Retrieving last logon information of AD users helps administrators identify inactive user accounts, track user login history, and detect anomalous user login patterns. While administrators can use PowerShell to accomplish this, Active Directory's m ethod of storing logon data presents unique challenges as there are multiple attributes, LastLogon, LastLogonDate, and LastLogonTimestamp, each with its own purpose and limitations. This article will explore how to effectively use PowerShell to obtain AD last logon information and easily retrieve it using the AD last logon reports in ADManager Plus, an AD reporting tool.
The following table compares how you can find the last logon value of AD users using PowerShell versus ADManager Plus.
Before you start, ensure:
To get an AD user's last logon information using PowerShell, open Windows PowerShell as an administrator and execute the following script:
Get-ADUser -Filter * -Properties LastLogonTimestamp
To get an AD user's last logon information using the lastLogon attribute, use the following script:
Get-ADUser -Identity "John" -Properties LastLogon | Select-Object Name, lastLogon
To get an AD user's last logon information using the lastLogon attribute, use the following script:
Get-ADUser -Identity "John" -Properties LastLogonDate | Select-Object Name, lastLogonDate
To find an AD user's last logon value using ADManager Plus:
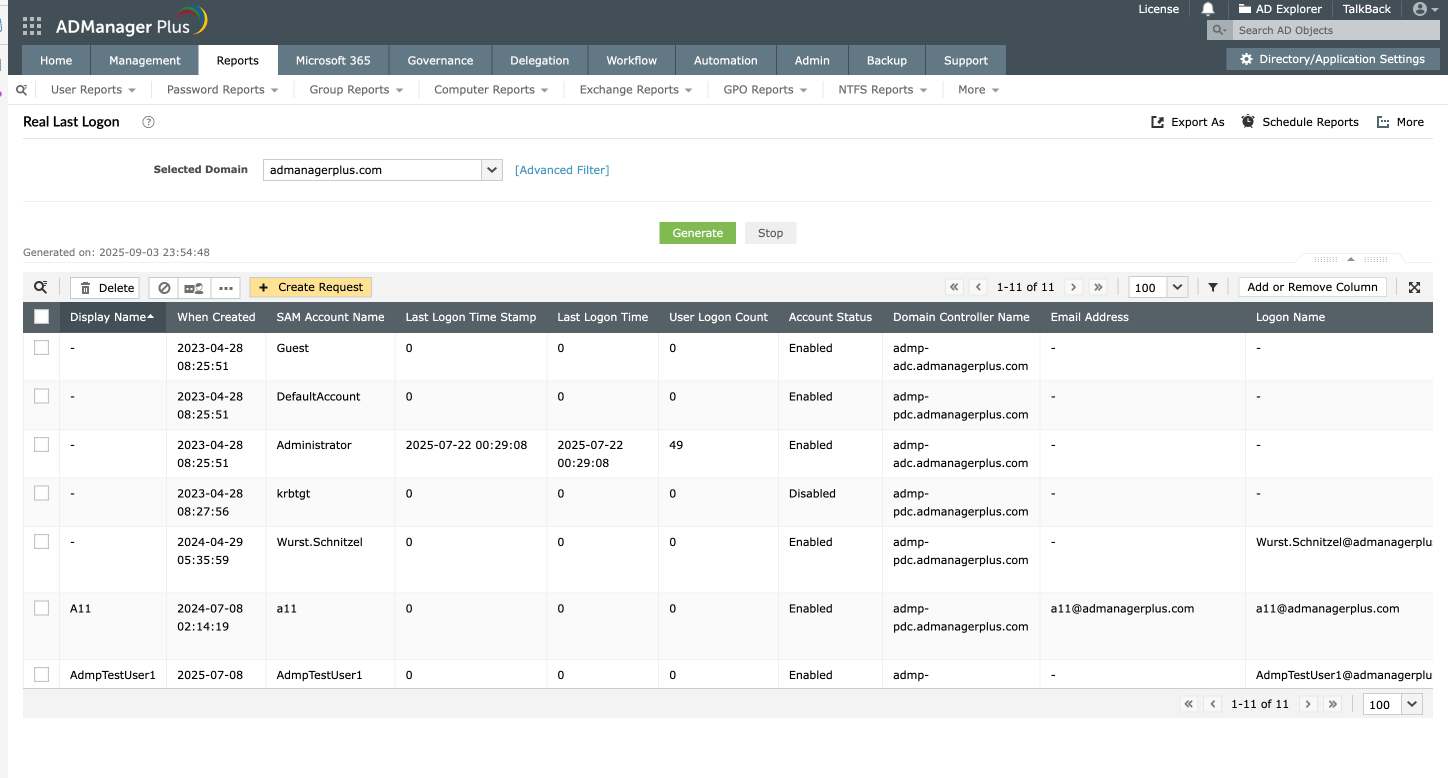
Here are a few variations and practical use cases:
To get the last logon time for a single user, you need to query the LastLogonTimeStamp property in PowerShell and convert it from its raw FileTime format to a readable date.
Get-ADUser -Identity "John" -Properties LastLogonTimeStamp | Select-Object Name, @{Name='LastLogon';Expression={[datetime]::FromFileTime($_.LastLogonTimeStamp)}}
This script finds all users who have not logged on in the last 90 days:
$inactiveDays = 90
$cutoffDate = (Get-Date).AddDays(-$inactiveDays)
# Convert the cutoff date to FileTime format for the AD filter
$cutoffFileTime = $cutoffDate.ToFileTime()
Get-ADUser -Filter "LastLogonTimeStamp -lt '$cutoffFileTime'" -Properties LastLogonTimeStamp, EmailAddress | Select-Object Name, SamAccountName, EmailAddress, @{Name='LastLogon';Expression={[datetime]::FromFileTime($_.LastLogonTimeStamp)}}
Because the LastLogon attribute is not replicated, the only way to get the absolute most recent logon time is to query every DC and find the newest value. This script is more advanced but provides the highest accuracy.
$userName = "jdoe"
$latestLogon = $null
$logonDC = ""
$domainControllers = Get-ADDomainController -Filter *
foreach ($dc in $domainControllers) {
$user = Get-ADUser -Identity $userName -Server $dc.HostName -Properties LastLogon
if ($user.LastLogon -gt 0) {
$currentLogon = [datetime]::FromFileTime($user.LastLogon)
if ($currentLogon -gt $latestLogon) {
$latestLogon = $currentLogon
$logonDC = $dc.HostName
}
}
}
Write-Host "User: $userName"
Write-Host "Most recent logon: $latestLogon on DC: $logonDC"
While PowerShell can be used to obtain the last logon details of users, it comes with several limitations.
ADManager Plus is a comprehensive AD reporting solution that helps admins overcome PowerShell's limitations and seamlessly report on AD users.
You can convert the raw FileTime value using the [datetime]::FromFileTime() method. For example:
@{Name='LastLogon';Expression={[datetime]::FromFileTime($_.LastLogonTimeStamp)}}.
AD does not natively store the last logon computer on the user object. This is a complex task that requires scripting, appropriate permissions on all DCs, and can be slow in large environments. To find this information with PowerShell, you must query the security event logs on all your DCs.
You need at least Read permissions on user objects in AD to get the last logon details of users. For querying multiple DCs, ensure your account can authenticate to each DC.