On this page
Overview of India’s DPDP Act
The journey towards a comprehensive data protection law in India has been long and deliberate. The genesis of the Digital Personal Data Protection Act (the DPDP Act or the DPDPA) lies in the landmark 2017 Supreme Court judgment in the case of Justice K. S. Puttaswamy (Retd.) vs Union of India, which unequivocally recognized the right to privacy as a fundamental right under Article 21 of the Indian Constitution. This verdict served as the constitutional bedrock for the creation of a dedicated data protection framework. The government, recognizing the need for a modern and adaptable law, embarked on a multi-year process of public consultation and legislative drafting, culminating in the passing of the DPDP Act in August 2023.
The key objective of the Act is to provide for the processing of digital personal data in a manner that recognizes both the right of individuals to protect their personal data and the need to process such data for lawful purposes. It seeks to balance the interests of the individual—the Data Principal—with the needs of businesses—the Data Fiduciaries—that drive the digital economy. The Act aims to create a relationship of trust by specifying clear obligations for those who handle data and providing recourse for individuals if their data is mishandled.
The scope and applicability of the DPDP Act are broad. It applies to the processing of digital personal data within India. Critically, it also has extraterritorial application, meaning it covers the processing of personal data of Data Principals in India; even if the processing occurs outside the country, this applies so long as it is in connection with offering goods or services to individuals in India. This broad reach ensures that foreign companies with a significant presence in the Indian market cannot evade compliance. The Act applies to both the public and private sectors, encompassing a vast range of entities from government ministries to multinational corporations and small startups.
The DPDPA: Back to basics
The Act defines a Data Principal as the individual to whom the personal data relates and a Data Fiduciary as any person who determines the purpose and means of processing personal data. A Data Processor is a person who processes personal data on behalf of a Data Fiduciary. The Act places a clear and non-delegable responsibility on the Data Fiduciary for all data processing activities, even those carried out by a Data Processor.
Data Principals are granted several fundamental rights:
Conversely, Data Fiduciaries have a corresponding set of obligations, including implementing reasonable security safeguards, providing clear and transparent notice, and obtaining valid consent.
The financial repercussions for non-compliance with the DPDP Act are significant. The penalties are designed to be a strong deterrent. For example, a failure to implement reasonable security safeguards to prevent a personal data breach can lead to a fine of up to ₹250 crore. This is a clear signal from the government that data security is not an optional add-on but a fundamental requirement. Furthermore, a failure to notify the Data Protection Board and affected Data Principals of a personal data breach can result in a penalty of up to ₹200 crore. These steep fines highlight the seriousness with which the Act views data security and transparency. A study by a global consultancy firm projected that as much as 80% of Indian businesses are unprepared for the full scope of DPDPA compliance, particularly regarding cross-border data transfers, underscoring the urgent need for a clear and actionable strategy for CISOs.
DPDP Act: Core principles governing cross-border transfers
The DPDP Act's approach to cross-border data transfers is one of its most distinctive features and a key consideration for CISOs, as it deviates from the adequacy model seen in regulations like the GDPR. Under the DPDP Act, cross-border transfers are governed by Section 16, which adopts a negative list approach. This is a fundamental principle that sets India's law apart.
Instead of creating an allowlist of countries that are deemed to have adequate data protection laws and allowing transfers only to those jurisdictions, the DPDP Act takes the opposite approach. The default position is that all cross-border data transfers are permitted, with the caveat that the Central Government may, by notification, restrict the transfer of personal data to a specific country or territory. This negative list or blocklist model is designed to facilitate global data flows while providing the government with the power to intervene and protect Indian Data Principals if a particular jurisdiction is deemed to pose an unacceptable risk.
This approach is highly significant for the global digital economy. It provides a degree of flexibility for businesses, as they do not need to seek pre-approval for transfers to every country. However, it also introduces a degree of uncertainty. Companies must remain vigilant and continuously monitor for any government notifications that may add a new country to the restricted list. This requires a dynamic and adaptable compliance framework, a responsibility that often falls squarely on the CISO's shoulders.
It is crucial to understand that even when a transfer is made to a country that is not on the negative list, the Data Fiduciary still has a series of contractual and security obligations. The DPDP Act does not absolve the Data Fiduciary of its responsibility to protect the data once it has been transferred.
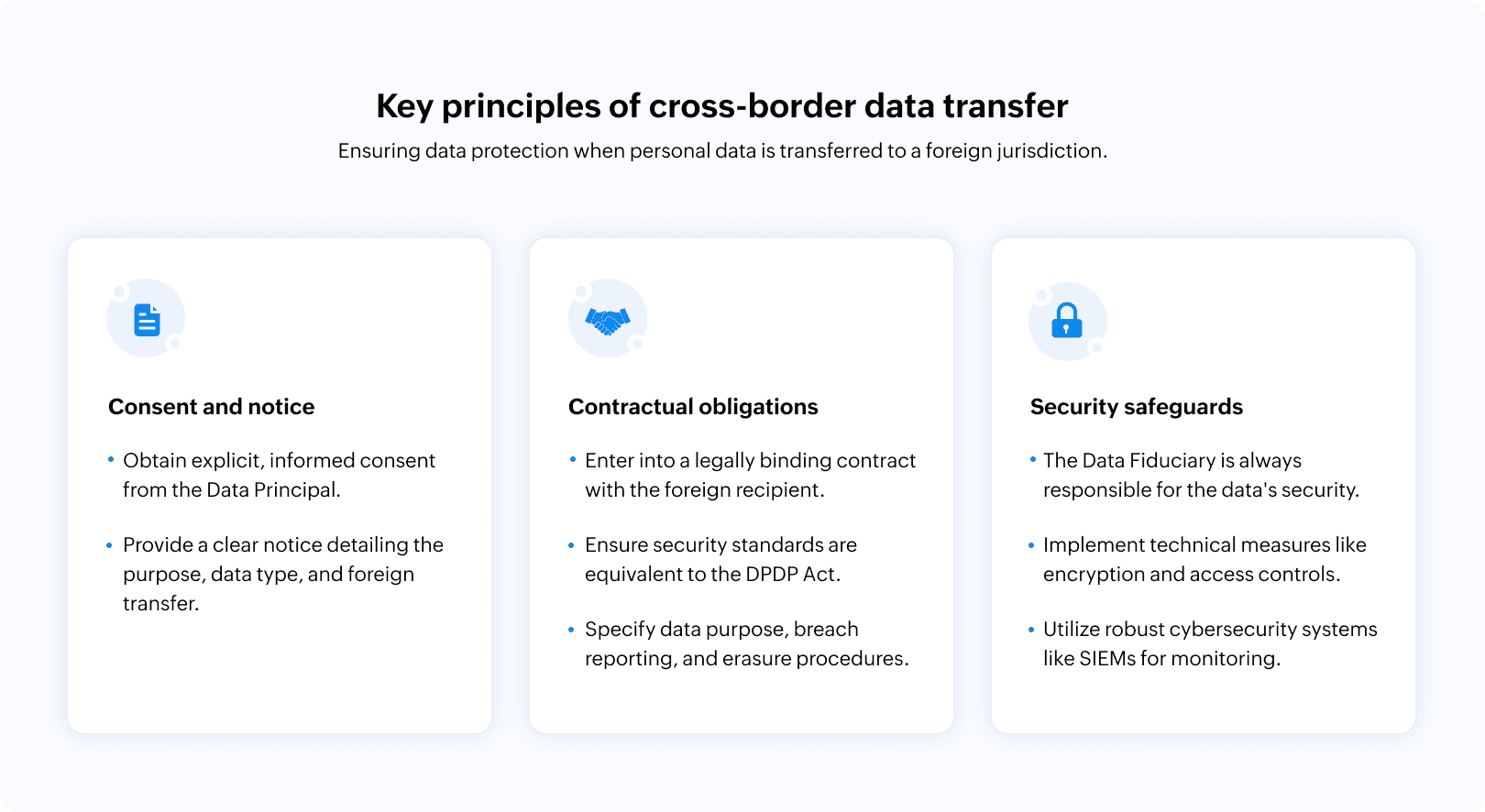
Checklist for lawful cross-border data transfers under the DPDPA
Achieving and maintaining compliance with the DPDP Act's provisions for cross-border transfers requires a structured and proactive approach. For a CISO, this is not merely a legal exercise but a core part of the enterprise's risk management strategy. The following guidelines provide a roadmap for Data Fiduciaries to ensure their data transfers are lawful and secure.
1. Pre-transfer due diligence and risk assessment
Before initiating any cross-border data transfer, thorough due diligence and a risk assessment must be conducted. This is not merely a formality but a critical exercise to identify and mitigate potential risks. This assessment should include:
- Jurisdictional analysis: Evaluate the data protection laws and regulatory environment of the recipient country. While the DPDP Act employs a negative list, understanding the local laws is essential to ensure that the recipient can uphold the contractual obligations to protect the data.
- Recipient assessment: Scrutinize the recipient’s data handling practices, security posture, and past compliance record. This includes assessing their technical and organizational safeguards.
- Data mapping: Accurately map the personal data to be transferred. This involves identifying the specific types of data, the volume, and its sensitivity. Knowing what you are transferring is the first step to protecting it.
- Purpose limitation: Clearly define and document the specific, lawful purpose for which the data is being transferred. This aligns with the DPDP Act's principle of purpose limitation and helps prevent misuse.
2. Mandatory elements in contracts
The contract between the Data Fiduciary in India and the recipient entity abroad is the cornerstone of DPDPA compliance. For a CISO, this is a critical legal and technical document. This contract must be more than a boilerplate agreement; it must be a legally binding document that reflects the specific obligations under the DPDP Act. Key elements to include are:
- Security standards: Mandate the use of reasonable security safeguards that are at least equivalent to those required under the DPDP Act. This can be benchmarked against international standards like ISO 27001.
- Data Principal rights: Ensure that the foreign entity is contractually obligated to assist the Data Fiduciary in fulfilling the Data Principal's rights, such as the rights to correction, erasure, and access.
- Breach reporting: Establish clear and rapid breach reporting protocols. The foreign entity must be required to notify the Indian Data Fiduciary without undue delay upon discovery of a data breach. This is critical for the Data Fiduciary to meet its own notification obligations to the Data Protection Board and the affected Data Principals.
- Sub-processor management: If the foreign entity plans to use sub-processors, the contract must require prior approval from the Data Fiduciary and ensure that the same DPDPA-equivalent obligations are trickled down to the sub-processors.
- Return or deletion of data: Specify the conditions under which the data must be returned or deleted upon the termination of the contract or once the purpose of processing is fulfilled.
3. Security safeguards required (technical and organizational)
The DPDP Act's requirement for reasonable security safeguards is not abstract. It necessitates the implementation of concrete technical and organizational measures. This is the domain of the CISO.
Technical safeguards:
- Encryption: Data must be encrypted both at rest (when stored) and in transit (when being transferred). This is a foundational security measure.
- Access controls: Implement robust access control mechanisms to ensure that only authorized personnel can access the personal data. This includes role-based access, multi-factor authentication, and regular access reviews.
- Network security: Deploy firewalls, intrusion detection or prevention systems, and network segmentation to protect the data processing environment.
- SIEM solution: This is where a modern cybersecurity approach truly shines. A SIEM
solution
is a powerful tool for DPDPA compliance. It works by collecting, normalizing, and analyzing
a massive volume of log data and events from across an organization's entire IT
infrastructure—including servers, network devices, and applications—in real time. This
provides a unified and centralized view of the security posture. For cross-border data
transfers, a SIEM solution can be invaluable in several ways:
- Real-time threat detection: It can detect anomalous behavior or suspicious activities related to the transferred data, such as unauthorized access attempts or unusual data exfiltration patterns.
- Breach identification: By correlating events from different systems, a SIEM solution can rapidly identify a personal data breach, even if it originates with a foreign Data Processor. This allows the Indian Data Fiduciary to meet its timely notification obligations.
- Audit and reporting: A SIEM solution provides a comprehensive audit trail of all data access and processing activities, which is critical for demonstrating compliance to the Data Protection Board in the event of an investigation. It can generate reports to prove that reasonable security safeguards were in place. SIEM systems are not a magic bullet, but they are a force multiplier for security teams, providing the visibility and intelligence needed to effectively protect data in a globally distributed enterprise.
Organizational safeguards:
- Data protection policies: Develop and enforce clear, comprehensive data protection policies that apply to all employees and contractors, both in India and abroad.
- Employee training: Conduct regular training for employees on data protection principles, security best practices, and their responsibilities under the DPDP Act.
- Vendor management: Establish a robust vendor management program to continuously monitor the compliance of all Data Processors and foreign entities with whom data is shared.
- Incident response plan: Create a detailed incident response plan that specifically addresses personal data breaches, including clear steps for notification, containment, and remediation.
4. How to prepare for government notifications and adaptability
The negative list approach of the DPDP Act necessitates an agile and adaptable compliance strategy. Organizations shouldn't just wait for a notification to react; they must be prepared to act swiftly if there is an addition to the list. For CISOs, this means:
- Scenario planning: Conduct scenario-based planning for what would happen if a key jurisdiction is added to the negative list. This includes identifying alternative data storage and processing locations.
- Building redundancy: Where possible, organizations should build redundancy in their data processing infrastructure so that if a transfer to one country is restricted, they can quickly pivot to another compliant jurisdiction.
- Engaging with legal counsel: Work closely with legal and compliance experts who can provide timely updates and guidance on regulatory changes.
- Documentation and record-keeping: Maintain meticulous records of all data transfers, contracts, and security measures. In the event of a government inquiry, this documentation will be a primary defense.
Translating the DPDPA into actionable metrics: A CISO's guide to cross-border data compliance
For CISOs specifically, the challenge with DPDPA implementation lies in turning regulatory principles into measurable, monitorable outcomes. The following industry-specific metrics offer a practical lens to assess compliance, detect anomalies, and reinforce governance. These aren’t exhaustive, but they provide a strong foundation for aligning security operations with DPDPA mandates across sectors like healthcare, education, BFSI, and IT and IT and engineering services (ITES).
Healthcare industry
1. Unauthorized access attempts on patient data from foreign IPs
- Insights: Frequent or repeated unauthorized access attempts originating from foreign IP addresses signal a potential breach or misuse of sensitive healthcare data. Monitoring this metric helps ensure that cross-border access controls—including IP filtering and geo-restriction policies—are functioning properly, which is critical for maintaining patient confidentiality and meeting the DPDPA’s mandate of reasonable security safeguards. Promptly flagging and investigating such attempts reduces the risk of data leakage or non-consensual data access, which could trigger regulatory penalties and reputational damage.
- Implication for the DPDPA: Demonstrates enforcement of reasonable security safeguards and adherence to consent-based data sharing under the DPDP Act.
2. Incidents of data transfer outside approved purposes (e.g., clinical trials or research)
- Insights: Tracking data transfer incidents for purposes beyond explicit consent (e.g., unauthorized clinical trial use or sharing beyond emergency exemptions) provides a direct compliance validation tool. This metric helps verify that contractual restrictions, anonymization, and data minimization principles are honored. Elevations or spikes in such out-of-scope data use events could indicate process breakdowns or insider misuse, requiring rapid remediation to avoid DPDPA violations and loss of stakeholder trust.
- Implication for the DPDPA: Ensures contractual compliance mandates restricting data use are being respected, preventing misuse under clinical exemptions or emergency provisions.
Education industry
1. Unusual login events on learning management systems or student information systems from foreign IPs
- Insights: Since educational data often includes minors’ personal information, detecting unusual foreign login activity helps prevent unauthorized access and enforces parental consent requirements under the DPDPA. This metric strengthens data governance by confirming that the institution’s access policies effectively exclude unverified or suspicious international accesses, thereby reducing exposure to data breaches and compliance violations, especially those involving children’s data protection provisions.
- Implication for the DPDPA: Supports verification of verifiable parental consent and sector-specific safeguards for minors' data transfers.
2. Data export events outside approved platforms or vendors
- Insights: Monitoring data export beyond authorized systems or vendors reveals potential gaps in third-party risk management and vendor due diligence frameworks. Given the diversity of EdTech providers, this metric allows CISOs to spot unexpected or unauthorized cross-border flows early, preventing accidental non-compliance with DPDPA vendor oversight and contractual safeguards. It also supports ongoing audits and accountability in digital education ecosystems.
- Implication for the DPDPA: Enforces vendor due diligence and contractual adherence requirements for overseas EdTech or cloud providers.
BFSI industry
1. Real-time alerts on suspicious outbound cross-border data flows
- Insights: BFSI institutions operate under stringent regulatory scrutiny, and any unexplained outbound flow of sensitive finance-related data can be an indicator of fraud, an insider threat, or non-compliance with DPDPA and RBI or SEBI overlays. This metric provides near-instant visibility of anomalous data transfers, empowering rapid incident response teams and minimizing exposure windows for breaches. It is vital for meeting the dual compliance and operational security mandates specific to BFSI.
- Implication for the DPDPA: Critical for timely breach reporting and aligns with RBI or SEBI mandates layered on top of the DPDPA.
2. Unauthorized access or policy violations from foreign locations on core banking systems
- Insights: Core banking system access patterns are highly sensitive and any deviations from cross-border access policies highlight potential unauthorized intrusions or improper use. Tracking this metric ensures that only authorized personnel within permitted geographies or through approved channels access critical financial data, supporting compliance with the DPDPA’s data localization and restricted transfer provisions. It strengthens the integrity of anti-money laundering and fraud prevention controls as aligned with sector regulations.
- Implication for the DPDPA: Demonstrates governance over sector-specific data localization and transfer restrictions.
IT and ITES industries
1. Volume and destination analysis of cross-border data transfers
- Insights: Detailed metrics on how much data is transferred and to which countries are essential for assessing adherence to the DPDPA’s negative list and contractual requirements. This metric offers transparency at scale, enabling IT CISOs to quickly identify if data is being transferred to government-prohibited regions or beyond contractual terms. It facilitates risk-based decision-making, compliance reporting, and strategic adjustments in subcontractor or cloud service provisioning.
- Implication for the DPDPA: Shows compliance with government blocklisting restrictions and contractual safeguards in global service delivery.
2. Incident rate of unauthorized data transfers or anomalous data access events in foreign cloud environments
- Insights: Given the IT and ITES industries' complex supply chain and multi-cloud ecosystems, monitoring anomalous events and unauthorized transfers in foreign cloud environments is crucial for maintaining consistent DPDPA compliance. This metric helps reveal gaps in sub-processor governance, cloud security posture, or automated controls, which might otherwise go unnoticed. The incident rate trend analysis enables proactive adjustments in security architecture, minimizing compliance risk and enhancing trust with global clients.
- Implication for the DPDPA: Enables scalable, automated monitoring necessary for complex sub-processor governance and regulatory compliance.
Each of these metrics provides CISOs with actionable insight and KPIs to manage and demonstrate effective governance over cross-border data flows. By leveraging SIEM for continuous monitoring, organizations can rapidly detect, investigate, and remediate anomalies or violations, enabling a practical, evidence-based approach to meeting India’s DPDP Act obligations.
Related solutions
ManageEngine AD360 is a unified IAM solution that secures digital identities with adaptive MFA and role-based access control—helping prevent insider threats, even if credentials are compromised.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM platform that combines UEBA, DLP, CASB, and SOAR to detect threats, protect networks, monitor the dark web, and automate response—reducing breach impact and compliance risk.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
