Certificate-based authentication: Beginner's guide
In today’s threat landscape where cyberattacks evolve faster than many defenses, organizations are being forced to ask a critical question: How do we verify that users or machines are who they claim to be?
The emerging answer is certificate-based authentication, a method that replaces weak, human-managed passwords with cryptographic proof rooted in public key infrastructure (PKI).
Certificate-based authentication isn’t new, but its importance has surged with the rise of Zero Trust security, hybrid work, and the growing need for secure machine-to-machine communication. If you're exploring modern identity or passwordless strategies, understanding what certificate-based authentication is and how it works is essential.
What is certificate-based authentication?
Certificate-based authentication is an identity verification method that uses digital certificates instead of passwords. These certificates are issued and validated by a PKI, enabling users, devices, applications, and services to prove their identities using cryptographic trust rather than memorized credentials.
Each certificate includes:
A public key.
Identity information (e.g., user, device, or service).
A Certificate Authority (CA) digital signature.
Validity period.
Usage constraints (e.g., client authentication, server authentication, code signing).
During authentication, the system verifies that the certificate:
Was issued by a trusted CA.
Has not expired.
Has not been revoked.
Matches the private key held by the requester.
If all checks succeed, authentication completes without a password ever being typed or transmitted.
Why do certificates beat passwords?
Passwords fail for one predictable reason: humans manage them. We forget them, reuse them, overshare them, and store them insecurely.
Here's how certificate-based authentication eliminates these weaknesses:
Resistant to phishing: There’s nothing to type or share, and users can't be tricked into sharing certificates.
Strong cryptographic identity: Identity is verified through asymmetric key pairs, which are highly resilient to attacks.
No password fatigue: No resets, no complexity rules, and no recurring password changes.
Scales across modern environments: Ideal for organizations managing thousands of devices, cloud workloads, containers, and APIs.
Zero Trust ready: Certificate-based authentication supports continuous, identity-centric trust validation.
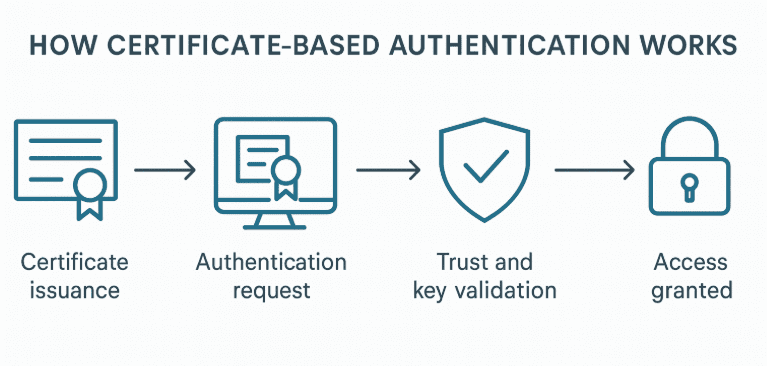
How does certificate-based authentication work?
At its core, certificate-based authentication relies on a cryptographic trust exchange. Here is the typical process:
1. Certificate issuance
A user, device, or service requests a certificate from a CA. The CA validates the identity and signs the certificate.
2. Authentication request
When the user or device attempts to connect to a VPN, Wi-Fi network, application, or through mutual TLS (mTLS), it automatically sends its certificate as part of the secure connection setup, usually during the TLS handshake or the authentication protocol.
3. Trust and key validation
The system checks:
Is the certificate issued by a trusted CA?
Is it still valid?
Has it been revoked?
Does the requester hold the matching private key?
4. Access granted
If the certificate passes the validation checks, authentication succeeds and a secure session is established.
Common use cases for certificate-based authentication
Certificate-based authentication strengthens security and improves the user experience, making it widely adopted across industries.
Enterprise and network access
Organizations use certificates to authenticate users and devices when connecting to Wi-Fi networks, VPNs, and internal applications. This eliminates the need for passwords and ensures only trusted, enrolled devices can access corporate resources.
Endpoint and mobile security
Mobile device management (MDM) and mobile application management platforms automatically deploy certificates to laptops, mobile devices, and IoT endpoints. This enables secure, passwordless authentication and ensures that only managed, compliant devices can communicate with enterprise systems.
Secure API and service communication
In microservice and API environments, mTLS uses certificates on both the client and server sides to verify identity before data is exchanged. This prevents unauthorized services or malicious actors from impersonating trusted components.
Workforce identity
Smart cards, personal identity verification credentials, and hardware tokens embed certificates to authenticate employees in high-security environments. This provides strong, phishing-resistant identity verification for government, finance, healthcare, and other regulated industries.
Cloud and DevOps workload authentication
Modern DevOps and cloud systems use short-lived certificates to allow applications, containers, and automation tools to prove their identity. These certificates are generated automatically and expire quickly, eliminating the need for stored passwords or hardcoded secrets. This approach strengthens security and reduces the attack surface.
Certificate-based authentication best practices
To ensure secure, scalable, and reliable deployments of certificate-based authentication, organizations should follow these key best practices:
Automate issuance and renewal: Leverage protocols like Simple Certificate Enrollment Protocol (SCEP) or Automated Certificate Management Environment (ACME), or integrate with an MDM platform or Intune, to automatically issue, install, and renew certificates. Automation reduces human error, prevents expired certificates, and scales across large device environments.
Use short-lived certificates: Short-lived certificates minimize the time in which a compromised certificate can be exploited. They also reduce reliance on revocation mechanisms, since certificates naturally expire quickly.
Enforce strong private key protection: Store private keys in hardware-backed environments, such as secure enclaves or hardware tokens. This prevents key extraction or tampering, even if the device is compromised.
Implement certificate revocation checking: Revocation ensures that compromised, expired, or invalid certificates cannot be used for authentication. Certificate Revocation List (CRL) and the Online Certificate Status Protocol (OCSP) provide real-time validation to block untrusted certificates.
How ADSelfService Plus enhances certificate-based authentication
ADSelfService Plus enhances certificate-based authentication by integrating PKI trust with Active Directory (AD) and simplifying deployment across large environments. It supports smart card authentication, validates certificates against trusted root CAs, and ensures that each certificate correctly maps to the user’s AD identity through configurable attribute mapping.
ADSelfService Plus also supports passwordless login and allows certificates to be combined with its wide range of multi-factor authentication options for higher assurance. With centralized configuration, trusted CA management, and seamless smart card support, ADSelfService Plus makes deploying and scaling certificate-based authentication significantly easier and more secure for enterprise environments.
Certificate-based authentication is not just a security tool; it represents a long-term shift in how digital trust is established. It transforms identity from something users must remember into something the system can verify cryptographically. It is secure, seamless, scalable, and essential for modern enterprises navigating the complexities of hybrid work and Zero Trust cybersecurity.
If your organization still relies heavily on passwords, now is the time to take the next step. Certificate-based authentication is not just the future of identity—it's already here, reshaping how the digital world works.