How to configure AWS in NetFlow Analyzer
- Amazon CloudWatch Logs API, enables you to capture, monitor, or store the IN and OUT traffic data that passes through the network interfaces in your VPC.
- VPC Flow log can be requested through CloudWatchLogs API. Every minute, NetFlow Analyzer uses this API, to request AWS for events created from Cloudwatchlogs.
- These data will then be stored in a file and dumped to the database for every 10mins, (similar to NetFlow packet processing).
How to discover VPC flows using NetFlow Analyzer?
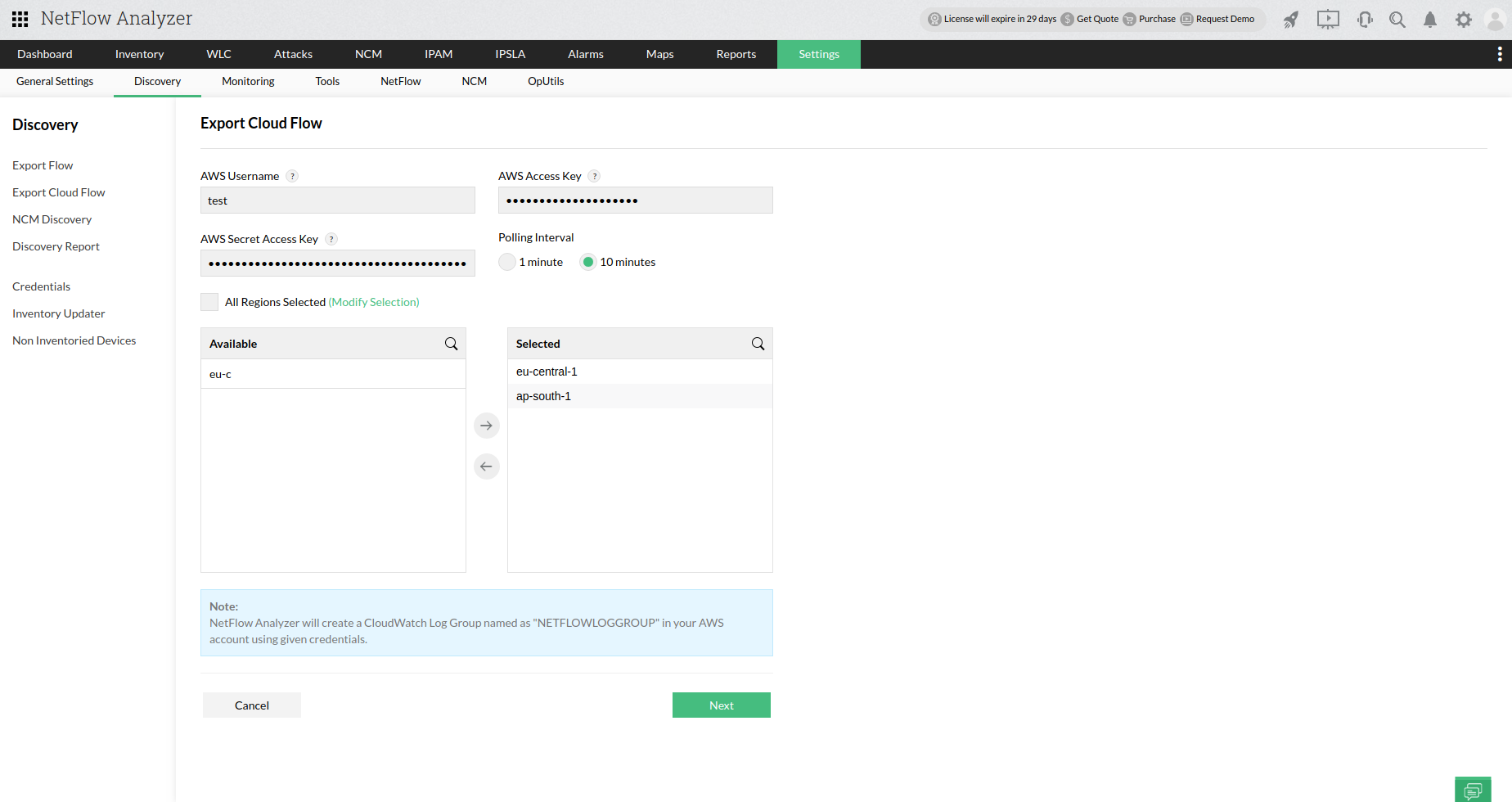
- Navigate to Settings> Discovery> Export Cloud Flow. Flow.
- Click Add - AWS Credentials
| AWS Username |
This field only used for display purpose in NFA |
| AWS Access Key & AWS Secret Key |
- In your AWS account, Navigate to My Security Credentials > Access Keys
- If not available, create a new access key.
|
| Polling Time |
This field will decide, at what interval NFA will have to fetch FlowLogs from AWS |
| Region Selection |
- Regions can be selected to get interfaces from AWS.
- Make sure all regions are enabled for Global endpoint
|
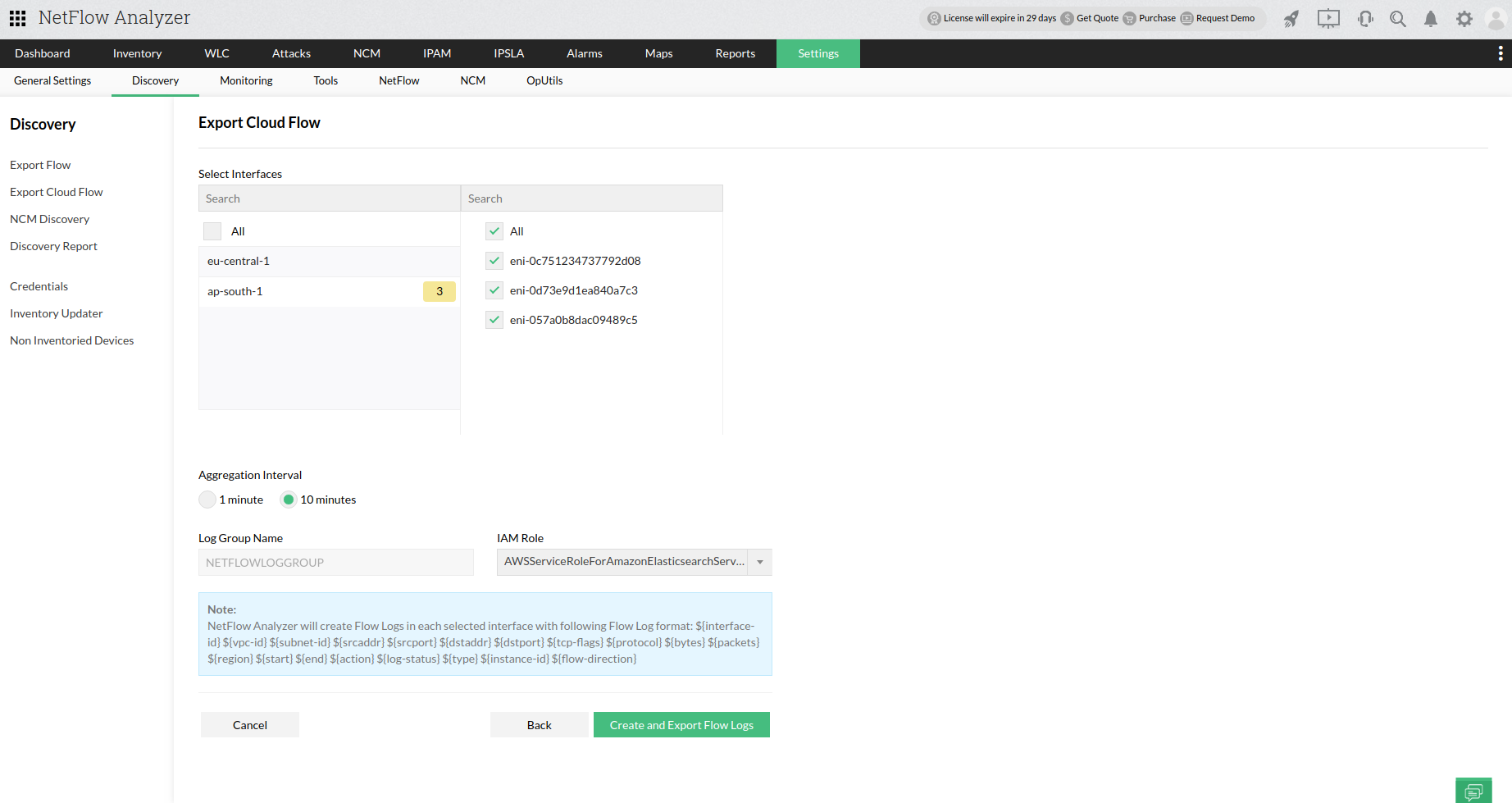
Click Next to fetch the AWS Interfaces list. From the list Select the interfaces you want to monitor it in NFA.
Aggregation Interval - 1 min or 10 min
- Decides whether AWS flowlogs should be aggregated at a 1min or 10min interval.
Log Group Name
- NFA will generate a LOG GROUP Name in CloudWatch with the name "NETFLOWLOGGROUP".
NFA supports only the following Flow Log format and will process only the formatted data.
IAM Roles
- Need to choose respective IAM roles listed from AWS to create flow logs.
- Only based on the selected roles the flows will get exported.
Note:Ensure that you are a root user or provide root user keys.
Follow these steps to create AWS IAM Role Permission.
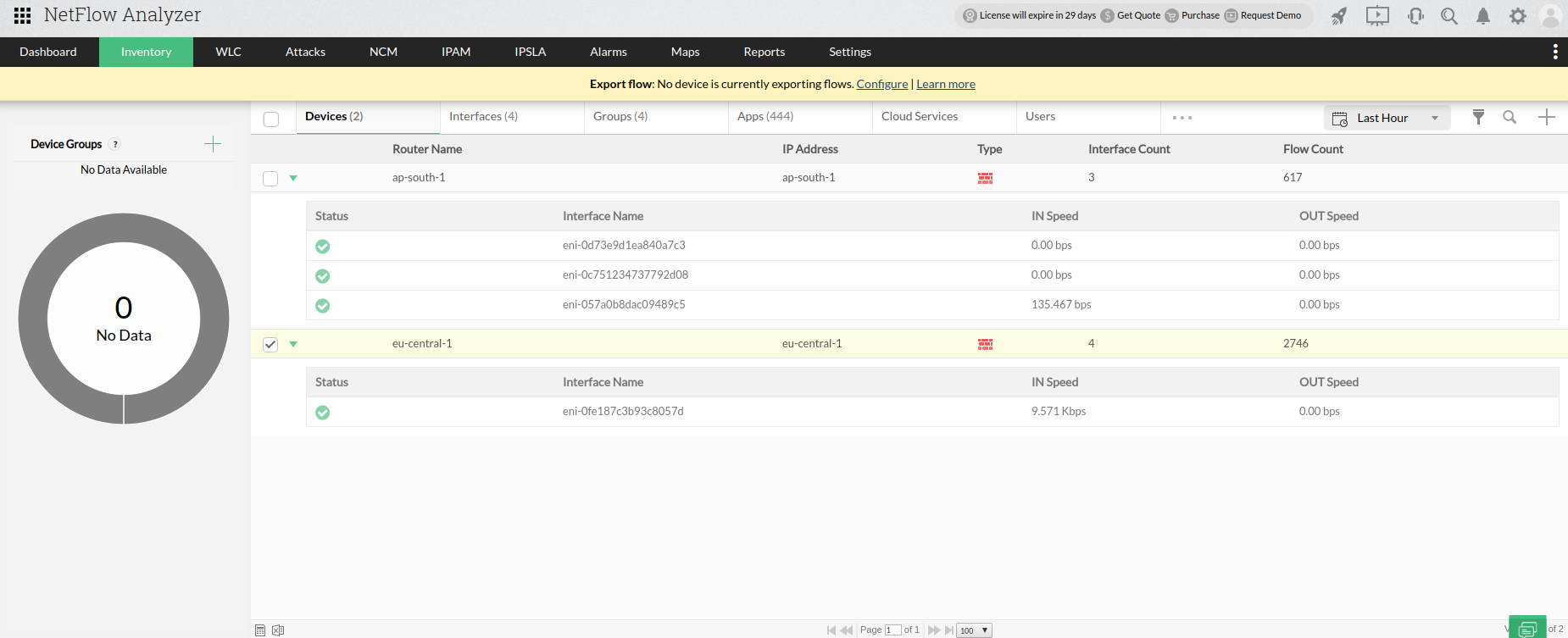
- After importing VPC flows, the devices tab should display the AWS regions along with their interfaces.
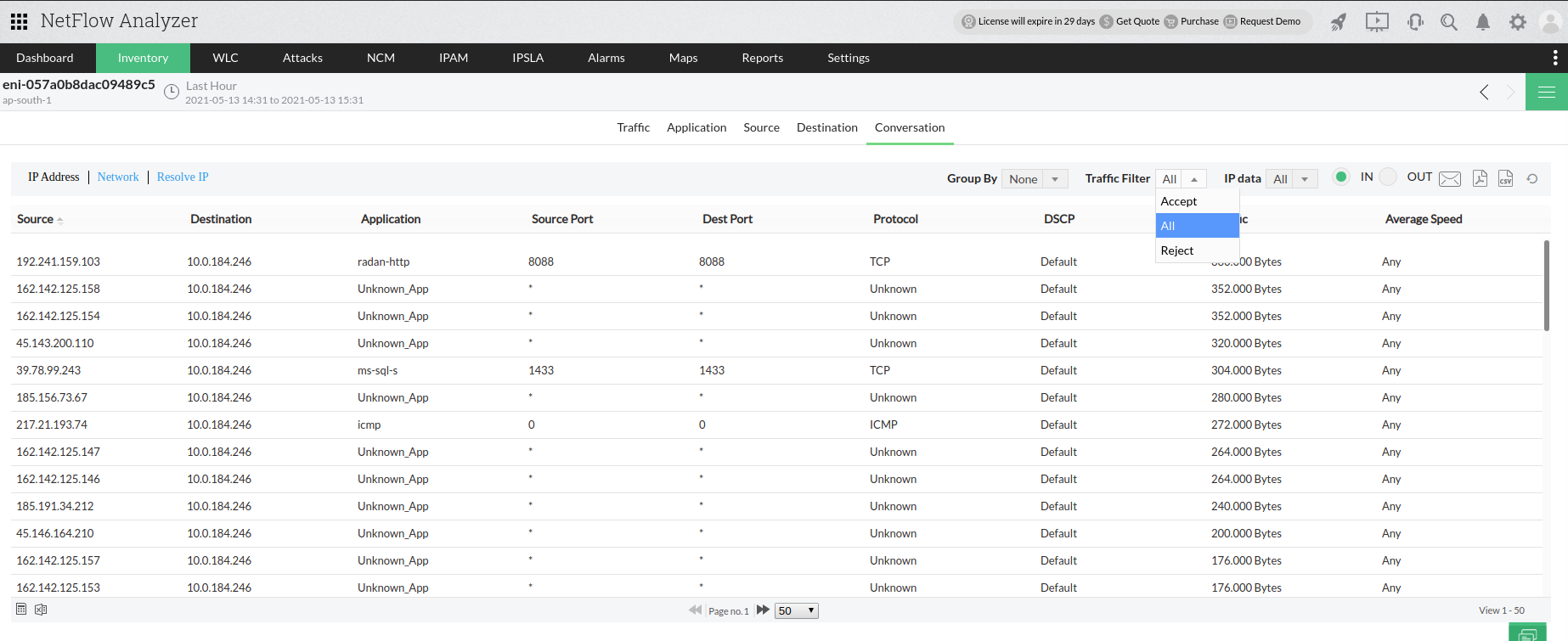
- The interfaces can be drilled down to display the following tabs Traffic, Source, Destination, Application, and Conversation. In addition the Source, Destination and Conversation tabs now display options to ACCEPT and REJECT traffic.
- If a device is used primarily for multiple VPC's, you can use NFA's grouping feature to create a device group which displays a list of VPC traffic in a single page.
Thank you for your feedback!