- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
Why regular Active Directory password changes are important
Changing passwords periodically is a healthy habit that helps thwart cyberattacks that exploit stolen credentials. Security experts suggest that administrators require users to change AD passwords by implementing effective password expiration policies.
Regular Active Directory password changes reduce the risk of credential compromise by limiting how long a stolen or exposed password remains usable. Periodic password updates also help organizations meet security and compliance requirements, minimize the impact of brute-force and phishing attacks, and ensure continued protection of user accounts and sensitive business data.
Ways to change Active Directory passwords
Organizations typically rely on four native methods to perform an Active Directory change user password operation. Each has its own limitations, especially for hybrid or remote users.
1. Windows Ctrl+Alt+Del change password screen
Users can change Active Directory passwords through the Change a password option, but it requires direct domain connectivity and doesn't update cached credentials for remote users.
2. PowerShell Active Directory change password commands
Admins use Set-ADAccountPassword for scripted or bulk updates, but PowerShell change AD password commands are not user-friendly and offer no authentication or password policy guidance.
3. Forced password change upon logon
By enabling “User must change password at next logon,” admins can push users to complete a change AD password action. However, it fails for remote or VPN-off users who can't reach a domain controller.
Self-Service Change Password Active Directory
ADSelfService Plus provides a secure, web-based self-service portal with multi-factor authentication for Active Directory and self-service password reset capabilities. Hybrid and remote users to change Active Directory passwords without accessing the corporate network. Administrators can enforce stronger, custom password rules using the Password Policy Enforcer, which displays real-time complexity requirements to help users create compliant passwords.
During remote password changes, only the Active Directory password is updated, leaving local cached credentials unchanged—often causing login failures. ADSelfService Plus resolves this with automatic cached credentials updates, ensuring remote users can sign in seamlessly even when off VPN. Additionally, the Password Expiration Notification feature keeps users informed ahead of time, reducing last-minute lockouts and help desk calls.
Challenges with Native Active Directory Password Change Methods
Native options such as the Windows AD change password screen, ADUC, and PowerShell change password commands often fall short in hybrid environments. Key challenges include:
- Network dependency: Users must be connected to the corporate network or VPN to successfully change AD password, making it unreliable for remote users.
- Cached credential issues: Passwords updated in AD don't automatically sync to local machines, causing login failures after users change password in AD.
- No MFA support: Native AD password change methods rely solely on the current password, offering no additional identity assurance.
- Not user-friendly: There is no AD change password web interface or mobile app. The existing change password screen may not always be suitable for end users on the go.
Step-by-Step Active Directory Password Change Using ADSelfService Plus
Follow these steps to change AD password with ADSelfService Plus
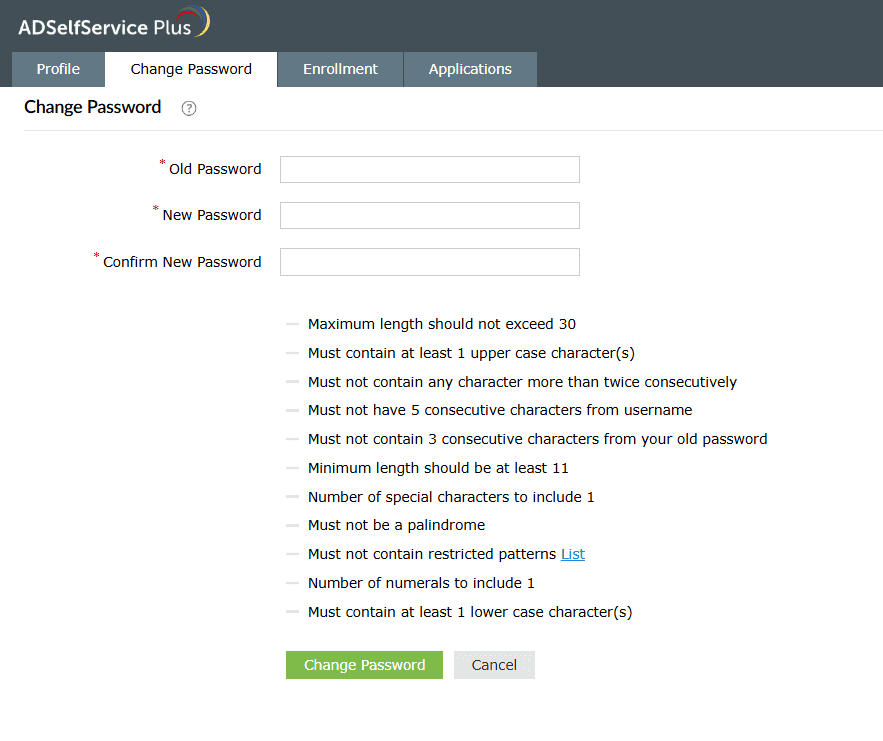
- Log in to the ADSelfService Plus end user portal by completing MFA. Go to the Change Password tab.
- Enter your existing AD password in the Old Password field.
- Provide a new password in the New Password field, and re-enter it in the Confirm New Password field. Make sure your new password meets the displayed complexity requirements.
- Click Change Password.
Why you should use ADSelfService Plus for Active Directory password changes
Strong password policies
ADSelfService Plus' Password Policy Enforcer allows you to configure a custom password policy stronger than the default AD password policy, ensuring your users create robust passwords that are immune to brute-force and dictionary attacks.
24/7 availability
With ADSelfService Plus' web-based password change portal, users can change their passwords from any browser or mobile phone—anytime, anywhere.
Advanced authentication
ADSelfService Plus offers 20 different MFA methods, including passwordless and phishing-resistant options such as FIDO passkeys, biometrics, and YubiKey, allowing you to choose the best way to secure the password change process for your users.
Compliance-ready auditing and reporting
ADSelfService Plus provides detailed audit trails and ready-made reports for all password change activities. This helps organizations meet compliance requirements and gives administrators complete visibility into who changed what, when, and how—without manual tracking or additional tools.
Password change vs. password reset
| Password change | Password reset |
|---|---|
| User updates their current password . | User recovers their forgotten password. |
| Usually initiated by the user when their password is about to expire or when instructed by their administrator. | Initiated by the user (self-service) or the administrator when the user forgets their password and loses access to a resource. |
| User authentication is mandatory. | User authentication is mandatory in case of self-service. |
| User is required to enter their current password before choosing a new one. | User is not required to enter their current password before choosing a new one. |
While Microsoft offers multiple ways for administrators to reset AD users' passwords, ADSelfService Plus enables domain users to perform self-service password resets and changes through its web-based portal after their identities have been verified using strong authentication methods configured by the administrator.
Highlights of ADSelfService Plus
Password self-service
Unburden Windows AD users from lengthy help desk calls by empowering them with self-service password reset and account unlock capabilities.
Multi-factor authentication
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
One identity with single sign-on
Get seamless one-click access to more than 100 cloud applications. With enterprise single sign-on (SSO), users can access all their cloud applications using their Windows AD credentials.
Password and account expiry notifications
Notify Windows AD users of their impending password and account expiry via email and SMS notifications.
Password synchronization
Synchronize Windows AD user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Password policy enforcer
Strong passwords resist various hacking threats. Enforce Windows AD users to adhere to compliant passwords by displaying password complexity requirements.
FAQs
You can check a password change in Active Directory using PowerShell to find the last password change date or by reviewing the Security event logs in Event Viewer to track specific reset events. For PowerShell, run Get-ADUser yourusername -Properties pwdlastset to see the timestamp of the last change for a specific user.
ADSelfService Plus offers secure, web-based and mobile-app-based password change for Active Directory. Allowing remote users to change their passwords while away from the domain network securely.
You can reset an Active Directory admin password by:
- Using the "Active Directory Users and Computers" console
- PowerShell commands
- Booting the server from installation media










