Your first step to win the battle of defense: Detect the enemy.
If you're looking for a solution that can detect cyberthreats in your environment, send real-time alerts, and automate incident response, you're at the right place. Log360, ManageEngine's SIEM solution, can accomplish all of that and more.
Analyze threats with contextual data obtained from Log360's powerful correlation engine integrated with a comprehensive threat intelligence platform that reduces false positives and features:
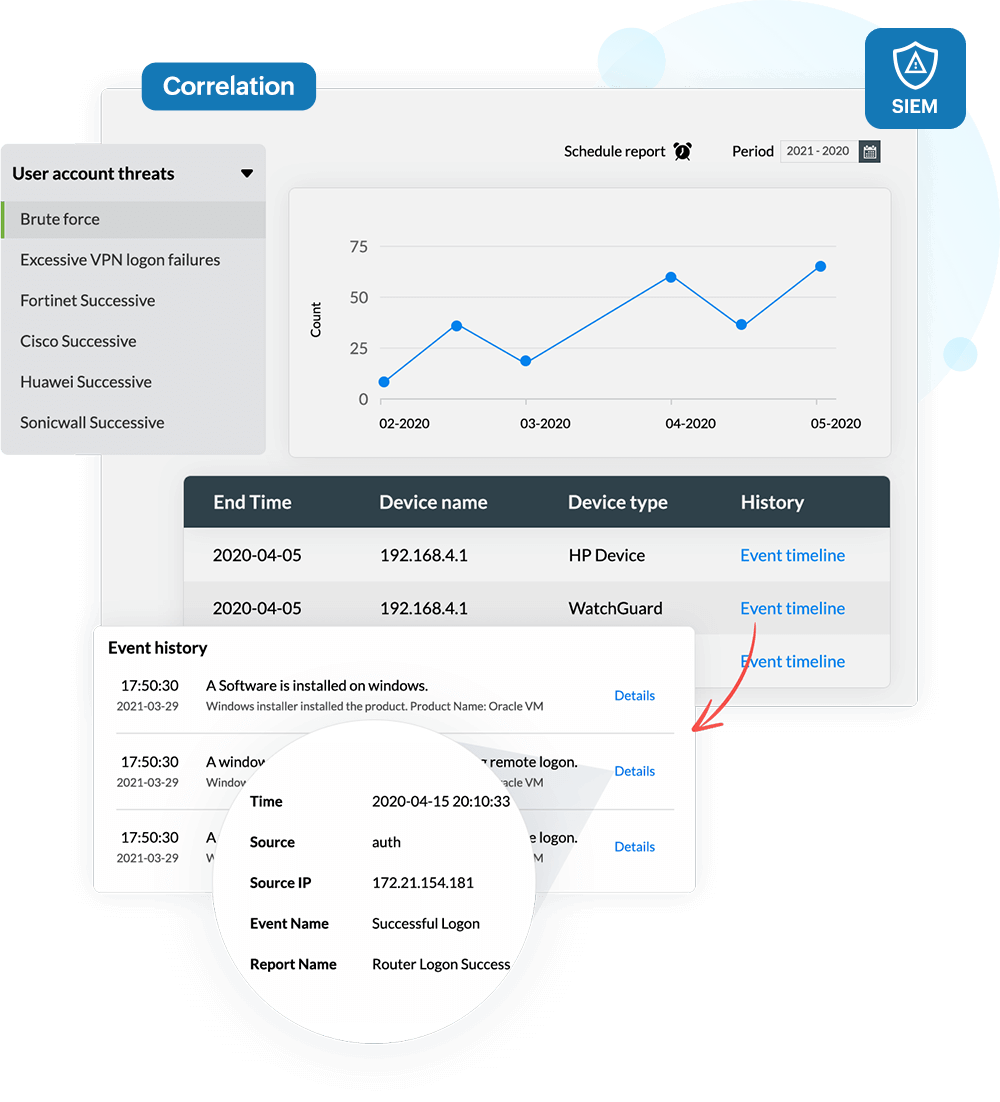
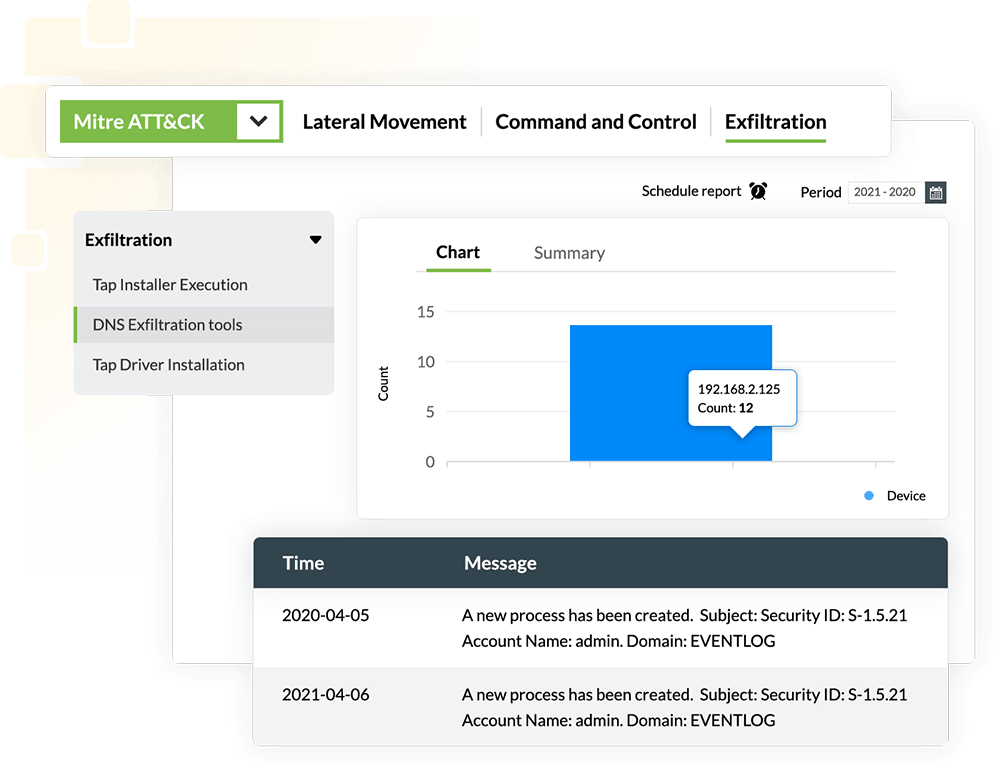
Log360 supports the MITRE ATT&CK framework that traces and uncover intruders, and provides:
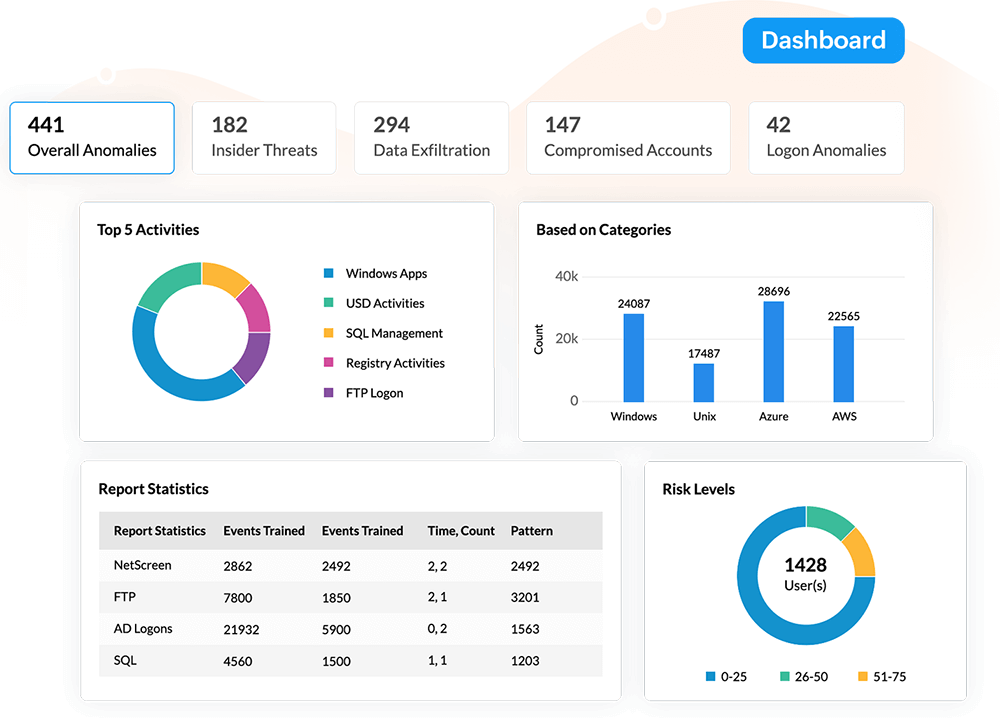
Spot and stop malicious insider threats, compromised accounts, privilege abuse and misuse, unauthorized data
access and exfiltration, and benefit from:
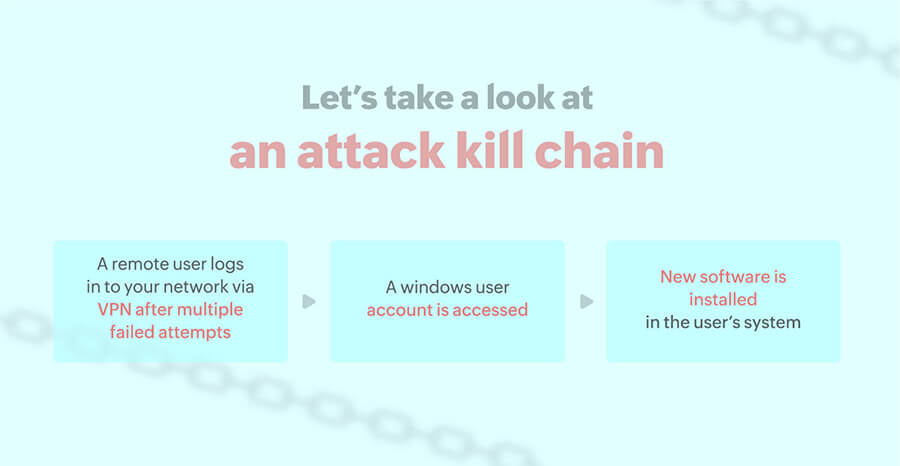
Malware is one of the most persistent cyberthreats in the modern world. As new malware appears, detecting it remains a challenge. Log360 unmasks the presence of malware in the network utilizing its predefined correlation rules. It spots suspicious software or service installations by malicious actors, alerts security admins immediately, and provides detailed incident timelines for investigation. This solution also lets you associate a workflow profile to stop the service or process, facilitating an immediate incident response.
Read the complete use case here.Often, attackers executing advanced and sophisticated attacks are detected when they try to leave your network perimeter with the stolen data. Log360 spots and alerts your security team to data extortion in real time. The solution monitors security events and uncovers techniques such as data exfiltration over alternative protocol (T1048), and unusual data flows in the network. If any of the applications send more traffic than they receive, this will be deemed suspicious, and an alert will be triggered to warn the security team of a possible security threat.
Read the complete use case here.Leverage machine learning to spot malicious insiders It is more difficult to spot insider attacks as they are carried out with legitimate access. Log360's UEBA component ingests log data of the users over a period of time and profiles all of their behaviors. When a chain of suspicious behavior, such as odd logon times, unusual access to sensitive data, or multiple file downloads is detected, the user's risk score for insider threat increases and the security team is alerted. Log360 also provides detailed event timelines for further investigation.
Explore these interactive graphics to see how risk scores add up during threats.