- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
Why 2FA/MFA for Windows logon?
Stolen or weak machine passwords are a prevalent attack vector. The Microsoft Digital Defense Report 2024 states that 99% of identity cyberattacks are password-based. Advancements in credential-based attacks mean that when it comes to keeping your systems safe, amping up the complexity of machine passwords does not suffice. Depending solely on password-based authentication, especially at the enterprise level, leaves the organizational network, data, and IT infrastructure fragile, possibly resulting in lateral movement, privilege escalation, data exfiltration, ransomware attacks, and other security consequences.
Two-factor authentication (2FA), which is a subset of multi-factor authentication (MFA), is a simple yet sturdy mechanism to thwart credential-based attacks. By enabling Windows two-factor authentication and multi-factor authentication for workstations and servers, organizations can avert a significant percentage of cyberattacks.
Secure your logins with a robust Windows two-factor authentication solution
ManageEngine ADSelfService Plus offers the ideal Windows login 2FA solution that's backed by robust authentication methods, risk-based access controls, and offline protection. Its comprehensive Windows MFA capabilities fortify all Windows endpoints, including workstations, servers, RDP, and UAC.
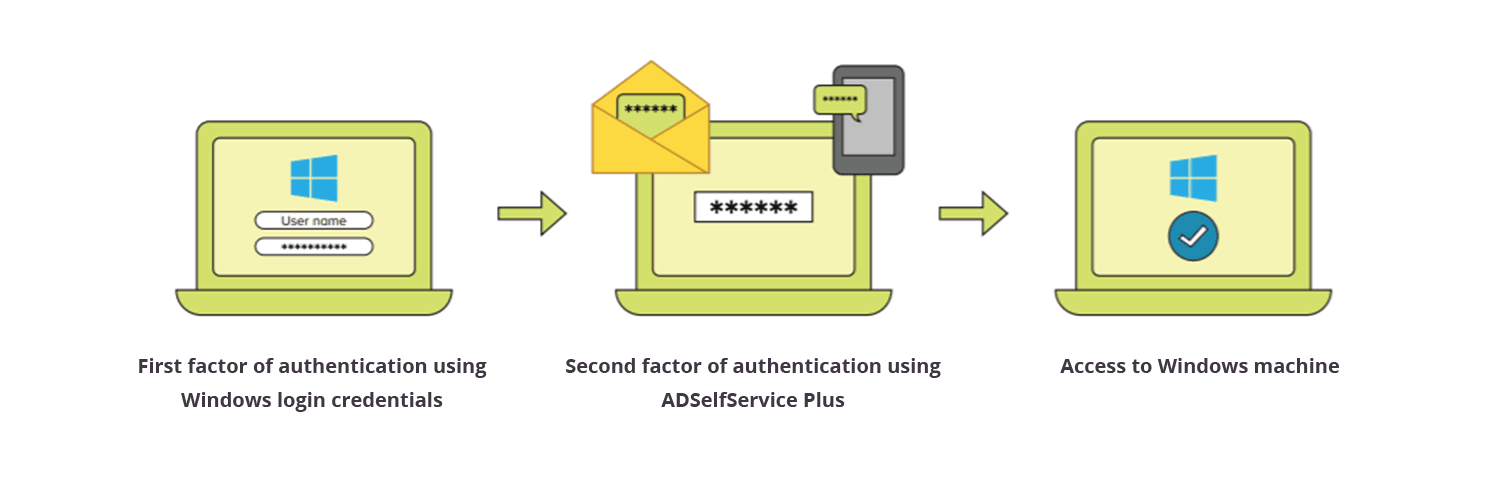
How Windows login MFA works?
- When 2FA for Windows login is configured, users logging in to their Windows machines must first verify their identities using their AD domain credentials.
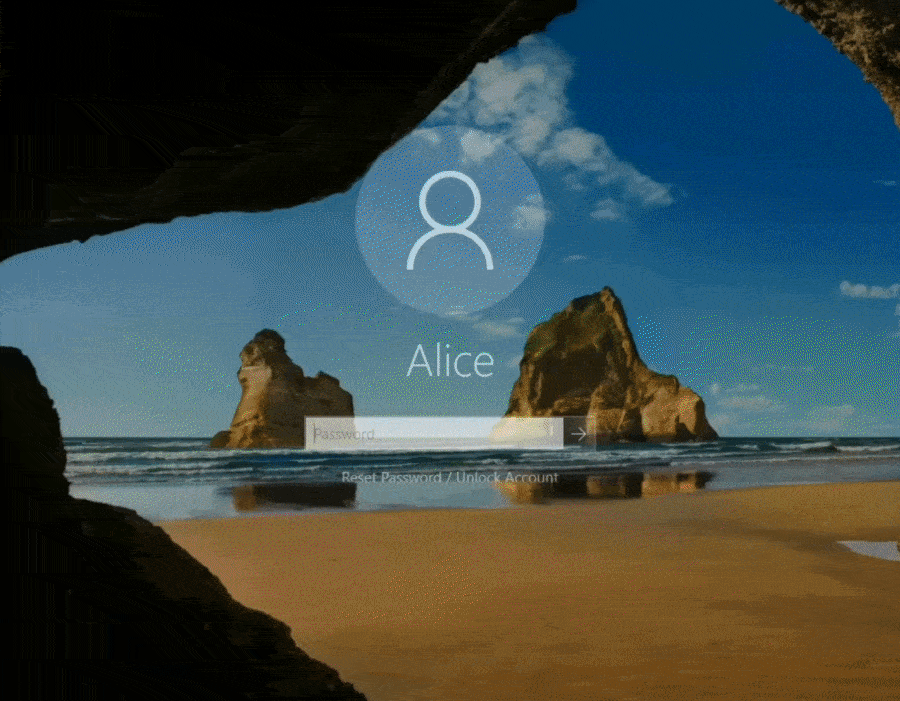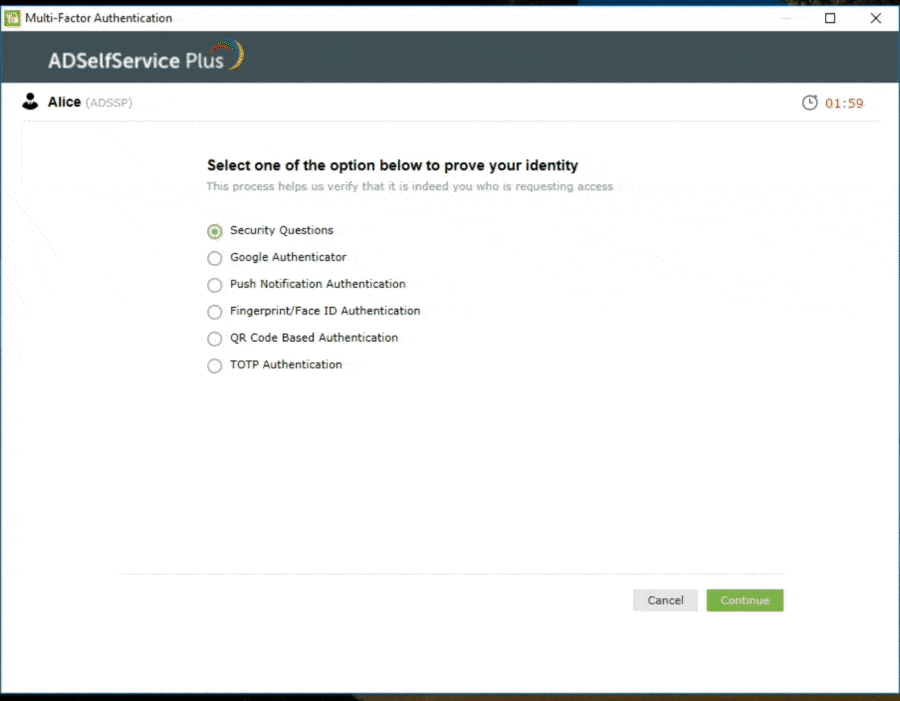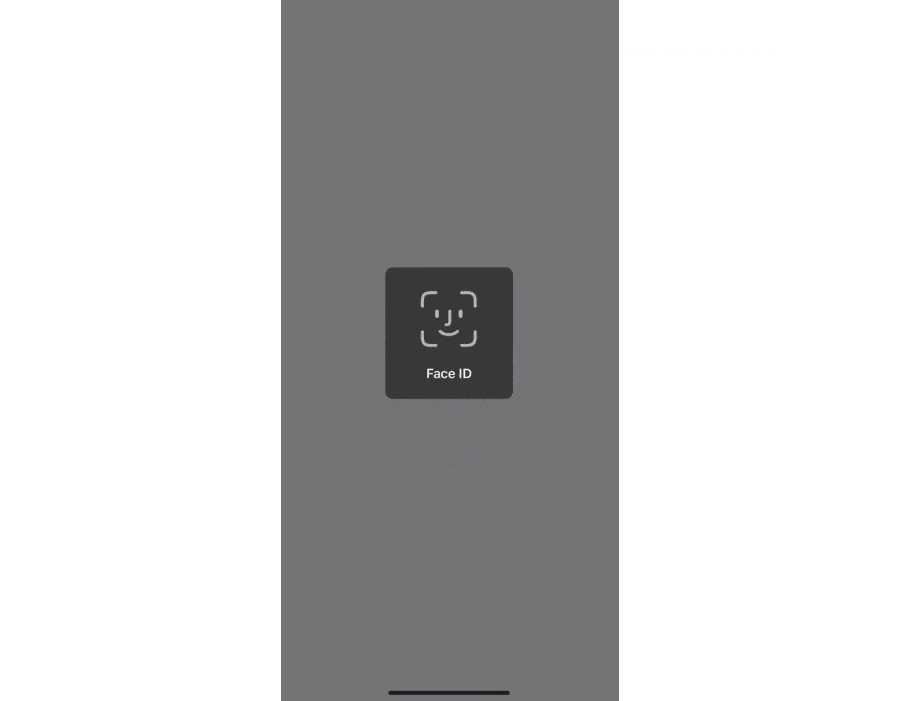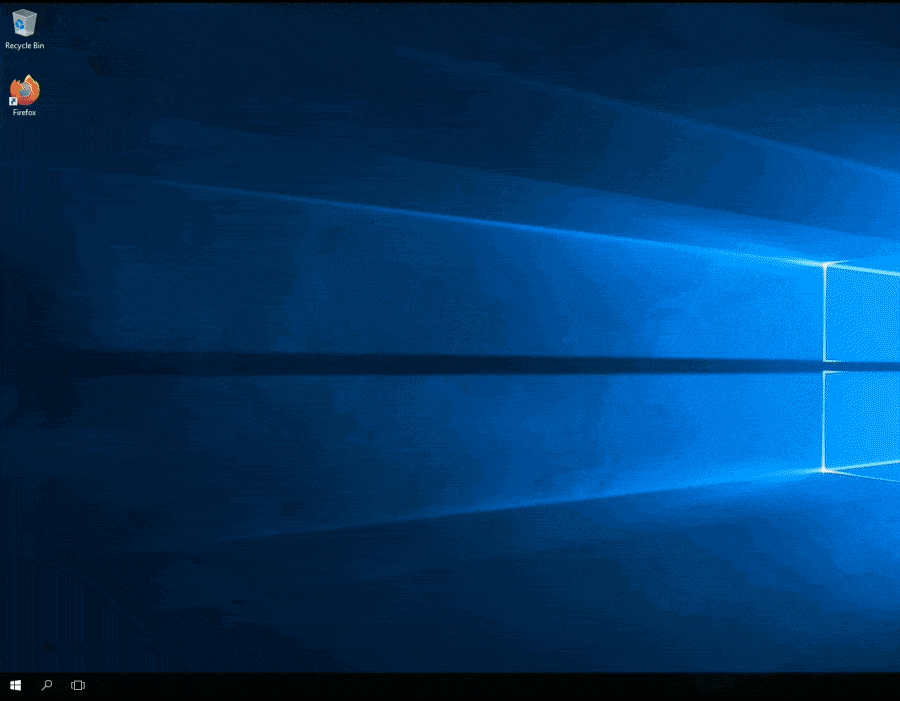
- Next, they complete the Windows login MFA process by authenticating with additional methods such as biometrics, TOTP, or SMS verification. Depending on the configuration, users may need to verify their identities through one or more authentication methods.
- Finally, users are logged in to their Windows machines once they have successfully verified their identities using the configured authentication methods.
The solution supports both Windows local and RDP MFA, providing enhanced login security.
What are the MFA methods supported for Windows logins?
ADSelfService Plus supports a comprehensive list of knowledge, possession, and inherence authentication methods for admins to design the Windows login MFA and 2FA flows appropriate to the target users. Here is the complete list of supported authenticators:
Explore all 20 supported authentication factors for Windows login security.
How to setup MFA for Windows logins via ADSelfService Plus?
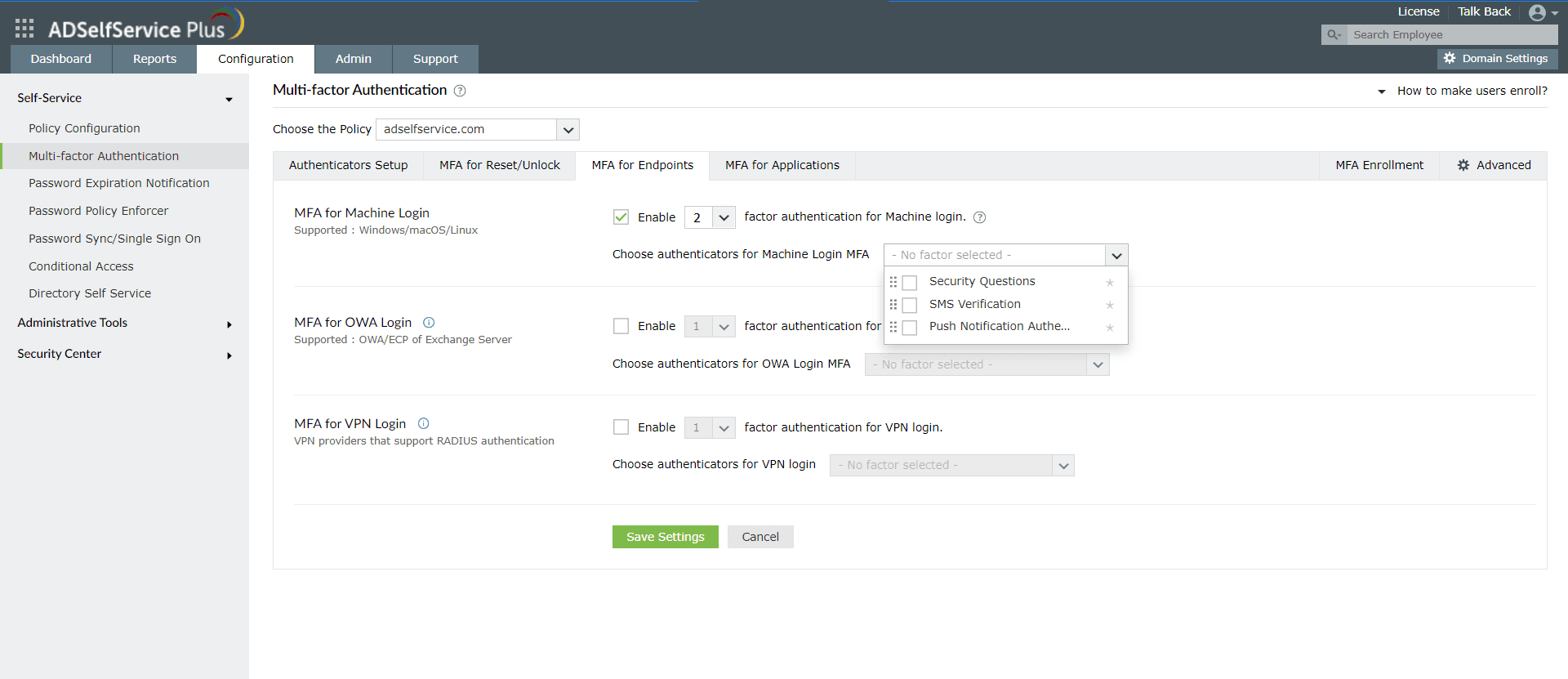
- Log in to the ADSelfService Plus web console with admin credentials.
- Navigate to Configuration > Self-Service > Multi-factor Authentication > MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This will determine which authentication methods are enabled for each set of users.
- In the MFA for Machine Login section, check the Enable __ factor authentication box, select the number of authentication methods, and specify which ones you'd like to use from the drop-down menu.
- Click Save Settings.
Effective integration with major OS versions for Windows MFA
ADSelfService Plus supports enabling MFA for Windows logins for the following OS versions:
| Windows Server | Client machines |
|---|---|
| Windows Server 2022 | Windows 11 |
| Windows Server 2019 | Windows 10 |
| Windows Server 2016 | Windows 8.1 |
| Windows Server 2012 R2 | Windows 8 |
| Windows Server 2012 | Windows 7 |
| Windows Server 2008 R2 | Windows Vista |
| Windows Server 2008 |
Apart from Windows OS, the solution also supports 2FA for macOS and Linux OS.
Tailored Windows 2FA to fit any organization's needs
Admins can customize ADSelfService Plus' Windows login MFA feature to align with their organization's specific security, policy, and compliance requirements.
- Granular authentication controls: Enable specific authenticators for users in particular AD domains, groups, and OUs. Create granular Windows login 2FA flows appropriate to a user's job role, device policy, and preexisting authenticators.
- True MFA: Configure different numbers of authentication levels—with a maximum of three—for users based on their AD domains, OUs, and groups. Heighten or relax the authentication process based on a user's job role and privileges.
- Flexible enrollment policies: Enforce mandatory authentication factors for enhanced security or allow users to choose their desired authenticators from a preconfigured list.
- Trusted device exemption: Allow selected users to skip MFA for Windows logins when using a trusted device. A trusted device refers to a device that has been previously authenticated through the MFA process. This trust remains valid for a set period, after which reauthentication is necessary.
MFA for Windows RDP
RDP access attempts are the most vulnerable, as remote connections to the organizational network may have exploitable security gaps. By enforcing MFA for RDP, ADSelfService Plus ensures that remote access is secured by advanced authentication methods. Moreover, the solution's Windows RDP 2FA process is twofold, safeguarding both RDP server authentication and RDP client authentication prompts from manipulator-in-the-middle, phishing, and credential-based attacks.
MFA for Windows UAC
ADSelfService Plus also integrates MFA for Windows UAC elevation prompts. Any time a user or process attempts to perform an administrative action, a second authentication factor is required. This prevents privilege escalation by malicious insiders or malware posing as trusted applications.
Windows server MFA
Enforcing Windows server MFA is crucial for protecting critical servers from unauthorized access. Windows servers often store sensitive data and run essential services, making them a gold mine for threat actors. By implementing Windows server 2FA with authentication methods like biometrics and one-time passwords, admins can ensure that even if credentials are compromised, attackers cannot gain access to their Windows Server instances. This feature is compatible with Windows Server 2008 and above.
Machine-centric Windows 2FA
Machine-based 2FA is where the Windows login 2FA is triggered based on the device policy settings rather than individual user account settings. When this is enabled, all users logging in to a specific machine must verify their identities using 2FA. Admins can configure authentication methods for machine-based 2FA for Windows, selecting from a range of authenticators.
2FA for Windows offline logins
ADSelfService Plus supports offline 2FA for Windows machines, ensuring secure logins even when users are remote, offline, or unable to connect to the product server. Administrators can configure multiple authentication methods for secure logins. To enable offline access, users must enroll in their chosen authentication factors while online. This offline Windows 2FA solution enhances security for remote workers, ensuring continuous protection even without internet connectivity.
Local user MFA
ADSelfService Plus extends MFA protection to local user accounts on Windows machines. This ensures that even accounts not connected to domain controllers are safeguarded against unauthorized access. By enforcing MFA for local logins, organizations can prevent attacks targeting standalone systems and enhance security for all users, regardless of network connectivity.
Benefits of implementing Windows multi-factor authentication
- Simple deployment: The intuitive admin web portal simplifies Windows MFA configuration and offers scheduler-based, automated MFA agent deployment across end-user devices. The MFA agent is automatically installed on devices new to the domain at a set time.
- Comprehensive configuration: MFA extends to macOS and Linux logins, VPNs, Outlook on the web, and major enterprise applications, ensuring an enterprise's attack surface is minimized as much as possible.
- Assured user enrollment: Bulk enrollment and mandated enrollment options are provided to ensure users' Windows machines and domain accounts are secured by 2FA.
- Real-time reporting: The built-in reporting feature offers audit-ready logs that track every authentication attempt across endpoints. These real-time insights help administrators monitor access patterns, detect anomalies, and ensure compliance with security policies.
- Compliance with regulations: The 2FA feature helps organizations meet industry mandates by enforcing strong, identity-based access controls. It aligns with standards like the GDPR, the PCI DSS, HIPAA, and the NIST CSF by minimizing the risk of unauthorized access to sensitive systems and data.
FAQs
Windows 2FA involves securing logons to Windows machines using username and password followed by another authentication factor to verify a user's identity before giving them network access. Windows MFA secures logons with more than two factors of authentication.
Windows supports 2FA, but not natively. You'll need to implement it through a third-party MFA solution like ADSelfService Plus.
Yes, by implementing MFA for Windows logins, you can add extra layers of security to users' machines. Guarding machine logons using only a single factor—traditionally a username and password—leaves them vulnerable to attacks. However, incorporating additional authentication measures fortifies machines in your organization and safeguards them against breaches and attacks.
By using ADSelfService Plus to secure Windows and RDP-based logins, you can choose your preferred methods from a range of authenticators like biometrics, Duo Security, push notification authentication, Microsoft Authenticator, Google Authenticator, YubiKey, and email verification.
You can safeguard Windows machines in your organization by implementing ManageEngine ADSelfService Plus' Windows logon 2FA for local and remote logons. Apart from Windows machines, the solution provides 2FA for Linux and macOS machines as well. You can also enjoy other 2FA features, like:
To gain a better understanding of the solution's 2FA capability, please schedule a personalized web demo with one of our solution experts or download a free, 30-day trial to explore the solution on your own.
You can easily deploy 2FA for the machines in your organization with a few simple steps using ADSelfService Plus. ADSelfService Plus allows you to enable more than two authenticators during logins and includes strong authenticators such as biometrics and YubiKey.
Highlights of ADSelfService Plus
Password self-service
Unburden Windows AD users from lengthy help desk calls by empowering them with self-service password reset and account unlock capabilities.
Multi-factor authentication
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
One identity with single sign-on
Get seamless one-click access to more than 100 cloud applications. With enterprise single sign-on (SSO), users can access all their cloud applications using their Windows AD credentials.
Password and account expiry notifications
Notify Windows AD users of their impending password and account expiry via email and SMS notifications.
Password synchronization
Synchronize Windows AD user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Password policy enforcer
Strong passwords resist various hacking threats. Enforce Windows AD users to adhere to compliant passwords by displaying password complexity requirements.










