Agent-based and agentless monitoring are two types of the server-based performance monitoring system. While OpManager supports both the monitoring methods, there is a key distinction between the two of them, which we'll be discussing in detail.
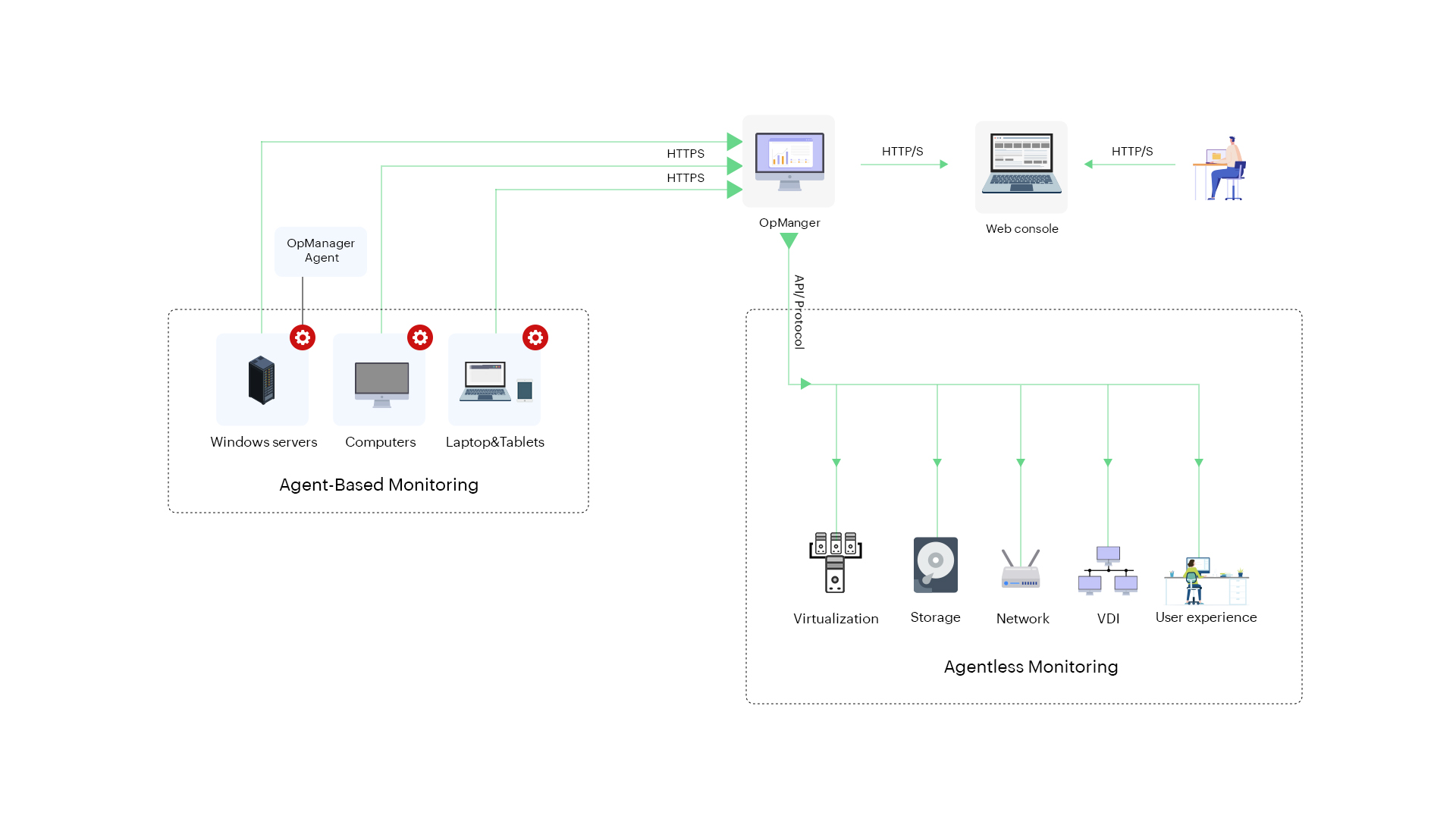
As the name suggests, an agent-based network monitoring technique uses agents to monitor the devices in a network. The agents are installed on the devices that need to be monitored. These agents are in constant contact with the network monitoring tool and are involved in data collection. The collected data is then sent to the monitoring tool for tracking and management.
An agent is a lightweight software application that is installed in the end devices to monitor their performance. Agents collect the monitor data by themselves and send it to the main server for further tracking and analysis. The information flow is not bidirectional but unidirectional i.e. only the agent can contact the main server and not the other way around. Agents reduce the workload on the main server by collecting data all by themselves. Furthermore, even when the OpManager server is down, no data is lost since the agent collects and stores data even if the prime server is under maintenance.
Agentless network monitoring technique monitors the devices remotely with the use of protocols, rest APIs, third parties etc. Agentless network monitoring doesn't require the installation of agents on the network devices.
The Network world is not the way it was before. Things are changing at an increasingly faster pace. Organizations are using networks that are getting more and more complex day by day. Such complexity calls the need for both agent and agentless monitoring techniques. Both agent and agentless monitoring techniques have their fair share of pros and cons. Hence, a network admin must leverage the pros and use techniques that are best for a given situation. Rather than focusing on what type of technique to be used, a network admin must focus on the end result and how to achieve it effectively.
Thank you for your feedback!