The Padding Oracle On Downgraded Legacy Encryption (POODLE) attack is a cyberattack that takes advantage of a vulnerability in the Secure Socket Layer (SSL) and older versions of the Transport Layer Security (TLS) protocols. This vulnerability lets perpetrators eavesdrop on or meddle with data encrypted with the SSL 3.0 and TLS 1.2 protocols (or lower). However, this exploit is no longer possible with the TLS 1.3 protocol.
An SSL or TLS protocol is something a computer uses to connect to a web server to communicate securely, encrypting the data in transit. However, the SSL protocol is about 30 years old, so it isn't entirely foolproof and is not capable of dealing with modern exploits such as POODLE. Though the SSL protocol is about three decades old, this vulnerability only surfaced around 2014, 20 years after its inception.
The POODLE vulnerability lets the attacker listen in on encrypted conversations, enabling them to steal secrets that are shared across the network such as passwords, session cookies, and file sums. This is possible due to a vulnerability in the configuration of the SSL and older versions of the TLS protocols. These protocols use different algorithms to encrypt communication between the endpoint and the web server.
Any computer that connects to a web server using an SSL or TLS protocol communicates in the form of encrypted cipher suites. Each cipher suite consists of a fixed block of data depending on the connection (either 8 bytes or 16 bytes). Each block contains data that is dependent on the previous block.
If a message that needs to be sent does not completely fill all blocks of the cipher suite, the respective protocol used to encrypt the connection fills the void blocks with junk values. This process is called padding. This padded value is then removed by the web server after decrypting the message sent using the decryption key that is established during the initiation of the connection.
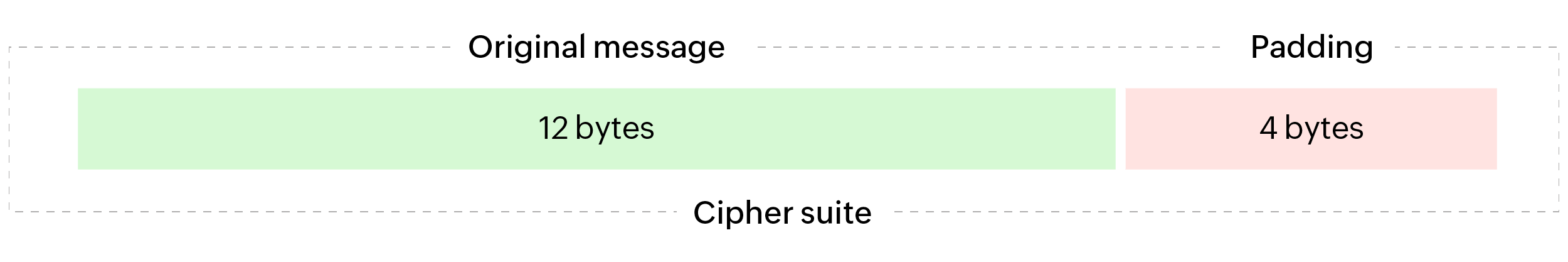
In the context of a POODLE attack, the term "oracle" refers to the web server that is capable of revealing information about a message's padding status. The man in the middle pings the oracle with messages that contain random padding values, and the oracle will decrypt the message using the key and return the padding error. Gradually, if this process is repeated multiple times, an attacker will possess enough information to assume the padding pattern. This process is called padding oracle, which exposes the fundamental systemic flaw of some SSL and TLS protocols that makes the POODLE attack possible.
To perform a successful POODLE attack, one must first complete a successful man-in-the-middle attack. By doing this, the attacker can accomplish two goals.
A man in the middle, as the name suggests, is an intermediary who taps into the connection between the primary endpoint and the web server. These types of interceptions commonly occur in unsafe public internet environments. Since the latest version of the TLS protocol is more secure and makes executing such interceptions hard, the man in the middle repeatedly pings the web server with random messages that will mislead the web server to assume that its associated encryption protocol does not match the sender's supported version. This convinces the web server to downgrade its connection to a lower SSL or TLS protocol version which is much less secure and easy to intercept. Once that is done, the man in the middle can now eavesdrop on the conversation on the channel. However, this conversation is still encrypted as demanded by the protocol.
Although the web server, or in this context the oracle, has been convinced to downgrade the connection to a lower version of the SSL or TLS protocol, the messages in the conversation are still completely, comfortably encrypted. However, during the man-in-the-middle attack, when the attacker repeatedly pings the oracle with random messages, these random messages also contain padding values. The constant pings not only make the oracle downgrade the SSL or TLS version, they also force the oracle to return a padding error for every message that was sent by the attacker.
Once the attacker has enough padding errors returned, they will be able to figure out the padding pattern. Since in a cipher suite every block's data is connected to the previous block, the padding values are enough for the attacker to decrypt the rest of the message without the private or public key set by the protocol.
Thus, the attacker conquers the 30-year-old encryption technology with a simple man-in-the-middle attack.
The only simple and obvious way to prevent a POODLE attack is to disable the web server from supporting SSL or previous TLS protocol encryption. This will eradicate the possibility of the attacker performing an SSL downgrade. However, there is an interim solution to prevent a POODLE attack: the TLS Fallback Signaling Cypher Suite Value (TLS_FALLBACK_SCSV).
The TLS_FALLBACK_SCSV is an algorithmic security input that restricts a web server from downgrading its encryption. When a client-side system connects to a server-side system by sending the Client Hello, both sides are obliged to perform an SSL or TLS handshake. This handshake defines the protocol version that will be used throughout the course of the connection.
The TLS_FALLBACK_SCSV is a signal that is sent to the server side along with the Client Hello and other messages from the client side that will instruct the server to drop all handshakes that support a lower SSL or TLS protocol version. However, this only prevents connections with handshake misunderstanding. There is nothing to say that there are not other issues that might arise on the server side that can lead to a protocol downgrade, and hence the TLS_FALLBACK_SCSV is not entirely foolproof.
Manually implementing such an intricate security specification throughout an enterprise's IT certificate inventory is a tedious task. Therefore, organizations tend to use solutions that automate the process by helping them discover, vault, share, monitor, and audit their certificates and keys centrally.
It affects all versions of the SSL and older versions of the TLS protocols, including TLS 1.2.
It is highly possible that you are also vulnerable to attacks such as BEAST (Browser Exploit Against SSL/TLS) or CRIME (Compression Ratio Info-leak Made Easy). These attacks also target vulnerabilities in SSL and TLS encryption protocols.
In the context of POODLE, the term legacy encryption refers to outdated encryption standards, specifically SSL and TLS protocol versions that are vulnerable to the POODLE attack.