Ransomware attacks are a hacker favorite, and so is demanding ransom in cryptocurrencies. In fact, security experts have been researching if the increasing popularity of ransomware can be attributed to cryptocurrency and vice versa. According to an HSGAC report, the use of cryptocurrency has further enabled ransomware attacks, and attackers are increasingly targeting hospitals, schools, government agencies, and other critical infrastructure.
To help you gain an in-depth understanding of the role of cryptocurrency in ransomware, in this blog, we will cover the following topics:
A ransomware attack is a cyberattack in which threat actors deploy malware to encrypt the data of the victim organization, and demand a ransom in exchange for decrypting that data. Attackers do this by exploiting vulnerabilities in the organization's network to gain entry. They then elevate privileges and move laterally until they gain access to an account with high privileges to carry out their attack. To increase their chances of being paid, attackers may design the ransomware to hunt for and destroy backups. Since these attacks involve the use of encryption algorithms, this malware is also called crypto ransomware. Wannacry, Conti, and BlackCat are few popular examples of crypto ransomware. Some attackers take it a notch further and perform cryptojacking using the victim's device (illegal mining of cryptocurrencies) after encrypting their data.
A cryptocurrency is a digital currency created for use over the internet. It's built based on blockchain technology and encrypted using cryptography. The first cryptocurrency, Bitcoin, was created in 2009. However, as of July 2023, over 26,140 cryptocurrencies, such as Monero, Ethereum, and Tether exist. In Figure 1, you'll see some of the top cryptocurrencies with a huge market capitalization.
 Figure 1: Some of the top cryptocurrencies in terms of market capitalization.
Figure 1: Some of the top cryptocurrencies in terms of market capitalization.
To understand blockchain, you should first know what a block is.
A block refers to a storage unit that stores and encrypts cryptocurrency transaction records. Each block contains details regarding the sender, receiver, and the number of transacted coins. Blocks also contain two cryptographic hashes: one indicates the block's own hash, and the other is the hash of the previous block.
Blockchain refers to a set of unique blocks that are cryptographically linked to one another. The blocks in a blockchain are stacked on top of one another, with the first (genesis) block at the bottom of the vertical stack. Blockchains facilitate the use of a decentralized and peer-to-peer network to secure and store cryptocurrency transactions. These transactions are digitally timestamped to prevent backdating and double-spending.
Attackers prefer receiving cryptocurrency as the ransom payment for the following reasons:
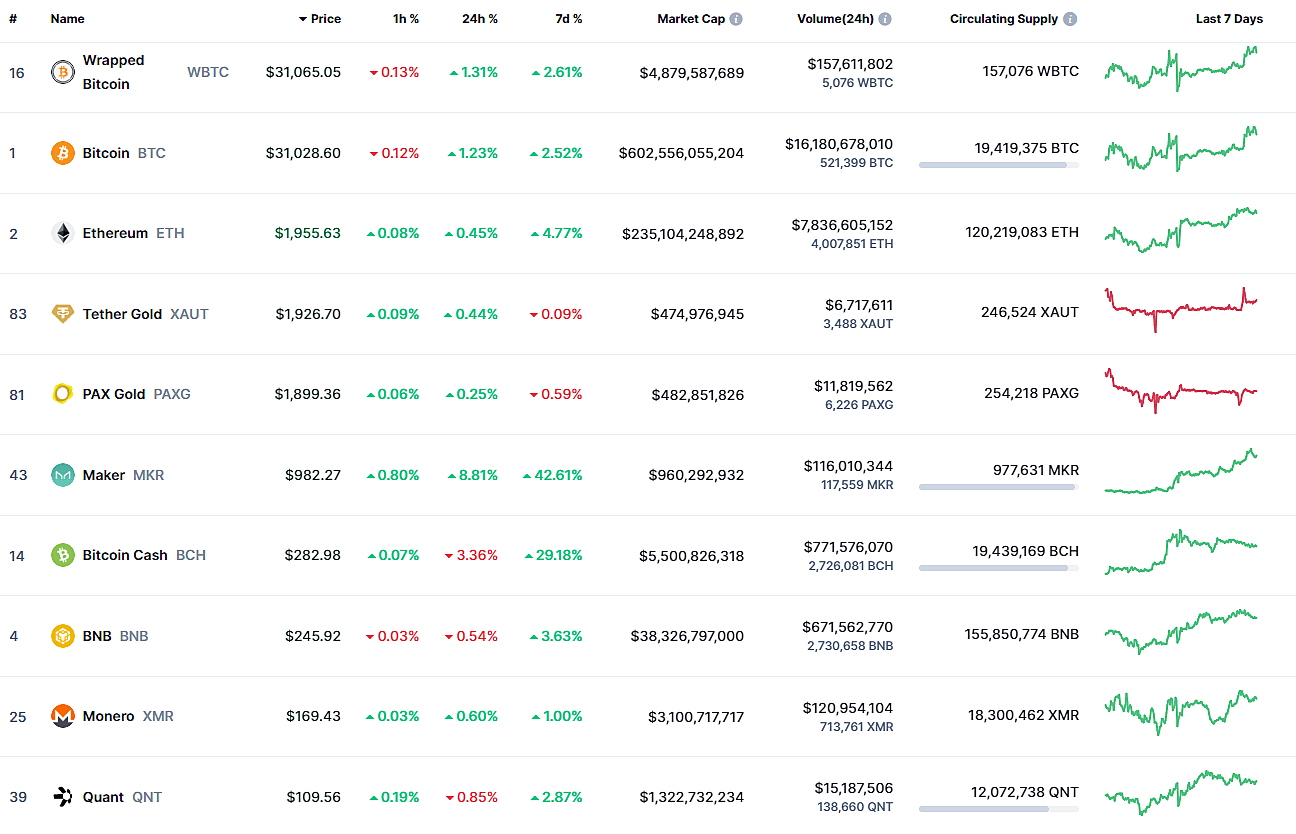 Figure 2: The market worth of a few cryptocurrencies as of July 4, 2023.
Figure 2: The market worth of a few cryptocurrencies as of July 4, 2023.
To better understand why tracking the transactions is difficult, let's take a look at how the ransom payment process works.
When it comes to paying the ransom, the victim can do it by themselves, or they can engage an incident response vendor (a forensic investigator or negotiation firm) to purchase cryptocurrency. The cryptocurrency now available in the victim's crypto wallet is then transferred to the wallet address mentioned in the ransom note. Usually, the address mentioned by the attacker would not have been previously used, and hence can't be tied back to their previous activities. Cybercriminals also tend to create and use unhosted wallets where the transactions are not monitored by cryptocurrency exchanges. Moreover, to further impede forensic investigations, attackers may also share different wallet addresses for different ransom notes, as was the case in the ESXiArgs ransomware attack.
Once the funds reach the wallet mentioned in the ransom note, attackers employ additional measures to mask the trail of stolen funds and protect their identity. These tactics are as follows:
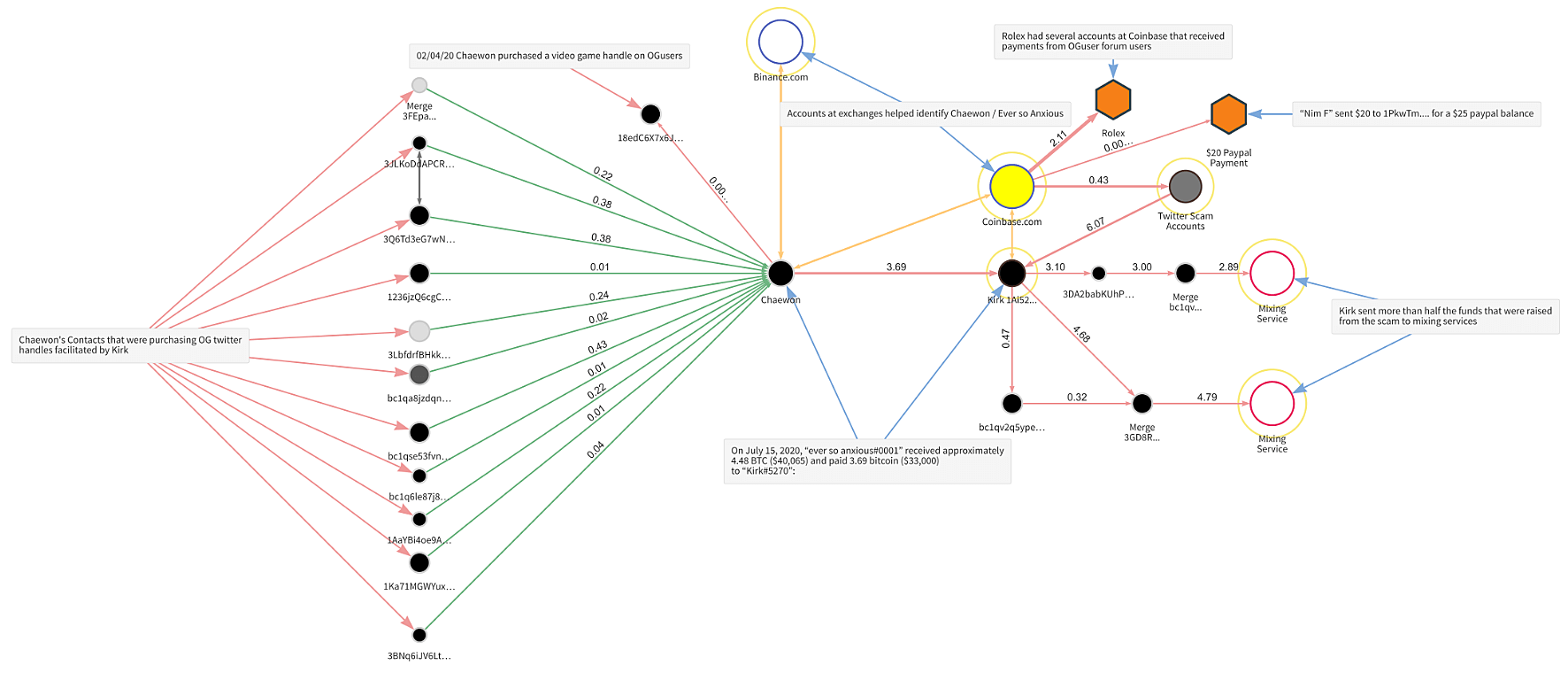 Figure 3: Chainalysis showing the transactions of the Twitter hackers scam in 2020.
Figure 3: Chainalysis showing the transactions of the Twitter hackers scam in 2020.
Figure 4 depicts the ransom payment pathway and potential intervention points as illustrated by the Ransomware Task Force.
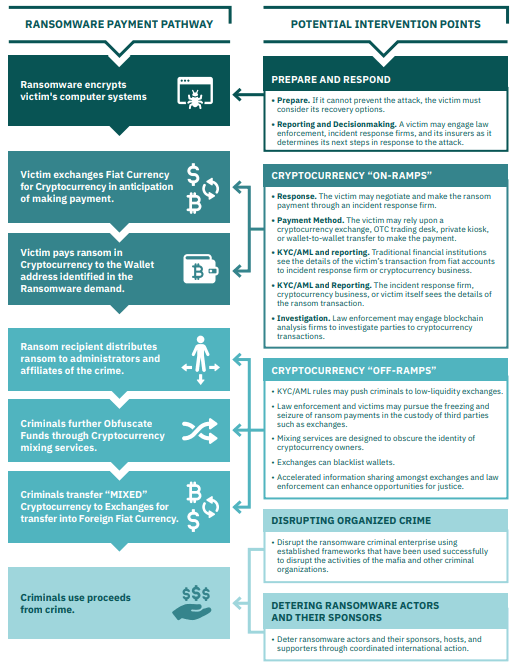 Figure 4: Ransom payment pathway and potential intervention points
Figure 4: Ransom payment pathway and potential intervention points
This is the million dollar question, and the answer depends on the following factors:
Security experts and law enforcement agencies usually advise against making ransom payments. This is because they fear the stolen funds will be used for more nefarious purposes, and might also encourage attackers to strike more often. A recent study reveals that 80% of organizations that paid ransom were targeted again, and that too with a higher ransom demand. That's why the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) issued an advisory stating that organizations that pay ransom would be in violation of the OFAC's regulations, and suggested organizations should rather spend on increasing their cyberdefense and resilience against ransomware.
A unified SIEM solution with integrated DLP and CASB capabilities like ManageEngine Log360 provides:
With the insights gained from a SIEM solution's threat intelligence, correlation engine, and anomaly detection capabilities, organizations can prevent and defend against various attacks including ransomware. To learn more, read our blog, How to detect ransomware attacks using a SIEM. If you're interested in learning how Log360 can enhance your cyberdefense, sign up for a demo and talk to us. Thanks for reading, folks!
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.