Security teams are overwhelmed by a flood of alerts every day. According to Gartner, 57% of organizations say their SOCs struggle with aggregating and correlating security data effectively, which slows down timely threat detection and response. In the face of alert fatigue and data overload, modern security operations centers (SOCs) need more than visibility—they need contextual intelligence.
Powered by Zoho’sZia, Log360—a unified security information and event management (SIEM) platform—uses generative AI (GenAI) to transform security events into concise insights that highlight the who, what, when, and how, so analysts can focus on what matters. By bringing together the root cause, key entities, and remediation steps in one view, Zia Insights eliminates the need to piece together fragmented data, thereby accelerating threat understanding and response.
To accelerate log analysis and improve response in SIEM, Zia Insights provides contextual insights based on each log's type and behavior patterns. When users invoke Zia Insights, logs are interpreted as error logs, security logs, audit logs, or crash logs, enabling the delivery of targeted recommendations and remediation steps aligned with the nature of the log.
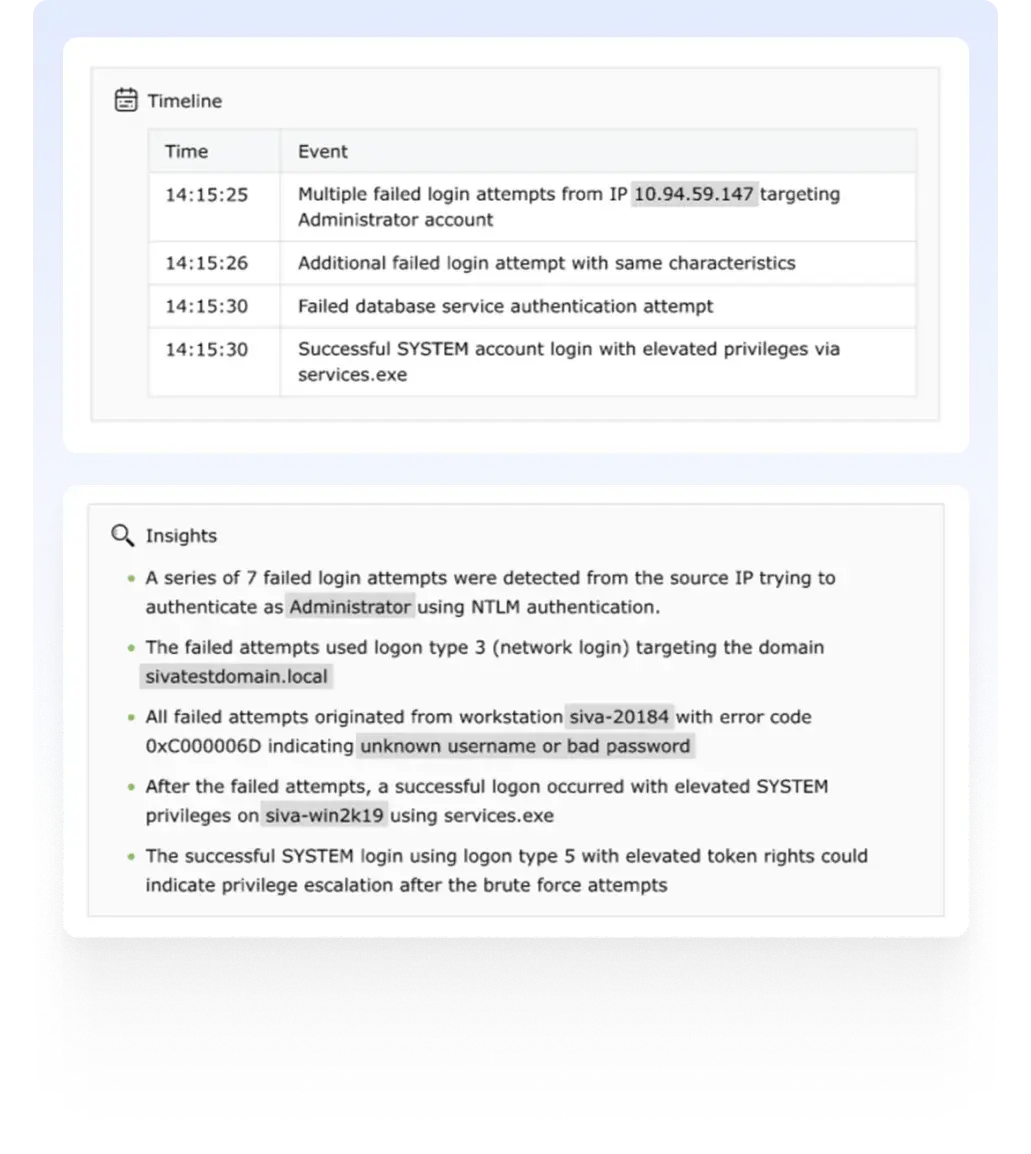
Zia doesn't just summarize logs; it understands them. It evaluates detection patterns, event sequences, system activity, and user behavior to provide a contextual breakdown of each detected event. Key entities involved—such as usernames, IP addresses, endpoints, applications, and event sources—are highlighted and connected to a narrative that explains how the event unfolded.
For example, a brute-force login attempt summary might include:
This helps analysts assess risk levels and act with confidence.
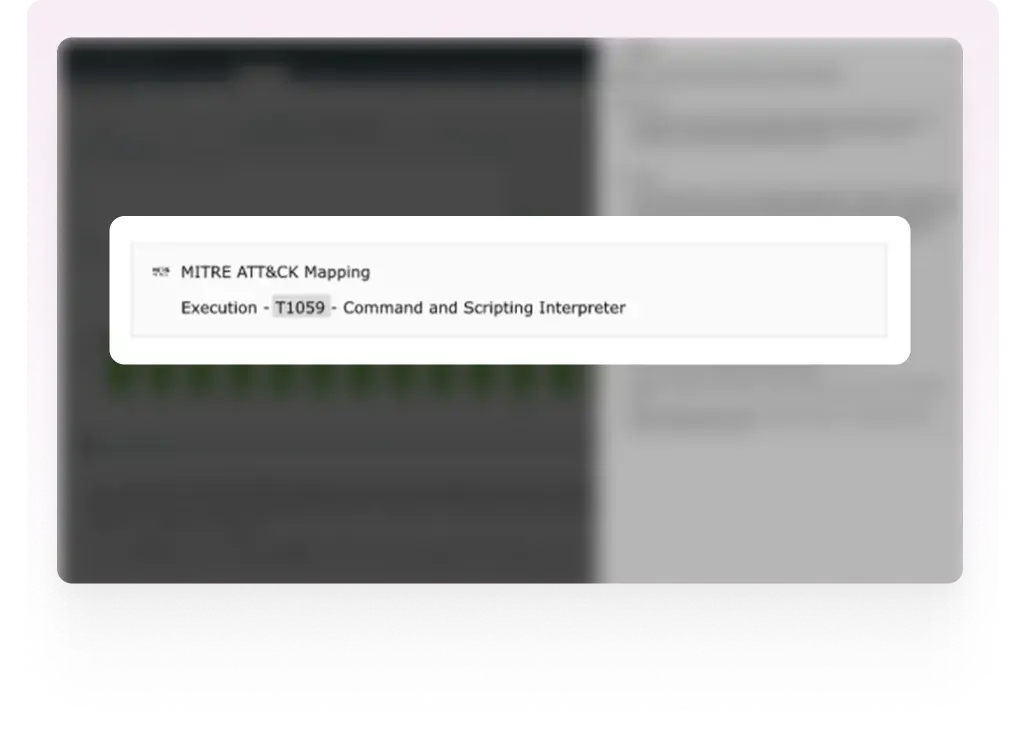
Zia Insights leverages the threat modelling framework MITRE ATT&CK® to map observed behavior to known Tactics, Techniques, and Procedures (TTPs).
Each relevant event will be mapped to a:
This mapping enhances incident triage and helps align investigation efforts with a globally recognized threat taxonomy.
Zia Insight's Summary doesn’t stop at surfacing anomalies; it goes a step further by offering context-aware mitigation and remediation suggestions, tailored to the nature of the log data. Whether you're reviewing a failed login attempt or investigating a crash error, Zia Insights provides practical and relevant next steps to help you respond with confidence.
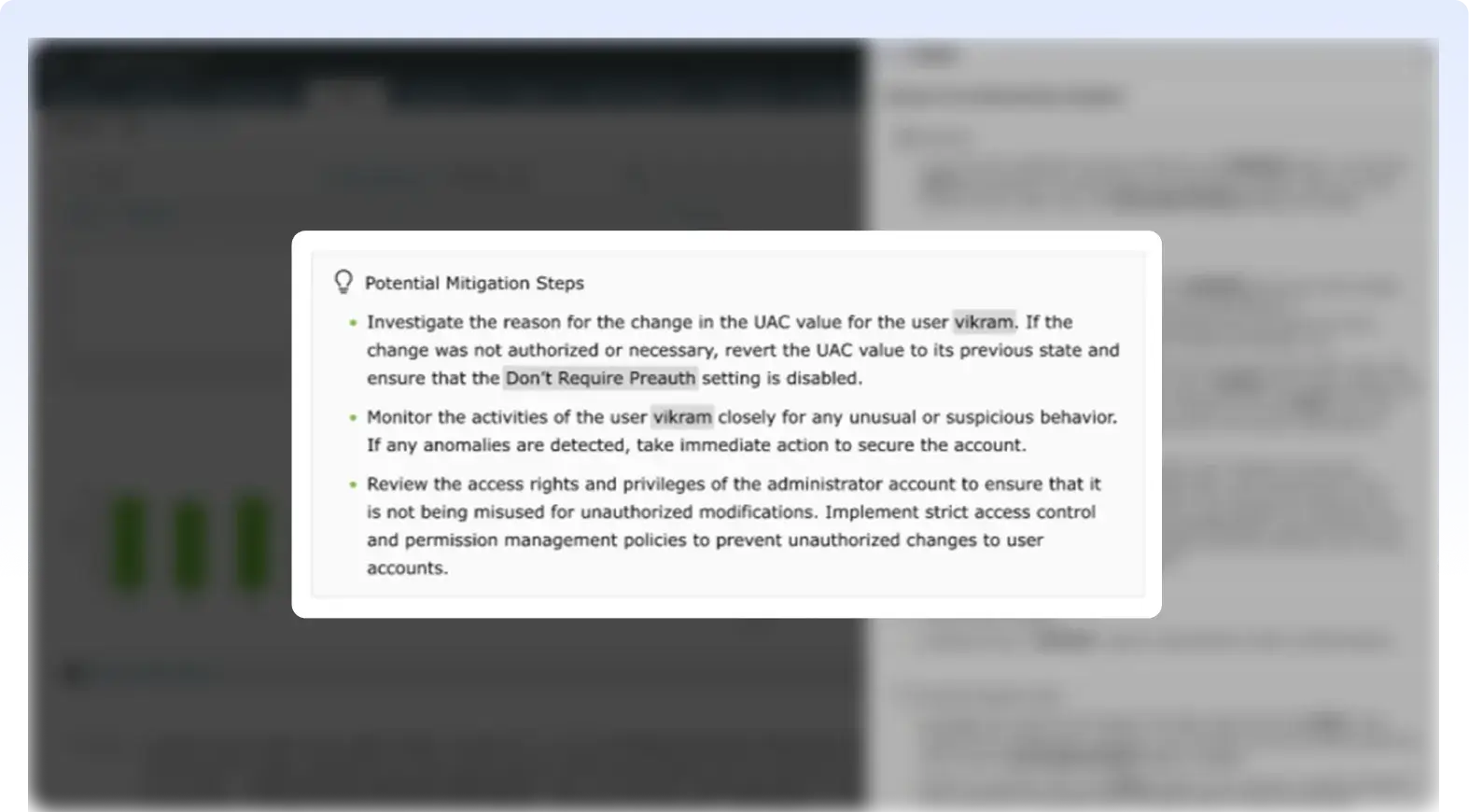
Zia Insights delivers remediation guidance tailored to the nature of each log, whether it's an error, crash, audit, security, or anomaly event. By interpreting the context and identifying relevant indicators, Zia Insights provides targeted recommendations that help contain incidents, troubleshoot issues, and ensure compliance. This focused guidance reduces guesswork and accelerates response across a wide range of log scenarios.
For behavioral anomalies like off-hours logons or access from unrecognized IPs, Zia Insights provides investigation-first guidance that mimics a SOC analyst’s thinking:
Suspicious behaviors—such as unauthorized UAC modifications or triggered security alerts—trigger potential mitigation steps, like verifying the legitimacy of the change and rolling back unauthorized actions.
If Zia Insights detects policy violations or unauthorized access changes, it provides compliance-oriented actions, such as reinforcing access controls or enabling real-time alerts for sensitive audit events.
Zia Insights is built on a Bring Your Own Key (BYOK) model using Azure OpenAI, allowing organizations to retain full control over their data and model usage. Once you configure your own Azure OpenAI key, Zia can securely generate insights tailored to your log data, ensuring compliance and privacy without compromising on analytical depth.
Security teams are buried under a mountain of alerts, logs, and fragmented context. Zia Insights helps you cut through the noise, so you can stop searching and start understanding.
Whether you're chasing down a suspicious login, unusual system behavior, or a complex incident, Zia Insights provides immediate answers to your most critical questions:
Zia Insights enhances every stage of the security analysis lifecycle. By processing alerts, audit trails, and incidents, Zia Insights delivers actionable insights, surfaces key risks, and enriches events with contextual information. It also automatically maps relevant MITRE ATT&CK® techniques, suggests potential mitigation steps, and offers troubleshooting guidance, so your SOCs can take decisive action, faster.
This section provides a side-by-side comparison of Log360's AI-driven SIEM features (Zia Insights)
with similar offerings from leading SIEM solutions.
| Feature | Log360 | Splunk Enterprise | Exabeam | QRadar | SentinelOne |
|---|---|---|---|---|---|
| AI-powered summaries | |||||
| MITRE ATT&CK® technique mapping | |||||
| Mitigation/ remediation guidance | |||||
| Customizable with Azure OpenAI |
Zia Insights helps you accelerate investigations by summarizing key details from logs, alerts, and incidents including involved entities (users, IPs, devices), event sequences, detection patterns, and relevant MITRE ATT&CK® techniques. It highlights anomalies and offers remediation guidance, giving your SOC team the context they need to investigate threats and respond smarter.
Zia Insights leverages Azure OpenAI through a BYOK approach, allowing you to configure your own key. This ensures that while you benefit from powerful AI-driven analysis, your data remains secure and under your control.
Yes. More than 120 million users trust Zoho, ManageEngine's parent company. We have a strong privacy policy and security infrastructure.
Sign up for a 15-day free trial or access our cloud-based SIEM and configure Zia Insights to get actionable insights.
Start using Zia Insights in Log360 and empower your SOC team with intelligent summaries, timelines, and mitigation guidance.
Sign up