Zero-down on threats with Log360's precise model of ML-based adaptive threshold
Current network security tools and SIEM solutions aid security analysts in gaining an overall visibility of enterprise networks and defending against cyberthreats. However, as the scale and volume of network logs, incidents, and threats grow exponentially, it has become inevitable for SOC teams to deal with the following pain points:
Manual handling
Analysis, configuration, and periodical revisions for multiple threat cases.
False alerts
Sifting through 1,000s of notifications from security tools to find one or two critical alerts.
As we transition to more advanced and automated threat detection systems to resolve these concerns,
ManageEngine Log360 has stepped into the world of a true next-gen SIEM by introducing
the industry's first adaptive threshold capability for real-time alerting.
Explore what the feature offers:
How does Smart Threshold work
- The Smart Threshold functionality is a part of Log360's Vigil IQ, the threat detection, investigation, and response (TDIR) module of Log360, which works with the real-time event response console, and user entity behavior analytics (UEBA).
- Utilizes the exponential moving average (EMA) algorithm to automatically analyze and fix a baseline count for events and anomalies occurring within a specific timeframe.
- Updates the baseline threshold periodically for every 15 data sets.

Events aggregated from across your network with with Log360's centralized log management system.
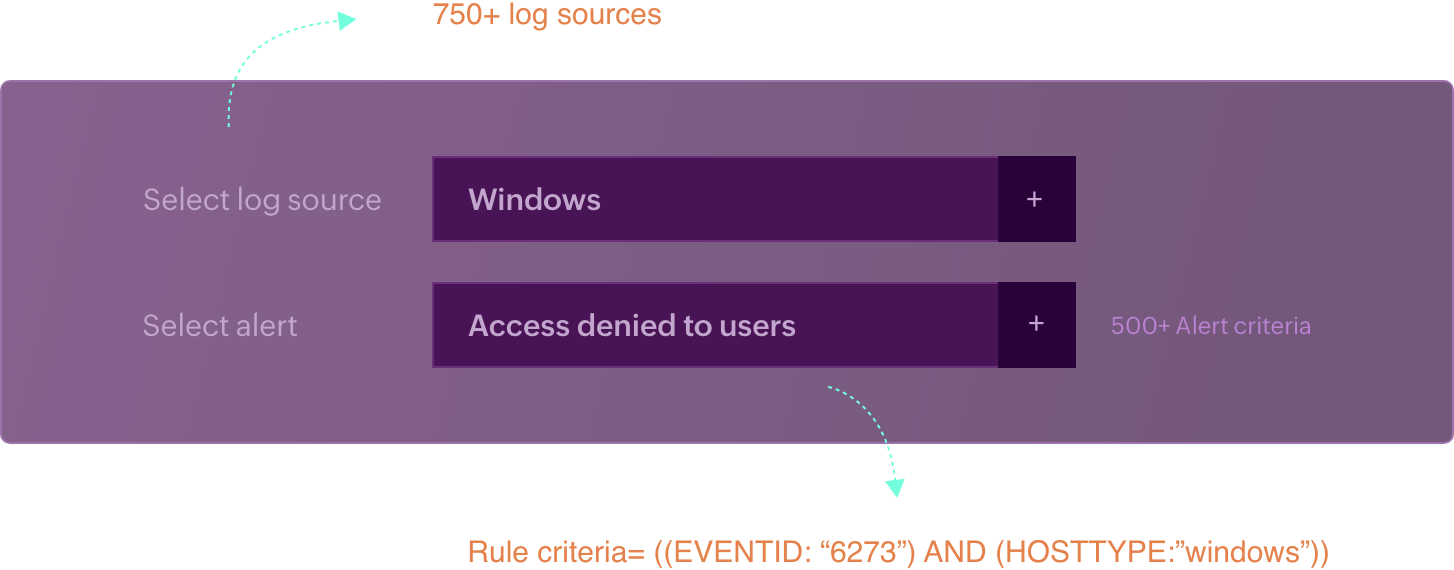
Log360 collects, parses, and analyzes logs from 750+ log sources, providing real-time records of all the events occurring in your network.

Detecting anomalous events and patterns with alerting modules.
The SIEM alerting module uses 100s of prebuilt criteria specific to different log sources to detect malicious activities from the recorded events.
The UEBA capability uses ML-based behavior analytics and pattern detection to trigger anomaly alerts.

Precision tuning to filter true alert cases with adaptive threshold.
The alert generation is further fine-tuned using the adaptive threshold functionality to precisely notify you when there is a deviation from the usual occurrence of events or anomalies.
Why should you consider adopting Smart Threshold?
- Automation
- Threat detection
- Accuracy over time
- Count-based anomalies
Automation
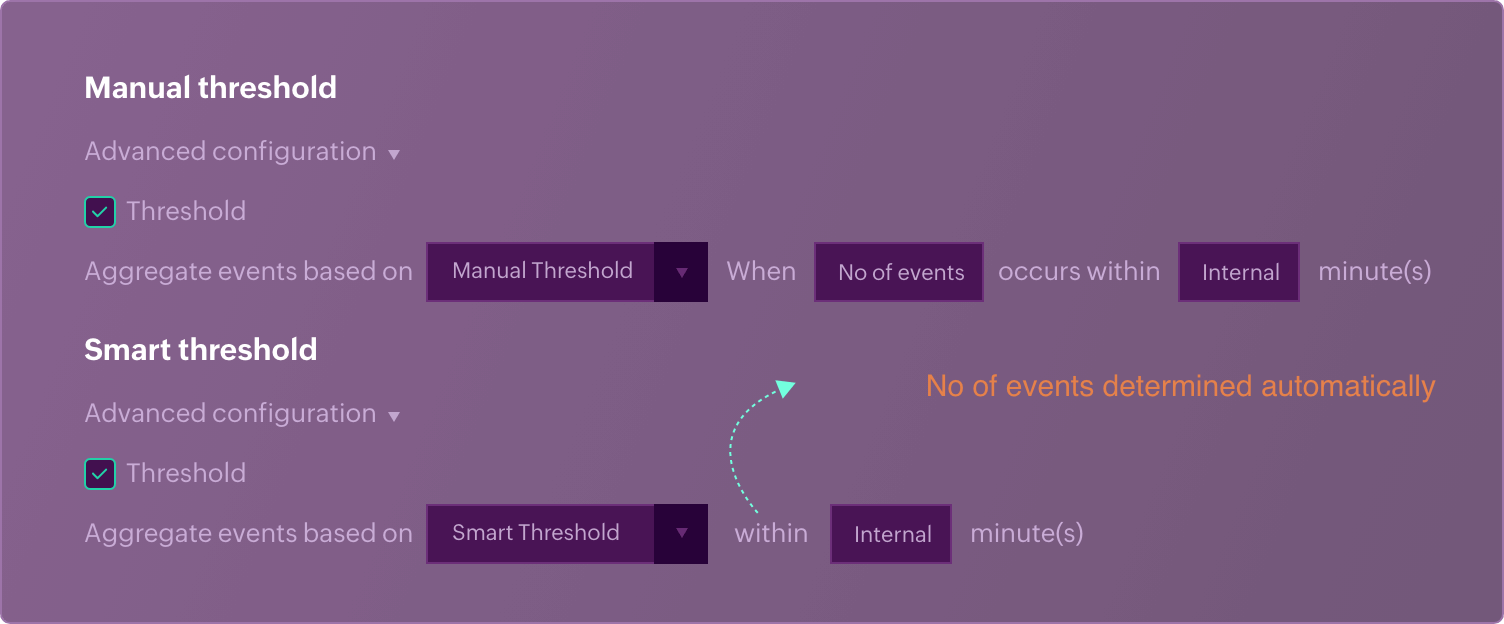
Setting thresholds for specific timeframes, based on the log sources and alert criteria, is one of the advanced configurations offered in SIEM solutions to reduce alert noise. Log360's adaptive threshold feature automates this functionality and aids SOC teams in enabling multiple alert profiles required for their environment, without the hassles of manual configuration.
Dual-layered model for precise threat detection
While the UEBA module accurately finds anomalies, precise threat detection is also needed to avoid working on low priority, non-threat events, or false positives. The Smart Threshold layer along with the UEBA module will contextually enrich the anomaly feeds and precisely identifies real threats. While the first layer of the prebuilt anomaly detection in UEBA finds deviations from established patterns and prioritizes them based on risk score, the second layer creates a baseline threshold for the frequency of deviations to spot anomalies that are real threats.
Improved accuracy over time with dynamic adaptation
With Log360's Smart Threshold, there's constant learning and fine-tuning of the threat detection process. The dynamic ML model of EMArevises the threshold baseline for every 15 data sets based on the changes in the network such as:
- Evolving user behavior
- Increase or decrease in the amountof log sources
- Configurational changes, such as an updated firewall rule, that might start allowing more traffic
- Modifications in the SIEM alert criteria and anomaly rules.
Early detection of count-based anomalies and remediation
Count-based anomaly detection is configured for commonly occurring network events to help capture important indicators of compromise early on, before threat patterns of ransomware attacks, and advanced persistent threats fully develop. The table below provides examples of some count-based anomalies that can be early indicators of known attacks.
| Count-based anomalies | Early indicators of compromise |
|---|---|
| Logon | Brute-force attack Credential compromise |
| Abnormal spikes in new outbound or inbound connections | Command and control channel compromise, data exfiltration |
| Increase in DNS redirect events | Pharming attacks, botnets |
| New files popping up, increases in resource utilization and application crashes | Malware |
Log360's adaptive threshold helps find significant spikes in these events without a constant trigger of false alarms. The early detection IoCs also facilitates immediate response and remediation of threats, gradually reducing the mean time to discover (MTTD) and mean time to respond (MTTR).
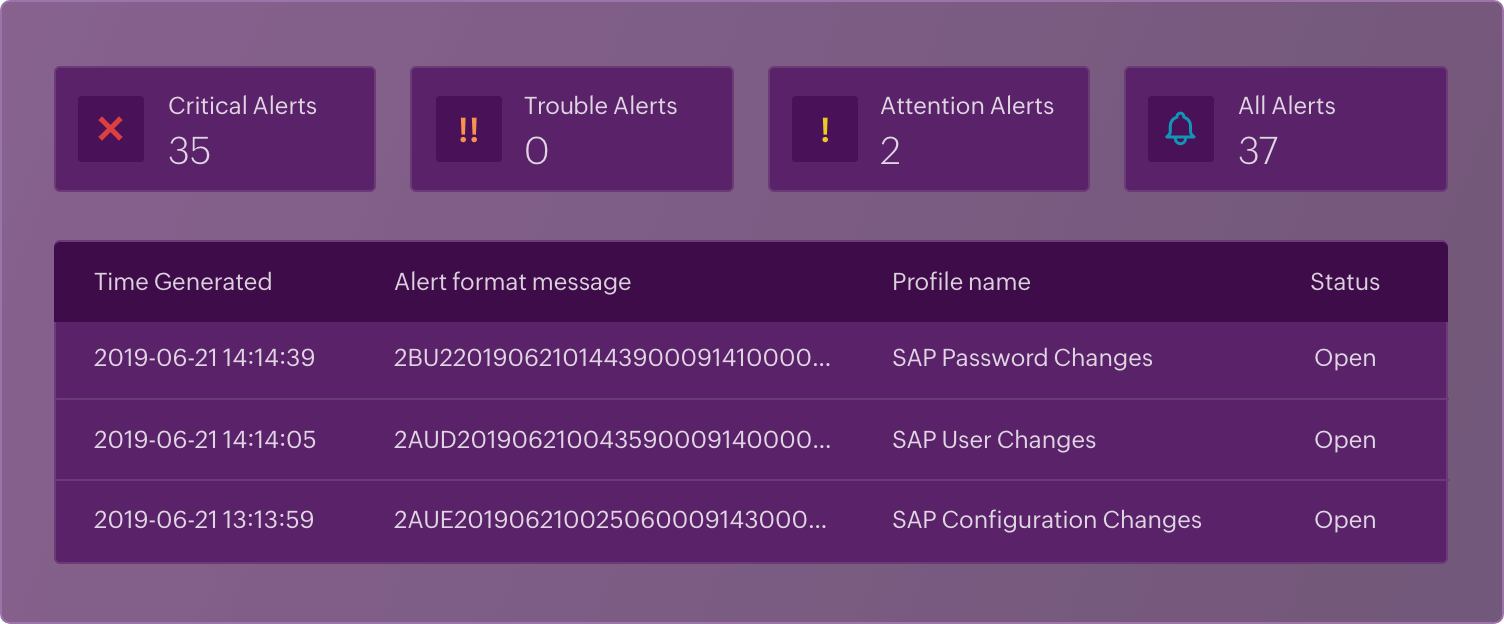
Alerts in Log360
- Add log sources and criteria
- Manual vs smart threshold
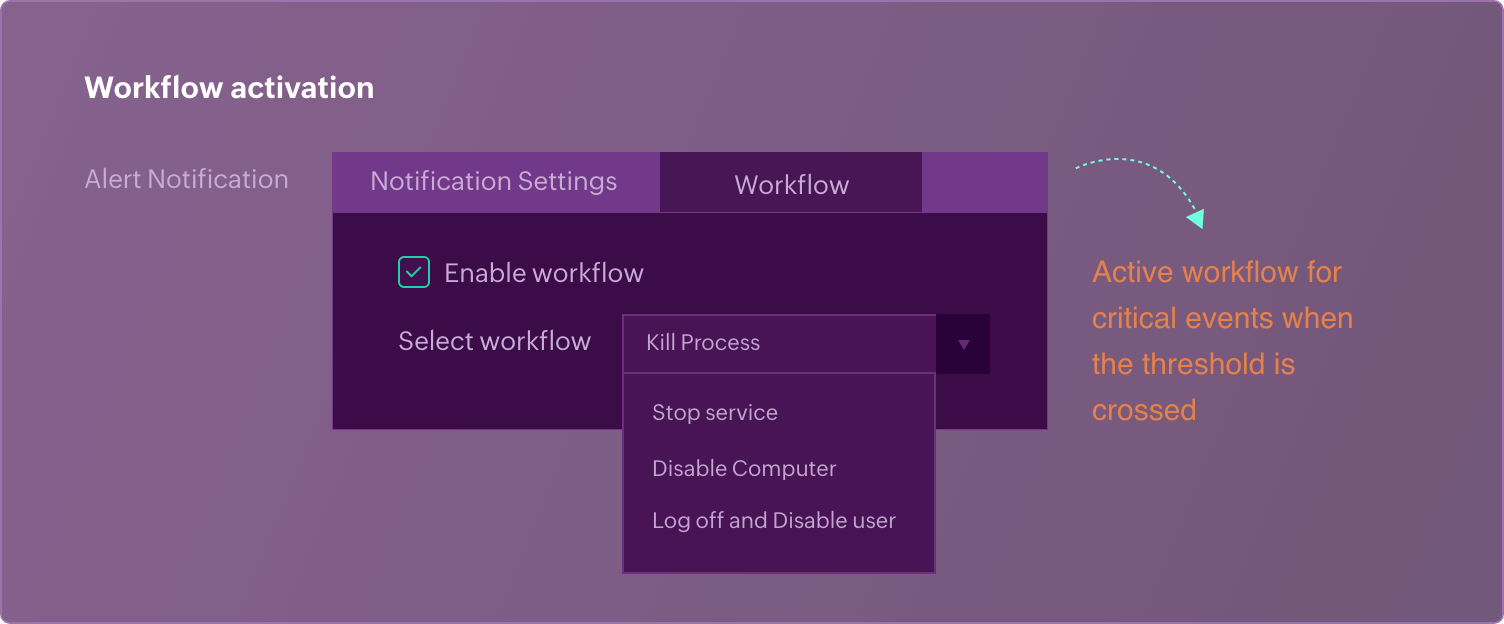
- Remediation workflow
- Manage alerts in a central dashboard
Add log sources and criteria
Manual vs smart threshold
Remediation workflow
Manage alerts in a central dashboard
Why Log360?
Ease of configuring alerts
Build your alert profiles with ease by using Log360's real-time alerts dashboard that offers:
- A variety of log sources, including a wide range of network devices, applications, vulnerability scanners, and more.
- Over 500 prebuilt criteria for different usecases
- Advanced configuration with automated adaptive threshold
- Single console to monitor alerts, filter them based on severity, and create tickets
- Integrated workflow activation for alert profiles
Advanced threat intelligence
Log360 also ingests STIX/TAXII and Alienvalult OTX threat feeds for contextual threat detection along with offering rule-based pattern detection with real-time event correlation and implementation of threat modelling framework MITRE ATT&CK.
A complete suite of integrated tools
Level up your TDIR game by deploying a comprehensive SIEM solution like Log360 with UEBA, CASB and integrated DLP capabilities that brings all your security needs into single console, and helps you precisely detect threats with automated features like adaptive alert threshold.
Frequently Asked Questions
What is adaptive threshold?
In the context of SIEM solutions, adaptive threshold is a mechanism that dynamically analyzes the occurrence of events in the monitored network to create a baseline that differentiates normal behavior and true anomaly cases. Adaptive threshold dynamically adjusts to the changing environments and uses statistical ML models to achieve this.
What is a layered threat detection system?
Threat detection modules discover malicious patterns in a network, find abnormal spikes in flow of events, and use rule-based and signature-based methods to detect threats. Sequencing multiple methods of anomaly detection produces a layered threat detection system.
In Log360, count-based filtering using adaptive threshold is layered on top of behavioral-based anomaly detection. Here's an example to understand how it proves effective with precise threat detection:
Layer 1 behavioral pattern - Generate anomaly if important work files are accessed during non-working hours.
Context: Consider an enterprise environment with 1000s of employees. Employee A is a malicious insider, who is about to leave the company. He/she has been suddenly accessing multiple files during non-working hours. The above mentioned pattern will generate alerts for this behavior. But the issue is, this true alert will be buried in 100s of similar false alerts. There can be multiple genuine reasons for user behavior deviations in an enterprise with huge number of employees.
Layer 2: Smart Threshold - if a particular user account generates multiple anomalies within a specific timeframe that deviates from the usual count, generate alert.
A layer 2 of filtering with count based adaptive threshold, will cut down the alert noise for the 100 other users who usually have a few anomalies normal to their behaviour. But it will single out employee A's activities by generating alert, since it crosses the threshold.
Listen to those who transformed security with Log360
Try Log360 for free
Experience the extensive capabilities of unified SIEM utilizing Log360
Download nowWalkthrough with experts
Schedule a one-on-one call with our solution experts to explore Log360
Schedule demoZoho Corporation Pvt. Ltd. All rights reserved


