Security fundamentals
Hiranmayi is a cybersecurity specialist at ManageEngine, the IT management division of Zoho Corporation. A thought leader and an accomplished writer, she has authored numerous blogs, articles, and e-books exploring the latest trends and challenges in cybersecurity. Her expertise focuses on User and Entity Behavior Analytics, and Cybersecurity Strategy and Leadership. Through her work, Hiranmayi aims to empower businesses with actionable insights to strengthen their security posture and stay ahead of emerging threats.

Security fundamentals

Education
Healthcare

BFSI

Threatscape

Tech central

Tech central

Tech central

Tech central

Healthcare

Education

Threatscape

Threatscape

Threatscape

Healthcare

BFSI
Security fundamentals

Security fundamentals

Security fundamentals

Security fundamentals

Security fundamentals

Infographics

Infographics

Infographics
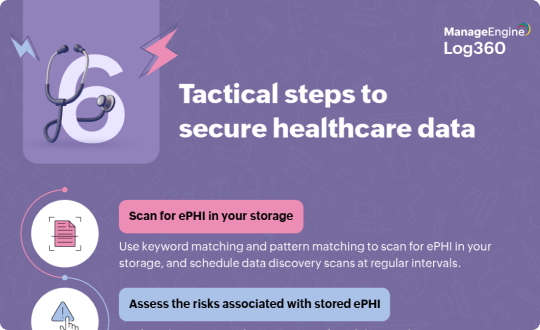
Infographics

Infographics
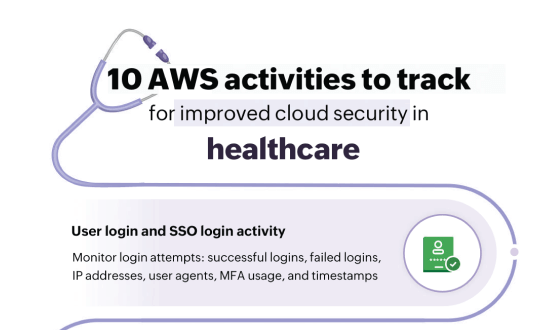
Infographics

Infographics

Infographics