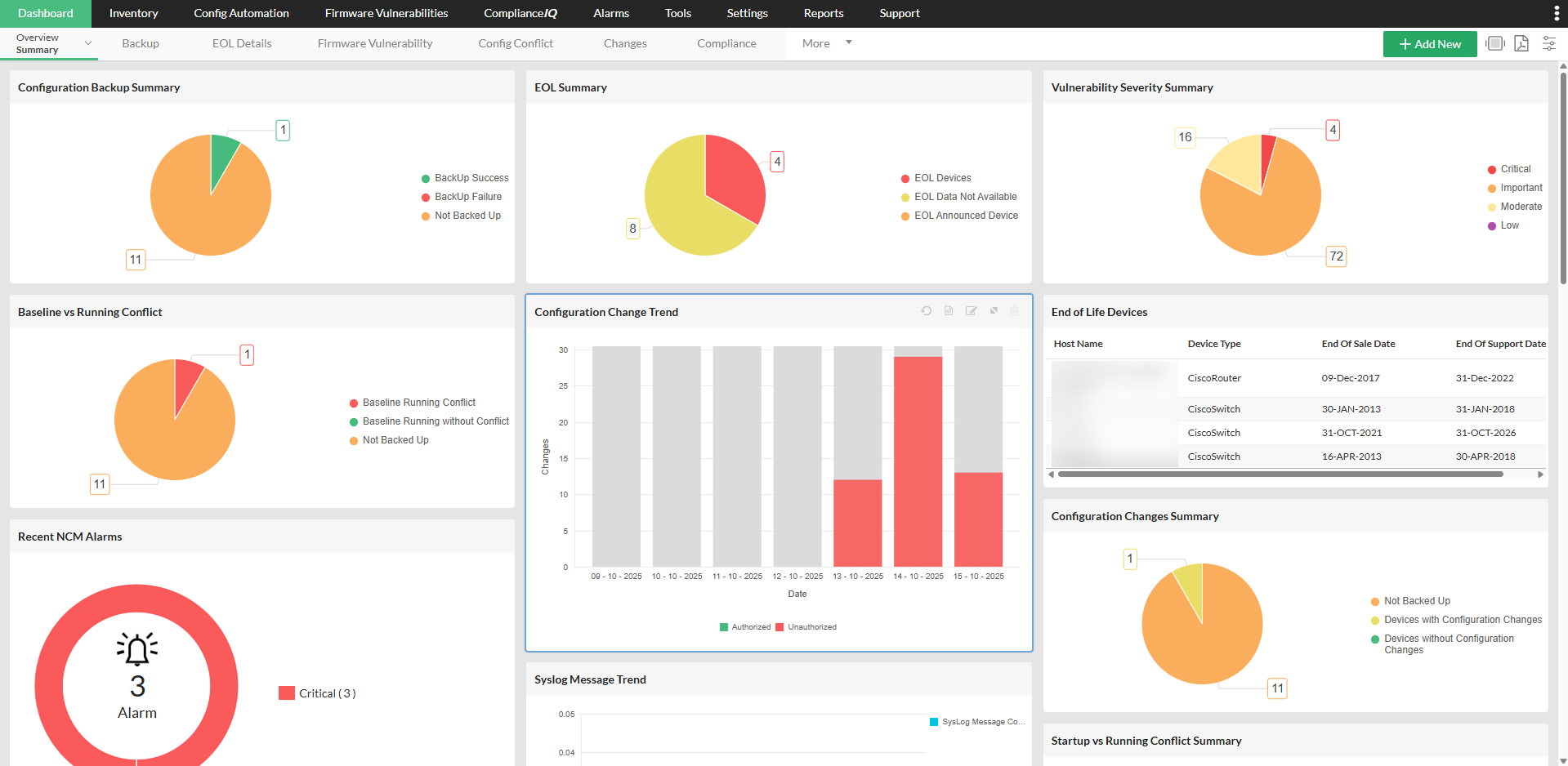
Most network teams operate under constant pressure as devices, configurations, and security rules change faster than they can respond. When everything depends on manual effort, things slow down, mistakes slip in, and keeping the network stable becomes harder than it should be.
A good network automation tool steps in by handling all the repetitive, time-consuming work that eats up an engineer's day. It applies configuration changes across devices, keeps backups updated, tracks every modification, and makes sure nothing drifts away from what the business expects. With the right network automation software running quietly in the background, teams get a network that stays consistent, easier to manage, and far more predictable even when it continues to grow.
Why is network automation important?
Network automation is the simplest way to keep large, fast-moving networks stable without drowning administrators in repetitive work. Instead of manually logging into devices and pushing configurations, automation handles routine tasks. This improves reliability, speed, and security.
- Reduced manual intervention: Everyday tasks like config updates, backup collection, compliance checks, and policy roll-outs can run on their own. This removes hours of manual typing and reduces the chance of someone accidentally pushing a wrong command during rush hours.
- Dramatically improves efficiency: A change that would normally take multiple steps such as logging in, comparing configs, validating syntax, pushing updates; can be completed in minutes. Teams move quicker, and networks stay consistent even when device counts keep growing.
- Ensures consistency across devices: Automation keeps every device aligned with the same configuration standards. Instead of routers and switches drifting over time due to one-off manual edits, predefined templates and policies maintain uniform settings across the network. This reduces unexpected behaviour, simplifies troubleshooting, and gives administrators full confidence in the accuracy and stability of each device’s configuration.
- Gives better visibility and control: Automation tools show which configurations changed, who made the change, whether it’s compliant, and whether a device needs attention. You’re not guessing or digging through logs; everything is tracked, compared, and clearly visible.
- Strengthens security: Automated backups and version tracking help detect unauthorized changes instantly. If something goes wrong, you can roll back to a last-known-good configuration within seconds, preventing downtime or security gaps.
Manual configuration management becomes risky as networks grow. Automation keeps the entire environment stable and predictable, reduces downtime, and frees administrators to focus on more strategic improvements instead of repeating the same commands every day.
Solving real-world operational challenges with network automation
Network automation offers a scalable way to simplify network configuration management while improving its integrity and uptime. Here are some of the most impactful scenarios where automation transforms daily work:
- Zero-touch provisioning (ZTP): When new devices arrive, onboarding shouldn’t take hours of manual setup. With ZTP, switches, routers, and firewalls configure themselves the moment they connect. This speeds up deployments across branches, eliminates inconsistent setups, and gets teams productive faster.
- Automated firmware upgrades: Keeping devices patched is critical, but doing it manually risks missteps and after-hours fatigue. Automation lets you schedule firmware upgrades in controlled batches, validate versions, and roll them out without disrupting live traffic; ensuring security without burning out administrators.
- SNMP/TACACS configuration and audits: Monitoring and access control settings must be consistent across every device. Automating SNMP/TACACS deployment ensures uniform credentials, correct community strings, and clean audit trails. No device gets missed, and compliance becomes a repeatable routine instead of a rushed fire drill.
- Policy-driven compliance enforcement: Whether it’s internal standards or industry regulations, automation helps you scan devices on a schedule, flag violations instantly, and even trigger predefined remediation actions. This keeps the network compliant round-the-clock instead of relying on periodic manual checks.
- Bulk configuration roll-outs across devices: Changes like VLAN updates, ACL modifications, or routing adjustments often need to happen across dozens of devices. Automation pushes these updates consistently, validates them against templates, and prevents the drift that usually comes from one-off manual edits.
Each of these scenarios tackles a real operational bottleneck. When automated, they reduce errors, speed up roll-outs, remove repetitive overhead, and give administrators complete control; even in large, fast-expanding networks.
Benefits of network automation
In most networks, the toughest problems don’t come from big outages; they come from everyday tasks that pile up, repeat endlessly, and demand precision every single time. Network automation replaces manual effort with predictable, consistent operations that run in the background.
- Fewer human errors, less repetition: Backups, audits, updates, and roll-outs run automatically, reducing manual steps and accidental mistakes.
- Tracks and reverses unwanted changes: Unauthorized or incorrect edits are detected instantly, notifications are sent, and the system can roll them back before they cause disruption.
- Stronger compliance enforcement: Policies are enforced continuously across devices, ensuring they meet internal standards and regulatory requirements at all times.
- Better device security: Baselines stay intact, configuration drift is eliminated, and firmware vulnerabilities surface earlier.
- Improved team productivity: With routine work offloaded, IT teams can move toward higher-impact improvements instead of reacting to day-to-day tasks.
Cons of not using network automation
- Manual workloads overwhelm teams: Admins face mounting pressure with repetitive tasks and fragmented visibility.
- Inconsistent configurations: Manual changes often lead to discrepancies and misalignment across environments.
- Increased downtime risks: Missed updates or delayed fixes can cause avoidable outages.
- Lack of real-time alerts: There's no immediate visibility into unauthorized changes or compliance issues.
- Slower reaction to vulnerabilities: Outdated firmware and unsafe configurations remain undetected longer.
A network that automates the routine becomes more stable, more secure, and far easier for teams to manage; while a network that stays manual keeps accumulating risk with every new device added.
Why do IT teams need a network automation tool?
Managing device configurations manually is labor-intensive and risky. A configuration automation tool helps network teams solve core challenges such as:
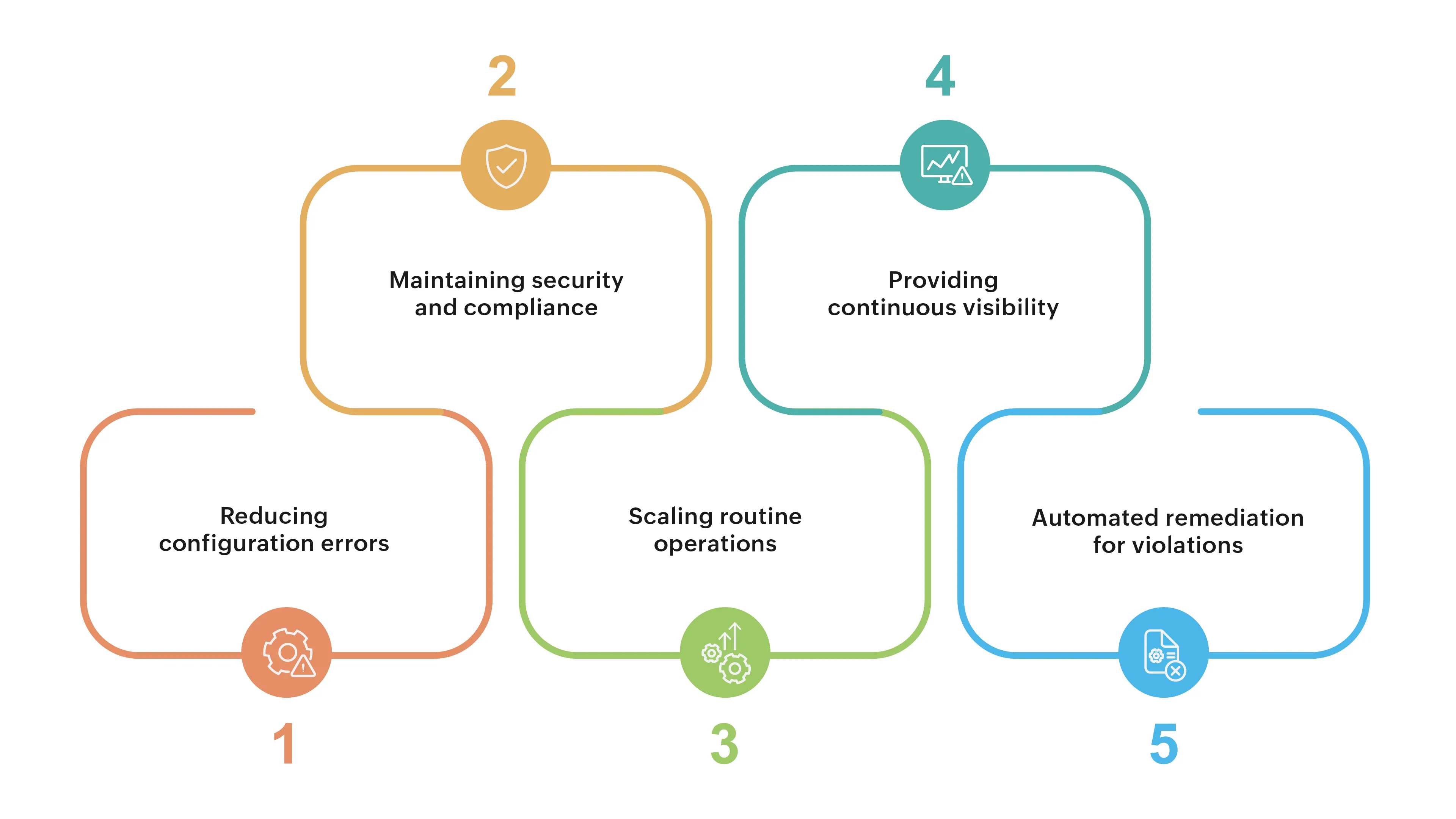
- Reducing configuration errors: Manual changes often result in misconfigurations, which can cause outages, degrade performance, or block access to critical subnets. Automation ensures consistency and minimises human error.
- Maintaining security and compliance: Staying compliant with industry standards (like HIPAA, or NIST) is vital. Automation tools continuously audit device configs, flag violations, and help enforce security policies at scale.
- Scaling routine operations: Need to enable SNMPv3 on 20,000 devices? A task that would take weeks manually can be done in minutes with automation, freeing your team for higher-level tasks.
- Providing continuous visibility: Automated tools offer 24/7 monitoring, version tracking, and alerting. Even when you're not on-site, you can stay informed and respond quickly to any unexpected changes or failures.
- Automated remediation for violations: Whenever a compliance violation appears, admins can use remediation templates created earlier while defining custom policies. This resolves issues quickly without manual rework.
ManageEngine Network Configuration Manager: A must-have network automation tool
ManageEngine Network Configuration Manager combines automation, configuration control, and visibility to help admins manage multi-vendor networks without manual device logins or scattered scripts. It removes repetitive work, keeps configurations consistent, and gives teams full visibility into what is happening across their infrastructure.
Instead of forcing admins to jump between tools or wait for issues to appear, Network Configuration Manager creates a steady and controlled way to run day-to-day operations. It brings the essential pieces of configuration management into one place such as:
- Automated configuration backups
- Stronger change management
- Automation with Programmable Configlets
- Continuous compliance enforcement
- Firmware vulnerability insights
- Dashboard and reports
Automated configuration backups
Network Configuration Manager captures configuration changes automatically. When someone logs out of a device, the syslog message is detected, a backup is triggered, and the new file is compared with the previous version. Only versions that actually contain changes are stored securely, keeping your version history clean and reliable. Admins can also schedule backups whenever they need, including hourly, daily, weekly or monthly, ensuring that critical devices are always protected.
Stronger change management
Every configuration change is reported instantly through email, SNMP traps, syslog or ticketing tools, giving teams clear visibility into what changed, when it changed and who made the change. If an unauthorized change is detected, Network Configuration Manager alerts the team immediately so they can take action before it spreads further. And if a change results in errors or an unstable configuration, the rollback capability can restore the last known good version, ensuring the network continues to run smoothly.
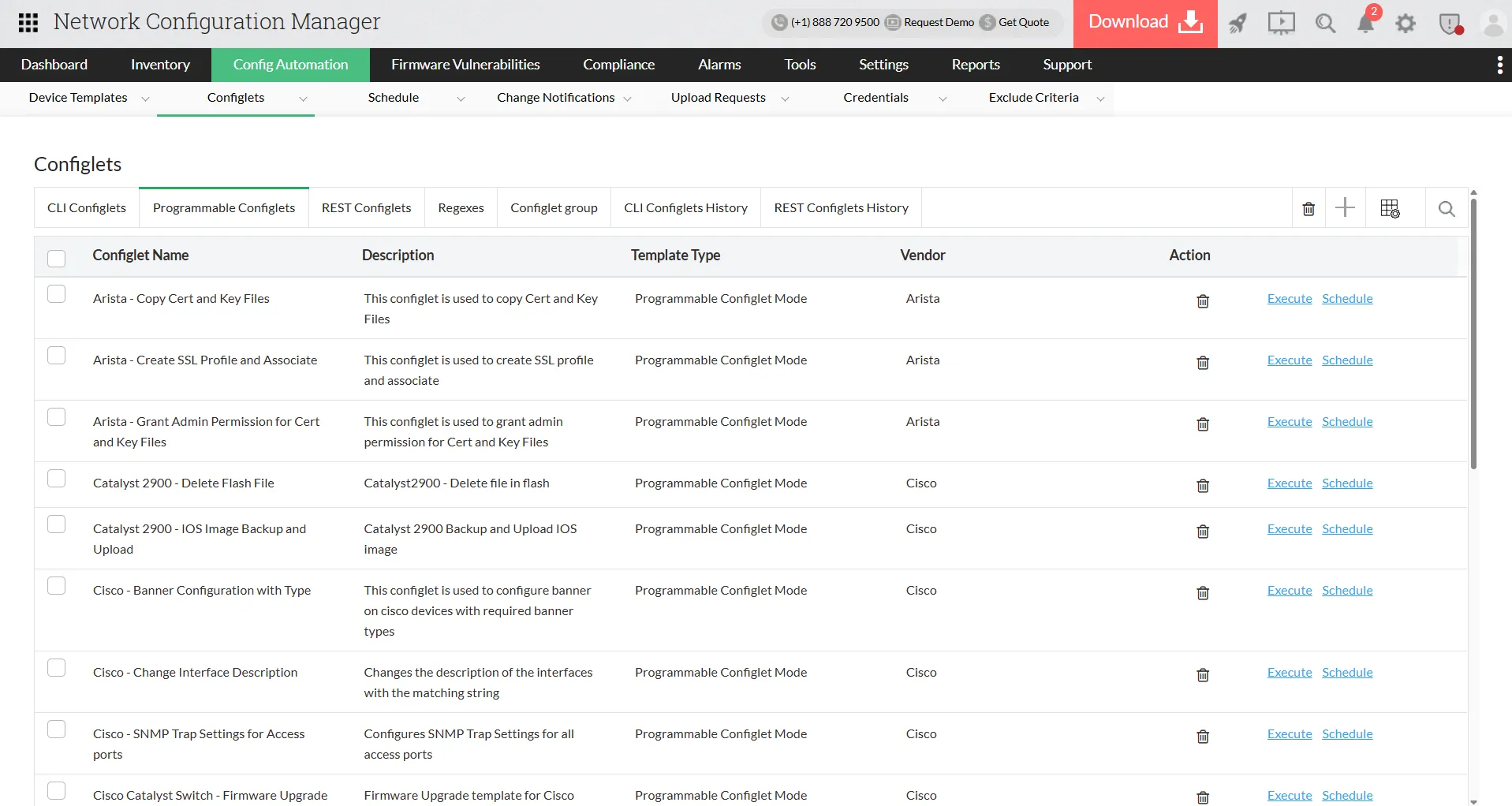
Automation with Programmable Configlets
Programmable Configlets act as advanced script templates that allow admins to automate complex tasks across multiple devices with precision. They are ideal for large-scale configuration updates, structured patch deployment and enforcing organization-wide changes without manual effort on each device. Because they support logic, variables and conditional actions, Programmable Configlets give teams far more control than basic scripts. They can also be scheduled, ensuring recurring tasks run reliably in the background while admins focus on higher-priority operational work.
Continuous compliance enforcement
Network Configuration Manager continuously checks device configurations against compliance standards such as CIS, SOX, and HIPAA, as well as any custom policies created by the organization. If a violation appears, it is highlighted immediately and can be fixed using a remediation Configlet. This helps maintain consistent, audit-ready compliance across the network.
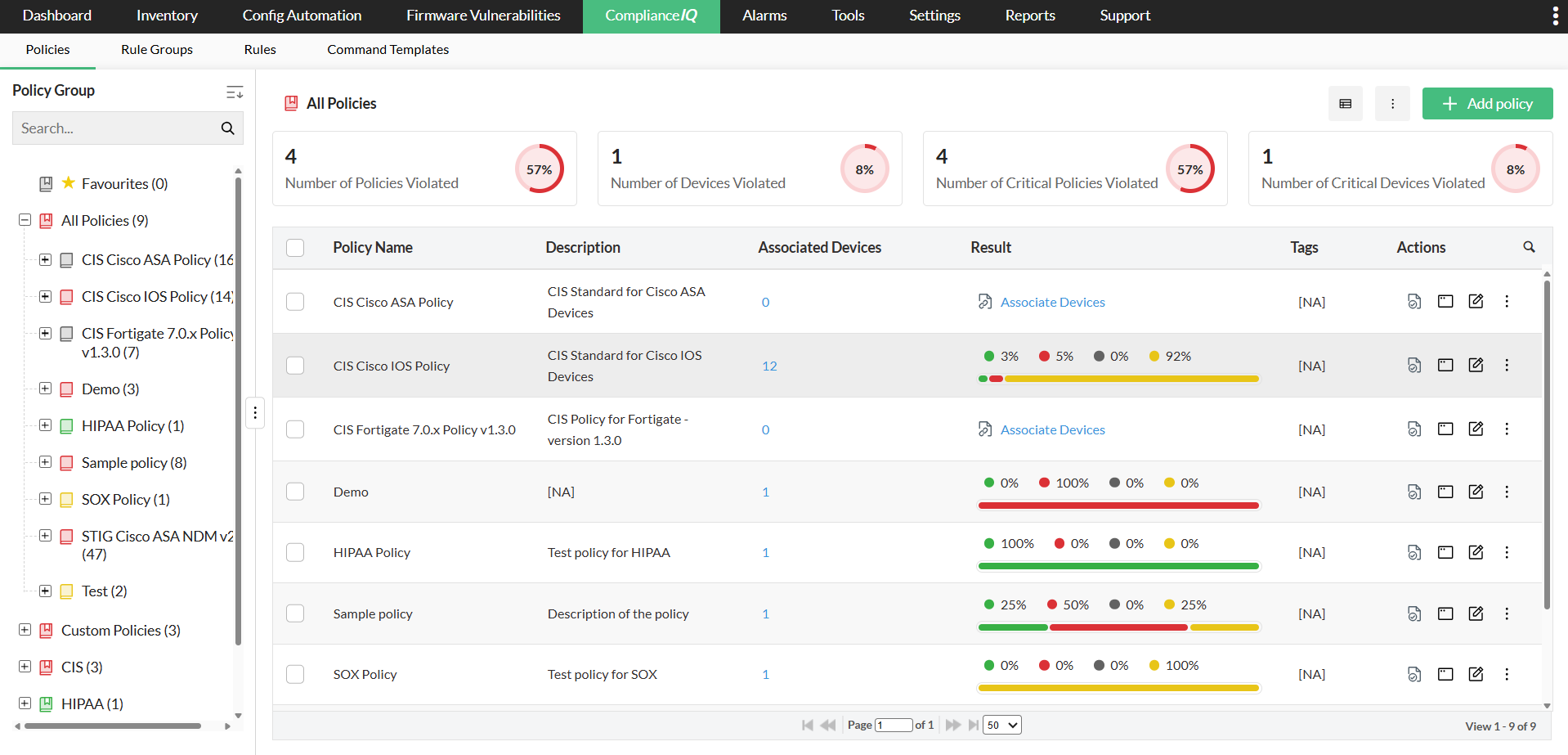
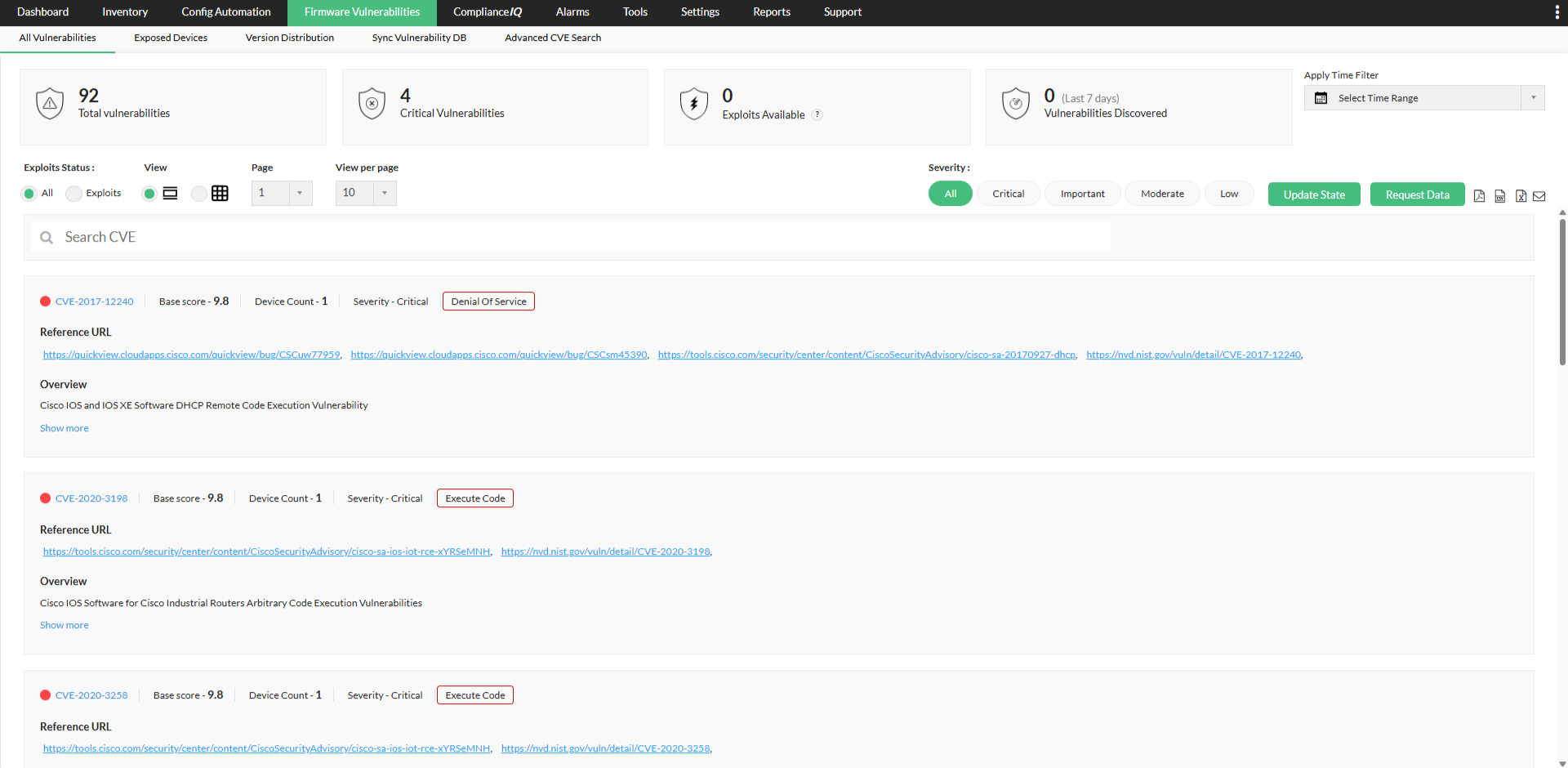
Firmware vulnerability insights
Network Configuration Manager retrieves vulnerability information from NIST every day and matches it with your device firmware versions. It flags exposed devices, presents relevant CVE details, and provides severity and patch references. This gives teams clarity on which devices need immediate attention and strengthens overall security.
Dashboards and reports
The platform includes a fully customizable dashboard that gives admins a clear snapshot of backups, changes, compliance status and vulnerabilities all in one place. Detailed reports can be generated at any time, exported in multiple formats, scheduled in advance or delivered automatically after a task completes.
How Network Configuration Manager supports network automation best practices
Effective network automation is not just about running scripts. It requires a disciplined approach where changes are controlled, configurations stay consistent and teams always know the state of the network. Network Configuration Manager helps organizations put these best practices into action in a way that is structured, safe and scalable.
- Start small with safe automation: Network Configuration Manager makes it easy to begin with low-risk activities such as read-only audits, scheduled backups and compliance scans. These smaller steps help teams build trust in automation while ensuring that no live network operations are exposed to unnecessary risk.
- Apply CI/CD principles to configurations: The platform supports pre-deployment staging and scheduled roll-outs, allowing configuration updates to move through a controlled release process similar to CI/CD in software development. This prevents unstable changes from reaching production and gives admins more predictable outcomes.
- Automate rollbacks for reliability: If a configuration fails or if an unauthorized change is detected, Network Configuration Manager can immediately restore the previous stable version. This automatic rollback reduces downtime and ensures that misconfigurations never linger long enough to cause operational issues.
- Maintain detailed documentation effortlessly: Every policy, programmable template and configuration version is archived automatically. Teams gain complete visibility into what changed, who made the change and when it happened. This level of documentation is invaluable for audits, security reviews and day-to-day troubleshooting.
- Empower teams with script and template tools: Network Configuration Manager includes automation scripts, programmable Configlets and low-code templates that help both senior engineers and junior admins perform tasks accurately. These tools eliminate guesswork and ensure that changes remain consistent across devices.
- Schedule periodic validation to prevent drift: Configuration drift is one of the most common causes of outages and vulnerabilities. With scheduled scans and compliance checks, the platform continuously identifies deviations, policy violations or unapproved changes so teams can fix issues before they escalate.
The future of network automation
Network automation is evolving quickly with new technologies like AI, machine learning, and advanced analytics. Some of the emerging trends include:
- Intent-based networking: You define the desired outcome for the network, such as restricting certain applications, and the system automatically applies the right configurations to achieve that outcome.
- AI and machine learning integration: The network can detect unusual activity or potential problems and suggest or take corrective actions automatically.
- Self-healing networks: The network can identify and fix issues on its own, reducing downtime and the need for manual intervention.
- Zero-touch provisioning: Devices and network services can be set up and configured automatically, even across multiple locations and cloud environments, without manual setup.
- Automation for 5G and edge networks: With more devices and complex infrastructures, automation helps manage large-scale networks efficiently, especially at the edge of the network.
Networks are becoming too dynamic and too critical to manage manually, making automation an essential part of staying secure, compliant and efficient.
If you are ready to strengthen your automation journey, you can start a free 30-day trial of ManageEngine Network Configuration Manager or request a personalized demo to see how it fits your environment.
FAQs on network automation
What does a network automation engineer do?
A network automation engineer designs, implements, and manages automated processes for network tasks like configuration changes, backups, compliance checks, and monitoring to reduce manual effort and improve reliability.
What is the best network automation tool?
Network Configuration Manager is a comprehensive network automation tool that simplifies configuration management, automates routine tasks, enforces compliance, and provides real-time visibility across multi-vendor networks.
How can I ensure my network stays compliant with regulations?
Using automation, you can continuously monitor device configurations against standards like CIS, SOX, and HIPAA, receive instant alerts for violations, and apply remediation templates to fix issues quickly.