How to protect your organization from Snake ransomware
Take charge and identify the checkpoints to keep your organization's data from being held hostage.
The year 2020 has taught us one thing—that prevention is better than having to find a cure. This applies to not just the novel coronavirus, but also to Snake, a notorious 2020 ransomware. Snake ransomware can stealthily encrypt your sensitive files and extort money from you. It is hard to detect Snake without a robust IT team, and an even more robust IT security solution.
In this blog, we will discuss every stage of the Snake ransomware attack, and provide practical tips for defending against this new type of attack. This might save you a lot of money some day—maybe even today!
The intrusion: How Snake ransomware enters
Phishing emails, malicious ads, web injections, and fake updates are different ways ransomware can enter a network. However, the initial point of entry for Snake ransomware is often through an insecure remote desktop protocol (RDP) connection. The best way to prevent its entry is to disable remote access for users, unless of course, it is a business requirement.
The solution: Use log monitoring tools such as ManageEngine's Log360 to instantly identify any changes made to the users' remote access rights in Group Policy. Alerts can be configured so that IT administrators are notified when specific users' remote desktop access rights change. Figure 1 shows a Log360 report, reflecting findings from the ADAudit Plus add-on, about changes made to user rights assignments.
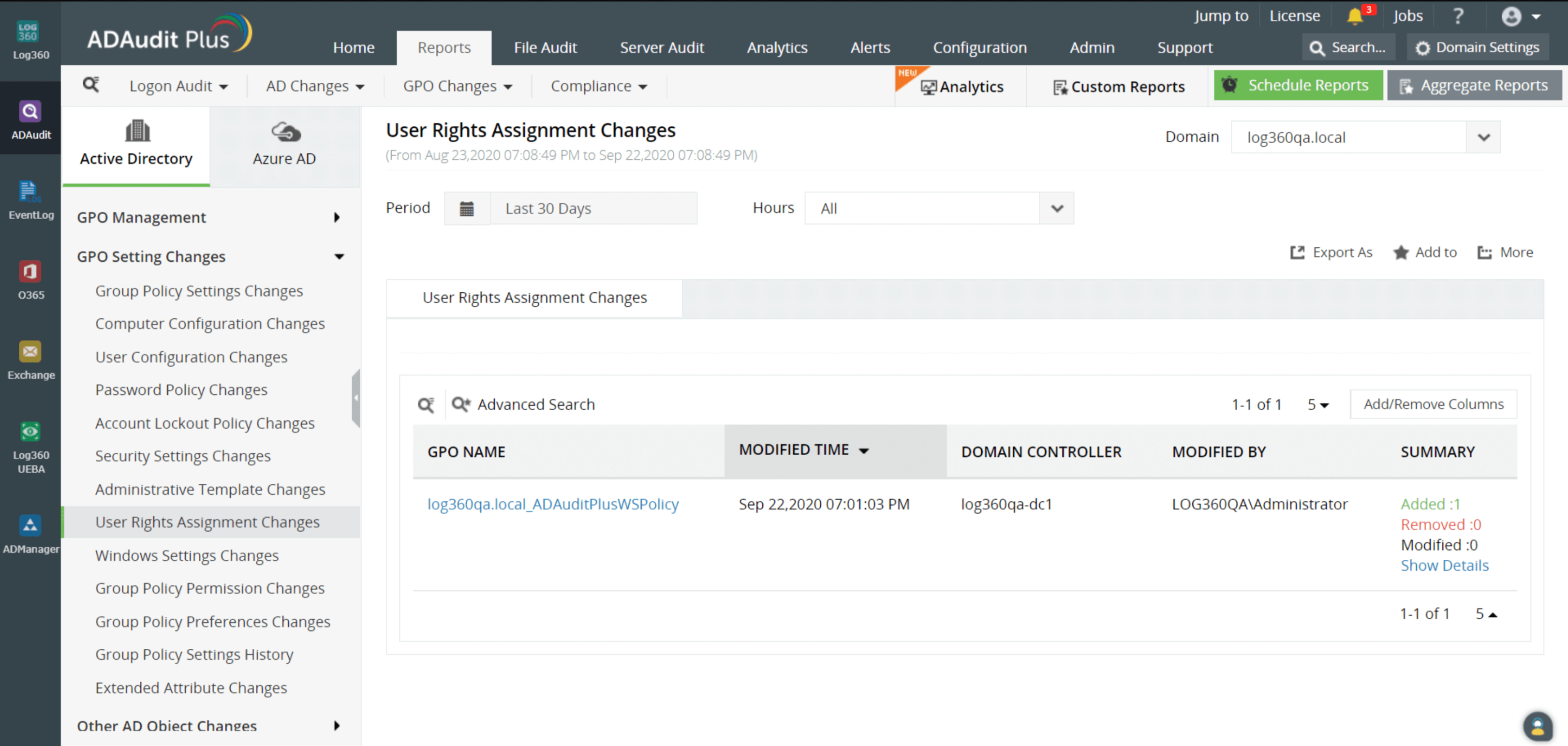 A report on changes made to user rights assignment in ManageEngine's Log360
A report on changes made to user rights assignment in ManageEngine's Log360
The installation: Has the device already been infected?
Once Snake ransomware gains an initial foothold in a machine, it registers a mutual exclusion object (mutex) marker named EKANS to crosscheck whether the machine has already been infected (EKANS is Snake spelled backwards). If the machine is found to be already infected, Snake automatically stops executing commands.
However, Snake proceeds with the attack if it confirms that the machine is not already infected.
Snake changes firewall settings
Prior to encrypting the files, Snake carries out two processes to isolate the system from communicating with the outside world. First, it modifies the Windows firewall settings to block all incoming and outgoing connections that are not already configured. Second, all communications that do not match the firewall's existing rules are blocked. A built-in tool in Windows, called netsh, is used to change the firewall configurations.
The solution: Monitoring changes in firewall configuration rules and keeping a tab of traffic in firewall connections can help spot Snake ransomware at this stage of the attack.
Snake deletes the backed up data
Another important characteristic of Snake ransomware is that it looks for and deletes volume shadow copies, the backup copies of computer files created in Microsoft Windows systems, so that the victim has no data recovery options. Quick detection of the problem is key to control the damage.
The solution: With the file integrity monitoring capability of ManageEngine's Log360, administrators can instantly receive alerts when files are changed or deleted. Figure 2 shows a sample report from Log360's file integrity monitoring as reflected in findings from the ADAudit Plus add-on.
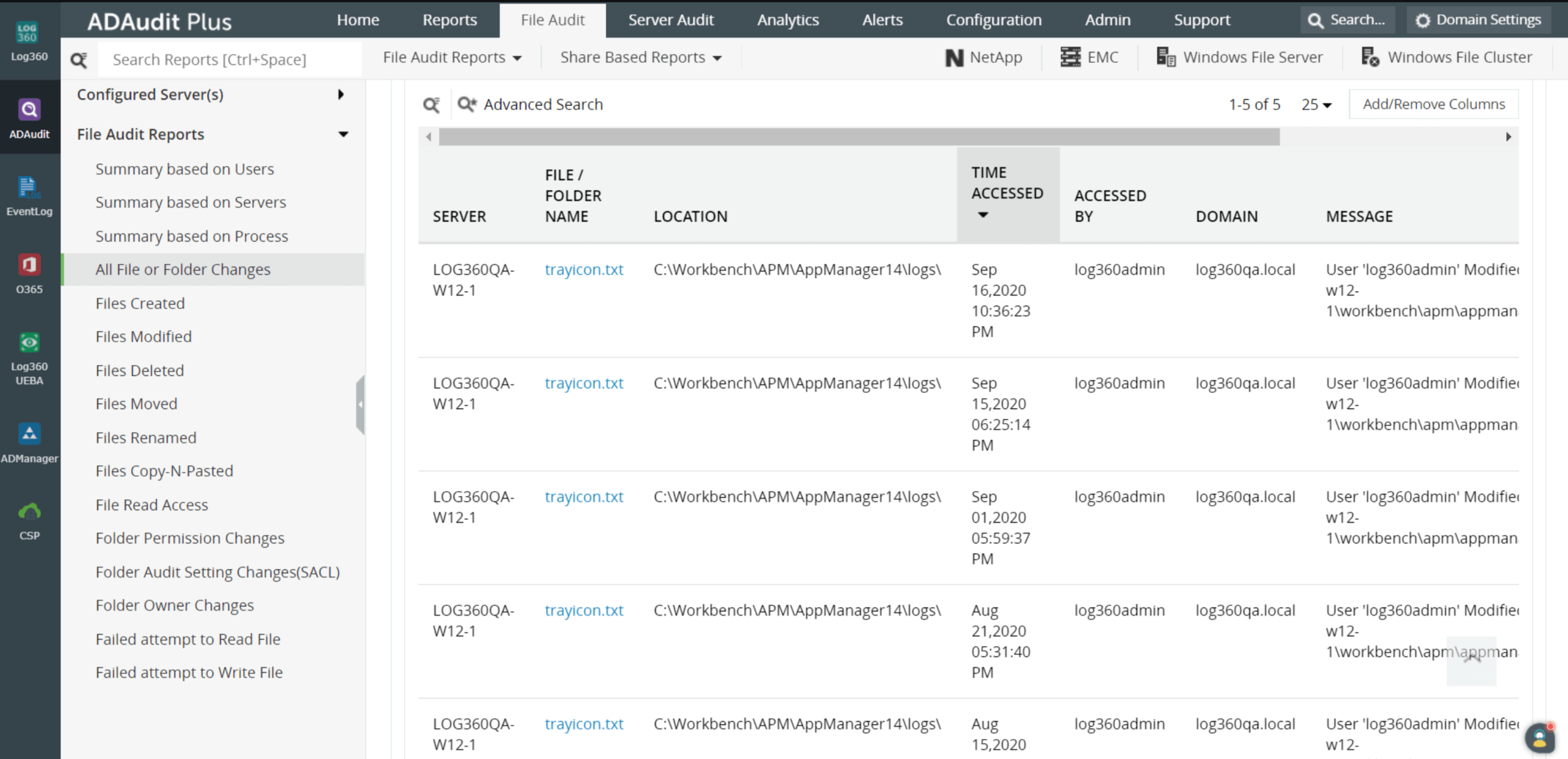 All file or folder changes report on ManageEngine's Log360
All file or folder changes report on ManageEngine's Log360
Snake kills automated processes
After deleting the shadow copies, Snake uses pre-written code to kill numerous processes such as machine automation processes crucial for the operation of manufacturing units, remote management tools, virtual machines, network management, and more.
Prolonged downtime and production stoppages lead to enormous pressure on the victim to pay the ransom. Now you can recognize that processes grinding to a halt in your organization might indicate a Snake attack. Act quickly to defend your infrastructure!
Until this point, your data is still available to you. You should have identified that there is a cybersecurity issue through the various detection methods mentioned above.
Let's see what happens in case you don't detect any of the signs of a Snake attack.
The encryption begins
Snake ransomware starts encrypting your files. System files and folders are left unencrypted by this sneaky ransomware so that you can still log on to your system, and not get suspicious.
After encrypting all the targeted files, the ransomware renames them. A random 5-character string is appended to the file extension to hide itself from signature ransomware detection methods. For example, a file named "finance.doc" may be renamed as "finance.dochGDyf", and a file named "santa.py" may be renamed as "santa.pyDQulKh."
The detection tool is outsmarted!
You may think that you can use solutions that alert you instantly when files are renamed. True, but that would be too late. Snake first encrypts all the target files, and then starts to rename them. By the time you receive an alert that files are being renamed, the encryption is over, and the damage is done.
It's all about the $$$
To decrypt the files, Snake asks for ransom through a text file, "Fix-Your-Files.txt", left on the victim's desktop. To gain the victim's trust, the attacker may offer a free decryption of any three encrypted files.
Other measures you could take to protect your organization from Snake ransomware include:
1. Monitor user logons: Users can log on using RDP, Remote Authentication Dial-In User Service (RADIUS), and virtual private networks (VPNs). You should monitor each of these logon types, and analyze both the source computer name and the source IP address. Any unusual activity should be detected immediately, and action should be taken if tell-tale signs of attacks are noticed.
2. Analyze if attackers are attempting to hide their tracks: After gaining a foothold, attackers attempt to hide their tracks by deleting event logs. After doing this, they may attempt to change audit policies so that subsequent actions are not logged. You should be able to detect both of these malicious activities.
3. Look for unusual software installations: If suspicious software is being installed anywhere in your organization's network, you should be able to detect it. Log360 helps you establish an automated incident response, and helps you detect atypical installations in real time so you can take immediate action.
4. Block the hash: Certain versions of the Snake ransomware can be stopped from executing by blocking the malware's hash. These two hashes are key indicators of compromise:
(i) SHA256 e5262db186c97bbe533f0a674b08ecdafa3798ea7bc17c705df526419c168b60
(ii) MD53d1cc4ef33bad0e39c757fce317ef82a
5. Implement multi-factor authentication (MFA): MFA should be implemented at all user touchpoints if possible. Even two-factor authentication helps deter attackers.
By following these safety measures, you can protect your organization not only from Snake ransomware, but also from worms, trojan horses, spyware, and other malicious malware lurking around your network.
Take the right steps to defend your organization from Snake ransomware
Download a free trial version of Log360