Secure Remote Desktop Software
Secure remote access is essential in today's digital landscape. With the potential dangers of unprotected, unattended remote access, it's crucial to prioritize robust security in remote access solutions. Introducing Remote Access Plus — a strengthened secure remote desktop designed to maintain your privacy and meet regulatory standards. Whether you're an IT expert, support staff, or a strategic CIO, trust Remote Access Plus for reliable remote control and unmatched data security.

Key-features of our secure remote desktop software
Authenticating admins/technicians
To ensure the security of your accounts, it's crucial to have a robust security plan that begins before you log in. Enhance your login process's security with MFA (multi-factor authentication), 2FA (two-factor authentication), SSO (single sign-on), and SAML (security assertion markup language). Utilizing 2FA, you can employ apps like Zoho OneAuth, Google Authenticator, Microsoft Authenticator, or Duo for an added layer of protection during login.
Keep your account safeguarded by personalizing your own password policy, specifying:
- Maximum number of incorrect password attempts.
- Duration of lockout for repeated incorrect attempts.
- Minimum password length.
Encrypted and password-protected screen recording
- Stay productive while working remotely with Remote Access Plus! Safely capture your screen during remote work sessions.
- Keep your recordings secure with password protection. Only authorized users can download and view them.
- Enjoy peace of mind with Remote Access Plus! Users will receive notifications when screen recording is in progress to prioritize their privacy.
Secure file transfer
Securely transfer any type of file with Remote Access Plus. Our advanced security technology keeps your data safe during encrypted transfers, so you can relax knowing your files and important folders are protected from cyber threats. No more worries about interception or data theft!
Additional layer of security for roaming users
Safeguard your data while working remotely! Our exclusive Secure Gateway Server acts as a protective shield, ensuring your information remains secure during remote sessions. No need to worry about hackers or unauthorized access when communicating or transferring data to our central server from your roaming computers. Stay protected with our secure remote desktop solution!
Compliance customizations
Safeguarding your privacy is our priority! To ensure fairness and security, we adhere to important regulations like HIPAA, GDPR, and PCI DSS. When it comes to remote access, we offer user-friendly options such as seeking your approval before starting a remote session or accessing your command prompt or file manager.
Privileged-based restrictions
In larger companies, multiple technicians and admins utilize the product console. To simplify operations and ensure clarity, we offer various access levels based on roles. Each person has specific permissions, allowing them to see and perform only what's necessary. Some enjoy complete control, while others have limited viewing access. This approach maintains organization and enhances security for everyone involved.
How to set up secure remote access?
Here is how to set up secure remote access with Remote Access Plus:
Harden Credentials
- Strengthen your login details: Change the default credentials for added security.
- Access your profile: Click the user icon on the top right and select Personalize.
- Update your password: Go to the Change Password tab and enter your new, secure credentials
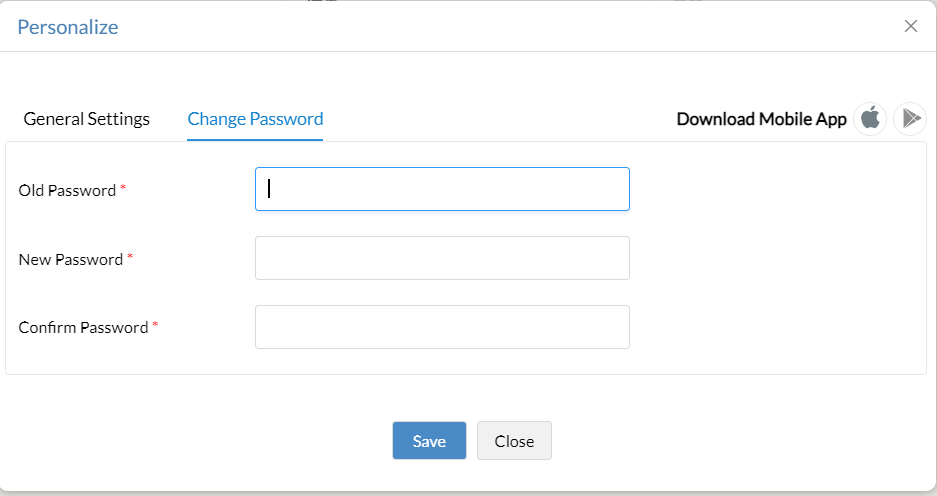
-
- You can customize password policies for technicians by navigating to Admin -> Global Settings -> User Administration -> Secure Authentication -> Password Policy.
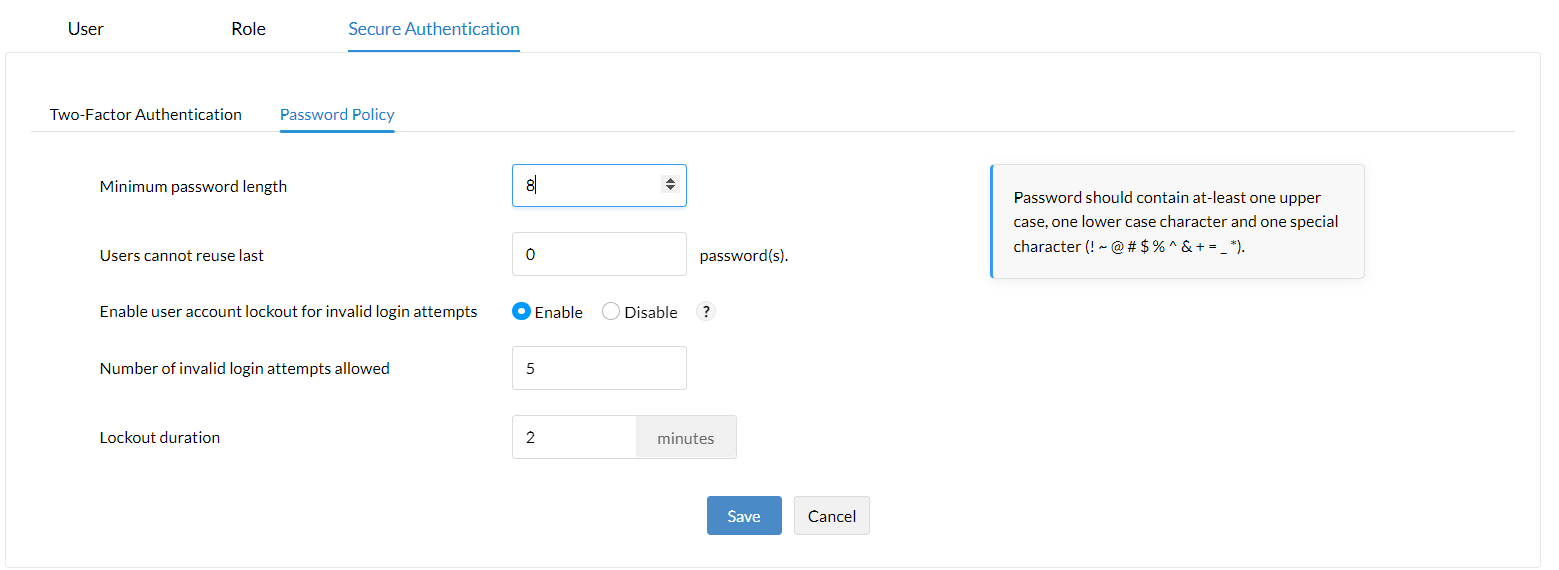
Authenticate and Secure
- To enhance security, it's crucial to activate the built-in two-factor authentication for the web console. Simply follow these steps:
- Go to Admin > Global Settings > User Administration > Secure Authentication > Two-Factor Authentication.
- YFrom there, you can select either email or an authenticator app as your preferred two-factor authentication method, depending on what works best for you.
- Additionally, Remote Access Plus offers SSO and SAML authentication. For configuring SAML authentication, just click on Admin > Global Settings > SAML Authentication.
Set a Security Fence
- Restrict the end user from uninstalling or stopping the service.

- Only technicians within the configured IP scope will have access to the console.
Note: For more security settings, navigate to Admin -> Security Settings. Know more
FAQs about secure remote access solutions
1. What is secure remote access?
Secure remote access involves the capability to connect to a computer or network from a remote location while safeguarding the transmitted data, preserving the user's session privacy, and preventing unauthorized access. This secure remote access solution is commonly employed by remote workers, IT administrators overseeing servers, and support personnel resolving client issues.
2. What does secure remote access software do?
Secure remote access solutions enable users to securely connect to another computer or network from a distinct location. These solutions establish a protected and encrypted link between a remote user and the target system, guaranteeing the confidentiality of transmitted data and safeguarding it against unauthorized access or tampering.
3. Why is secure remote access solution important?
In today's digital era, secure remote access solutions are vital for users to connect to systems and data from any location without compromising security. With the increasing trend of remote work and global collaborations, the need for accessing information remotely is crucial. However, this convenience poses risks like cyberattacks and data breaches.
Secure remote access solutions address these challenges by providing flexible and efficient connectivity while ensuring the protection of sensitive data and systems. Through encryption and authentication, these solutions safeguard organizational assets, ensuring business continuity and maintaining user trust.
4. Is secure remote desktop software free?
Yes, Unlock the full potential of Remote Access Plus' free edition! Enjoy complete access to advanced security measures and remote control features. Start exploring and experiencing it now!
- Stay secure by verifying the technician's identity when they log in to the system.
- All communication from a remote location will go through a gateway.
- To protect your privacy, we won't establish a remote connection without your permission.
- Your data, files, folders, and any recorded videos will be safely encrypted to keep them secure.
6. What technologies used for Secure Remote Access?
Remote Access Plus is a secure remote access solution that allows you to access your computer remotely without being physically present. Here's how we keep your data safe:
- Login: We use multiple layers of security to ensure only authorized users can access your computer. This includes requiring you to provide more than one form of identification, using a single sign-on system for convenience, restricting access based on specific roles, and enforcing a strong password policy.
- Communication: When transferring files between your computer and the remote access server, we use encryption to keep your data secure. We also have a dedicated server for mobile devices, so you can connect securely even when you're on the go. Additionally, we use a special and secure protocol for establishing the remote connection itself.
- Privacy: We value your privacy and give you control over remote connections and diagnostic tools. You have to confirm and authorize each remote connection, and screen recording is password-protected to ensure that only authorized individuals can access and view the recorded sessions.
7. Benefits of secure remote access solutions
- Follow company rules easily: By using secure remote access solutions, you can easily stay compliant with your company's policies and guidelines.
- Better communication for people on the move: If you're someone who travels or works outside the office, secure remote access solutions help you stay connected securely and ensure smooth communication.
- Enhanced security with controlled access: Secure remote access solutions provide an extra layer of security by allowing only authorized users to access sensitive information or resources.
- Stay protected from threats and attacks: By using secure remote access solutions, you can stay one step ahead of potential threats and attacks that could compromise your data or privacy.
- Customize and protect your privacy: With secure remote access solutions, you can make simple adjustments to maintain your privacy while accessing important resources or information.
8. How to choose a secure remote access software?
- Make sure the software meets important rules and regulations.
- Look for software that can use strong security measures like using your existing login (SSO) or requiring multiple factors to log in (MFA).
- Choose software that allows you to control who can access your network as it grows.
- Consider software that has helpful features like reports, logs, and the ability to monitor everything that happens.

