Event Viewer
Written by Sakthi Sri, IT security team, ManageEngine Updated on August 2025
What is Event Viewer?
Event Viewer is a tool in the Microsoft Windows operating system that provides a comprehensive log of system events to offer administrators the information required for system upkeep, security, and accountability.
To understand Event Viewer better, consider the analogy of a building's surveillance network: If Windows OS is a security camera and event logs are the recordings, Event Viewer is the CCTV monitoring system. A good surveillance monitoring system will have visibility features like zoom-in or HD. Similarly, Event Viewer offers features to help you discern a critical event from a regular, discountable event.
With features such as the ability to filter and group events, a powerful search engine, and enhanced reporting capacity, Event Viewer is your window into the world of Windows event logs.
How to open Event Viewer
- In the Windows search bar, enter Event Viewer, then click the app to open it.
- Or, press the Windows key + R and type Eventvwr.
Windows event logs
A flurry of activities happen on a computer every day. The Windows OS records every event pertaining to system performance, applications, and security aspects of a computer in a log at C:\WINDOWS\system32\winevt.
The Event Viewer reads from these raw event logs, then presents the information in a readable format.
What is the purpose of event logs?
The information stored in these logs is exhaustive; every detail about the computer’s hardware, software, users, and their interactions are logged. For example, one can find general information about when a process started, data about an application crash, or details about when a user authenticated or failed authentication. All this information enables administrators to spot and remediate potential threats or issues before they snowball into bigger catastrophes. Further, the security-related event data helps administrators improve their security posture and establish accountability.
The format of event log data and how it is presented in the Event Viewer
Windows classifies every event that occurs on a computer into the following categories:
- System log: In this log, events related to the computer system including hardware are registered. For example, events like system startup and shutdown are logged here.
- Application: All events related to the apps hosted on a machine are logged in this space. For example, information pertaining to apps like MS Word is recorded in this log.
- Setup: Events that occur during installation or upgrade of OS. For example, information about Windows OS updates can be found here.
- Security: The Windows auditing feature continuously monitors for security events and registers their occurrence in this log. For example, user authentication events including successful and failed login attempts.
- Forwarded events: This is a special category introduced in 2008 which stores events forwarded from other computers.
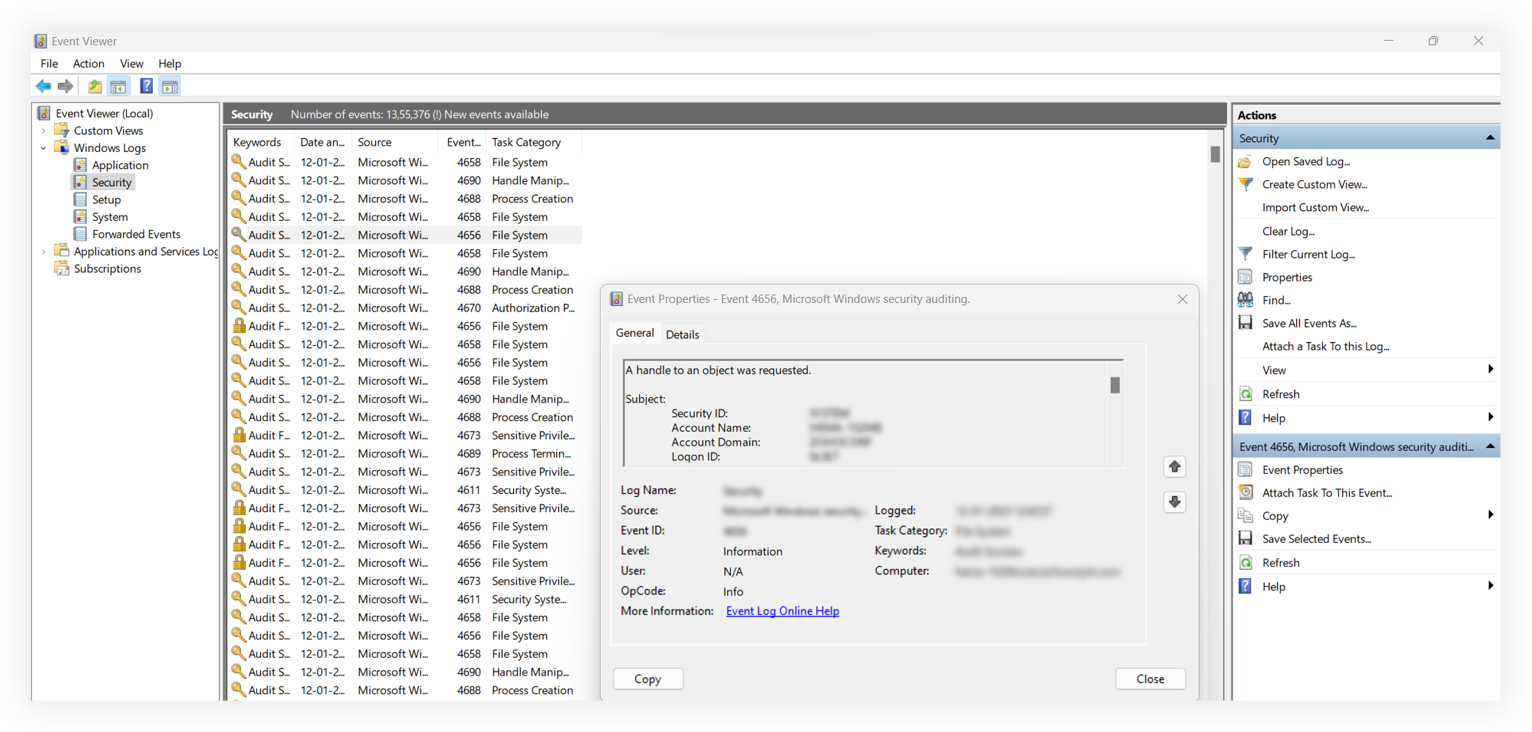
The following information is recorded for every event and detailed in the Event Viewer console:
- Event ID: A unique identification number that helps administrators identify an event (e.g., Event ID 6008 for unexpected system shutdown). Here are eight of the most critical Windows event IDs.
- Event date and time: The information on exactly when an event happened.
- Source: The details of the software, service, or process which caused the event.
- Log name: The type of log where this event has been registered (i.e., system, application, security, setup, or forwarded events).
- User: The information about the user who was logged in to the computer when the event occurred.
- Computer: The information about the computer where the event occurred.
Further, the severity level of the event is also specified. Windows assigns one of the following severity levels to each event to prompt administrators to act accordingly:
- Information: As the name suggests, this is plain good-to-know information.
- Warning: This is a clue that there is a potential problem.
- Error: This indicates a problem, but it might not need immediate remediation.
- Critical: This is a red flag. Attention and action is imperative for this event.
This is what the data in Event Viewer looks like:
Additional features of Event Viewer
- Event Viewer offers exclusive search filters to help find specific details in the log.
- The option to create custom views allows you to see only the details of interest.
- Event Subscription allows you to configure a collection of events from remote computers.
- Applications and Services Logs lets third-party apps register their events.
- The log archival mechanism allows administrators to file important logs, which is a critical step in IT regulations compliance.
Limitations of Event Viewer
Despite all its features, Event Viewer is no silver bullet for the challenges faced by an administrator. Its limitations can be felt even when working with just one machine, let alone a network of computers. It is crippled by various limitations, including:
- Event logs do not get replicated between computers on a network, making aggregating logs from multiple computers difficult.
- Trying to understand the Event Viewer reports involves sifting through a colossal amount of data.
- A lack of correlation and context. Often, an event seems insignificant on its own, but when seemingly unrelated yet connected events are correlated, the big picture emerges. This is not possible using Event Viewer alone.
- No security reporting or compliance audit reporting. This makes it impossible to rely solely on Event Viewer for compliance audits.
The ADAudit Plus advantage: Bridging the gap
ADAudit Plus is a UBA-driven change auditor which aggregates event logs from various computers, stores them centrally, and programmatically correlates related events to build the best context needed to take action. Additionally, it offers real-time alerts and notifications about critical events and changes. All this in just a few clicks!
About ADAudit Plus
ADAudit Plus is a UBA-driven auditor that helps keep your AD, Azure AD, file systems (including Windows, NetApp, EMC, Synology, Hitachi, and Huawei), Windows servers, and workstations secure and compliant. ADAudit Plus transforms raw and noisy event log data into real-time reports and alerts, enabling you to get full visibility into activities happening across your Windows Server ecosystem in just a few clicks.
Try all these features and more for 30 days with a free, fully-functional trial. Alternatively, you can also schedule a personalized demo for a guided walkthrough of ADAudit Plus.
Don't wait for your annual compliance audit.
- Audit your AD and Azure
- Monitor user logon
- Troubleshoot AD lockouts
Thanks!
Please check your inbox for demo details.