Critical IT policies that safeguard
your organization
7 mins read

Is your account secure? A quick glance at ManageEngine's security page will reveal an IT policy, which talks about our data security, identity and access control, and other vital components of our products and services. This policy has been fine-tuned over decades and has kept us safe from potential threats.
An IT policy is the cornerstone of cybersecurity and drafting a rock-solid one is crucial to our enterprise. We have to balance the need to safeguard the organization while ensuring there are no setbacks for people in doing their jobs.
The entire process involves months of research, input and collaboration of multiple departments, and a rigid approval process before it is finalized and implemented. In this article, we will provide a deep dive and offer insights into six IT policies for any enterprise.
1. IT acceptable use policy
An acceptable use policy provides a framework or standard governing the use of all IT resources provided by the company. It covers general use and ownership, security and proprietary information, unacceptable use of system and network activities, email and communication activities, and compliance. The purpose of this policy is to protect the organization from actions that may compromise its security or services. It also details how the policy will be executed and any legal consequences that violators may face. As far as IT policies are concerned, this one should be at the top of your list.
Stakeholders: All employees including but not limited to consultants, freelancers, contract employees including independent contractors employed by a company and its subsidiaries, interns, trainees etc.
Decision-makers: Legal, HR, and IT teams, as well as executive leadership, hold primary responsibility for creating this policy. It is a best practice to consult other stakeholders such as the risk management team, compliance team, union leaders, or any external advisors at the time of drafting.
Let's say an employee downloaded the bootlegged version of a popular video game on their company-issued device. This would be a violation of the acceptable use policy. As a decision-maker, you should be prepared and have a protocol in place to take appropriate action. Here's what an organization could do:
- Investigate: The IT team can conduct a preliminary investigation to gauge the severity of the offense. It is crucial to gather evidence at this stage to understand whether there's any malware in the system. Consult with the legal team to determine if there are any legal complications.
- Revoke: Temporarily suspend the employee's access to certain privileges
to prevent unauthorized activity. In this case, the employee's access to the organization CRM was revoked. - Notify: Issue a notification to the employee's supervisor/manager, the IT security team, and any other decision-makers who should be involved.
- Examine: Conduct a secondary investigation with the employee in the presence of HR to understand the intention of their actions. In this case, the employee admitted that they didn't realize that it was a bootlegged version since the source website mirrored the original. As this employee was a non-techie, they didn't understand the technical jargon used during the download, assuming it was a standard notification.
- Act: Disciplinary actions may be warranted, depending on the severity. Consequences may range from a verbal warning or probation, to termination of employment in extreme cases. Since the employee does not have a history of non-compliance, a verbal warning can be given and they can be advised to attend an awareness session with the IT team.
- Educate: The IT team can conduct training sessions on various subjects and make it mandatory for all employees to attend them virtually every year. In this scenario, the employee was asked to attend an in-person awareness session on copyright laws, the acceptable use policy, and the consequences of downloading unauthorized software.
- Review: Stakeholders must review the policy after an incident to determine if it requires any modifications to prevent similar incidents in future.
2. Gadget policy (Device/BYOD policy)
This policy includes procedures and protocols for effective organizational asset management, specifically electronic devices. It covers the end-to-end cycle of assets from acquisition, deployment, usage, maintenance, withdrawal, to disposal. It also covers usage in the instance of BYOD model. These policies are designed to protect individuals and the organization against financial losses associated with damage, loss, or theft of devices.
Stakeholders: Like the acceptable use policy, the gadget policy applies to employees, contractors, consultants, and contract workers employed by a company and its subsidiaries. If your organization works with vendors, they should be included in the policy.
Decision-makers: Legal, finance, HR, and IT teams, as well as executive leadership, hold primary responsibility for creating this policy. A risk management team and compliance team must be involved in the drafting process.
Zoho's wallet-based model
ManageEngine is a division of Zoho, which has opted for a self-service wallet-based store model for IT gadgets for its employees in India, home to a majority of the organization's employees. The wallet assigned to each employee utilizes a notional credit that helps the IT regulate the purchase and distribution of mobile phones, laptops, and accessories.
Employees are categorized based on their role-e.g. marketing, support, development, or design-and are provided with credits each year. The IT team provides a pre-defined list of devices that employees can choose from and sets a lifetime for these devices. For instance, three years for MacBooks used by a UI/UX designer or two years for an iPhone used by the sales team. At the end of the lifetime period, employees can use this credit to get an upgrade. Devices issued by the company are insured for loss and theft. Maintenance is handled by the IT team and replacement is considered on a case-by-case basis. However, any damage caused is fixed by the IT team and the cost incurred is deducted from their wallet credit, inculcating a sense of accountability and responsibility within the user. With this system, monitoring the usage of devices has become a much more streamlined task. It's also easier for employees to adhere to the policy.
3. Social media policy
With an increase of social media use within the workforce, it is vital to lay out clear dos and donts with respect to social media. This policy ensures that any form of communication with an external party or individual through social media is conducted while keeping in line with the ethics, confidentiality, and values of a company.
Stakeholders: All employees including but not limited to consultants, freelancers, and contract employees including independent contractors employed by a company and its subsidiaries, interns, trainees etc.
Decision-makers: Marketing, HR, legal, and IT teams. A risk management team and compliance team can be consulted in the drafting stage.
Social media apps are constantly evolving with new features, but the fundamental practice remains the same. Employees should understand the difference between their personal and professional identities and ensure that any content they put out does not reveal confidential information or disrespect another person's boundaries. For instance, posting about a new product launch before it goes live or posting a picture with your laptop's screen in the background (with customer details) is a violation of this policy and requires immediate action. Like the acceptable use policy, action taken against violators depends on the severity of the situation.
4. Password policy
A set of rules defined to increase cybersecurity, encourage users to create strong passwords, and help an organization manage the use of passwords within the network. The policymakers establish criteria for password strength at the user and organizational level.
Stakeholders: All employees, contractors, and third-party entities who access, manage, or interact with the organization's systems, data, and resources.
Decision-makers: IT team, the legal department, and executive leadership (particularly the CIO) hold primary responsibility for creating this policy. If the organization has a risk management team and compliance team, they must be consulted in the drafting process.
Here's a sample password policy categorized by complexity and management.
Complexity
Parameter |
Sample instruction |
|---|---|
Minimum password length |
Eight characters |
Minimum number of numeric characters |
One |
Minimum number of uppercase characters |
One |
Minimum number of lowercase characters |
One |
Minimum number of special characters |
One |
Management
Parameter |
Sample instruction |
|---|---|
Password reuse |
Do not allow passwords to be reused |
Password expiration |
Expire after six months |
Invalid login attempt |
Never lock any accounts |
Zoho combines the password policy with a Zero Trust principles that ensure passwords serve their ultimate purpose: protect an account from cybersecurity threats.
5. Disaster recover policy
A disaster recovery policy is a protocol to identify the occurrence of a disaster, how to manage a situation without affecting critical operations, a plan of action to recover lost data (if any), time restraints for each incident, and a checklist of all stakeholders that must be notified in such scenarios. A business continuity and disaster recovery (BCDR) policy is similar but encompasses a broader range of activities for overall business continuity, whereas a disaster recovery policy is more focused on the IT infrastructure, data, and operations.
Stakeholders: All employees including but not limited to consultants, freelancers, contract employees including independent contractors employed by a company and its subsidiaries, interns, trainees etc.
Decision-makers: Top-level executives (CXOs), senior IT managers, risk management leads, legal and compliance heads, and the PR team must be involved in this process. If your organization does not have an incident management (IM) team, now would be a good time to set one up. You can find out more about ManageEngine's process in our IM handbook.
Take an example of a data center failure. Obviously, this is an urgent situation that requires an emergency protocol. Here's a sample workflow that can be followed to help organizations return to normalcy:
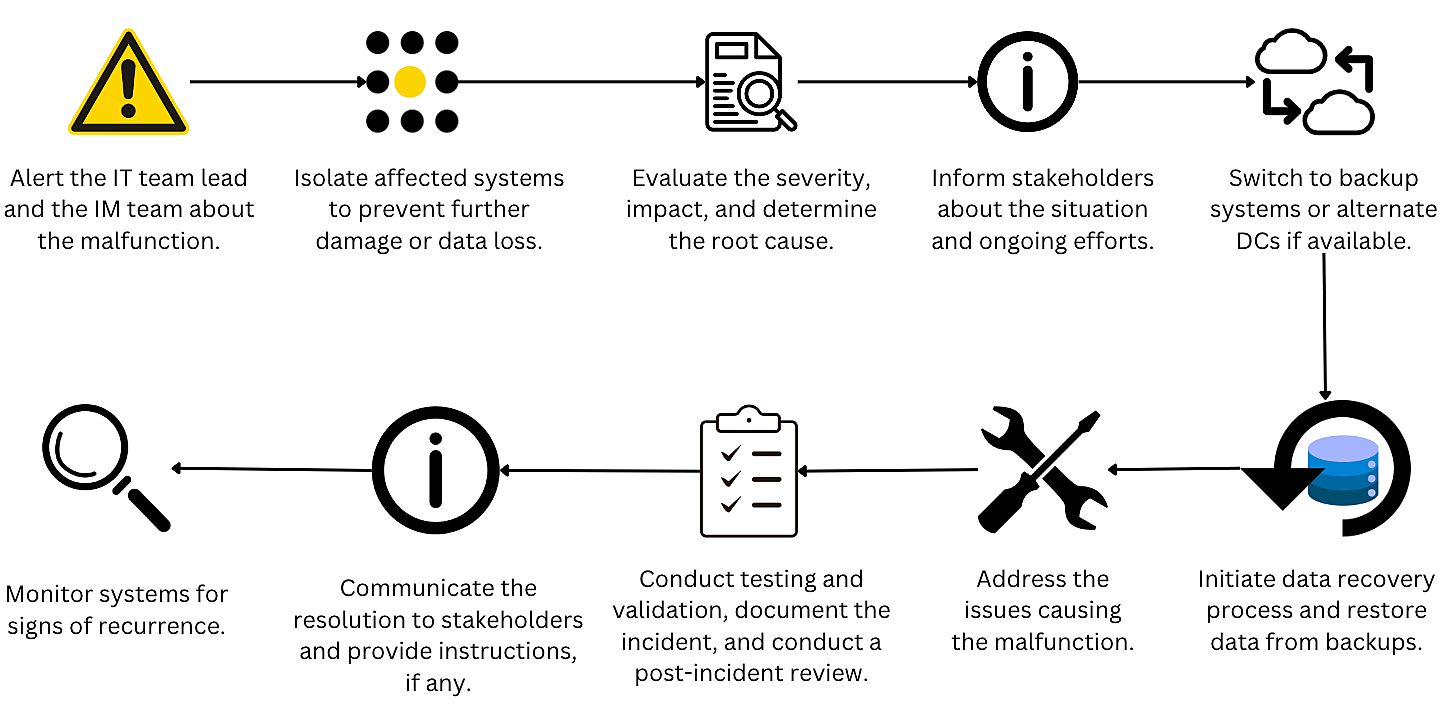
6. Remote access policy
For organizations that follow a hybrid or remote work model, the IT team must come up with guidelines that regulate the use of any endpoints outside the organization premises. It also outlines security protocol for accessing the corporate network via VPN. A remote access policy often contains some overlap with the password and device polices, along with standards and practices for encryption, access control, and logging. The pandemic showed us that work models can shift almost overnight, so it's important to have a policy in place even if you aren't currently operating remotely.
Stakeholders: This policy applies to anyone who has access credentials within an organization, regardless of their current work model.
Decision-makers: CIOs, IT security team, risk management leads, and legal and compliance heads should be involved, whereas other team leads can be consulted to identify any critical roles that require additional resources, like sales teams that travel overseas.
The banking sector comprises a few remote work roles like loan officers or mortgage
specialists. One of their tasks is to meet clients on-site for documentation. In this situation, they would require remote access to the banking system to obtain, verify, and upload client information. To achieve this, the loan officer would have to raise a request for remote access to the IT team, specifying the reason for the request, and the duration of access required. Once it goes through the hierarchy for verification and approval, the IT team configures a VPN on their company-issued device and the officer must gain access through approved authentication methods like MFA.
Wrapping up
The policies an organization would require for day-to-day operations are not restricted to this list. It depends on different factors like the needs of your business, customer data collected, and geographic location. Identify the purpose and scope of each policy and ensure clear communication with decision-makers and stakeholders for effective implementation.
