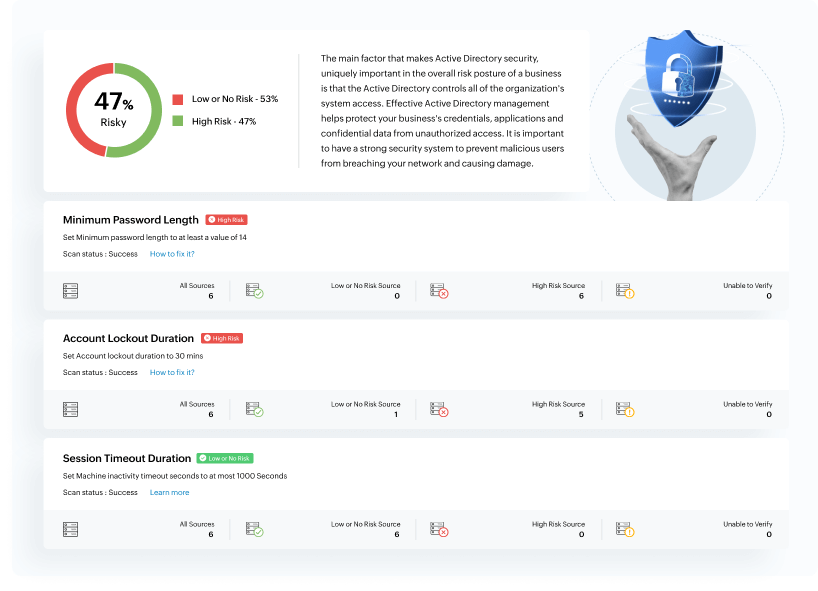
Learn moreGain a comprehensive view of potential security weaknesses in your critical environments like Active Directory and MS SQL servers. Log360's security and risk posture assessment identifies misconfigurations and security gaps, providing deeper insights into your network's risk posture and attack surface exposures, which empowers you to prioritize and address potential security issues before they escalate into incidents.
Learn moreSimplify security operations by automating repetitive tasks like incident assignment, data enrichment, and investigation workflows. This frees your security analysts to focus on high-impact threats. Log360 SOAR empowers you to orchestrate complex workflows with pre-defined playbooks, enabling swift threat neutralization and minimizing damage. Furthermore, seamless integration with your existing security landscape fosters a collaborative response environment, ensuring a unified defense against cyber threats.
Learn moreLog360 gathers a lot of information and puts it in a very easy-to-read format.
Farmers Trust & Savings Bank
We are pleased to have this log management and network security solution that comes with real-time log collection, correlation, analysis and achieving capabilities. We use the predefined Alert profiles and correlation rules to cover our requirement basically.
It is a powerful tool with simple deployment and easy to manage
ManageEngine Log30 has gained more traction in our environment with its log collection and retention functionality. We are able to set and get all compliance based alerts and set the schedule reports as needed.
Discover how Log360 strengthens security operations and data security with threat detection, real-time investigation, and automated incident response.
Collect, parse, analyze, store, and search log data efficiently from a single console, with a rapid ingestion rate and high-speed search purpose-built for security and compliance use cases. Log360 comes with over 750 pre-built log parsers and an option to parse and analyze any human-readable log with its custom log parser. The solution enriches log data from threat intelligence feeds, location, user-identity mapping, and dynamic peer grouping for security monitoring.
Learn more›Gain unparalleled visibility into your entire IT landscape with Log360. Effortlessly monitor critical infrastructure—from Active Directory and database servers to network devices, applications, endpoints, and even cloud platforms like AWS, Azure, GCP, and Salesforce. Log360 ingests data from every corner of your environment, transforming it into actionable insights.
Learn more›Start detecting threats immediately with our cloud-delivered detection library. Every rule is MITRE ATT&CK-mapped and categorized for easy deployment. Deploy standard rules for known attack patterns and policy violations, ML-powered anomaly rules to catch behavioral abnormalities, advanced correlation for multi-stage attack campaigns, and threat intel matches updated in real-time from global feeds.
Learn more›AI-powered smart thresholds that drastically reduce alert fatigue by dynamically adapting to changing user and system behaviors. The dual-layered system incorporates both accuracy and precision in threat detection, focusing only on the real threats by reducing false positives.
Learn more›Protect from external threats with dynamically-updated threat intelligence data that includes over 1,000 million threat feeds from our trusted technology partners. Boost threat detection accuracy through IoCs, IP/URL/domain reputation, and dark web crawling. Get contextual information—such as geolocation, threat reputation score, and more—to expedite threat investigation and find real threats.
Learn more›Playbooks streamline routine alert resolution and threat neutralization, freeing analysts for complex tasks. The seamless ITSM integration automates case management, saving valuable time. Curated threat feeds are automatically correlated with context-rich network event correlation to minimize false positives, empowering you to focus on real threats.
Learn more›Centralize data, streamline compliance, and scale effortlessly with a SIEM that is tailored to your needs.
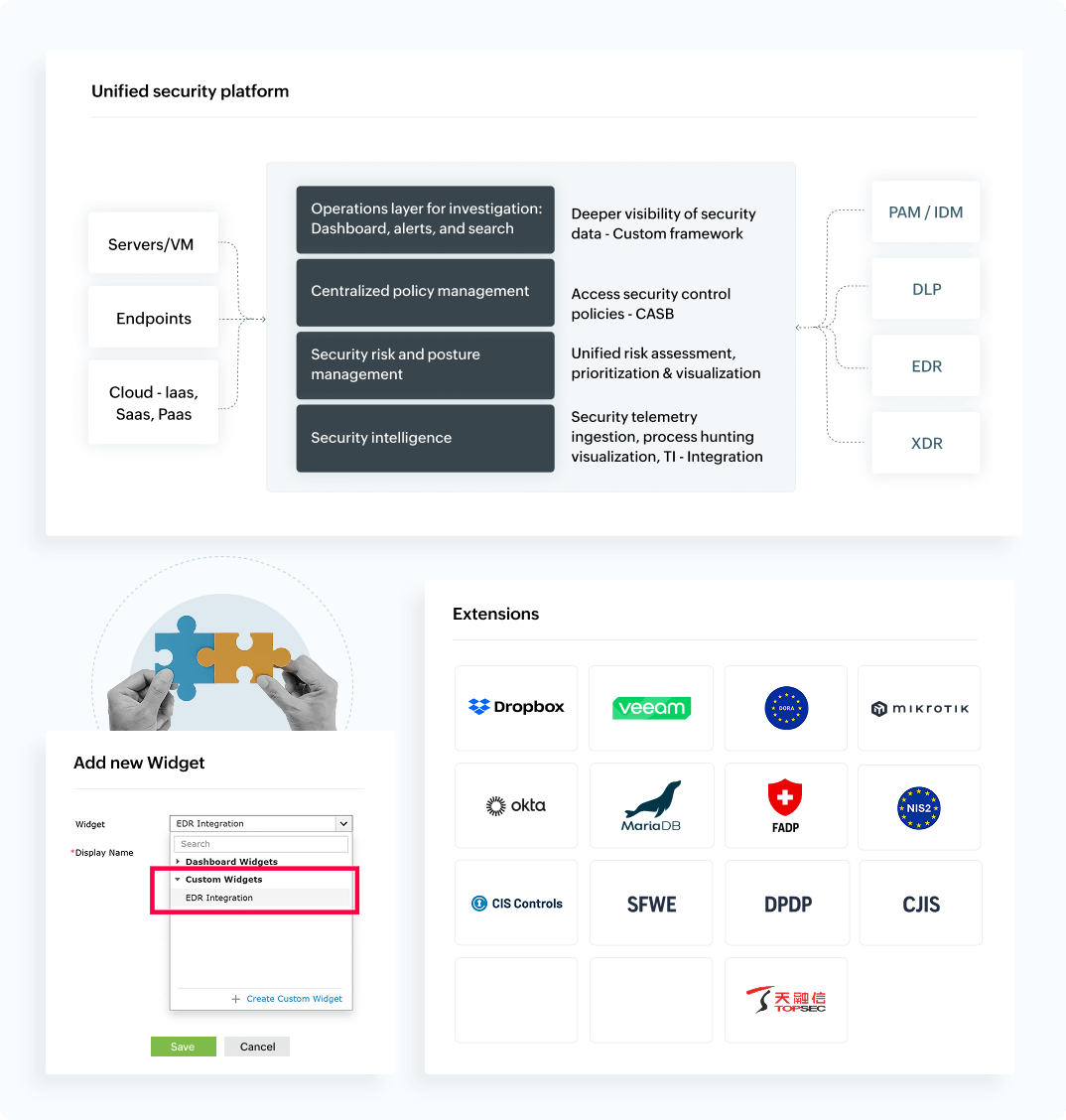
Explore all featuresConsolidate all your security data points into a single, intuitive console. Log360 acts as your security hub, streamlining threat investigations and delivering a seamless interface that empowers you to make data-driven security decisions with confidence, keeping your enterprise a step ahead of cyber threats.
Log360 empowers you to navigate compliance with confidence. Leverage over 30 pre-built audit templates for popular mandates, receive real-time violation alerts, and customize profiles for your internal security policies.
Embrace the agility and scalability of a cloud-based SIEM deployment with Log360. Eliminate the need for upfront hardware investment and enjoy effortless scaling to accommodate growing data volumes. Log360's high-speed event processing engine ensures real-time analysis, empowering you to detect and respond to threats faster—a critical advantage in today's dynamic security landscape.
Tailor core modules—such as security analytics, alerting engine, detection rules, and anomaly models—to match your industry, business goals, and security needs. The customization wizards for correlation rule building, report generation, alert criteria mapper, anomaly modeling, and audit-report generation enables you to optimally fine-tune the solution's performance.
Secure financial data from breaches, detect financial fraud, and be compliant with the PCI DSS.
Learn moreProtect patient health information and be compliant with the HIPAA.
Learn moreNo gaps and no breaches. Secure critical infrastructure and avoid data breaches.
Learn moreProtect against ransomware, PII thefts, and secure your network.
Learn moreEnsure your business's security and compliance with Log360. Begin your journey to better security management.