Integrate, automate, and streamline security operations with Log360
To protect an organization's IT infrastructure from security threats, organizations have many security tools in place. It is important to integrate these security tools to manage them effectively and increase the efficiency of security operations. Security orchestration refers to the integration of disparate security tools and systems to enhance automation of tasks, accelerate incident response, and boost the efficiency of an organization's security team.
By centralizing security-related data from various sources, security orchestration helps the security team by providing context that helps them make informed decisions and respond to threats quickly. It helps increase your SOC team's productivity by automating manual, repetitive tasks.
By collecting logs from multiple sources across your organization network, ManageEngine Log360 can help you analyze and gain in-depth insights into various security-related events, and detect and manage security incidents quickly and effectively.
Monitor network activitiesfrom a single interface
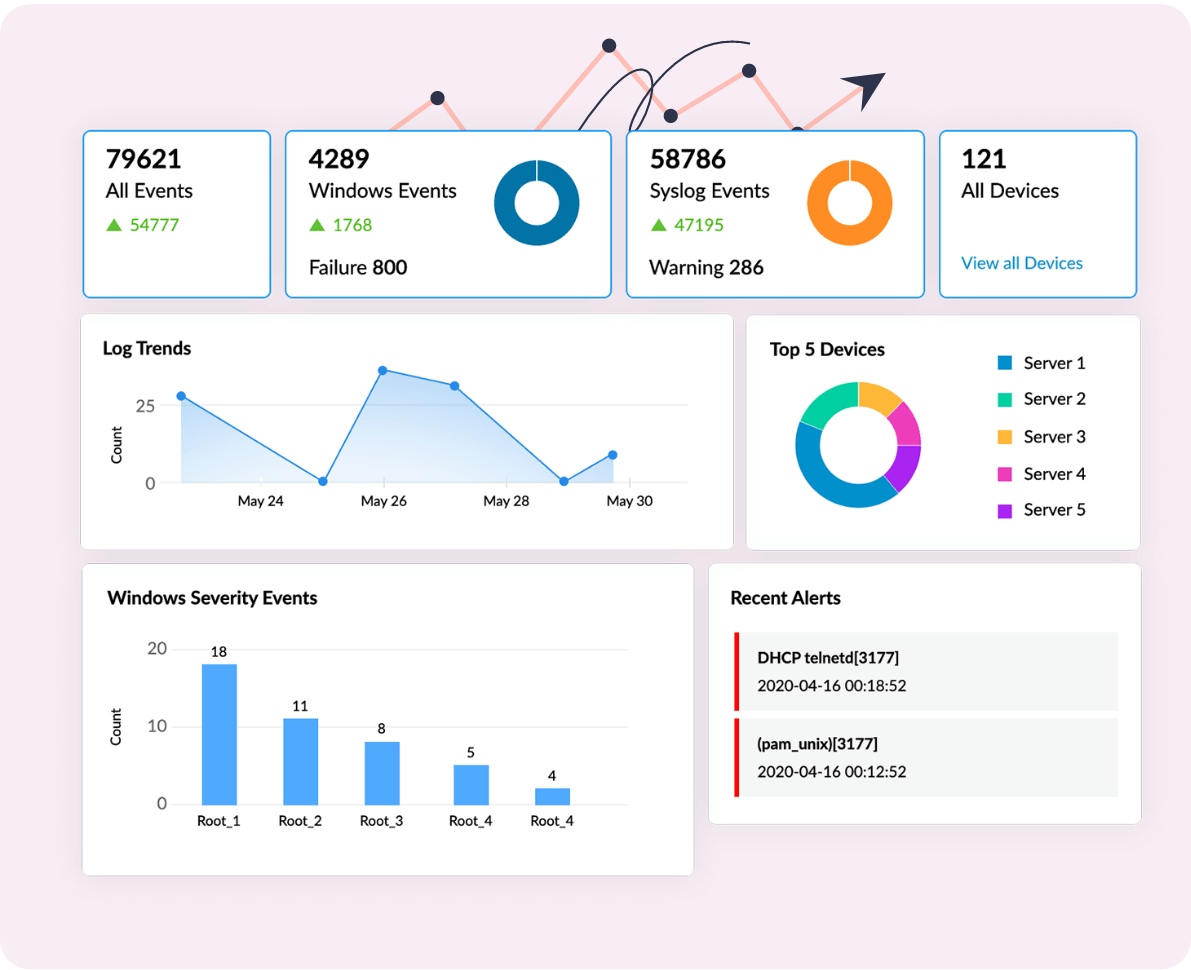
Log360's interactive dashboard widgets help you visualize critical network events in a specified time frame. Monitor and analyze log trends, recent alerts, websites accessed by users, allowed and denied connections, detected threats, identified vulnerabilities, and more.
Comprehensiveanalytical reports
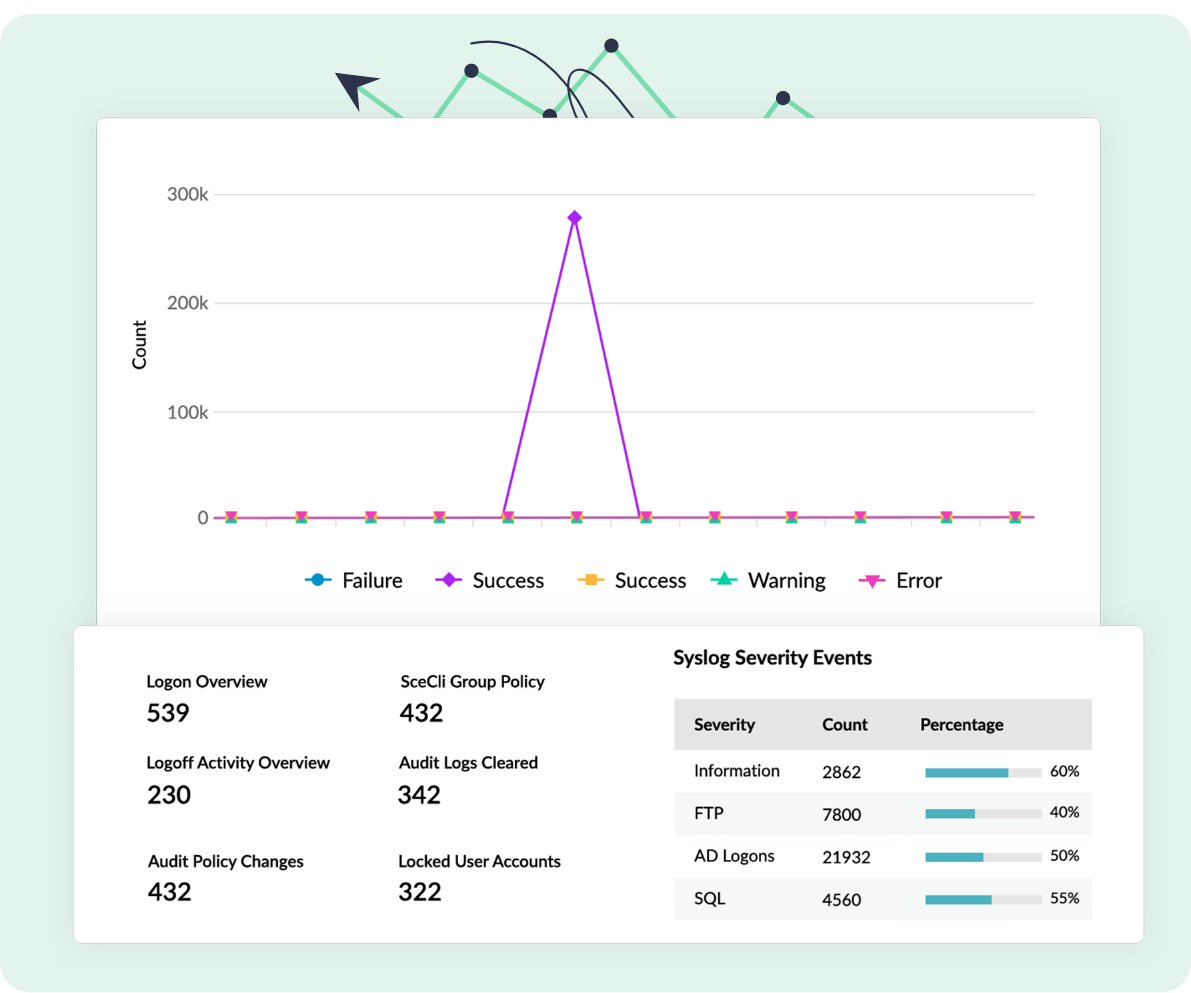
Analyze key network activities and meet compliance requirements with Log360's predefined, graphical reports that are generated and updated when logs are collected. Along with over 1,000 built-in report templates, Log360 lets you customize and create new reports to suit your requirements.
Get alerted inreal time
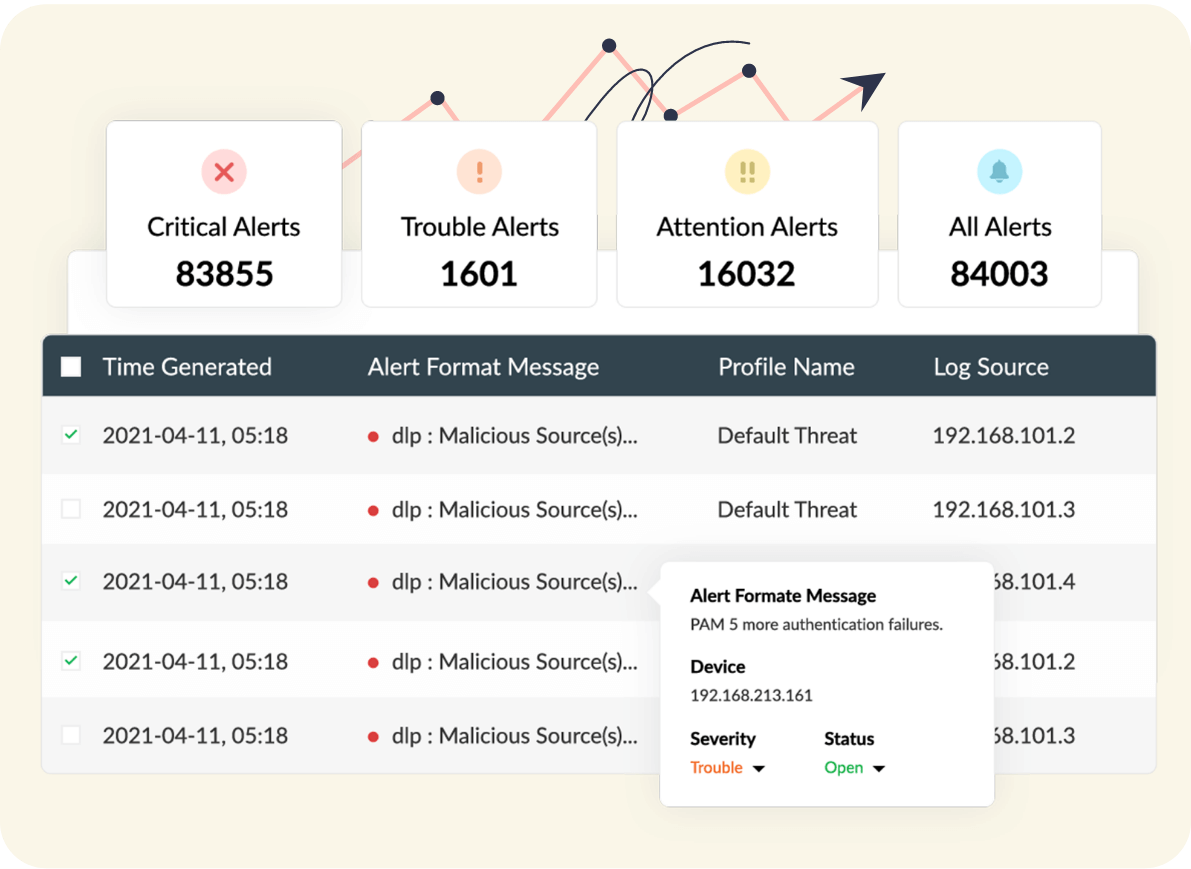
Bundled with over 1,000 predefined alert criteria covering a variety of security use cases, Log360 alerts you immediately when any security threat is detected in your organization network. Apart from alerting you, Log360 gives you in-depth information regarding the threat and lets you prioritize and address detected threats based on the severity of the alert: Attention, Trouble, and Critical.
Instant responses withautomated workflows
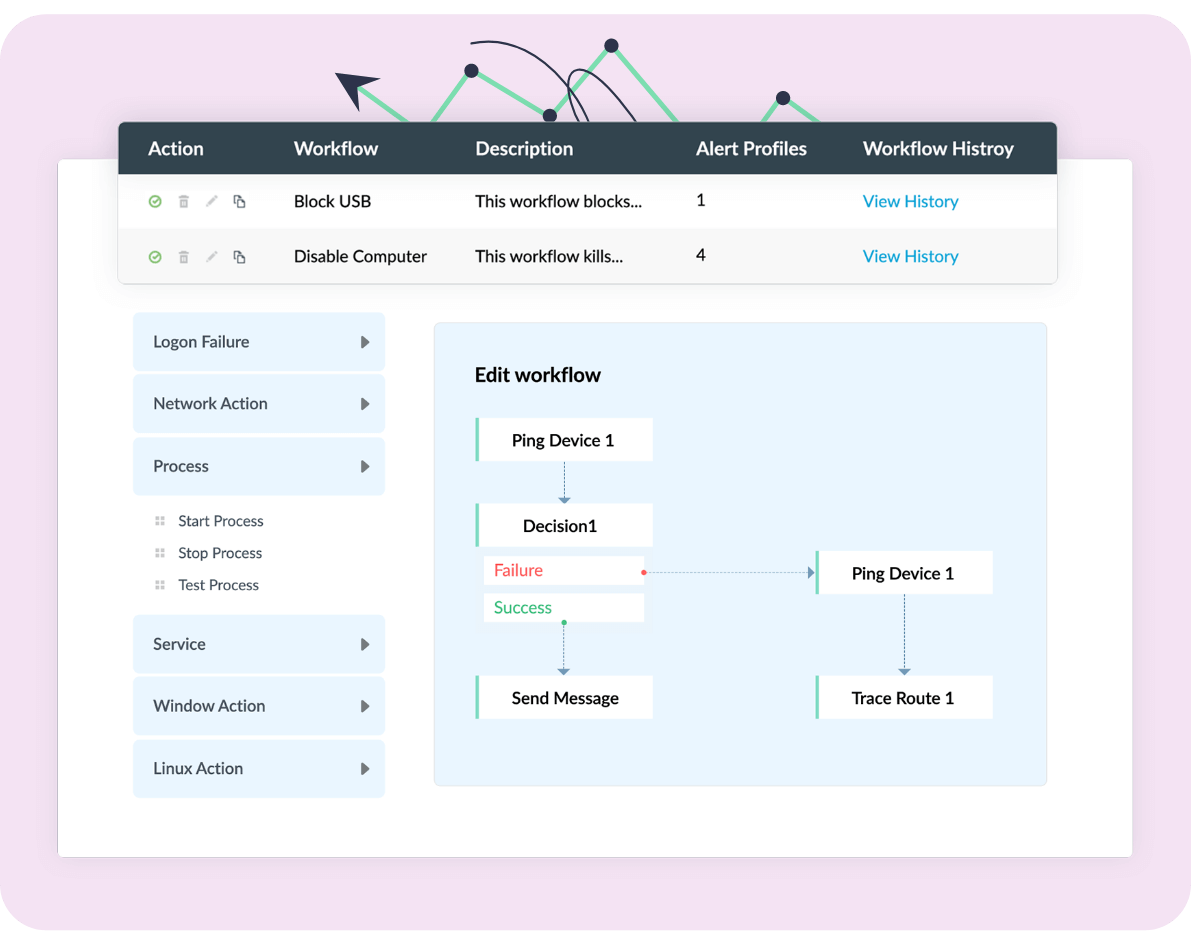
Respond to security incidents immediately with Log360's automated incident response workflows. With Log360's intuitive drag-and-drop workflow builder, you can customize response workflows as per your organization's requirements.
Why choose Log360 for
security orchestration
-
Built-in ticketing console
With Log360's built-in ticketing system, you can manage any security incident by raising tickets and assigning them to the appropriate security administrator as soon as an alert is triggered.
-
Threat intelligence
With Log360, you can integrate with open-source and commercial threat feeds to accurately detect malicious sources interacting with your organization network.
-
Integration with external ITSM tools
You can also integrate Log360 with other help desk software such as ManageEngine ServiceDesk Plus, Jira Service Desk, BMC Remedy Service Desk, Kayako, Zendesk, and ServiceNow to assign tickets and resolve security incidents.
-
Integration with Endpoint Management Solutions
You can integrate Log360 with endpoint management solutions such as ManageEngine Endpoint Central to get better visibility, quicker alerts, and automated incident responses in case of malicious endpoint activities Learn more.


