The TLS/SSL handshake is a cryptographic process that happens in the background whenever a client (such as a browser) establishes a connection with the server. This handshake protocol facilitates a secure connection between the client and the server to facilitate privacy, data integrity, and confidentiality.
The TLS/SSL handshake process is triggered whenever a client tries to establish a secure connection with a server. This includes cases when:
Although the term SSL is still widely in use, TLS is the latest protocol. However, the terms TLS and SSL are interchangeably used. Similarly, the terms TLS handshake and SSL handshake are interchangeably used.
Note: TLS versions 1.2 and above are currently considered safe and are widely used so as to safeguard against cyberthreats such as POODLE attack and Heartbleed vulnerability.
During a TLS handshake, the following exchange happens between the client and the server:
The entire TLS handshake process involves several steps of back and forth communication between the client and the server. Here's a detailed analysis of all the steps involved in the TLS/SSL handshake.
TLS protocol
The TLS version supported by the client
Cipher suites
A list of the client's preferred encryption algorithms. The server can then pick an option that suits both the client and the server.
Client Random
A bunch of randomly generated characters that will help secure the handshake process.
Server Random
A bunch of random bytes generated by the server, similar to the Client Random.
TLS protocol version
The TLS version selected by the server for this session.
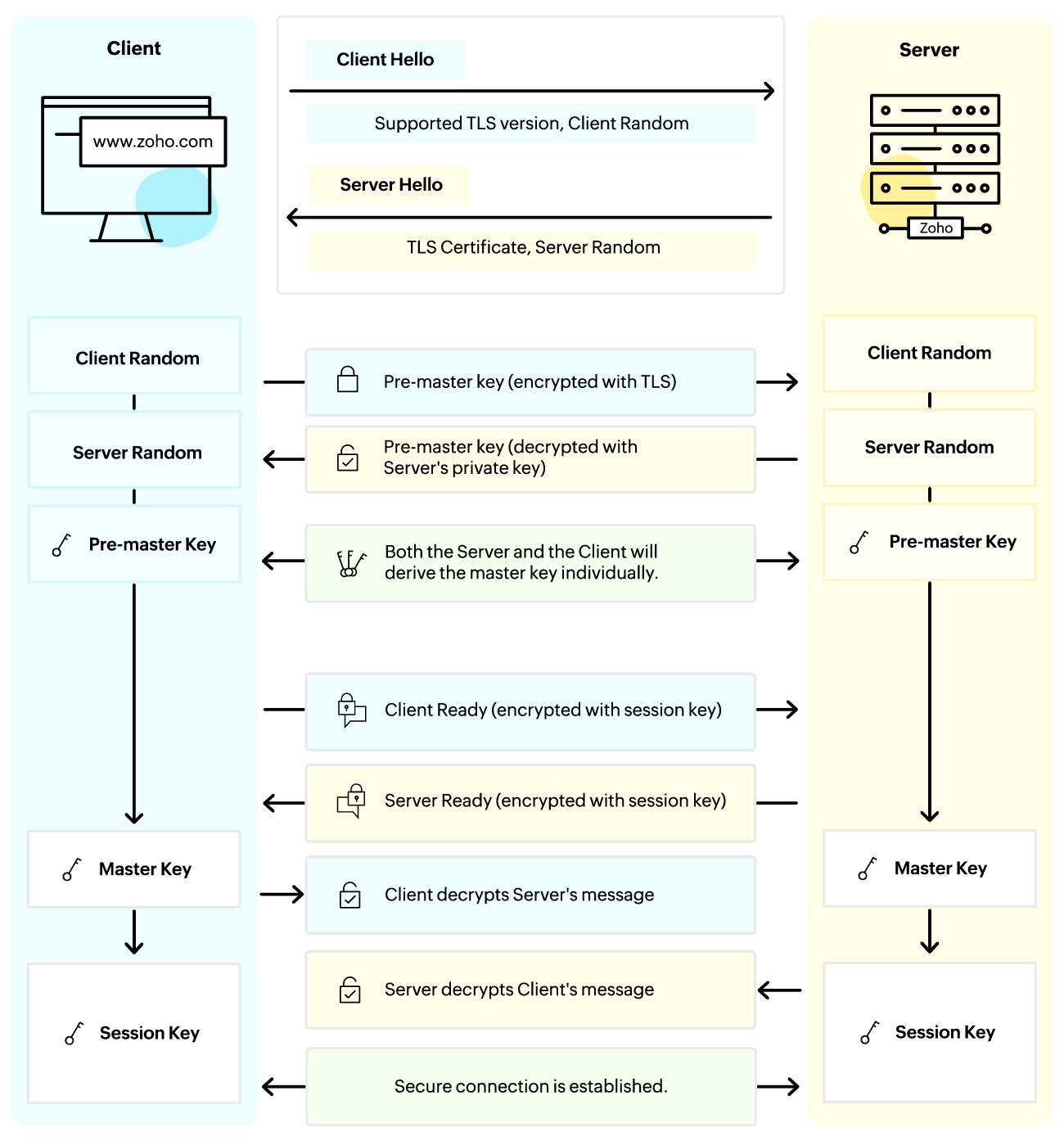
The client initiates the TLS handshake with the server by sending a hello message called the Client Hello. By default, this message will include information about the TLS protocol, Cipher suites, and the Client Random.
Other fields such as Session ID, Compression Methods, and Supported Extensions can also be included to facilitate session resumption, communicate client's support for compression, and enhance protocol capabilities.
In response to the Client Hello, the server will send a Server Hello which will include information about the TLS protocol version, Cipher suites selected by the server, and the Server Random
Other fields such as Session ID and Compression Methods will be included if sent by the Client along with the Client Random.
Along with the Server Hello, the server also presents its digital certificate to the Client. The client will authenticate the server's identity by validating this certificate with the corresponding certificate authority.
The Client then generates a premaster secret using a secure random generator. This key is used to establish a shared Secret Key between the Client and the Server, which in turn will then be used to derive the Session Key. This Session Key will be used to encrypt and decrypt the communication between the Client and the Server.
Note: The premaster key is unique and completely random for every TLS session. Thus, even if the private key of a server were to get compromised in the future, the encrypted premaster secret exchanged during the handshake will remain secure, thereby protecting past sessions from the impact of private key compromise.
The premaster secret is encrypted using the Server's public key (obtained from the TLS certificate) and is sent to the Server. This is done to ensure that only the Server can decrypt this secret. The Server will then decrypt the premaster key using its private key.
Both the Client and the Server generate the Session Key using the Server Random, Client Random, and the Premaster Key. These values should match.
The Client and the Server send a message to indicate that the handshake process is now complete.
Although most of the steps in the TLS handshake process for version 1.3 are similar to those found in version 1.2, the overall TLS handshake process varies slightly. In TLS 1.3, weak cipher suites are removed, number of back and forth requests between the server and the client is reduced to improve latency, and overall security against attacks that TLS 1.2 was vulnerable to (padding oracle attacks, renegotiation attacks, and BEAST) is upgraded.
While the handshake process in itself is secure, the TLS connection's security is based on the strength of the following:
A cipher suite is a set of cryptographic algorithms and the strength of the cipher suites plays an important factor in securing the TLS connection. It is thus important to use the latest cipher suites such as TLS_AES_256_GCM_SHA384, TLS_CHACHA20_POLY1305_SHA256, and TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA38 that are secure from vulnerabilities.
The certificate validation process ensures the authenticity and integrity of the server. However, if the process is not stringent—due to misconfiguration or non-compliance with best practices—it could lead to the acceptance of expired, revoked, or invalid certificates, thereby compromising the overall security of the TLS connection.
The server should be configured in such a way that it incorporates the TLS best practices such as disabling outdated and vulnerable protocols (protocols such as SSL), using strong cipher suites, and enforcing an encryption algorithm. Using these best practices to secure the TLS handshake process will help in establishing a secure TLS connection.
The TLS handshake protocol is responsible for establishing a secure communication channel between the client and the server. It not only secures sensitive data with strong encryption but also establishes trust by ensuring the authenticity and confidentiality of the data in transit. Thus, the TLS handshake protocol plays a vital role in ensuring secure online communication.
Cipher suites is a set of instructions that specifies the encryption algorithms and parameters used during the SSL/TLS handshake process. They play a vital role in the handshake process and help secure the communication between the client and the server. Strong cipher suites are often preferred to enhance security and reduce vulnerabilities.
As stated above, while the TLS handshake process in itself is known to be secure, it may be essential to use the latest TLS version and strong ciphers amongst other things to enhance the overall security of the TLS/SSL handshake process.
In environments with dynamic certificate management or complex network configurations, some common issues that can happen are incomplete certificate chains, expired certificates, and cipher suite mismatches during the handshake process. Such common TLS/SSL handshake issues can be addressed with proactive monitoring and maintenance.
The TLS/SSL handshake failure may happen due to reasons such as server misconfigurations, compatibility and certificate issues, and other security-related concerns. To troubleshoot such issues, verify cipher suites settings and other server-level configurations, ensure that both the client and server support compatible TLS versions and cipher suites, check the revocation status of the certificate involved, and identify other security vulnerabilities hindering the process.