- PAM360 8000 to 8500
- PAM360 7000 to 8000
- PAM360 6000 to 7000
- PAM360 5000 to 6000
- PAM360 4000 to 5000
ManageEngine® PAM360 Upgrade Pack Download
The latest PAM360 version is . If you are using an earlier version, you need to apply upgrade pack (Upgrade Instructions).
How Do I Find My Build Number?
Log in to PAM360. Click the 'user profile' icon at the top right corner of the web console and click 'About'. In the new window that opens up, you will find the build number of your currently installed PAM360 setup below the version number.
Download Upgrade Pack| Minor release ( )
Note: We strongly recommend you take a backup before migrating your data to prevent any accidental data loss.
From 8400 to 8500
e0edffe18df79586fa126c5e90b1f7fcad0383f6587736b800999f658bcaec3a
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 8300 to 8400
37737e2d37f87ba311090894b2c91a8abbd9468af679bb413f6d6a6234e6d7b3
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 8200 to 8300
451e411730b9103134d9787ef463cd4bba287e6702a356e0e51a848ece0d9fdd
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 8100 to 8200
52b308c9161c143c03d99dad68de8002d42bde59f69d849eab3e90e93072212a
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 8000 to 8100
a0d4e951dd604ac199ee5d56c6fb08a6f6610c2fb63d3a6a660b4116db7ee54e
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 7500 to 8000
cebed8bc5cb1ea28828ee4d0d050d2db84cd10c8d0b9b9751b62a67a27435315
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 7400 to 7500
d10f7c919191cb60b55cc91a8afffdc1a07f8432472381f4cdb7ef13083383e3
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 7300 to 7400
2e8d320f35a5306343b62d80e11d84dce34399988027cdd9c450a61daeb7518d
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 7200 to 7300
f6c53eff562a2e2391a6691ac73ffe45bf291fd134f3e757fd8ce544dfd0bd8e
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 7100 to 7200
a5869020212d4043457be2980f940d86a82b24f582c328125d3ce330d8f3cdbc
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 7000 to 7100
da3e3157ed1744c804f30525ad102d7f3dc2cec53d15dbc88729f8070773f13d
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 6700 to 7000
70a4229f97b66e7d8277ea44e5209cf94336ce6620981c681834c4e9ede8f2f5
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 6600 to 6700
b866e33ea5186795a9c2f2a357bec21f182420f55d1503614748dc112bd7f384
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
Note: Users who have downloaded the PAM360 build 6600 are strongly advised to use the latest 6601 build and SHA256 checksum hash value to ensure security measures and mitigate the risk of unauthorized access.
From 6500 to 6600
70df1c0d6788a8edaa3a34726df312272517668e977ec29fcbec72bf90213c0a
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
Note: Users who have downloaded the PAM360 build 6600 are strongly advised to use the latest 6601 build and SHA256 checksum hash value to ensure security measures and mitigate the risk of unauthorized access.
From 6400 to 6500
1865e8cae8c68436892f8c0468ac8de7ab2261d6f989e362f8937c7739c60f09
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 6300 to 6400
7284fb97e6937b5bf9b47c25f8bb584f5f38c81a25b4c39674bf46d8a124b46c
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
Note: For customers utilizing LDAP authentication in their environment and MS SQL as the backend database, please ensure to reconfigure the High Availability post the primary server upgrade. However, for customers not using LDAP, the upgrade pack will work seamlessly on both primary and secondary servers without requiring High Availability reconfiguration post upgrade.
From 6200 to 6300
cc75762842ed5b537fecb5900c9b89b6a1ad733722a35d40643b74424b624d6a
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 6100 to 6200
a8cfb604db1bcc7eeaff8f5c37262e211a200bfb140fc3192f239109a6b24df8
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 6000 to 6100
91f54ac0e156454b4eeecdadf32dc236e0e1d5860a8b7d275a61b2c5b5d1eb1c
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 5950 to 6000
bde248be2ef65f9c168236ede8cbcd21073acd85ab26f6a7d7f86393513d4cfa
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 5900 to 5950
345250bdbb8a9f9331753bfc123c016ded152df87de43f7cb65e65a23e105314
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 5800 to 5900
46e810bf0fa08caae676369a9c7144a282d4c23e0244fbd739c4bc4de4a27e64
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 5700 to 5800
0b707f9e79fe518177b60b5ad33635503b356e7128bd9b447f48f6b58a3b4741
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
| Read-Only Server (RO) | NA | |
From 5600 to 5700
e3a067d5917d5311898229b2d0b8cca1c1cff103fc2f45ac747f5dec505d030e
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
From 5500 to 5600
d0ab8e2cd7f11e32c1490ed9ae7880f09cbff9dc975d0b986e653342d174ad88
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
Note: If you are using Dropbox for cloud storage, this upgrade will delete auth tokens, and you will have to reconfigure PAM360 storage in Dropbox.
From 5400 to 5500
553b8669f97ab08e0b2fc4e680dace53de1d852a073cc9d5ce05fbe71004dc33
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | ||
| High Availability (HA) | ||
Note: If you are using Dropbox for cloud storage, this upgrade will delete auth tokens, and you will have to reconfigure PAM360 storage in Dropbox.
From 5300 to 5400
5c51b886e682839835eb87dd5a321d8820e0031e12b8ecaa02898c141adba761
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
From 5200 to 5300
7b93bd6d6b099f13ed6d810ec0defaaa878ee64f87a6c031d4b8f6a9d29d4ba5
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
From 5100 to 5200
23f9b8cb56416048ca97b30aa0ae19691e7a3dd00c0af320cad4d55e66c1189e
The .ppm file can be applied to the secondary PAM360 server without reconfiguring high availability - as per the below-tabulated scenarios only:
| HA Architecture Type | Support to apply the .ppm file on the secondary PAM360 server without reconfiguring high availability | |
|---|---|---|
| PGSQL | MS SQL | |
| Failover Service (FOS) | NA | |
| Application Scaling | NA | |
| High Availability (HA) | ||
Note: If your current Ticketing System is ServiceDesk Plus On-Premises or ServiceDesk Plus Cloud, this upgrade pack will disable the integration and delete the complete integration data. You will have to reconfigure the ticketing system again. So, make sure you have a backup of the advanced configurations in the form of screenshots for reference purposes.
From 5000 / 5001 / 5002 / 5003 / 5004 to 5100
f58db4b9e46129ddeaa429dc089d73abfa7d30ac2a69dabd896a53d0a7278173
From 4500 / 4501 to 5000
1eb9c094abd2f5b3ff24c1741b537918
From 4100 / 4101 to 4500
211a0ddde1f5ee34c78e49b8dc711b68
From 4000 / 4001 / 4002 to 4100
355aa1364063ebe5e85ad24f35dbce83
Note: Kindly upgrade to the latest version to setup HA.
Upgrade Pack Instructions based on Operating Systems
If you have PAM360 configured in the secondary server(s) of your environment, refer to this section before proceeding with the upgrade pack steps given below.
1. Windows
Prerequisites
- Stop the PAM360 service and exit the tray icon.
Note: If you store the 'database_params.conf' file in a different location, copy the file back to the original location, i.e., '<PAM360 Installation Folder>/conf/', before performing the upgrade. - Shutdown the PAM360 service - both primary and secondary, if running (Not applicable for Read-Only servers).
Notes:
• If you are using PostgreSQL as the database, ensure that the Postgres process is not running in the task manager.
• If you are using MSSQL as the database, ensure that the OpenJDK/Zulu platform process is not running in the task manager. - Perform a backup of the entire PAM360 installation folder, and store it someplace safe. You can revert to this copy in case of an upgrade failure with your settings intact. Additionally, take a backup of the PAM360 database.
Note: If you are using MS SQL as the database, perform a database backup using the SQL studio.
Steps Required
- To start with, right-click the Command Prompt and select 'run as administrator'.
- Navigate to the '<PAM360_Installation_Folder>/bin' directory and execute 'UpdateManager.bat'.
- During MS SQL server configuration for the PAM360 database, if you have opted for 'Windows Authentication,' start the command prompt using the service account with which the PAM360 service has been configured to connect to the SQL server (i.e., instead of running as administrator, run as the service account).
- To identify whether a service account is used or an SQL account is used, navigate to <PAM360_Installation_Folder>/conf directory and open the database_params.conf file. If you do not find a username and password in the file, then PAM360 is using Windows Authentication, and therefore you need to run the command prompt with service account privilege.
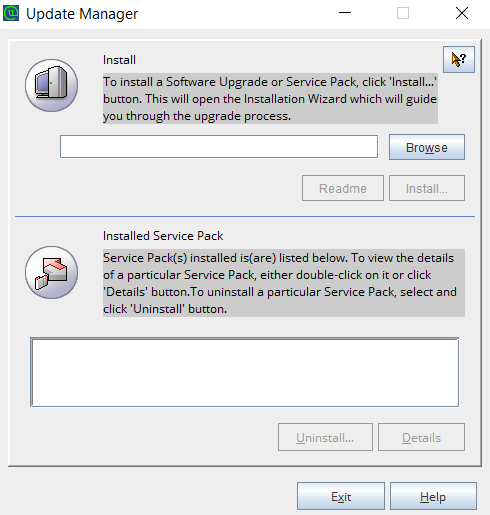
- Click Browse and select the .ppm file that you downloaded from the ManageEngine PAM360 Upgrade Pack section
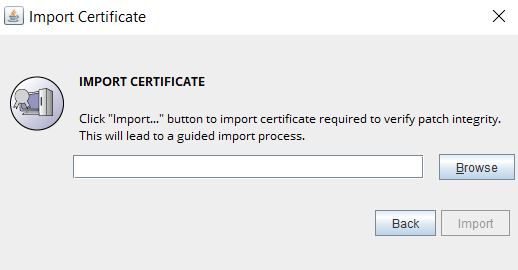
- As a part of patch integrity verification from PAM360 build 5400 onwards, PAM360 requires an SSL certificate to complete the upgrade process. PAM360 will automatically import this certificate during the upgrade. In case, if the automatic import does not happen, you will be prompted to manually add the SSL certificate. Click here to download the SSL certificate to be imported during the version upgrade.
- In this case, when the Import Certificate pop-up opens, click Browse and Import the SSL certificate you downloaded from the above step.
- Click Install in the Update Manager window to begin the upgrade process. Please note that importing the SSL certificate is mandatory while upgrading PAM360 from version 5.3 to 5.4. However, this is a one-time operation and you need not repeat the process during the next version upgrade.
- To apply multiple upgrade packs, do the following for each upgrade; exit the Update Manager, start & stop the PAM360 service once, and execute the above steps 1, 2, and 3.
- Once you have finished applying the upgrade packs, start the PAM360 service.
2. Linux
Prerequisites
- Stop the PAM360 service using the command /etc/init.d/pam360-service stop.
Note: In case you store the 'database_params.conf' file at a different location, copy the file back to the original location (i.e., <PAM360 Installation Folder>/conf/ ) before performing the upgrade. - Shutdown the PAM360 service - both primary and secondary, if running (Not applicable for Read-Only servers).
Note: If you are using PostgreSQL as the database, ensure that the Postgres process is not running in the task manager. - Perform a backup of the entire PAM360 installation folder and store it in some other location. In case something goes wrong with the upgrade, you can revert to this copy with your settings intact. Additionally, take a backup of the PAM360 database.
Note: If you are using MS SQL as the database, perform a database backup using the SQL studio.
Steps Required
- Navigate to <PAM360_Installation_Folder>/bin directory using the terminal.
- Execute the command sh UpdateManager.sh -c(This will run the Update Manager in CLI mode)
- Now, press i to install and supply the full path of the upgrade package that you have downloaded from ManageEngine PAM360 Upgrade Pack section.
- As a part of patch integrity verification from PAM360 build 5400 onwards, PAM360 requires an SSL certificate to complete the upgrade process. PAM360 will automatically import this certificate during the upgrade. In case, if the automatic import does not happen, you will be prompted to manually add the SSL certificate. Click here to download the SSL certificate to be imported during the version upgrade.
- Enter the SSL certificate's absolute path when prompted. Once the certificate is imported successfully, wait for the upgrade to complete until the message "Service Pack applied successfully" is displayed.
Please note that the SSL certificate import is a one-time operation, and you need not repeat the process during the next version upgrade. - To apply multiple upgrade packs, do the following for each upgrade; exit the Update Manager, start & stop the PAM360 service once, and execute the above steps 1, 2, and 3.
- After applying the upgrade packs, start the PAM360 service using /etc/init.d/pam360-service start
Applying the PAM360 Upgrade Packs Based on Secondary Server Configurations
1. Read-Only Server - PostgreSQL
- Ensure that the Read-Only servers are up and running.
- Apply the PPM file in the master server using the above instructions based on your operating system.
- Post applying the PPM in the master server, log in to the Read-Only server(s) and verify for the updated build version in the About to ensure a proper database update.
Note: The above steps only update the Read-Only server database and do not have any changes in the PAM360 application setup. To upgrade the PAM360 application in the Read-Only server to the recent version, apply the PPM in all available Read-Only servers. - Now, stop all the Read-Only server(s) and start the master server.
- Apply the PPM file one by one in all the available Read-Only server(s) using the above instructions based on your operating system and start all the Read-Only server(s).
- Now, you have successfully upgraded to the latest version of PAM360 configured with the Read-Only server(s) setup.
2. Application Scaling
If you have Application Scaling configured in your environment, upgrade your main node first followed by the subnodes. For the subnodes (secondary server), check if the existing .ppm file can be applied to your newer version from the ManageEngine PAM360 Upgrade Pack section. If the .ppm file is applicable, please follow the steps given below and proceed. Else, you will have to reconfigure the subnodes.
- Stop the main node and the configured secondary nodes of PAM360.
- Apply the PPM file in the main node and then to the subnodes one by one using the above instructions based on your operating system.
- Now, start the PAM360 main node and the available subnodes.
3. Failover Service - MSSQL
For the secondary instance configured as a failover service, check if the existing .ppm file can be applied to your newer version from the ManageEngine PAM360 Upgrade Pack section. If the secondary .ppm file is applicable, please follow the instruction and proceed. Else, you will have to reconfigure a fresh failover service in the secondary instance by following the deactivation steps given below the upgrade steps.
- Stop the slave server as it needs to be in a slave state and the primary server.
- Apply the PPM file to the primary server and then to the secondary using the above instructions based on your operating system.
- Now, start the PAM360 master and slave servers.
Deactivating the Failover Service
You can deactivate the failover service either from the primary or the secondary server by following the below steps:
- Open a command prompt in any of the servers.
- Navigate to <PAM360_SERVER_HOME>\bin directory.
- Execute the command: UninstallFOS.bat.
- Now, uninstall the PAM360 application entirely from the other servers.To reconfigure a failover service and set up a fresh secondary instance of PAM360, follow the steps given in the help guide: FOS.
4. High Availability - MSSQL
For the secondary instance, check if the existing .ppm file can be applied to your newer version from the ManageEngine PAM360 Upgrade Pack section. If the secondary .ppm file is applicable, please follow the instruction and proceed. Else, you will have to reconfigure or reinstall High Availability in the secondary instance by following the prerequisites given below the upgrade instructions.
- Apply the PPM file in the primary server and the secondary server using the above instructions based on your operating system.
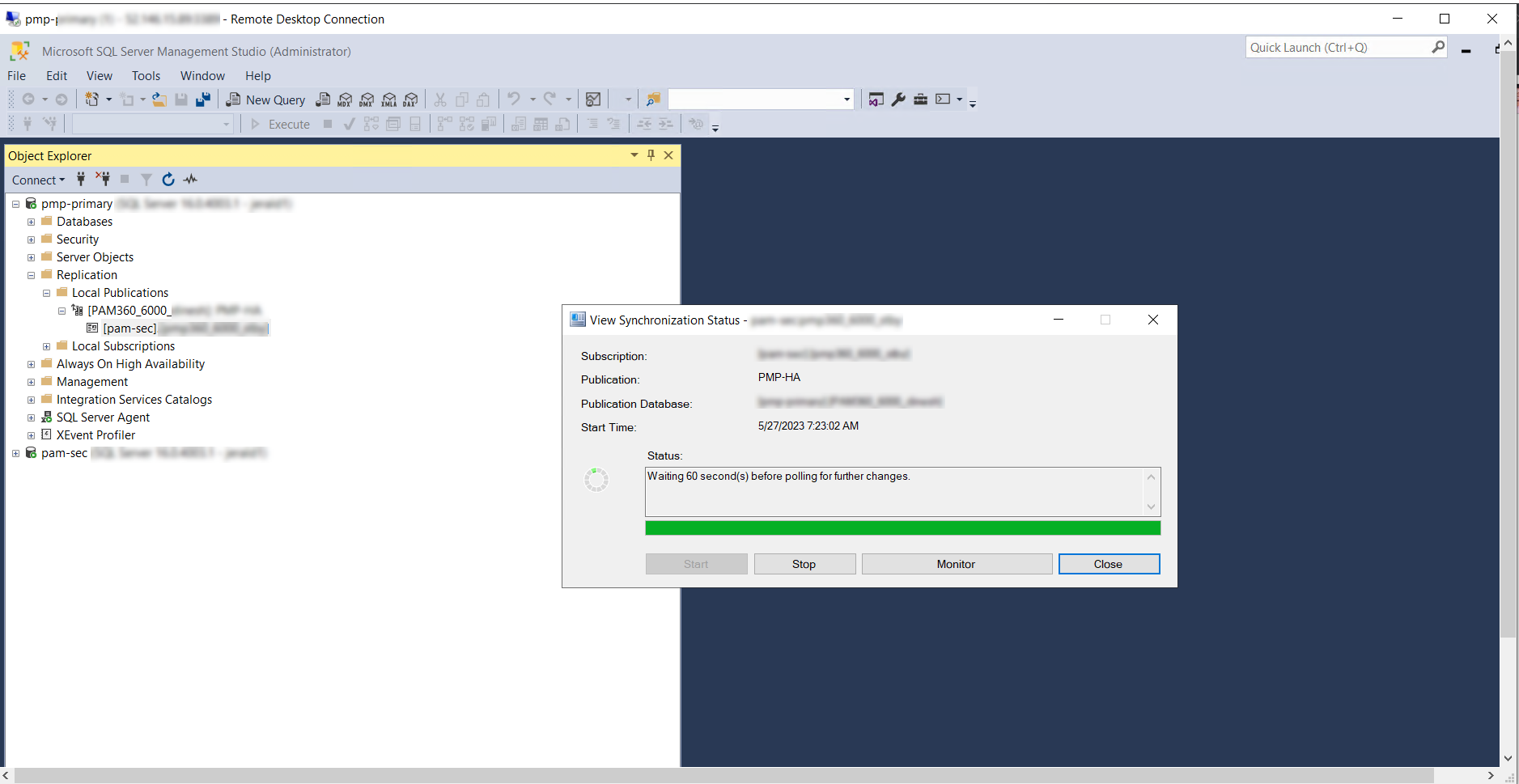
- Now, check the replication status in the primary server in (local publication >> view synchronization status), and it should be shown as below.
- Now, start the PAM360 secondary and the primary servers.
Prerequisites for Reconfiguring High Availability
To reconfigure a new High Availability instance, delete the replication data related to 'Subscriptions' and ''Publications', and disable 'Publishing and Distribution'. To do so, log in to MS SQL Server Management Studio and delete the following files/folders as explained below: (Skip these steps if High Availability is not configured).
- Deleting Subscription
Navigate to Replication >> Local Publications >> <Name of PAM360 database:PAM360-HA >. You will see a file with <PAM360 server name>:<Name of PAM360 database>. Right-click the file and press 'Delete' in the menu. - Deleting Publication
Navigate to Replication >> Local Publications >> <Name of PAM360 database:PAM360-HA>. Right-click the folder <Name of PAM360 database: PAM360-HA> and press 'Delete' in the menu. - Disabling Publishing Distribution
Now, right-click the 'Replication' folder and click the option 'Disable Publishing and Distribution'. Further, proceed with the configuration steps given in the help guide to reconfigure the High Availability.
5. High Availability - PostgreSQL
For the secondary instance, check if the existing .ppm file can be applied to your newer version from the ManageEngine PAM360 Upgrade Pack section. If the secondary .ppm file is applicable, apply the PPM file in the primary server and the secondary server using the above instructions based on your operating system. Else, you will have to reconfigure or reinstall High Availability in the secondary instance.
To reconfigure High Availability and set up a fresh secondary instance of PAM360, follow the steps given in the help guide: PgSQL.
For more assistance, please get in touch with our Support team pam360-support@manageengine.com.
 Upgrade Pack
Upgrade Pack
