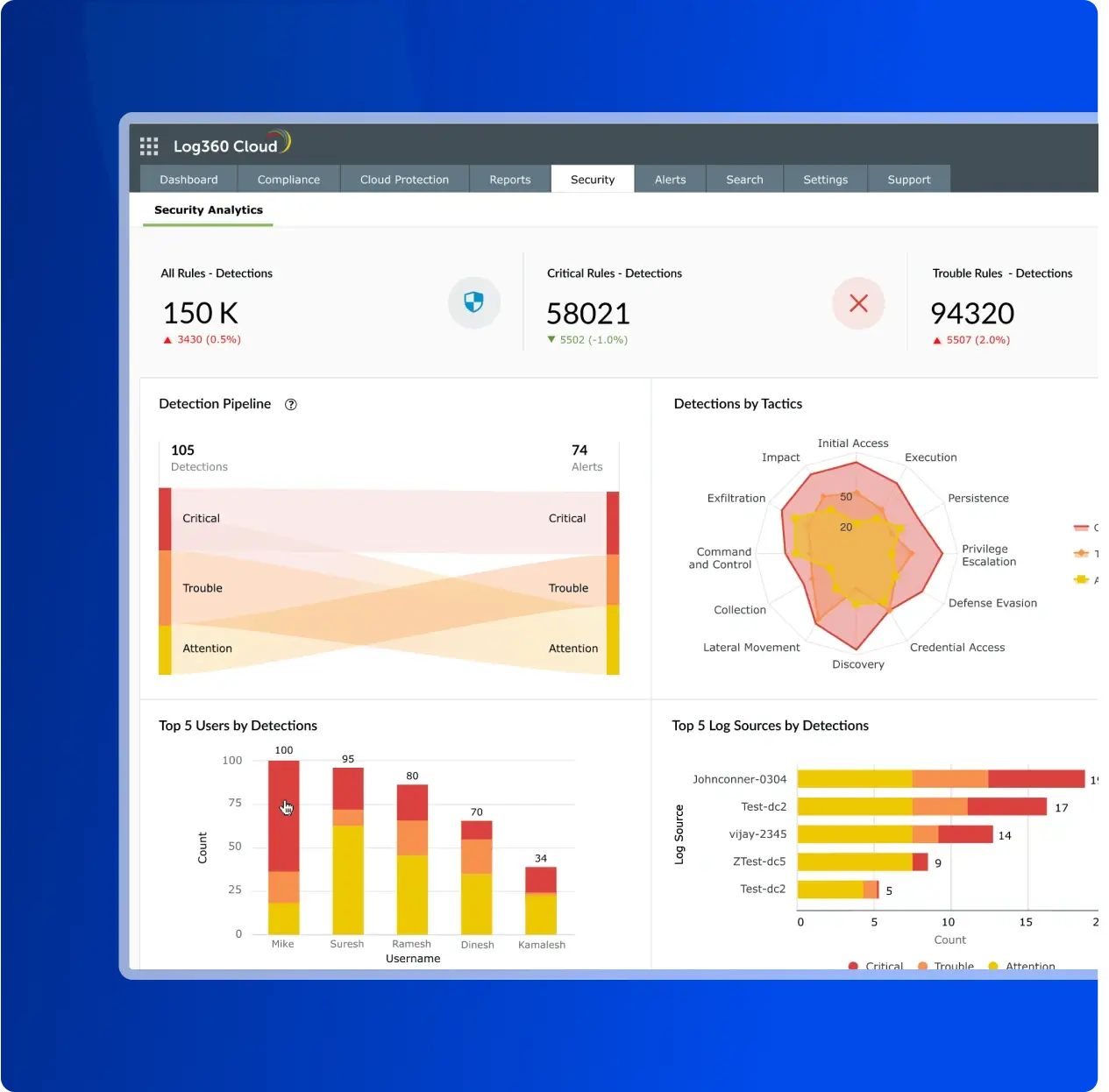
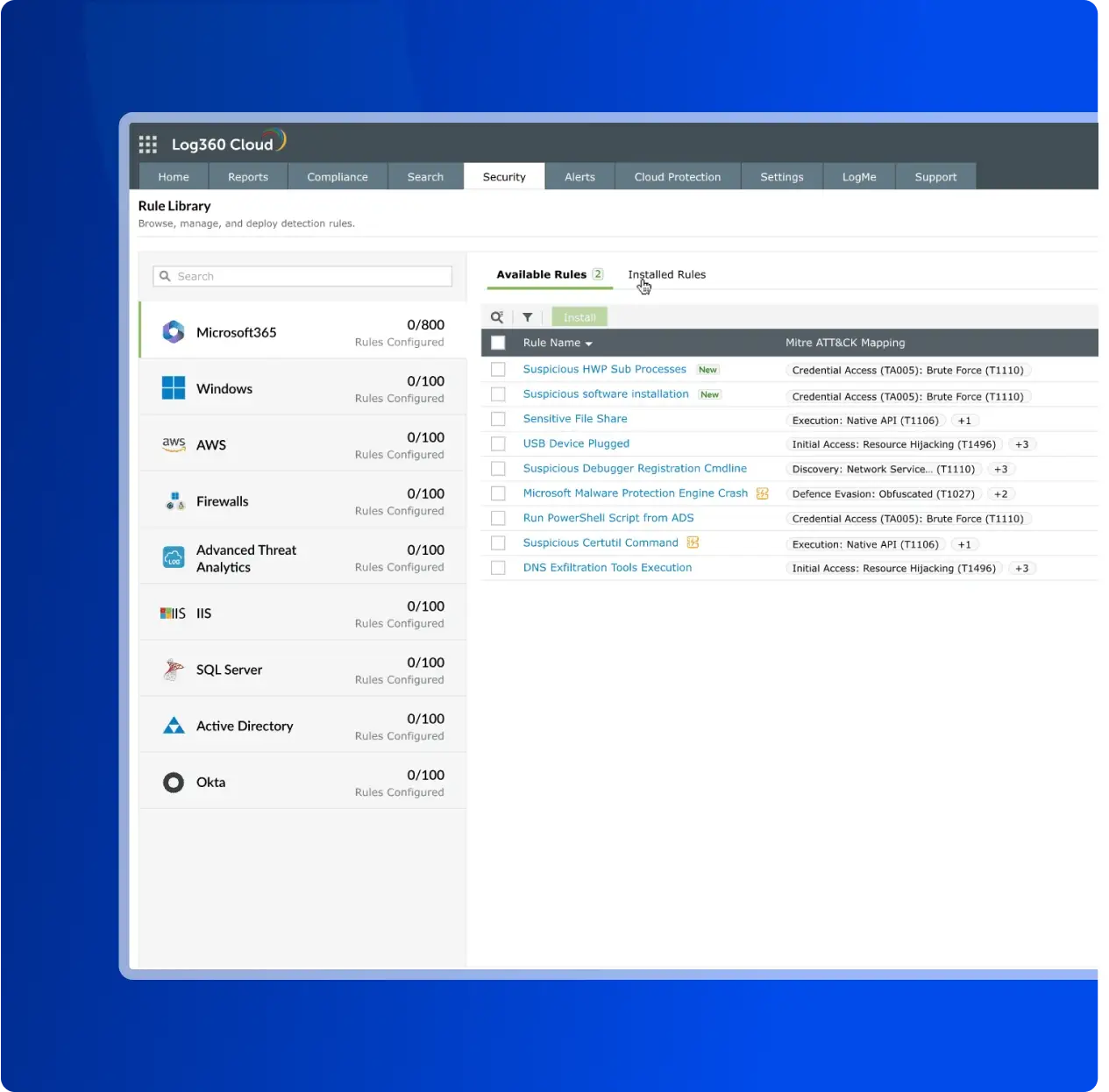
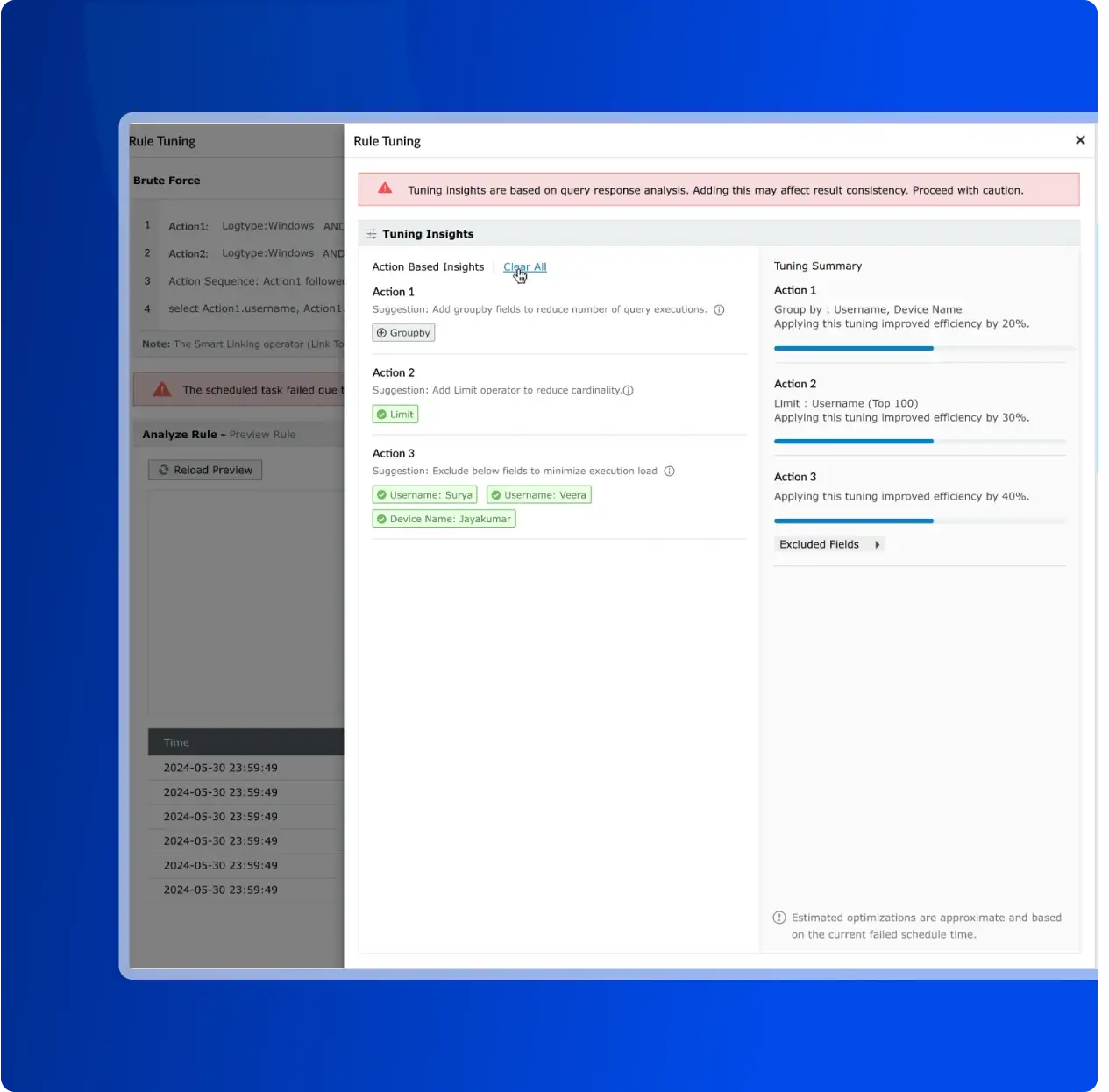
Threat detection is the process of employing a multi-layered approach to accurately detect and neutralize cyberattacks. An effective strategy is crucial for security operations, helping teams cut through alert noise and focus on what matters. This is achieved by combining real-time data correlation, user and entity behavior analytics (UEBA), and mapping threats to the MITRE ATT&CK framework to effectively prioritize and respond. Log360 unifies these capabilities, providing a centralized console for security analytics that delivers clear, actionable insights to strengthen your security posture.