Chapter 5:
Managing critical endpoints
Detecting phishing attacks
As ManageEngine has grown over the last couple of decades, we've been prone to numerous cybersecurity attacks, like phishing. Phishing is one of the well-known methods to extract critical information from our users. If any endpoint in our IT environment succumbs to a phishing attack, it could result in compromise of our IT environment's security.
Therefore, it becomes critical to protect our endpoints like mobile phones and laptops from phishing attacks. Our AI system detects such fraudulent pages that mimic the original one to get the user's credentials without their knowledge. Since these pages almost resemble the original one except for minute changes, probably in the URL or in the page layout, they often go unnoticed without AI support. Deploying AI in the detection of such phished sites has helped us avoid severe privacy violations, such as account compromises, and stolen credentials.
Our AI system employs techniques, such as URL analysis, and layout analysis, to compare and scrutinize suspicious pages with the original ones. Every attribute of the page is vetted and even the minuscule differences are exposed.
Supporting endpoint management with bots
Our AI system powers an NLP chatbot to help technicians manage endpoints from a central location. Among many other features, the NLP bot supports the technicians by responding to queries related to the IT environment.
Apart from simplifying complex workflows, the bot eliminates repetitive steps by answering queries and performing tasks on behalf of the technician. This frees up the technician's time for more important tasks. Our IT teams utilize this bot by retrieving crucial data, scheduling tasks and performing simple IT operations.
Here are a few scenarios:
- A technician wants to update Microsoft OS versions on a few devices. The technician can request the bot provide an overview of the devices and their operating systems to understand which devices need the update.
- A technician wants to understand the vulnerability of the endpoints in their IT environment. The technician requests the bot provide a summary of the most vulnerable devices in the environment so that they can analyze it further. The technician can use a simple statement like "Show me all highly vulnerable computers" to receive the details. The technician can select all these devices at one time and perform an operation like running a patch to improve the computers' security.
- A technician wants to know how many patches are missing in the network. They can obtain the details from the bot with a simple request.
- A technician can schedule and automate routine events like inventory scans.
Figure 10, below, is a sample of how our AI bots aid technicians in endpoint management:
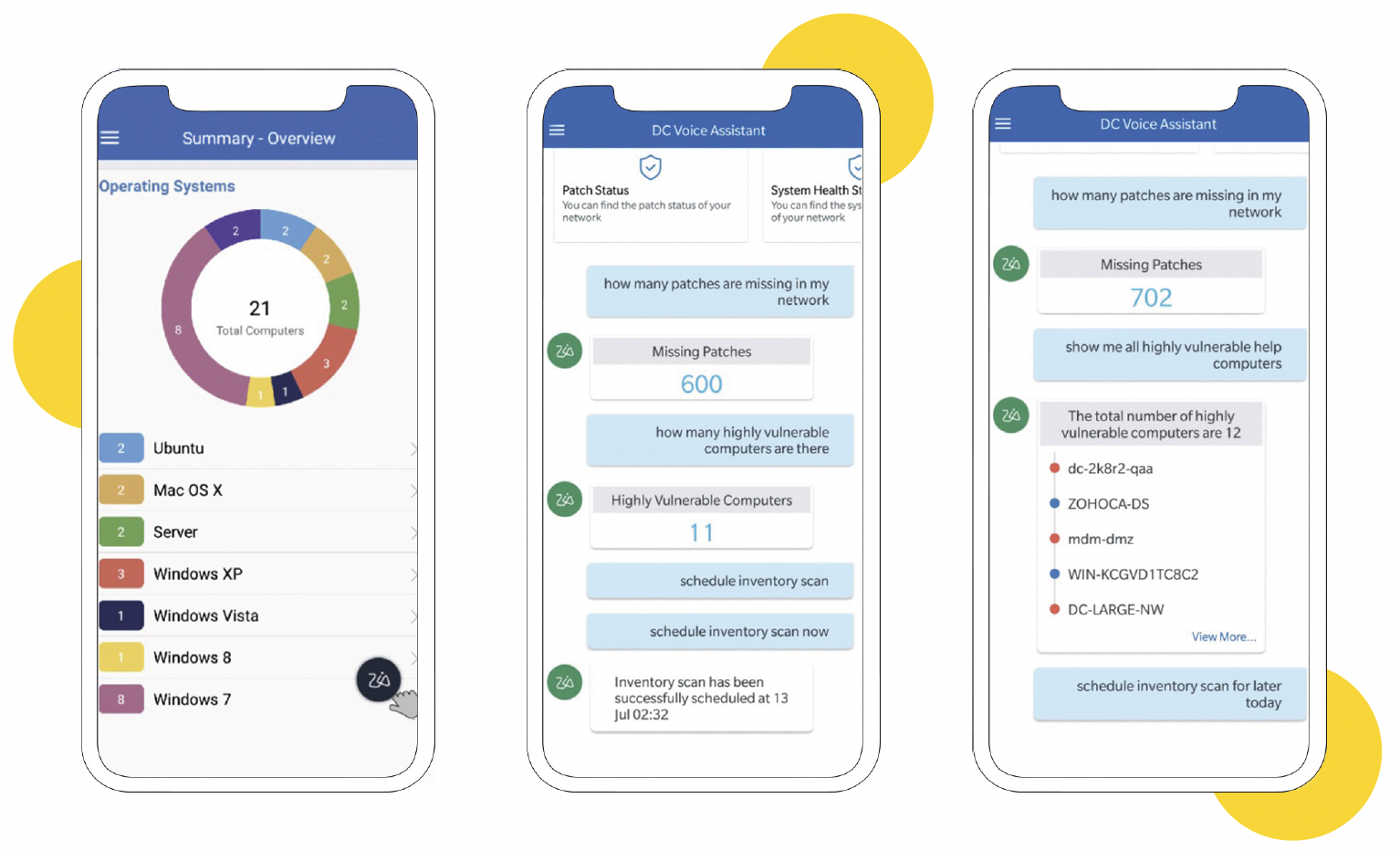
Figure 10: Example screenshots of NLP chatbot communications for endpoint management.
Conclusion
This e-book provides a glimpse of how AIOps can empower an IT organization like ManageEngine to improve its IT processes. Over the years, we have invested our resources in building comprehensive solutions for the most challenging IT problems, and AIOps is another step in the right direction.
Everyday, we seek to improve our processes, and our solutions, by improving our AIOps methods. We hope this book has inspired you to leverage the power of AIOps for your own organization. As we incorporate more powerful technology, introduce better processes, apply finer methods, and craft superior solutions, our AIOps engine will operate faster and more efficiently.
In the future, we'll share with you more advanced methods that we've utilized, and will invite you to try them out as well.