The days when employees and assets functioned only within the company network are long gone. Now, all that is required is a username and password to utilize the required IT resources from a remote location. The workforce today can accomplish most of their responsibilities from anywhere using mobile devices. The proliferation of remote work and cloud applications has increased productivity, enhanced the ease of use for many applications, and improved scalability through Software as a Service (SaaS) applications. At the same time, it has also increased the risk of shadow, IT, data exfiltration, and insider threats. A cloud access security broker (CASB) can be an effective cloud security tool to defend against shadow IT and data exfiltration.
What is shadow IT?
Research suggests that an average employee uses 10 SaaS applications everyday, and an average organization uses as many as 254 applications. These applications could be third-party analytics tools that ingest customer data sets, or consumer versions of approved enterprise apps like Microsoft 365 or Google Workspace, for example. The list goes on. However, not all of these applications are sanctioned or approved by the IT department. This phenomenon is known as shadow IT, where employees use unauthorized software or services without the knowledge or approval of the IT department. While shadow IT can sometimes provide solutions to specific business needs quickly and efficiently, it can also pose significant risks to organizations. These risks include data security breaches, compliance violations, integration challenges, and increased IT costs due to duplication of software and services.
What is data exfiltration?
Data exfiltration into the cloud refers to the unauthorized transfer of sensitive or confidential data from an organization's internal systems to cloud-based services or platforms. This can occur when individuals within the organization intentionally or unintentionally upload or store sensitive data on cloud services that are not approved or secured by the organization.
The risks associated with data exfiltration into the cloud include potential data breaches, loss of intellectual property, compliance violations, and reputational damage. To mitigate these risks, organizations should implement robust security measures such as encryption, access controls, data loss prevention (DLP) policies, and continuous monitoring of cloud environments to detect and prevent unauthorized data transfers.
On-demand webinar: How to stop malicious data exfiltration into the cloud with CASB
Implementing CASB: Benefits and deployment modes
A CASB, according to Gartner, is a cloud-hosted or on-premises software or hardware that functions as an intermediary policy enforcement point between enterprise assets (both on and off the company network) and cloud-based applications. With CASB, you can:
- Gain visibility into all the cloud applications used.
- Introduce policies to sanction or block shadow applications with the help of reputation scores.
- Prevent data exfiltration into third-party cloud apps.
- Become aware of user activity in the cloud.
Let's take a look at the ways of implementing CASB. The three deployment modes of CASB are forward proxy, reverse proxy, and API scanning.
Forward proxy
Forward proxy routes all managed asset traffic through a CASB at the organization's perimeter, enabling control over application access, real-time deep packet inspection (DPI), and data loss prevention (DLP) during uploads.
Reverse proxy
Reverse proxy involves cloud applications redirecting user requests to the CASB for identity validation via SAML, offering real-time monitoring and control over unmanaged devices, but only for approved applications
API scanning
API scanning directly connects the CASB to cloud applications to scan and quarantine data at rest, effectively safeguarding data stored across multiple sanctioned applications, albeit without application access control or real-time protection of data during transit.
Real-life forward proxy CASB use cases
1) Shortly before leaving his job, an engineer, who worked for a United States Navy contractor, transferred over 5,000 files to his Dropbox cloud and emailed a few of the documents to himself. These documents contained sensitive information about company finances and intellectual property pertaining to product designs.
The Dropbox Upload Requests report in Log360 helps administrators closely monitor file uploads to dropbox.com domain. The report provides contextual information such as time of request, user details, file name, file size, and file type. Uploads of sensitive documents, financial data, intellectual property, PII, and huge volume of uploads from a particular user can be identified and mitigated.
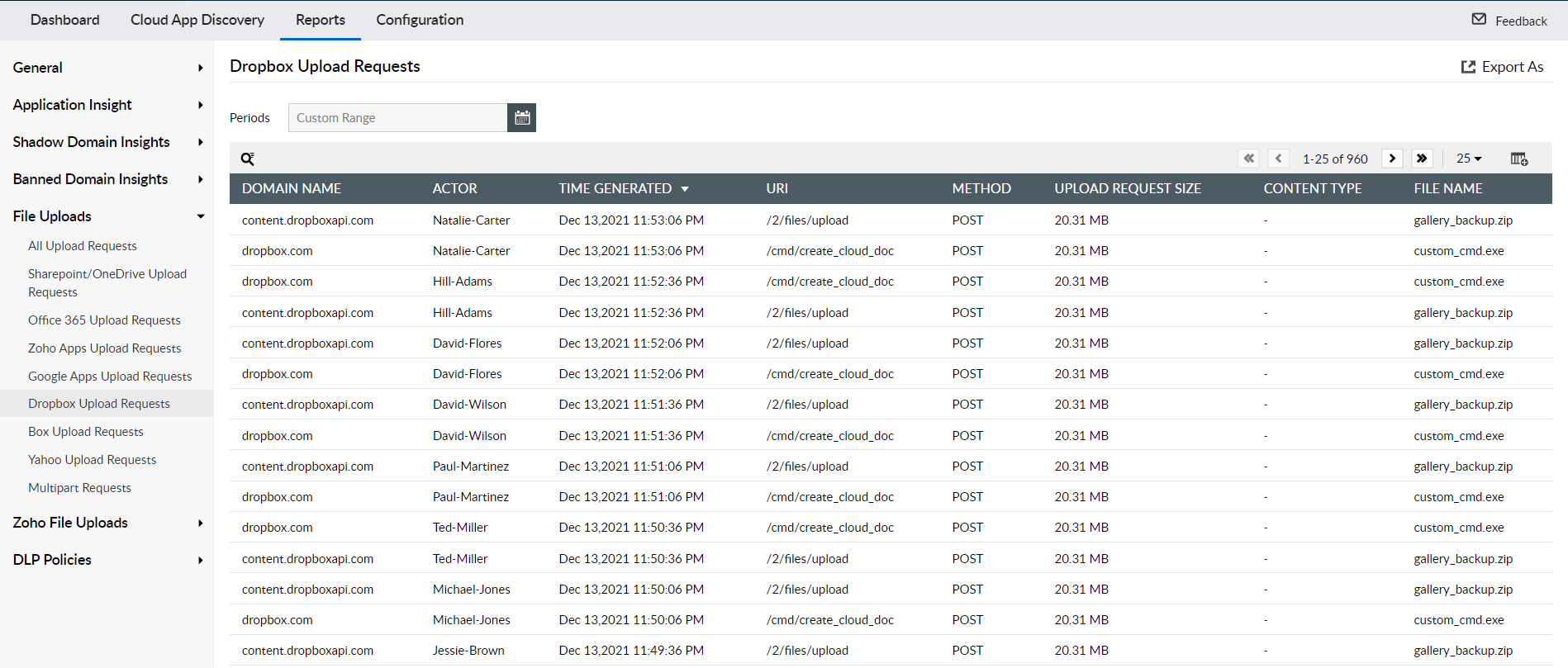
Figure 1: Dropbox Upload Requests report in Log360
2) Pfizer is suing a former employee to prevent the sharing of confidential data stolen while the individual was still employed by the firm. The 12,000 stolen documents include knowledge about the development of a COVID-19 medication. The data was uploaded to multiple personal cloud storage accounts.
CASB in Log360 allows administrators to configure policies to block access to cloud storage accounts. The image below shows how you can configure policies in Log360 to block all storage services other than M365. This will help administrators ensure that users have upload and download access only to sanctioned/official cloud accounts.
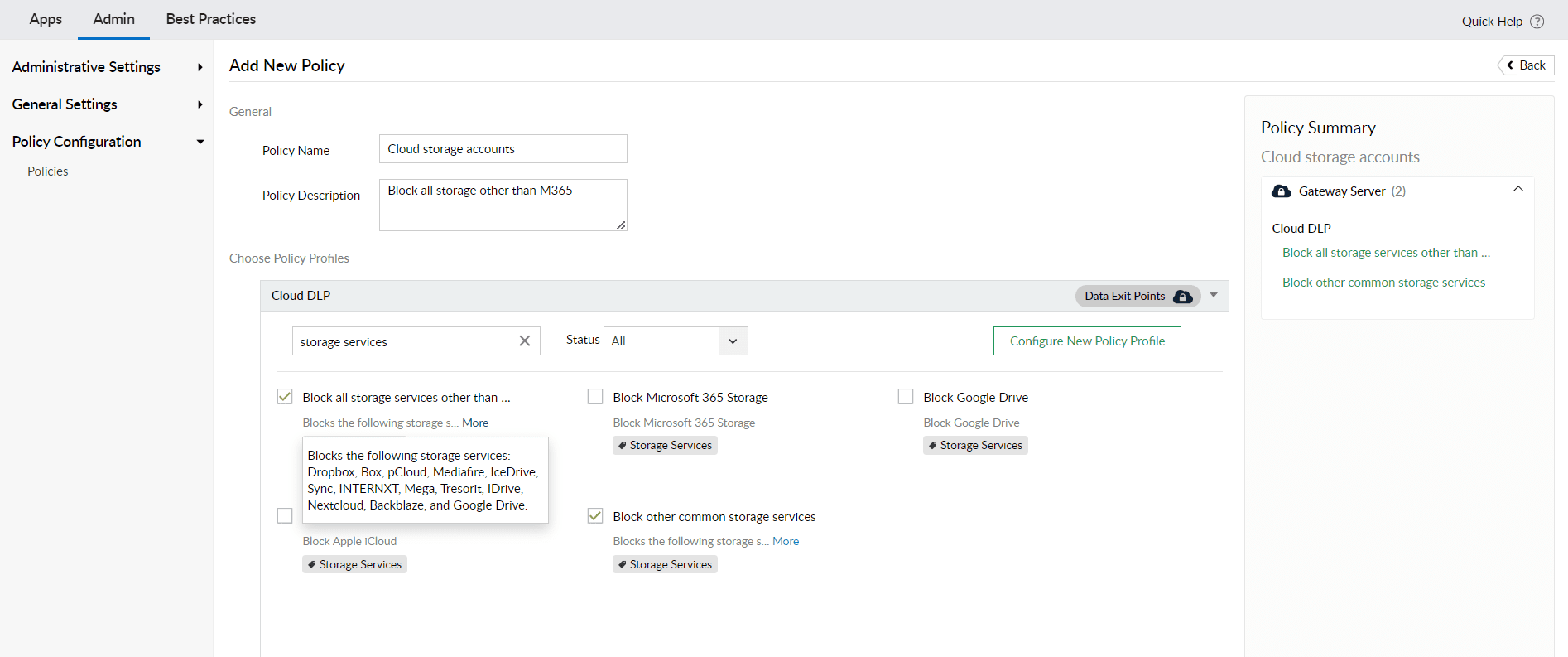
Figure 2: Data loss prevention(DLP) policy configuration in Log360
3)Microsoft was identified as one of the top impersonated brands with 30,621 distinct phishing URLs, according to Vade Secure, a global cybersecurity company. Employees who use Microsoft cloud apps are at risk of credential theft or data loss due to HTTPS spoofing that impersonates legitimate Microsoft applications.
With the All Requests report in Log360, administrators can view all user traffic to web applications including the domain, app category, app reputation, and the URL. This provides deeper insights to identify potential threats, investigate further, and enforce policies.
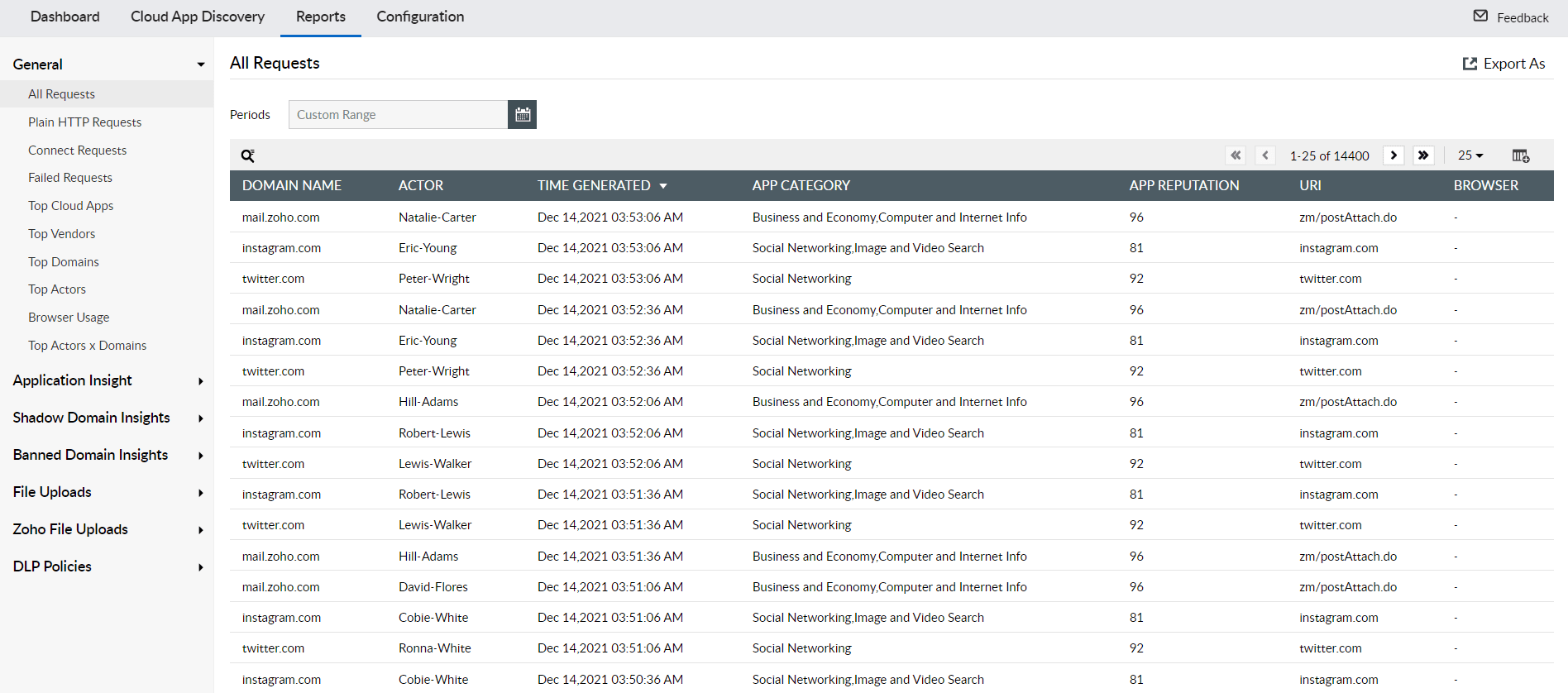
Figure 3: All Requests report in Log360 lists all requests to cloud applications with the domain, URL, App reputation, and user.
A forward proxy CASB can mitigate the risks described earlier by monitoring all traffic from your on-prem network to cloud services. Forward proxy CASB works best for discovering shadow applications and attempts of data exfiltration to any cloud application be it sanctioned, unsanctioned but safe, or unsanctioned and unsafe applications.
The integrated CASB capability of ManageEngine Log360, a comprehensive SIEM solution, discovers shadow applications, checks the application's reputation, and monitors file uploads. With DPI, you get better security context about the file that is being uploaded.
Deploying a stringent network policy that binarily blocks or allows applications might be easy, but it hinders productivity and is not employee-friendly. Given that cloud applications are here to stay, a CASB may be the best cloud security tool concerning shadow IT and data exfiltration.
Want expert guidance in CASB deployment, configuration, and use cases implementation? Sign up for a personalized demo of Log360 with our product experts here.



