What is key management?
Key management refers to the process of generating, distributing, storing, using, and ultimately destroying cryptographic keys. These keys are the essential element for encryption and decryption operations, ensuring that sensitive information such as personal data, financial details, and other confidential communications remain secure.
Imagine you're running a successful online business. You have customers from all over the world making transactions on your website, sharing personal data and payment information. Your business relies on encryption to ensure that this sensitive data remains safe.
Encryption is like locking away your customers' data in a vault, but if someone gets their hands on the keys, then they can open that vault and access everything inside. This is where key management steps in.
Key management is like being the master of all those vault keys. Strong key management ensures that only authorized individuals have access to those keys and that they're stored, rotated, and destroyed when no longer needed.
Why is key management important?
Key management forms the basis of all data security, as only authorized users have access to well-protected keys. Without a strong key management process, even the most sophisticated encryption systems would be like locking a door but leaving the key under the mat.
Keys are also essential for securely transmitting data over the internet. If a poorly secured key is stolen, attackers could impersonate a trusted service and infect victims' computers with malware through methods like code signing. Moreover, keys help companies comply with standards and regulations to ensure they are following best practices for protecting cryptographic keys.
Types of keys
Key management revolves around different types of cryptographic keys, each serving distinct purposes:
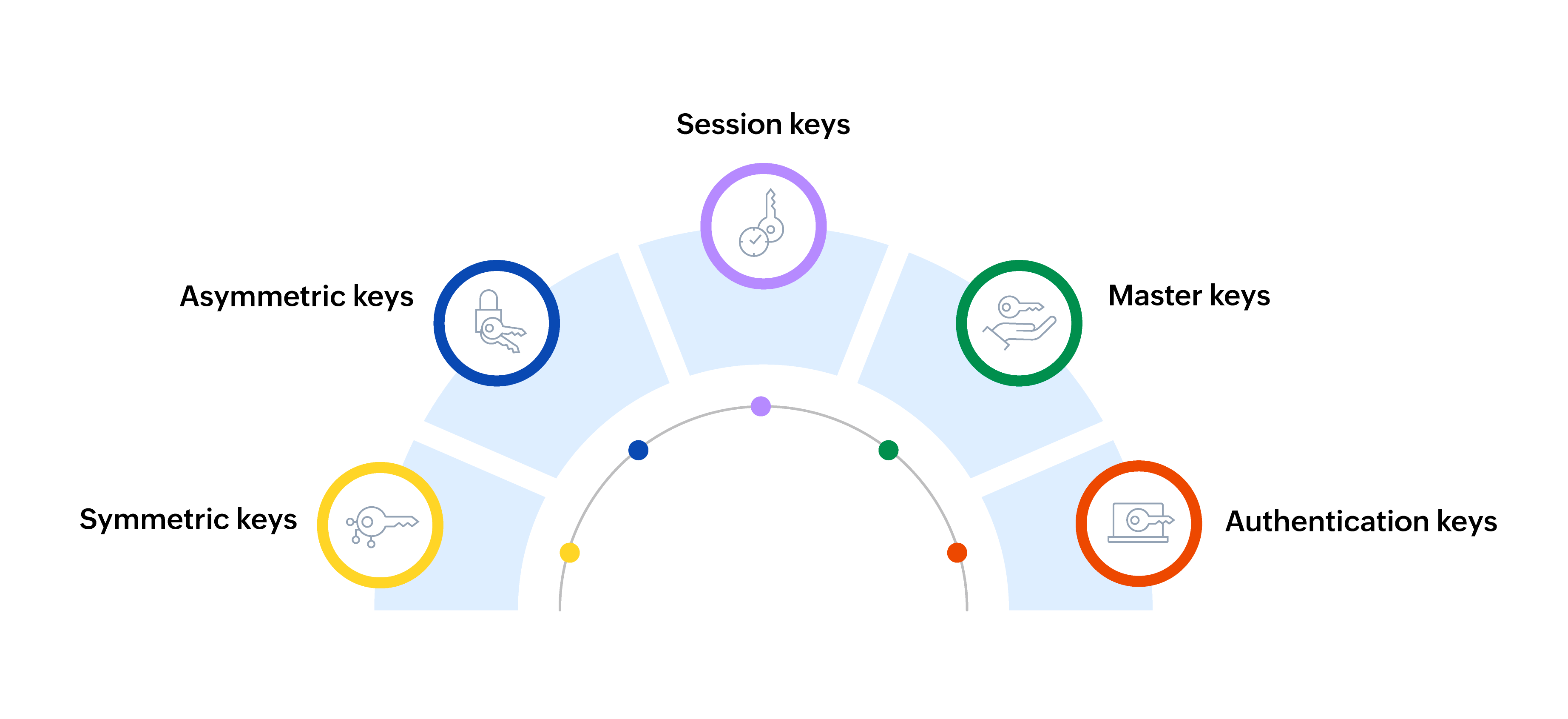
- Symmetric keys: These are used in symmetric encryption, where the same key is used to both encrypt and decrypt data. This makes symmetric encryption fast but also requires secure key distribution.
- Asymmetric keys: Asymmetric encryption uses a pair of keys—a public key for encryption and a private key for decryption. This is typically used in secure communications, like SSL certificates.
- Session keys: These are temporary keys used for a single communication session and are discarded after use, enhancing security by limiting the duration of exposure.
- Master keys: These are often used in systems to protect other keys, such as session or encryption keys.
- Authentication keys: Used to verify the identity of the users or systems in communication.
Key management life cycle
The key management life cycle is a structured process that outlines how cryptographic keys are generated, used, stored, and eventually retired in a secure environment. Effective key management involves careful oversight of keys throughout their life cycle. This includes:

Key generation
- This phase involves creating cryptographic keys using random or pseudo-random number generators to ensure security.
- Key generation parameters, such as length and algorithm, should meet compliance standards (e.g., AES-256 for encryption).
- Keys must be unique, and some organizations may use hardware security modules (HSMs) to increase security.
Key distribution
The keys are securely distributed to the intended users or systems. Methods include manual distribution, encrypted electronic transfers, or secure channels provided by key management systems.
Key wrapping (encrypting the key with another key) may be used to protect it during transit.
Key storage
- Secure storage is essential to protect keys from unauthorized access. HSMs or encrypted databases are commonly used for key storage.
- Regular audits ensure keys remain uncompromised. Backup keys should also be stored securely but separately from the primary storage to prevent single-point failures.
Key rotation
- Keys should be rotated periodically to limit exposure in case of compromise. Rotation intervals depend on usage and compliance requirements.
- Rotation involves generating new keys and updating all dependent systems while phasing out the old keys.
Key deactivation and expiration
- When a key is no longer needed, it should be deactivated, rendering it unusable for future encryption or decryption processes.
- Expiration dates can be set to render a key unusable after a certain time automatically, further reducing the risk of compromise.
Key destruction
- When keys reach the end of their life cycle, they should be destroyed to prevent unauthorized access.
- Destruction methods include overwriting and erasing from storage, especially if stored on physical devices.
Key management challenges and solutions
1. Key generation and distribution
Challenges
One of the most significant challenges is ensuring that the keys are generated using strong cryptographic algorithms and securely distributed to authorized parties.
Solutions
To tackle this problem, your company should utilize HSMs for secure key generation in secure hardware environments. Additionally, it is crucial to incorporate secure key exchange protocols such as Diffie-Hellman and utilize public key infrastructure (PKI) for efficient distribution of asymmetric keys.
2. Key rotation and revocation
Challenges
Regularly rotating your keys is essential to minimizing the risk of compromise. Key rotation involves generating new keys and securely replacing the old ones, while key revocation ensures that any compromised keys are rendered invalid.
Solutions
By implementing a centralized key management system, you can streamline the rotation and revocation processes, ensuring that all your keys are efficiently managed.
3. Compliance with regulations
Challenges
Many industries are governed by strict data protection regulations such as GDPR, HIPAA, and PCI DSS, which mandate strong encryption and key management practices. Non-compliance can lead to hefty fines.
Solutions
To meet compliance, organizations must maintain secure key management processes and undergo regular audits to ensure that their practices align with industry standards.
4. Integration with existing systems
Challenges
Integrating key management with your current IT systems can be challenging, especially in environments that utilize multiple platforms and devices.
Solutions
You should choose key management solutions that ensure broad compatibility and can integrate smoothly with your existing systems, including hardware security modules (HSMs), PKI, and cloud services.
5. Access control
Challenges
Ensuring the security of your cryptographic keys is of utmost importance. You should limit access solely to authorized users or systems, and it is imperative that you consistently enforce robust access control policies.
Solutions
By implementing role-based access control (RBAC), you can restrict key management and usage to only those personnel who need it for their duties.
Key management compliances and best practices
It’s not enough to know that strong key management is essential. The real question is: How can your organization implement it effectively to protect sensitive data and ensure compliance? Here’s a breakdown of the key management best practices that can help you build a secure framework:
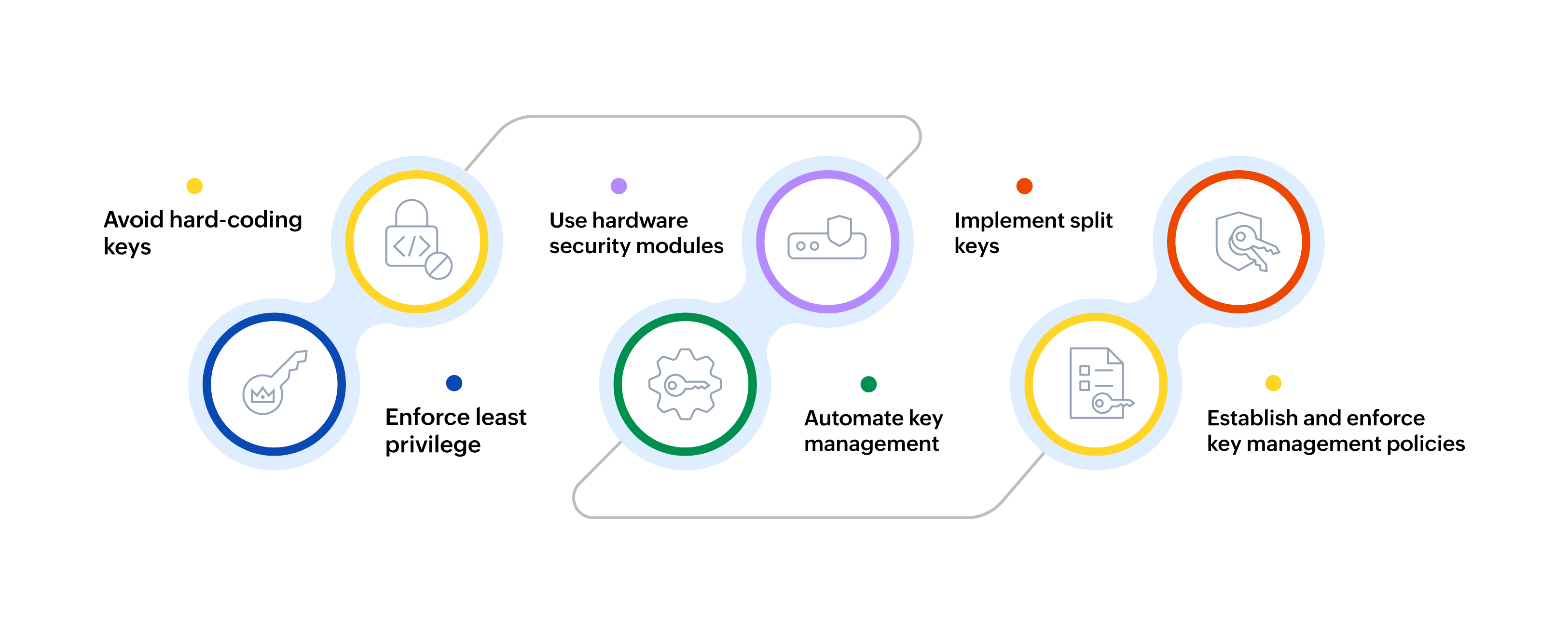
- Avoid hard-coding keys: Hard-coding cryptographic keys directly into applications is a critical vulnerability, as attackers can reverse-engineer these applications to extract keys. Instead, store keys securely in solutions like HSMs or key vaults to protect them from unauthorized access.
- Enforce least privilege: Access to cryptographic keys should be tightly controlled, with only essential personnel and systems given access. Enforcing a least-privilege approach reduces the potential attack surface, strengthening overall security.
- Use hardware security modules: HSMs offer advanced protection for managing cryptographic keys by securing them in a tamper-resistant environment. This approach ensures keys are generated, stored, and managed in compliance with stringent security standards.
- Automate key management: Manually managing keys can lead to security gaps and errors. By automating key rotation, distribution, and revocation, organizations can reduce human error and keep keys up-to-date seamlessly.
- Establish and enforce key management policies: Clear, well-defined policies covering key generation, storage, usage, distribution, and destruction are essential. Conduct regular audits and monitoring to ensure compliance with these policies and address any gaps.
- Implement split keys: In especially sensitive environments, consider using key-splitting techniques, where keys are divided into parts. This prevents any single person from accessing the full key, adding an extra layer of protection.
How can ManageEngine help with key management?
Managing cryptographic keys doesn’t have to be a complex, time-consuming process. Every second you delay in managing your cryptographic keys, your organization could be at risk. Expired SSL/TLS certificates can disrupt operations, unmonitored SSH keys can lead to unauthorized access, and overlooked vulnerabilities can leave you scrambling to fix avoidable problems.
ManageEngine Key Manager Plus has been designed to help organizations like yours simplify key management without compromising security. With Key Manager Plus, you get complete control over your SSH key life cycle management and SSL/TLS certificates from a centralized platform. It eliminates the need to juggle multiple tools or rely on manual processes, saving you time and reducing the risk of errors. By automating key discovery, deployment, renewal, and rotation, the solution ensures your keys are always secure and up to date.
Moreover, It helps you stay ahead of compliance requirements by offering detailed audit trails and reports. It also ensures your organization is protected with strong access controls and advanced encryption techniques, making your environment more secure.
ManageEngine Key Manager Plus is designed to grow with your needs, offering the flexibility and scalability modern businesses require.