BYOD describes the trend of employees using their private mobile devices to access corporate data. But employees accessing sensitive corporate data and applications on their personal devices present a huge risk to data security. Hence organizations must take adequate measures to protect corporate data and user privacy by deploying a mobile device management solution. Mobile Device Manager Plus provides various options to securely manage personally-owned devices while preserving users' privacy as explained below.
Managing Personally-owned devices
When managing personally-owned devices, organizations must ensure that they don't invade an individual's privacy. Thus, with MDM, personal devices are provisioned as Profile Owner, which creates a Work Profile, a logical container that seperates personal space from work space. The IT Admin will have control only over the work space and has zero control over the personal space. Any policies distributed through MDM will be applied only to the work profile and only the apps distributed through MDM will be managed, thus restricting Admin's access to data present in personal apps. You can identify the managed apps by the work badge icon that is displayed on the apps' icons.
Enrolling Personally-owned devices using Android Management API (Agentless Management)

The Android Management API, provided by Google, is a powerful tool that enables the integration of Android UEM features into Mobile Device Manager Plus. With this API, you can efficiently manage Android Enterprise devices without the need to install a client app on individual device. his streamlined approach allows for efficient and centralized management of Android devices through Mobile Device Manager Plus.
Features supported by Profile Owner
Profile Owner supports features such as
- Prevent sharing of data from workspace profile to personal profile.
- Restricting installation or uninstallation of apps.
- Restricting screen capture in workspace profile.
The complete set of restrictions supported by Profile Owner can be viewed here.
Personally-owned devices are enrolled using Self enrollment or Enrollment through Invitation, which ensures that an employee's device cannot be brought into management without user intervention.
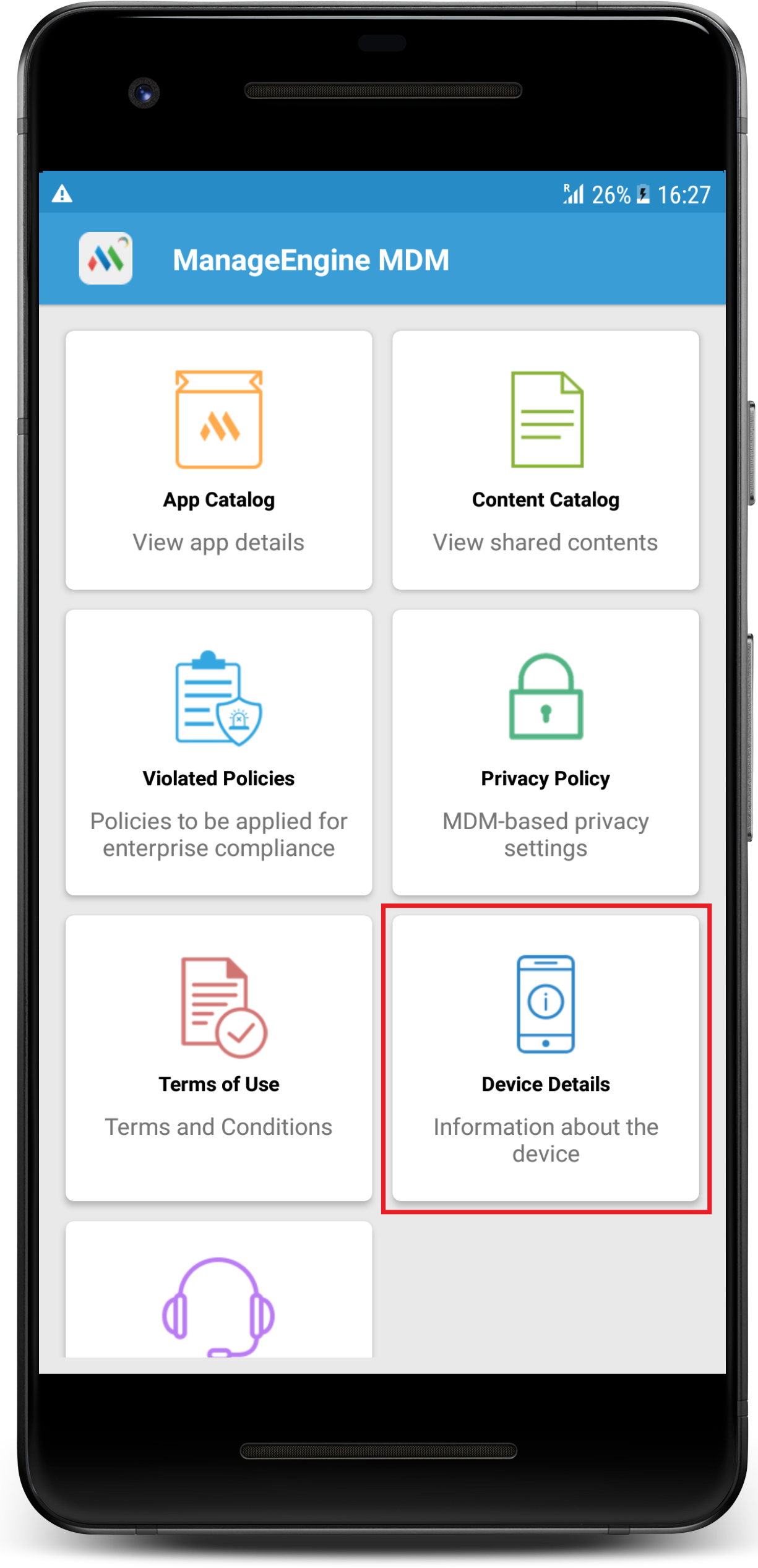
You can identify the device provisioning type by navigating to ME MDM App -> Device Details.
Note: In Windows devices, regardless of the enrollment method used, the provisioning type remains the same. However, the data that can be collected by MDM can be customized using Device Privacy settings.
Note: Irrespective of the provisioning type, MDM cannot collect or monitor users' call logs, browser history, app data, photos, files or passwords. Data that MDM can collect include device details such as device model, Operating System and version, storage space, Device name, serial number, IMEI number, phone number, app inventory.
Privacy Management Features offered in MDM
User transparency
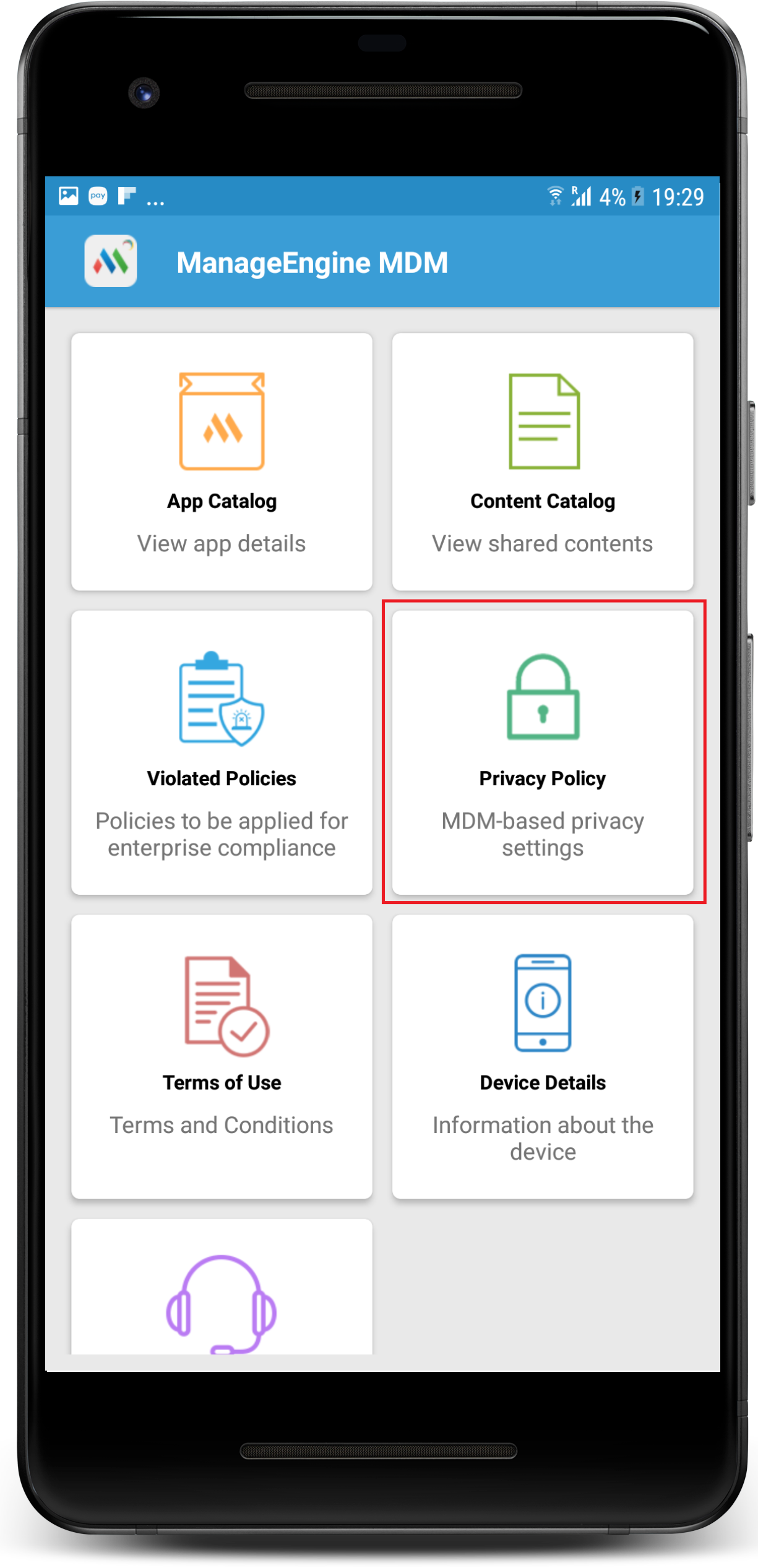
To ensure that employees are fully aware of the implications of the management software or profile installed on their device, MDM requires employees' consent to be obtained through Terms of Use policy during enrollment. This helps employees to understand what data will be monitored and/or accessed and how they will be processed. Users can view Terms of Use policy by navigating to ME MDM App -> Privacy Policy.
Identity preservation
In order to preserve the employee's privacy, MDM offers Device Privacy settings with which an IT Admin can opt to collect and display only requisite device details and choose do not collect for sensitive personal data such as location. Thus when do not collect location is chosen, the devices will be excluded from tracking. Using Device Privacy settings, IT Admins can also disable remote commands such as wipe or remote troubleshoot, etc. The privacy policy created by the admins can also be viewed on the employees' devices by navigating to ME MDM App-> Privacy Policy tab. Admins can also prevent personally-owned devices from being tracked, using Geo-tracking settings, by choosing to track the personally-owned devices' location only when they are lost or they can even exclude personally-owned devices from being tracked and track only Company Owned devices.
Securing data
To protect identity data, when Personally Identifiable Information (PII) collected from the devices is exported from the server, PII can be masked or hidden to avoid potential misuse of the data by any unauthorised person. In addition, once an employee leaves the organization, all the data collected from the employee's device that are stored in the server will be deleted, except the user name. For additional security, MDM provides various authorization mode for technicians trying to access MDM server and all the activities performed on the MDM console are logged, in order to avoid any unauthorised action.
Remote commands
For executing remote commands such as remote control/view, MDM requires the user to accept the session invitation. Hence, without user intervention, an IT Admin cannot initiate a remote control/view session. Similarly, remote wipe can be executed only on the corporate space in a device. Thus when a device is lost or when an employee leaves organization, IT admins can remotely wipe only the corporate data present on the devices leaving the personal data untouched.
While MDM provides various controls regarding the permissions/data collected from end users' devices and how it is utilized, only the IT Admin can determine how MDM is deployed in your environment, based on the organization's security policy. MDM does not assume any responsibility for any of the policy implementation. Contact your IT Admin to know about your organization's security policies.
Managing Corporate devices
In case of corporate devices, the devices are provisioned as Device Owner in case of Android devices and Supervised in case of Apple devices. This ensures the organization has full control over the device and provides additional features to ensure that the device and the confidential data in the device are secure and are protected from any unauthorized access.
Features supported by Device Owner
- Additional restrictions such as restricting factory reset, modifying Settings, restricting camera
- Configuring Conditional Exchange Access
- App lock(Kiosk Mode)
- Silent App installation
- Blocklisting/allowlisting apps/URLs
The complete set of restrictions supported by Device Owner can be viewed here. To know the complete list of restrictions supported for supervised devices, click here.
Android devices can be provisioned as Device Owner using the methods given below
In Apple devices, Supervision can be done using
Challenges with BYOD and privacy
BYOD (Bring Your Own Device) policies raise several privacy concerns that necessitate careful BYOD privacy management. While BYOD can boost productivity and flexibility, it also introduces potential risks to data privacy. Organizations must address BYOD privacy concerns to strike a balance between employee convenience and safeguarding sensitive information.
- Creating well-defined BYOD policies is essential to address privacy concerns effectively.
- Employers should enforce encryption measures on personal devices to protect sensitive information in case of theft or unauthorized access.
- Employers should enforce strict access controls, ensuring that only authorized individuals can view, edit, or share sensitive information.
BYOD privacy concerns
Let's explore some of these BYOD privacy concerns:
- Personal devices may lack the robust security measures present in company-owned devices, making them vulnerable to data breaches, unauthorized access, and malware attacks.
- BYOD privacy management is crucial to strike a balance between organizational data protection and respecting employees' privacy rights.
- Employers may need access to work-related data on employees' devices, potentially compromising their personal information.
- Employees may access work-related data on public Wi-Fi networks or unsecured connections. This increases the chances of data interception and unauthorized access.
What are the key features of a BYOD Policy to protect data privacy?
Here are the key features of a BYOD policy to protect data privacy,
- Employees can keep work-related data separate from personal data on their devices through containerization.
- You can mandate the use of strong authentication methods, such as complex passwords or biometric authentication, to access work-related applications and data on personal devices.
- The BYOD policy does data encryption on personal devices to safeguard sensitive information from unauthorized access or data breaches.
- With BYOD policy, you can remotely wipe work-related data from a personal device in case it is lost, stolen, or if the employee leaves the organization.