Network user reports
Your organization needs continuous access to information so that performance review and decision-making can be improved. Network reports in Network Configuration Manager serve this purpose by presenting comprehensive data about the ins and outs of your network. They attend to various levels of function and activity within your network, helping you understand where the faults are and what needs to be optimized for better performance.
Whenever network downtime occurs, admins typically look for a configuration change implemented by a user that may have caused it. In cases like this, network report would present the full picture of all the users that were present on the network that day along with what changes were made and when. Moreover, an admin should be able to track users over the network and detect unauthorized access or configuration changes. In the absence of reports, such tasks become tedious, if not impossible.
Within Network User Reports, Network Configuration Manager offers a range of specific reports, including:
All these reports present a quick summary of the network at the user level.
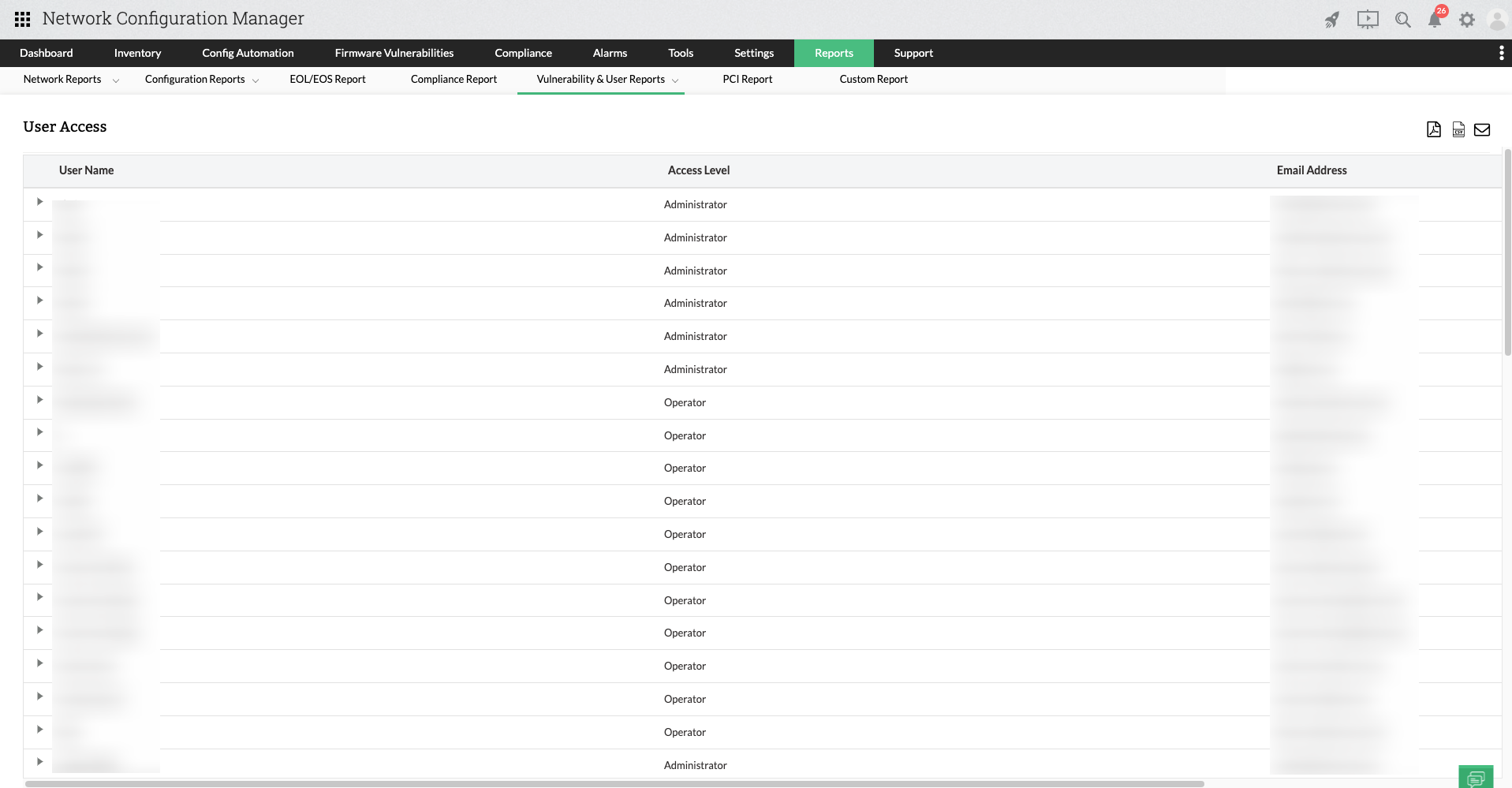
User Access Report
Network user access report conveys the full list of users that have access to your network. The report will show the username, access level, and email of each user. When clicking on a user, you can drill down to reveal more details, including host name, IP address, and device accessed. Click User Access Report in the Reports tab to access and generate the report.
To access this report, navigate to Reports -> Locate and click User Access Report within the Vulnerability & User Reports section.
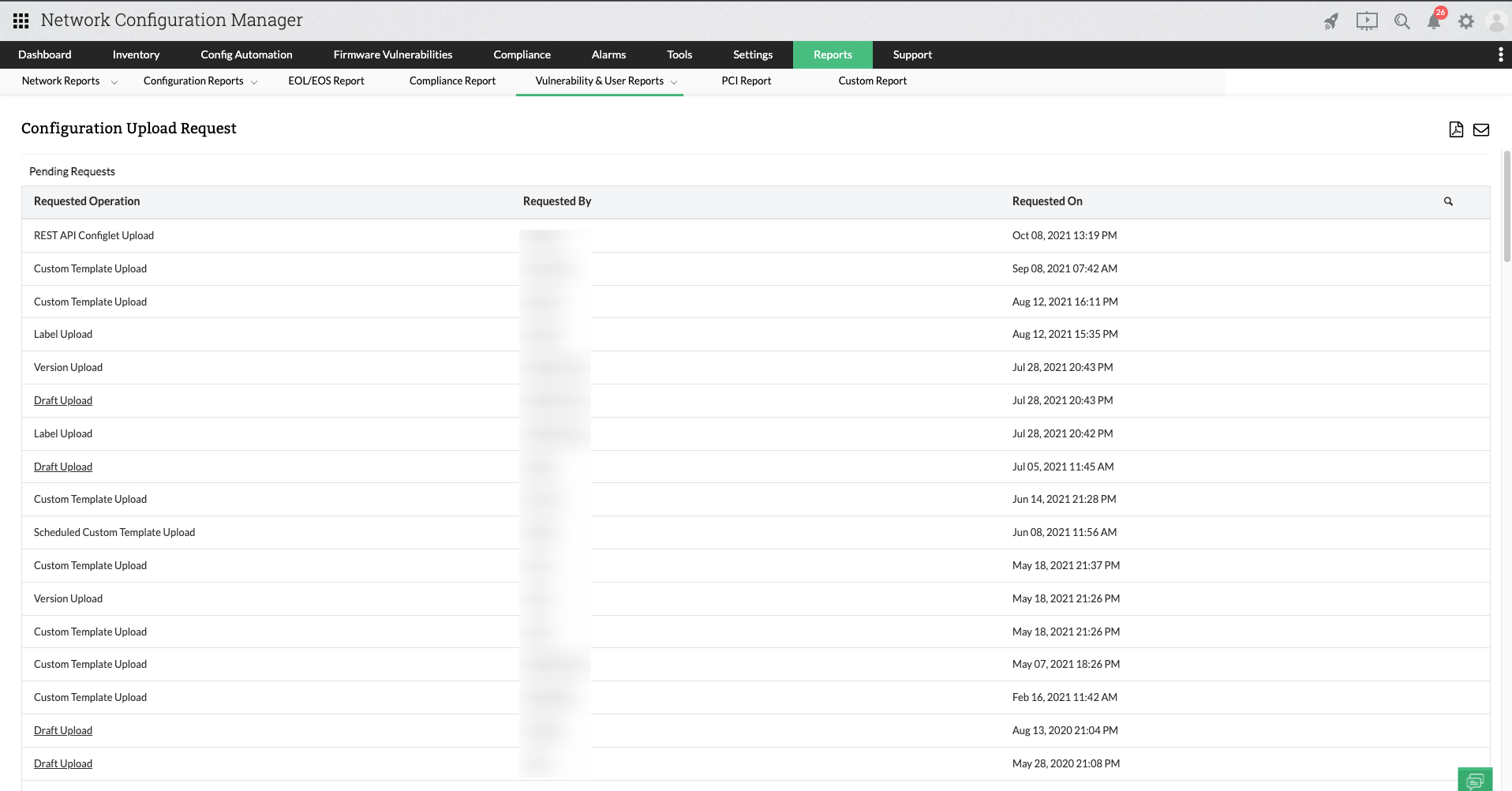
Configuration Upload Request Report
Users with access to your network devices can make configuration change requests. These requests go to the admin and only after approval will the configuration change be executed. Configuration upload request reports, under network user reports, give you an overview of the status of such requests. The report will have distinct tables showing pending, approved, and rejected requests. You can get the report by clicking Configuration Upload Request Report in the Reports tab.
To access this report, navigate to Reports -> Locate and click Configuration Upload Request Report within the Vulnerability & User Reports section.
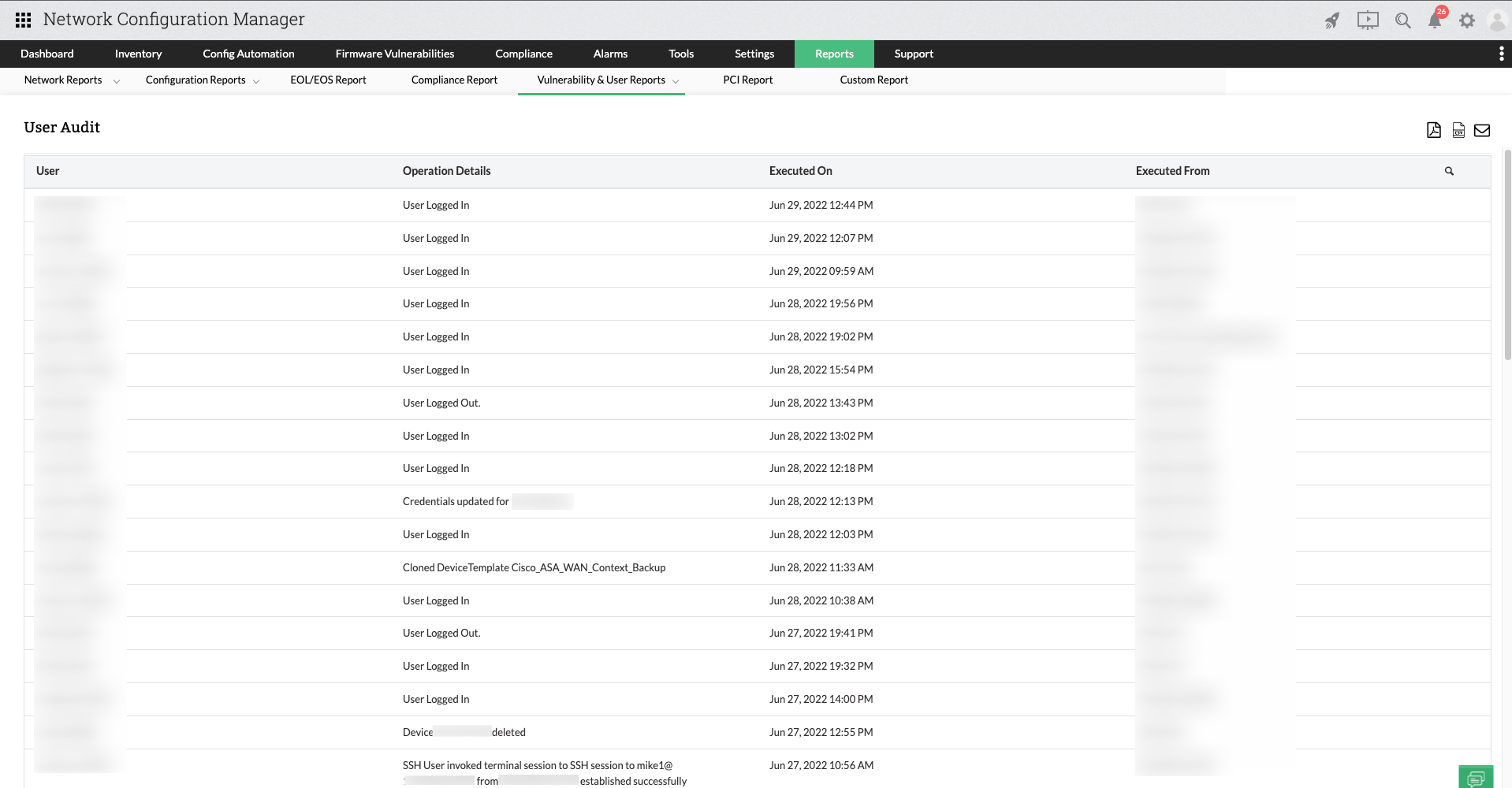
User Audit Report
User audit reports, under network user reports, present a detailed summary of user operations, listing what type of operation was executed along with the time and source (IP address). This enables an IT admin to understand the who, what, and when of user operations in a network. You can get this report by clicking User Audit in the Reports tab.
To access this report, navigate to Reports -> Locate and click User Audit Report within the Vulnerability & User Reports section.
Download Network Configuration Manager now and enjoy these and various other kinds of reports and audits with a free, 30-day trail.
Want to see the solution in action? Request a free, personalized demo.
You can also get a price quote based on your usage and needs.