- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
What is the UAE IAR?
The United Arab Emirates Information Assurance Regulation (IAR), formerly NESA compliance, refers to a set of cybersecurity standards and guidelines established by the Signals Intelligence Agency (SIA), a federal authority in the UAE.
The primary goal of the IAR is to protect the UAE's critical information infrastructure (CII) from cyberthreats. This CII includes various organizations such as government entities, infrastructure providers (e.g., for telecommunications, energy, finance, healthcare, and transportation), private sector organizations, IT and cybersecurity service providers, and consulting firms.
The UAE IAR compliance checklist
The SIA developed a comprehensive list of Information Assurance Standards, which are comprised of 188 security controls divided into management and technical families. They are further categorized into four priority levels: P1 (the highest), P2, P3, and P4 (the lowest).
Out of the 188, 39 are P1 controls and address 80% of threats identified by the SIA. Implementing P1 controls is the first step to becoming compliant with the IAR and building a strong cybersecurity foundation.
What are the UAE IAR requirements?
The table below lists important IAR security requirements and explains how ManageEngine ADSelfService Plus, an identity security solution, helps organizations satisfy them.
| Security control number | Control description | How ADSelfService Plus satisfies the requirement |
|---|---|---|
| T3.6.2 P2 |
Audit logging
The entity shall produce and keep audit logs recording user activities, exceptions, and information security events |
Logs all critical user actions like password resets, account unlocks, and MFA enrollments; these reports can be scheduled or exported in multiple formats |
| T5.1.1 P2 |
Access control policy
The entity shall establish an access control policy based on business and security requirements |
Supports the enforcement of access policies through MFA, SSO, and self-service password management to secure access with contextual awareness based on the user, device, and location |
| T5.2.3 P1 |
User security credentials management
The entity shall control the allocation of user security credentials |
Manages credential resets securely with identity verification via OTPs, push notifications, and biometrics |
| T5.3.1 P1 |
Use of security credentials
The entity shall require users to use security credentials in line with the entity’s security practices |
Promotes strong credential hygiene using the Password Policy Enforcer to restrict characters, repetition, patterns, and lengths while enabling MFA |
| T5.4.2 P1 |
User authentication for external connections
The entity shall use appropriate authentication methods to control the access of remote users |
Supports 20 different MFA methods for remote desktop access via RDP and secure logons on Windows, macOS, and Linux machines |
| T5.5.1 P1 |
Secure logon procedures
The entity shall control access to systems and applications using a secure logon and logoff procedure |
Provides conditional access policies with adaptive MFA to secure application logons by analyzing risk factors such as the IP address, access time, device, and user's geolocation |
| T5.5.2 P1 |
User identification and authentication
The entity shall create a unique identifier (user ID) for each user and implement a suitable authentication technique |
Supports various MFA mechanisms and identity verification workflows to secure access with contextual awareness based on the user, device, and location |
| T5.5.3 P1 |
User credentials management system
The entity shall implement a system for managing user credentials (i.e., passwords) |
Offers self-service password reset and account unlock capabilities, blocks compromised passwords via a Have I Been Pwned integration and other password security measures, and notifies users of upcoming password expirations |
| T5.6 P1 |
Application and information access control
To prevent unauthorized access to information held in application systems |
Implements centralized, one-click access to applications with SSO, tracks all logons with detailed reports, and enforces MFA to prevent unauthorized access |
How ADSelfService Plus helps you comply with UAE IAR requirements
ADSelfService Plus is an identity security solution that offers adaptive MFA, seamless SSO, and self-service password reset features to help your organization comply with the IAR.
- Mandate MFA for users: Secure user access to enterprise applications and services by enabling adaptive MFA for machines, applications, VPNs, RDP, and Outlook on the web.
- Get comprehensive support: Pick from 20 different authentication factors, including FIDO passkeys, biometrics, Duo Security, TOTPs, YubiKey, and smart cards.
- Apply context-awareness: Automatically intensify MFA methods for suspicious access requests using conditional access policies based on the user's IP, location, and time of access.
- Enforce password policies: Apply restrictions on dictionary words, repeated patterns, and palindromes while requiring special, numeric, and Unicode characters.
- Conditional access
- MFA
- Password Policy Enforcer
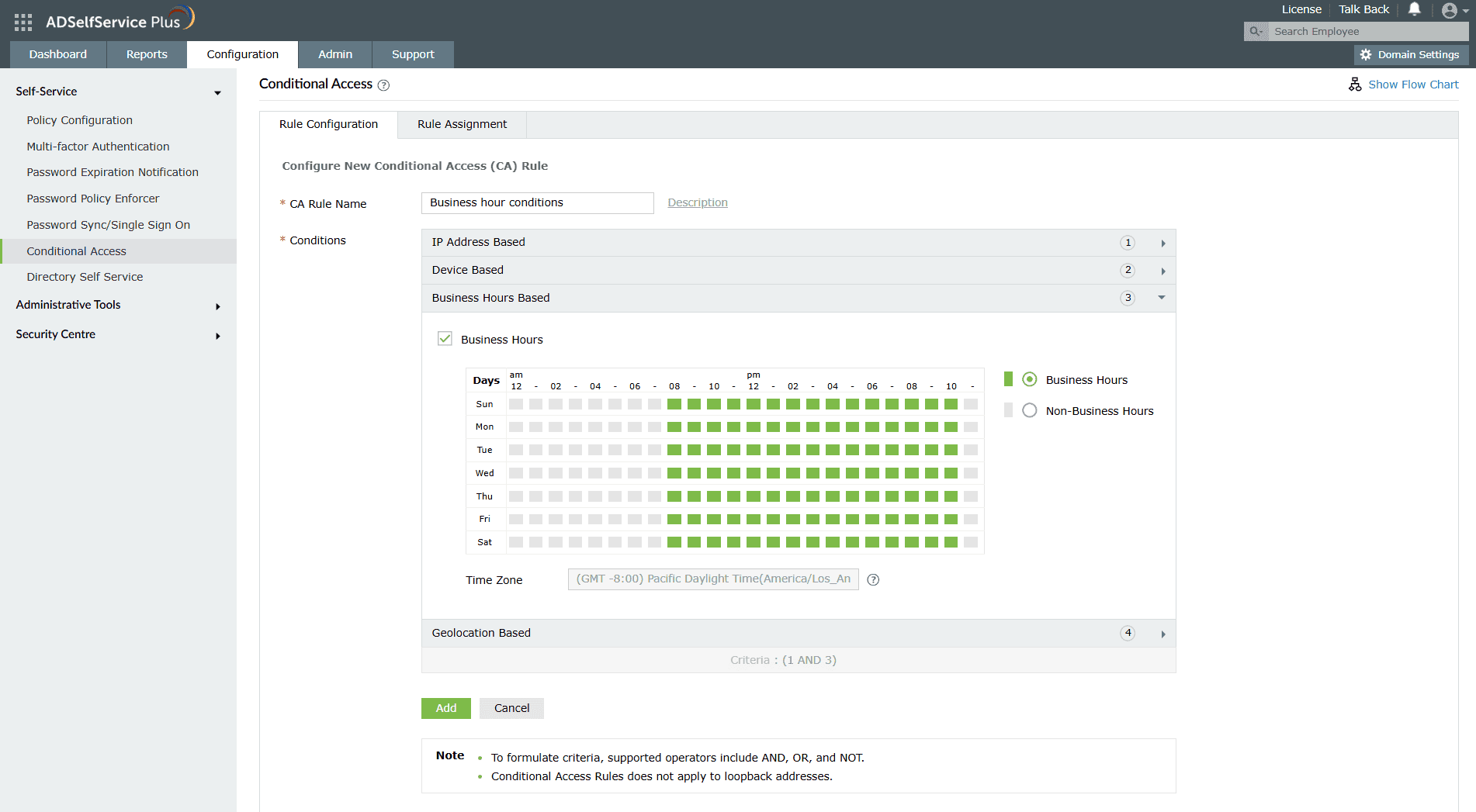
Configure conditions based on the IP address, device, business hours, and geolocation.
Drag to customize business hours.
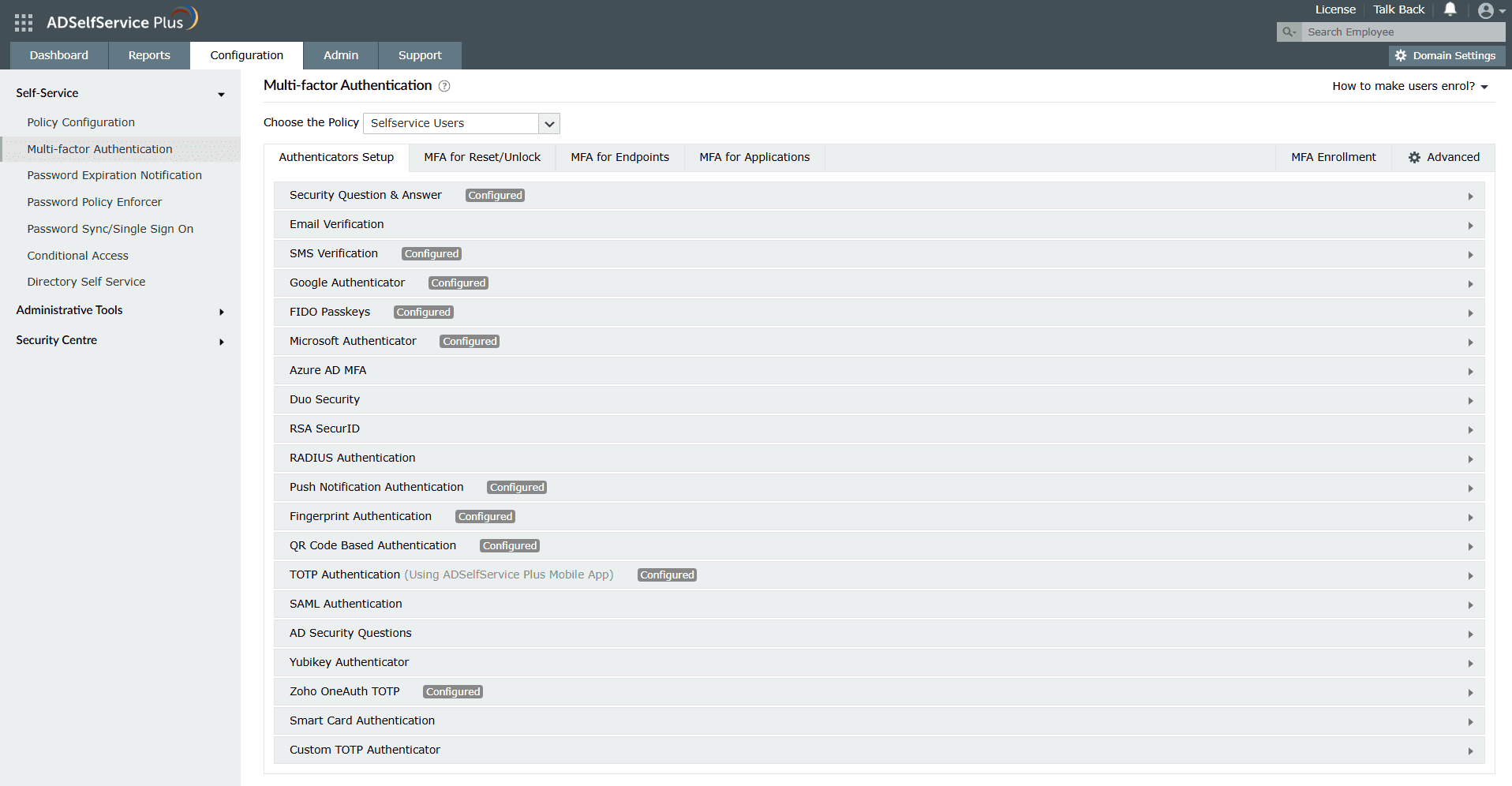
Set up different MFA flows for different groups or departments in your organization.
Choose from 20 different authenticators to verify your users' identities.
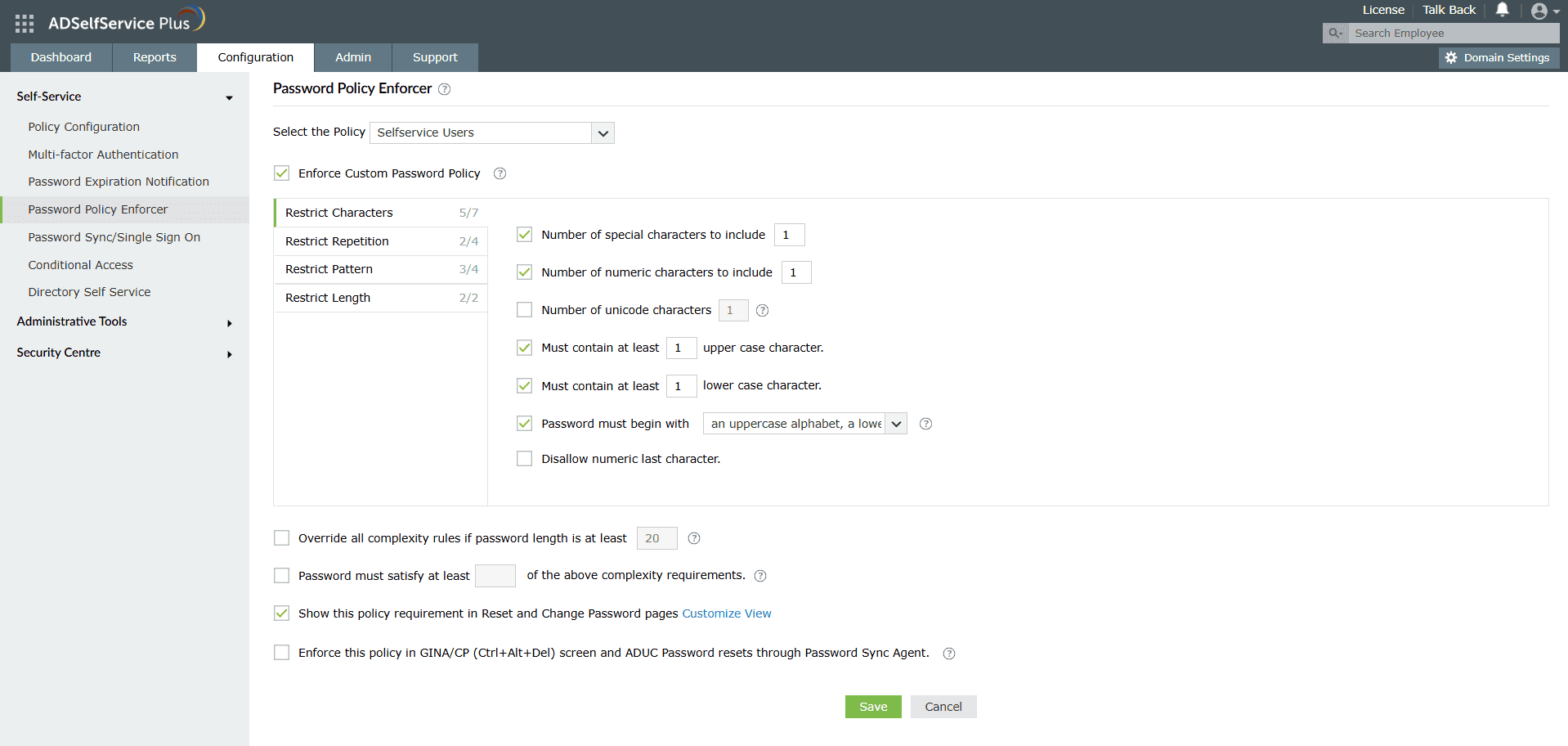
Enforce different sets of password rules for different policies.
Choose the complexity requirements that your users' passwords should satisfy according to your organization's security needs.
Benefits of using ADSelfService Plus to comply with UAE IAR requirements
- Fine-grained flexibility: Tailor password policies to various user roles within the organization based on their levels of access to sensitive data.
- An integration with Have I Been Pwned: Bolster the IAR's stringent password security requirements by integrating with Have I Been Pwned to prevent users from choosing breached passwords.
- Conditional access policies: Intensify MFA for suspicious logon attempts (based on the IP, location, time, etc.) to align with the IAR's requirements for adaptive security and stronger access controls.
- Compliance with other regulations: Ensure that your organization also complies with PCI DSS, HIPAA, Essential Eight, CJIS Security Policy, SOX, and GDPR standards.
Highlights of ADSelfService Plus
Password self-service
Unburden Windows AD users from lengthy help desk calls by empowering them with self-service password reset and account unlock capabilities.
MFA
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, Outlook on the web, and RDP logons..
1 identity with SSO
Get seamless one-click access to more than 100 cloud applications. With enterprise SSO, users can access all their cloud applications using their AD credentials.
Password and account expiration notifications
Notify AD users of their impending password and account expirations via email and SMS notifications.
Password synchronization
Synchronize AD user passwords and account changes automatically across multiple systems, including Microsoft 365, Google Workspace, and IBM i.
Password policy enforcer
Strong passwords resist various hacking threats. Enforce password complexity rules by displaying requirements in real time, helping AD users set compliant passwords.










