Defining incident response
Incident response (IR) is a systematic approach to helping IT teams be prepared and plan for IT incidents, including a service interruption, a breach to an organization's security, or a cyberattack. No organization is ever fully immune to IT incidents, particularly security incidents given the current remote work situation adopted by businesses. When security incidents hit, they hit hard, causing destruction to data, violating confidentiality, and inducing significant loss in terms of productivity and finances, which involves a lot of effort to bounce back from. However, with a constructive IR plan, it's possible to handle these situations more effectively and restore normalcy faster. Ponemon's Cost of a Data Breach Report confirms that organizations with a robust security IR plan have cut down security incident-instigated costs by an average of about $2 million USD.
Organizations should therefore consider a clear-cut IR plan and its course of action a priority, and design an IR process defining what an incident is to their company, create an incident response team with roles, and train them sooner rather than later.
Understanding the phases of incident response

The approach with which an organization responds to an incident, known as the response procedure, has significant bearing on the aftermath of the incident. Typically, the incident response process begins with establishing the IR plan, tailor-made for their organization and its functioning, and delegating roles and responsibilities to the incident response team. The following are the different phases of incident response for a security incident, according to the National Institute of Standards and Technology (NIST).
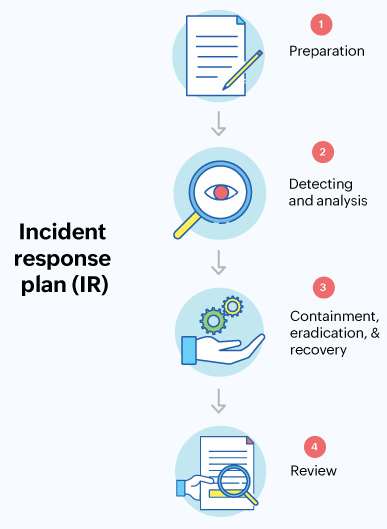
1. Preparation
Preparation is the most crucial phase of incident response. Drawing out a strategy, documenting it, building the incident response team, designating roles and responsibilities, appropriate communication and training, and procuring the required software and hardware are all part of the incident response plan and preparing for a security breach.
2. Detecting and analysis
This phase is when the actual IR takes place, starting with identifying and reporting security incidents. This leads to the question of who reports an incident and how.
All members of the organization should be aware of the IR plan in place, and should report security breaches as soon as they suspect it. It's also important to inform customers about the IR plan so they can keep an eye out, too. Employees and customers alike must report security issues that they detect in their working environment. The following are a few scenarios where the issue should not be ignored, and must be reported as soon as possible for a rapid response.
- Customers reporting security issues to the organization's support channels
- Threats to customer data through security issues detected internally
- Security alerts triggered from intrusion detection systems and monitoring tools
- Email communications that may carry viruses
- Detection of malware on any of the organization's devices
When an employee detects a security incident, they must report it to the IR team. The organization should enlist different modes through which security incidents can be detected, such as webforms on the self-service portal, emails, chats, phone calls, collaborative digital workspaces including Microsoft Teams, and more. This must be clearly defined as part of the IR plan, and published for employees and customers.
NIST lists five steps for the detection and analysis phase:
- Identifying the early signs of a security incident
- Analyzing the signs to differentiate an actual threat from a false alarm
- Documenting the incident with all the facts and relevant response procedures to be applied for handling the issue
- Prioritization of the incident based on an impact analysis, considering its effects on business functionality and confidentiality, and the time and response effort it requires for recovery
- Notifying the involved teams and individuals by the IR team, explaining the IR plan, and the steps to follow for quick recovery
3. Containment, eradication, and recovery
The idea behind the containment phase is to bring the incident under control as early as possible, and to halt its effects in a way that doesn't cause any further damage. This requires identifying the exact systems that are under attack, and mitigating the effects with the IR containment, eradication, and recovery strategies. Eradication of the issue can be carried out using an effective incident management tool, and driving resolutions using knowledge articles published in the service desk's knowledge base. For the security incident to be considered no longer a threat, a recovery strategy should be in place. This phase also includes checking the affected systems, and bringing them back to the business environment.
All of these strategies should be built on criteria such as the severity of the security incident, the condition of the affected systems, the impact on business, recording evidence and all information on the incident, and the tools and resources required to orchestrate the strategy.
4. Review (post incident analysis)
A feedback and review meeting involving the IR team, the organization's authorities, and every individual involved in the security incident is mandatory to record lessons learned, and analyze the effectiveness of the IR plan and its strategies in each phase. Here are a few points to reflect on during the review phase:
- The root cause of the incident and where it occurred
- Could the incident have been prevented
- The performance of the IR plan and the IR team
- The effectiveness of the strategies in every phase
- Tasks that may have fallen through the cracks
- Any step that would have worked better if done differently
- Threat detection to prevent similar incidents in future
Having understood how an incident response should be handled, it's also important to realize that achieving an effective IR process can be challenging without the right tools. Organizations sometimes lack the required skills in-house, and need to outsource IRs. Either way, to handle IRs effectively, a comprehensive tool to manage incidents is an advantage to ensure minimal damage and downtime from security incidents.
Quickly assess your IT incident management practices with our toolkit
- A self-scoring assessment to gauge your core incident management practices, from incident identification to closure
- A checklist to review your team's readiness to tackle major incidents for the hybrid work environment
- A cheat-sheet to help overcome the common incident management challenges faced in the hybrid work model

