ManageEngine named a Market Leader in KuppingerCole Leadership Compass 2024 for Identity Governance and Administration! Access the report
Cyberthreats are growing beyond human visibility. As companies become more sophisticated in their cloud adoption, so do attackers in their innovation.
Network boundaries are slowly vanishing, making identity the new security perimeter that needs protection. Identity analytics is the process of using AI and ML technologies and crunching identity-related data to generate actionable insights. Identity analytics tools evaluate risk based on identity-related information received from multiple sources.
ManageEngine AD360 gathers data on what users are doing across the company over a long period before establishing a baseline of normal activities unique to each user. It establishes strict access controls to ensure security across on-premises and cloud applications from a centralized console.
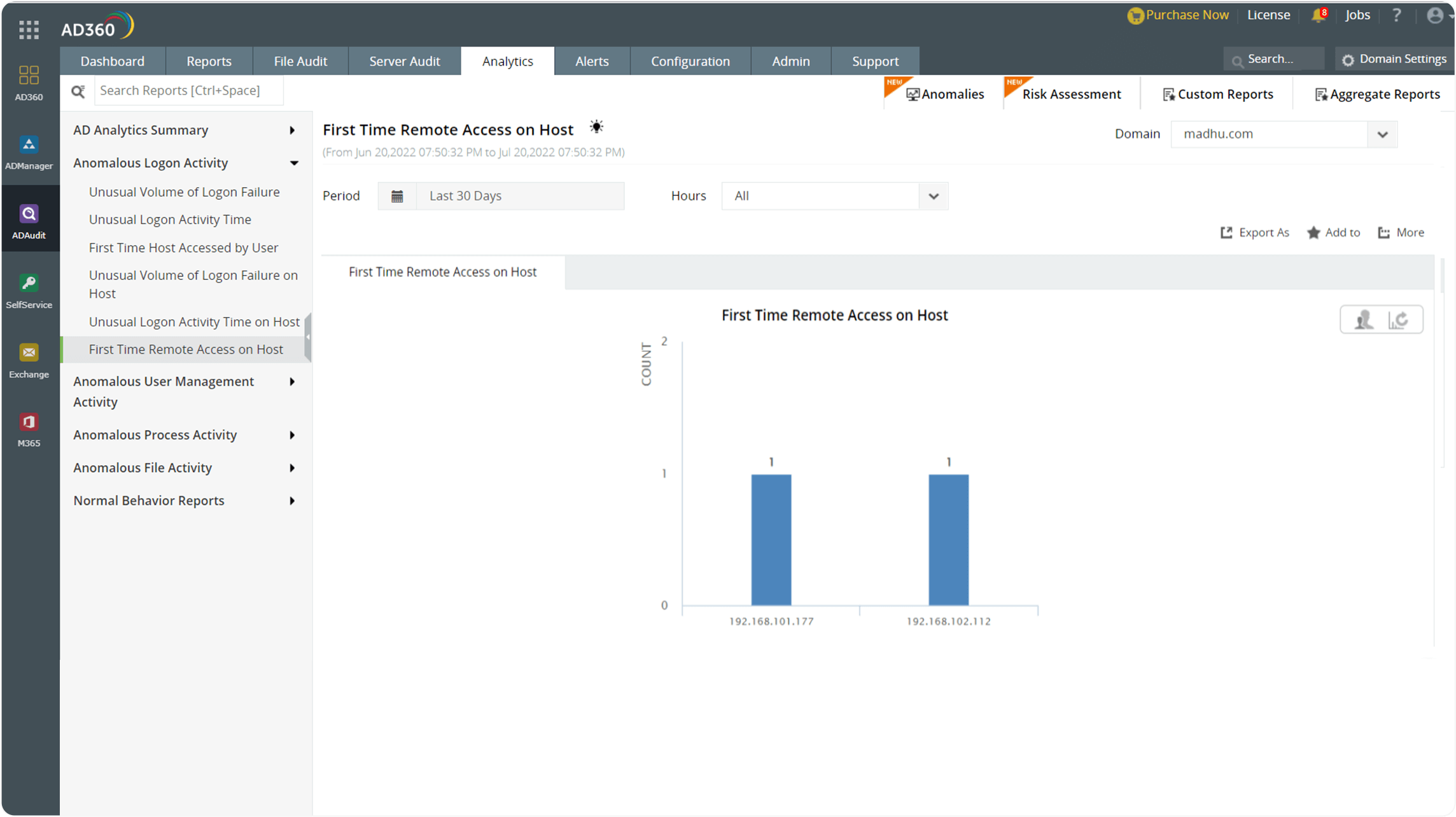
Get instant alerts when a host is accessed remotely for the first time.
Get instantly notified via email and SMS of critical activities such as file deletions.
Execute scripts to automate response actions, like shutting down a device or disabling an account.
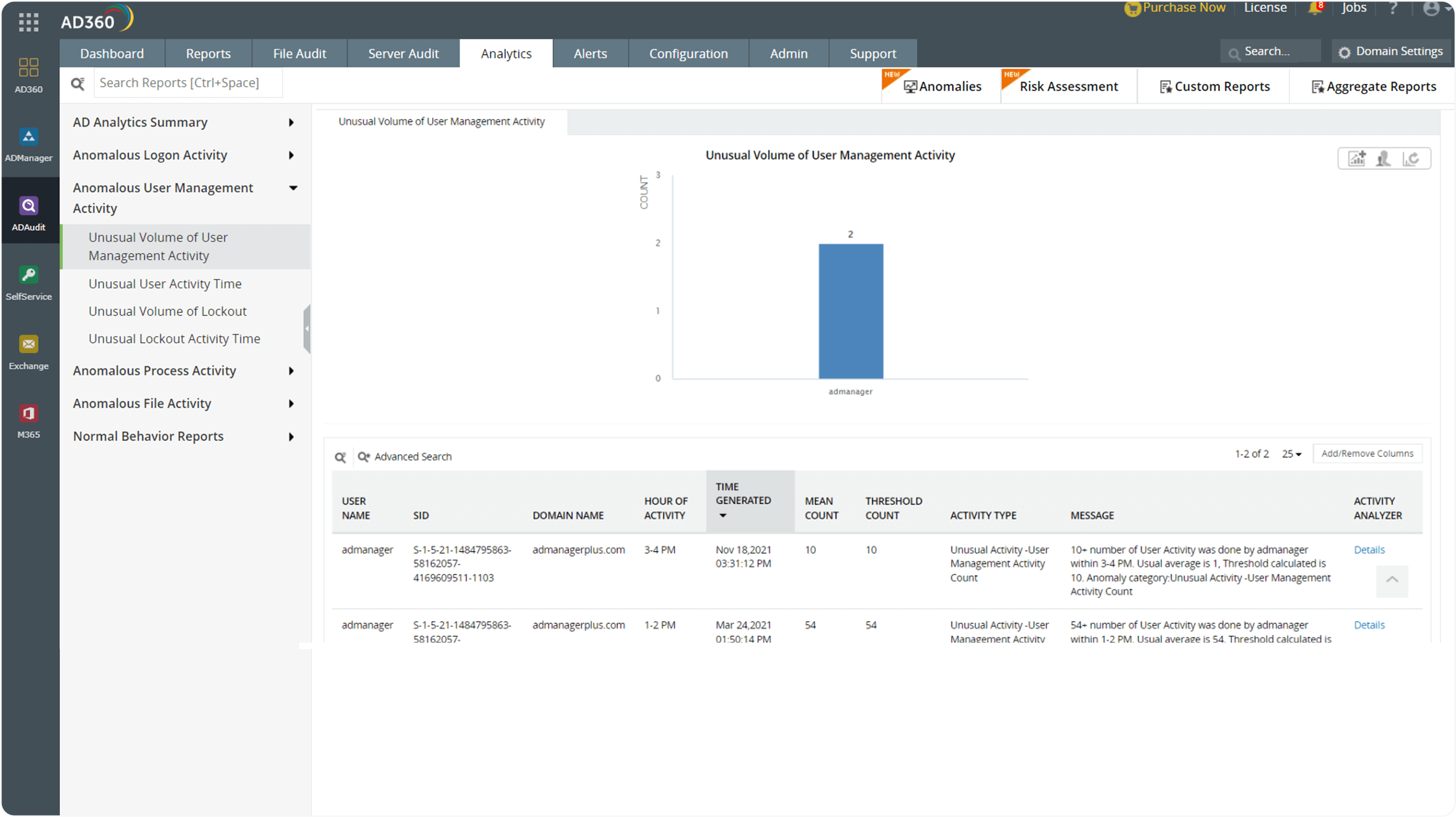
Establish user activity patterns and spot subtle anomalies.
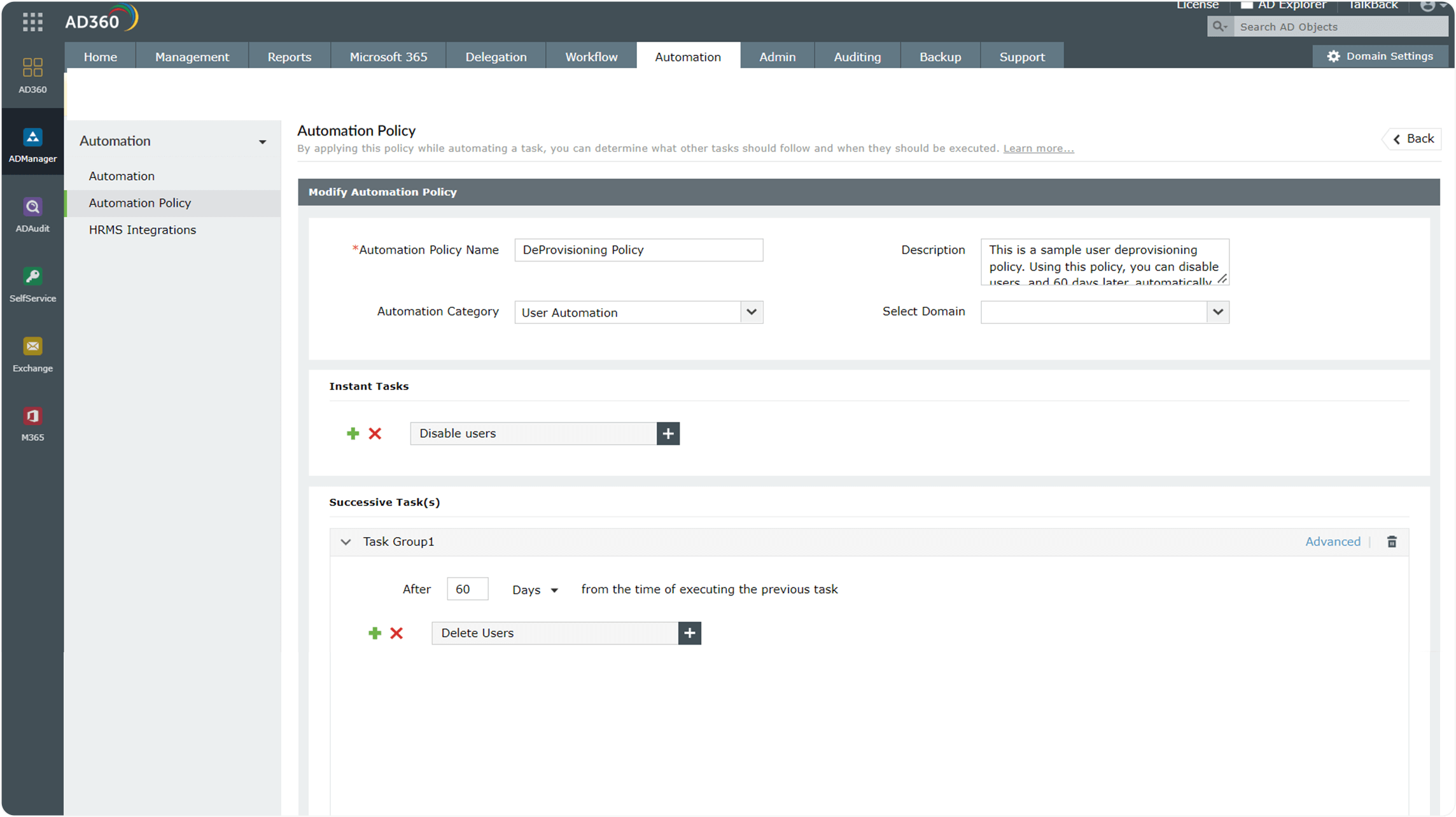
When you want to configure a sequence of tasks that should be executed at prespecified intervals, you can create an automation policy and implement it on the Automation tab.