Active Directory
The integration of Active Directory (AD) with ServiceDesk Plus MSP enables you to import user information from the Active Directory server into ServiceDesk Plus MSP. It also lets you schedule user import from AD, sync deleted users from AD, and configure AD authentication.
Role Required: SDAdmin
To configure AD related settings, go to Admin > Users & Permission > Active Directory.
Quick Links
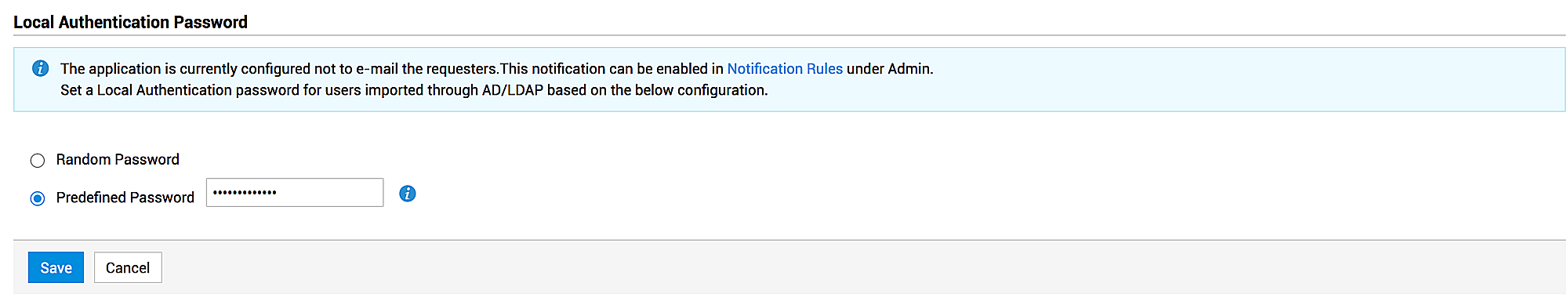
Set local authentication password for imported users
You can set a default local authentication password for users imported through AD. Users can change this password after their first login.
To set a local authentication password from the Active Directory configuration page,
-
Hover over the Local Authentication Password fields and click Edit.
-
You can choose to generate a random password for every user or set a predefined password for all users.
-
Click Save.
Users will be notified about their password via their login emails. You can configure email notifications for users from Admin > Automation > Notification Rules > Send Self-Service Login details.
Import Requesters from Active Directory
You can import users from any of the domains and their subsequent organizational units (OUs) present in the Active Directory. By default, AD users are imported using LDAP protocol and port 389.
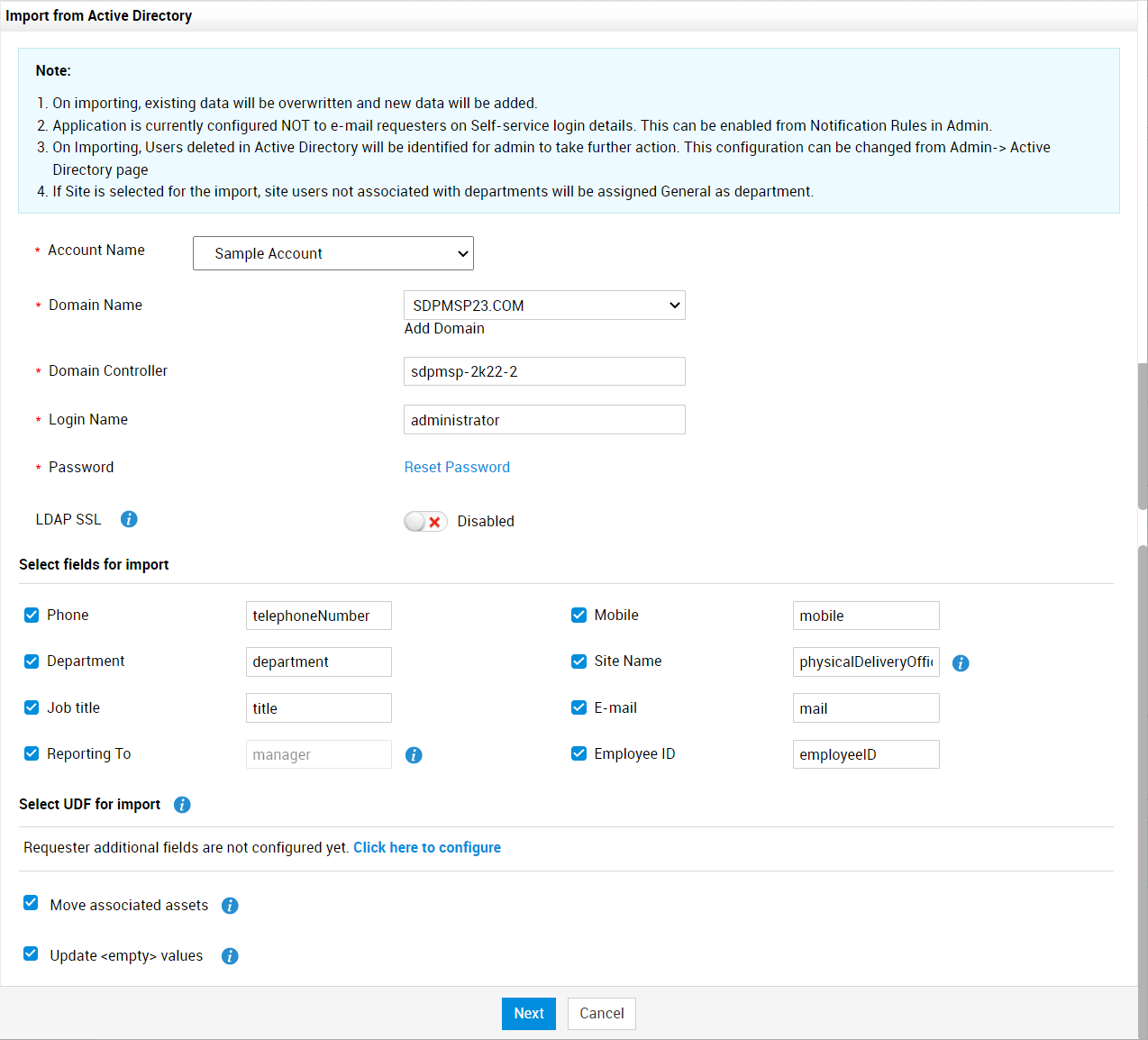
Click Import Requesters from Active Directory link on the Active Directory configuration page. Use the following pointers to configure the Import From Active Directory window pop-up.
|
Field Name |
Description |
|
Domain Name* |
Select the domain to import users from. If you have already provided the domain controller and login credentials for the domain in Windows Domain Scan, the Domain Controller and Login details will be auto-populated on selecting the domain. |
|
Domain Controller* |
Specify the domain controller that provides access to resources in that domain. |
|
Login Name* |
Enter the login name of your user account in the selected domain. |
|
Password* |
Enter the password of the above user account. |
|
LDAP SSL |
Toggle LDAP SSL option ON to enable secure communication between the ServiceDesk Plus MSP and Active Directory via port 636. Ensure your Active Directory supports SSL before enabling this field. Click here to learn about prerequisites for configuring LDAP SSL. |
|
Select fields for import |
Select the default user fields to be imported from the Active Directory. Specify the field name configured in the Active Directory beside the selected field to map them accurately. If the user already exists in ServiceDesk Plus MSP, their default field values will be overwritten with the values present in AD. To avoid over writing of values, unselect the relevant fields during import. If a field value is null in AD, the corresponding field will not be updated in ServiceDesk Plus MSP. |
|
Select UDF for import |
If you have configured user additional fields in ServiceDesk Plus MSP, you can select the UDF fields. Specify the field name configured in the Active Directory beside the selected field to map them. If you have not configured any user additional fields, use the Click here to configure link. You will be redirected to the User - Additional Field page where you can configure the additional fields to be imported from Active Directory. The numeric additional fields hold up to 19 digits. If your numeric value exceeds 19 digits, then configure the value in text field. |
|
Move associated assets |
If the site associated with the user/department is changed in the Active Directory, the assets belonging to the user/department should also be moved to the new site. To update this information on every import, select Move associated assets. |
|
Update empty values |
Enable this option to import and update <empty> data from Active Directory. For example, with this option enabled, user data with the First Name : Admin changed to First Name: <empty> in Active Directory will be updated in the application. If this option is disabled, then the First Name: <empty> data will not be updated and old values will be retained. |
* Mandatory fields
Click Next.
The import wizard displays various OUs available in that domain. Choose the specific OU from which you wish to import users by selecting the checkbox beside it.
Click Import Now. If scheduled AD import is enabled, you can import the users later by selecting Save and Import in Schedule.
If the user information in the selected OUs are imported immediately, the data on how many records were added, overwritten, or failed to import will be notified to SDAdmins via bell notification. If the import is scheduled for later, the SDAdmins will be notified via bell notification after the schedule is completed.
The imported users are listed in the users list view under Admin > Users & Permission > Requesters. You can perform further actions on the imported users such as editing the details or associating workstations from the users list view.
Schedule AD Import
You can schedule Active Directory import at regular intervals to keep your user repository in sync with the Active Directory. When you schedule an AD import, data from all domains in the application is imported once every specified number of days. Users and user details from all the domains in the application are synced to ServiceDesk Plus MSP in two ways:
-
Full Sync - Updates complete user information during every schedule.
-
Delta Sync - Updates the differences in data once every 30 minutes.
To configure an import schedule,
-
Hover over Import Schedule fields and click Edit.
-
Enable the Schedule AD import once in every option and specify the import period.
-
Specify the date and time to begin the schedule.
-
Click Save.
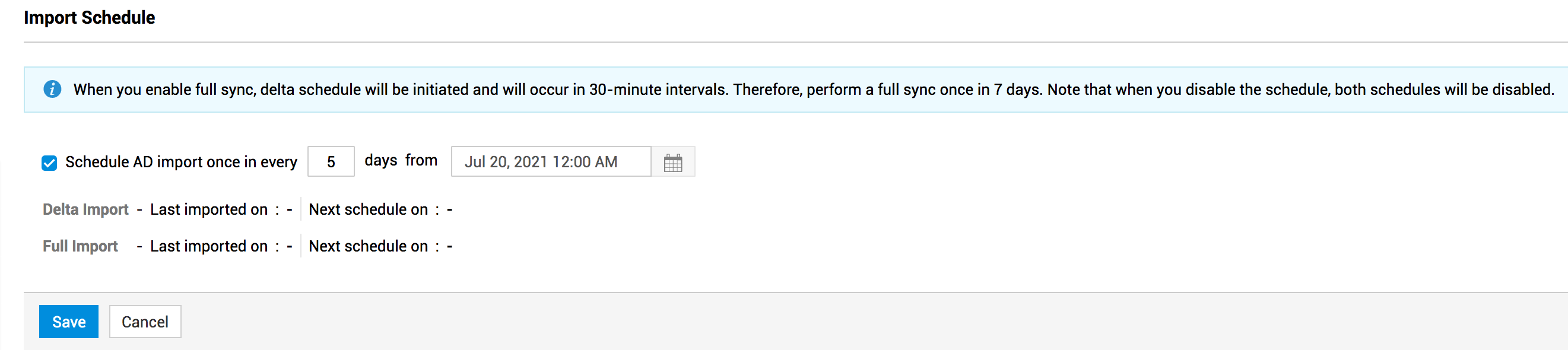
User details from domains will be imported periodically as per the number of days specified after the start date and time. The differences in the data will be updated every 30 minutes. You can view the last import time and the next schedule time in the Import Schedule section.
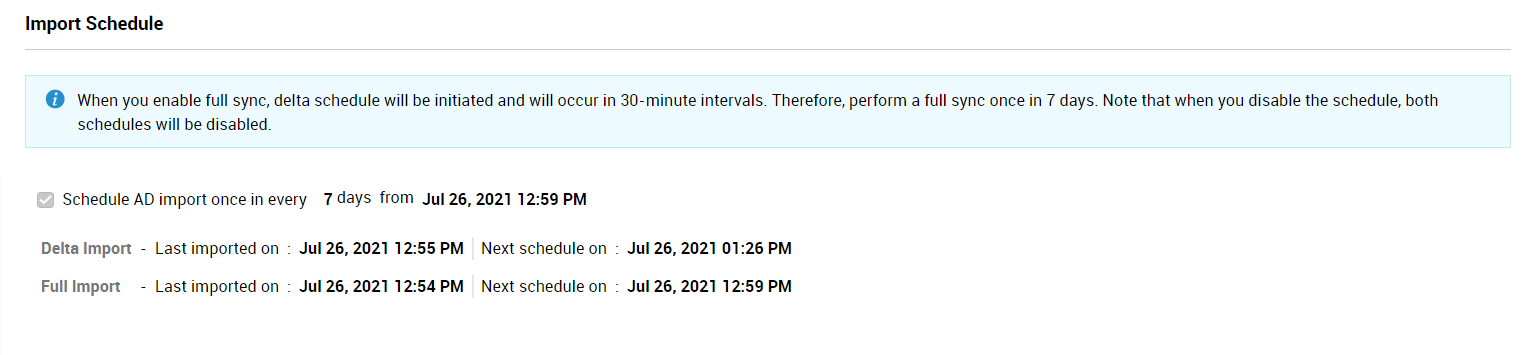
Note: During delta sync, only the user details that failed during import will be notified to the SDAdmins via bell notification.
The criterion for User Account overwrite in Active Directory User Imports:
While performing a user import from Active Directory,
Criteria 1: ObjectGUID - If the ObjectGUID of a user account in ServiceDesk Plus MSP matches with the user account in Active Directory, the record in ServiceDesk Plus MSP will be overwritten.
Criteria 2: Login name and Domain - If the login name and domain of a user account in ServiceDesk Plus MSP matches with the user account in Active Directory, the record in ServiceDesk Plus MSP will be overwritten.
Criteria 3: Email address - If the 'Override based on EmailId' option is enabled under Admin > General Settings > Advanced Portal Settings and if the email address of the user account in ServiceDesk Plus MSP matches with the Active Directory user account, the record in ServiceDesk Plus MSP will be overwritten.
Criteria 4: Login name and domain is '-' (not associated) - If a user account in ServiceDesk Plus MSP contains only a login name with an email address without a domain association and if the login name matches with the Active Directory user account, the record in ServiceDesk Plus MSP will be overwritten.
When a user is imported from AD, the ObjectGUID of the user is used as a unique identifier to update the user details in ServiceDesk Plus MSP. If the 'ObjectGUID' does not match for any user in ServiceDesk Plus MSP,
-
The 'loginname+domainname' of the user is used as a unique identifier to update the user details in ServiceDesk Plus MSP.
-
If the 'loginname+domainname' does not match for any user in ServiceDesk, the 'email address' of the user will be used as a unique identifier.
-
If the email address does not match, then the 'loginname + domain=NULL' ( where loginname is Howard (example) and domain name is NULL) is used as a unique identifier to update user details.
In cases where none of the specified conditions like 'ObjectGUID' , 'loginname+domainname', 'email address','loginname + domain=NULL' are absent in ServiceDesk Plus MSP, a new user will be added.
Sync deleted users from Active Directory
This option lets you sync the deleted users from Active Directory into ServiceDesk Plus MSP. Syncing of deleted users can be scheduled after a manual user import.
After the sync is completed, a list of deleted users is displayed. Based on the type of user, you can remove the deleted users from the list as mentioned below:
-
Requesters - You can enable automatic deletion for non-technicians from the deleted users list. When a requester is deleted from the active directory, the user will be removed from ServiceDesk Plus MSP as well.
-
Technicians - You can review the deleted technicians from the deleted users list and remove them manually. Automatic deletion is not available for technicians.
To configure syncing of deleted users,
-
Hover over the Sync Deleted User(s) from Active Directory checkbox and click Edit.
-
Choose your deletion method - automatic or manual. Note that even if you select automatic deletion, deleted technicians will not be removed automatically.
-
You can schedule syncing of deleted users periodically by enabling Schedule delete sync once in every option.
-
Specify the sync periodicity.
-
Enter the date and time to begin the syncing of deleted users
-
Click Save.
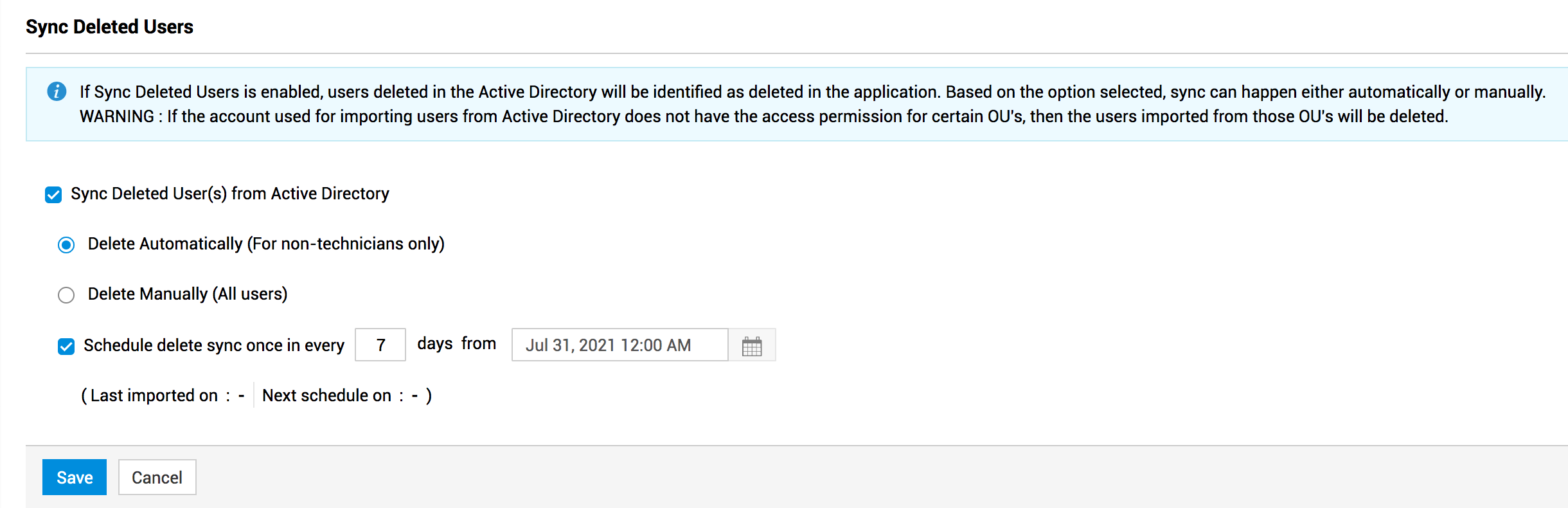
After the syncing of deleted users is scheduled, you can view the last imported time and the upcoming schedule time in the Sync Deleted Users section.
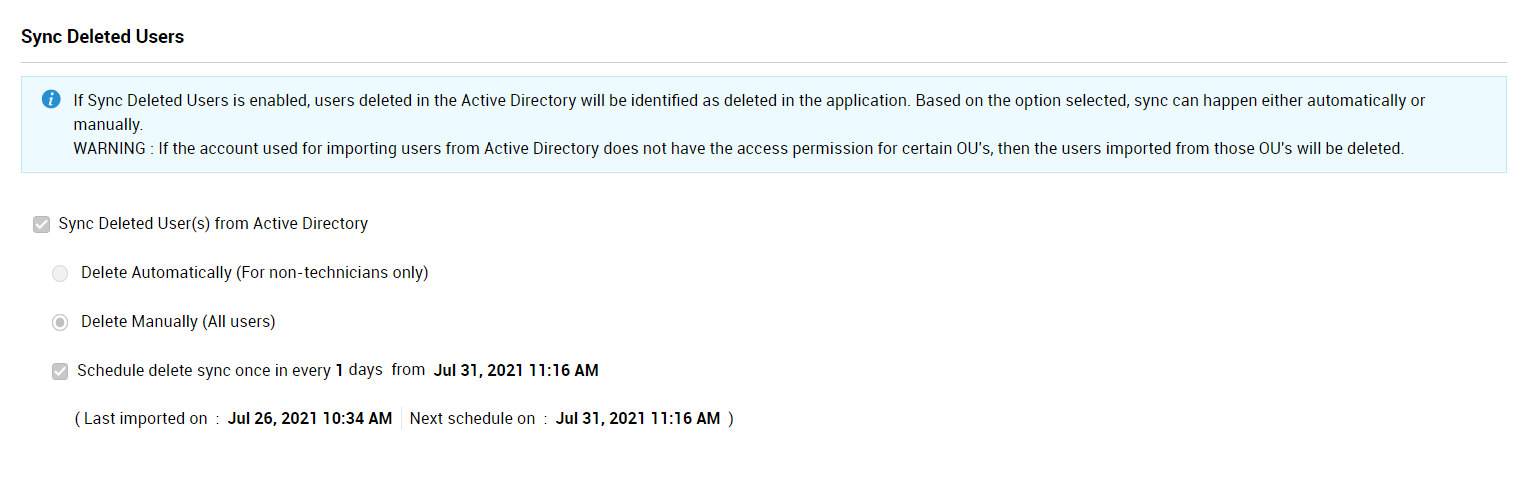
If manual delete is enabled, the link to the deleted users list will be displayed as a note on the top of the Active Directory configuration page. Use the links in the note to access and verify the deleted users before removing the deleted users from ServiceDesk Plus MSP.
If sync is disabled for deleted users, the deleted user details from AD will not be synced with ServiceDesk Plus MSP during manual or scheduled import.
Deleted user details will be notified to the SDAdmins through bell notification.
Active Directory Authentication
You can authenticate users login in ServiceDesk Plus MSP via Active Directory. AD-based authentication can be configured in two ways:
Login using AD Credentials
Facilitate login for users into ServiceDesk Plus MSP using the login name and password of their system.
-
Hover over Active Directory Authentication fields and click Edit.
-
Select Enable Active Directory Authentication checkbox.
-
Click Save.
In the Login screen, the users can specify their system/AD login credentials and select the Domain to log into ServiceDesk Plus MSP. They can also bypass AD authentication during login by selecting Local Authentication from the Domain drop-down and specifying their local authentication credentials.
NOTE: If a user account is not imported before configuring AD Authentication, the user will be added to ServiceDesk Plus MSP via dynamic user addition if proper login details are entered during authentication. Click here to learn how to enable dynamic addition of users.
If LDAP SSL is enabled for a domain in AD import page, AD authentication will also occur through LDAP SSL.
Allow Single-Sign On (SSO) using AD Credentials
SSO allows users to instantly access ServiceDesk Plus MSP without providing any login credentials. During login, users are automatically authenticated via an Identity Provider(IdP). You can enable SSO for AD users from SAML by configuring ADFS as the IdP. To learn more, click here.
Ensure that the AD users are imported to the IdP before configuring SSO.
Prerequisites for configuring LDAP SSL
By default, LDAP communications between client and server applications are not encrypted. This leaves the communication between the LDAP client and server computers vulnerable to network monitoring jump devices/software. ServiceDesk Plus MSP employs LDAP SSL to secure the communication between the AD server and ServiceDesk Plus MSP server.
Follow the prerequisites mentioned below to configure LDAP SSL for your AD server:
-
Ensure the server FQDN (Fully Qualified Domain Name) is accessible from client. Else, add the host entry in the host file in the client machine.
-
The Active Directory Certificate Services must be installed to use LDAP SSL certificate as explained in this documentation.
-
Enable your AD server to support LDAP over SSL. Click here to learn how.
-
The LDAPS certificate imported to AD server in the previous step must be fetched and imported it to the client machine (ServiceDesk Plus MSP server) in Personal folder as explained below:
-
Click Start, type mmc, and click OK.
-
Click File and click Add/Remove Snap-in.
-
Click Certificates and click Add.
-
In Certificates snap-in select Computer account and click Next.
-
On the Certificate Store page, right-click Personal > Import certificate, import the LDAP certificate from the copied folder, and provide the password set while creating the certificate.
-
Import Root CA certificate in Trusted Root Certificate Authority to allow your client machine to trust the imported LDAP certificate. This is vital since imported LDAP certificates will not be trusted due to cross domains, by default.
-
Access the CA web console: https://<CA Server>/certsrv and provide Administrator credentials. If the URL is not accessible, install Certificate Enrollment Web Service as explained in this guide.
-
In the console, click Download a CA certificate, certificate chain, or CRL.
-
On next page click Download CA certificate and save the certificate.
-
Import the downloaded CA certificate to the Trusted Root Certificate Authority as explained in the below steps,
-
Click Start, type mmc, and click OK.
-
Click File and then click Add/Remove Snap-in.
-
Click Certificates and then click Add.
-
In Certificates snap-in select Computer account and click Next.
-
On the Certificate Store page, right-click Trusted Root Certificate Authority and import the above certificate.
Behavior Changes after 12000 upgrade
-
AD and LDAP schedules are now executed independently. Therefore, users must configure them individually.
-
User details updated in the Active Directory will be reflected in ServiceDesk Plus MSP via Delta Sync. This schedule is initiated 30 minutes after the previous import schedule is completed.
-
Delta Sync can be enabled only if Full Sync is enabled.
-
Syncing of deleted user details should be scheduled independently of the user import schedule.
-
SDAdmins will be notified of the import success/failure details via bell notifications.
-
LDAP security protocol can be enabled while importing users from AD. If LDAP SSL is enabled, the ServiceDesk Plus MSP will connect with AD through port 636.
To add users dynamically after enabling AD authentication, the domain details and attributes must be configured in the Import Users pop-up at least once
Configure Pass-Through Authentication
On enabling single sign-on, ServiceDesk Plus MSP directly authenticates your windows system user name and password. Hence you need not login again to enter into ServiceDesk Plus MSP.
ServiceDesk Plus MSP Pass through Authentication uses NTMLV2 which provides better security and validates the credentials using NETLOGON service.
-
Enabling Active Directory, activates the Pass-through authentication (Single Sign-on) option.
-
If you like to activate single sign - on, select the Enable Pass-through Authentication (Single Sign-On) option.
-
You can enable Pass-through authentication for users from a particular domain. To do so, select the Domain Name from the drop-down list. Enabled domain should be two-way trusted.
-
Specify the DNS Server IP of the domain in the provided field.
-
To use the NTLM security provider as an authentication service a computer account needs to be created in the Active Directory with a specific password. Specify a unique name for the Computer Account and Password for this account.
-
The Bind String parameter must be a fully qualified DNS domain name or the fully qualified DNS hostname of a particular AD server.
-
Save the authentication. You will get a confirmation message on the authentication.
Upon saving the details, a new computer account will be created on the Active Directory (with the help of VB Script). If the user specifies existing computer accountname, the password specified here will be reset on the Active Directory for the computer account. User can choose to reset the password of computer account by clicking on the Reset Password link as well.
If there is a problem in creating a Computer Account or resetting a password of the existing Computer Account using VB script from SDP server(upon save, the script will be called automatically) , the details specified here will be saved and user can execute the script locally on the AD server specifying the same details to create computer account / reset password.
If there is an issue with computer account creation, user can specify an already created computer account name and reset password of that computer account with the help of reset password script.

